Why are passwords hopelessly outdated and why are they still used?
A study by DLBI was released in February by the most popular passwords in Russia. Analysts collected accounts (email – password) leaked in 2023 and identified unique ones. In total it turned out 44 million records. Based on this database, researchers compiled the top most popular passwords.
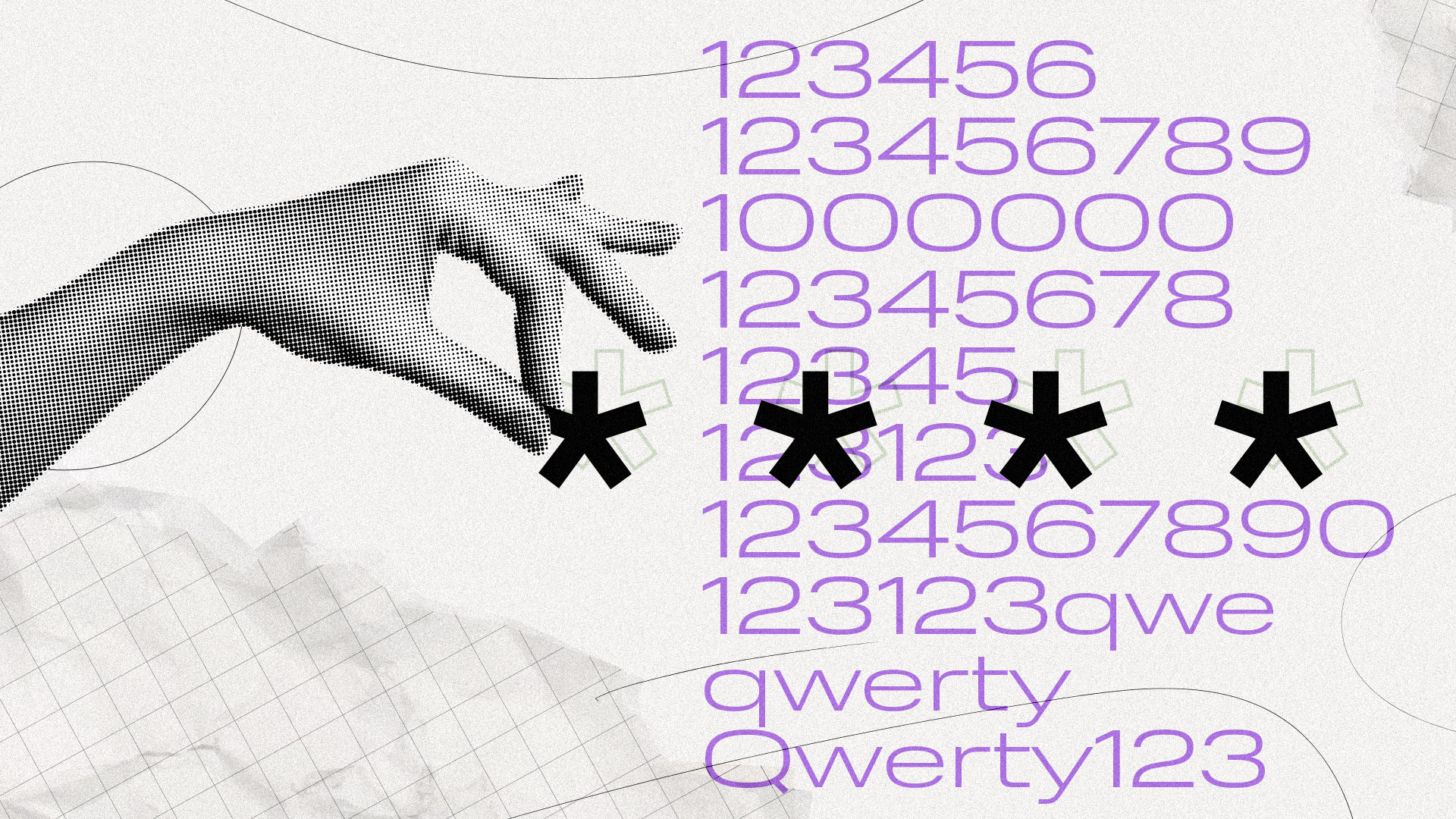
The most popular passwords of 2023:
123456
123456789
1000000
12345678
12345
123123
1234567890
123123qwe
qwerty
Qwerty123
This list makes you wonder: are we really living in the 21st century? It is surprising that, despite the abundance of articles about the rules for creating secure passwords, people still use options like “12345”. But the problem is not only with users – after all, developers also do not limit the possibility of using such combinations.
Even if the service requires a combination of upper and lowercase letters, numbers and special characters as a password, users choose combinations of adjacent keyboard buttons – “1qaz@WSX”, “!QAZ2wsx” and the like.
If passwords are so weak, is it time to forget them? I am Vasily Ognev, head of multi-factor authentication at MTS RED, and I will tell you why this is difficult to do.
The first computer passwords
The creation of computers required a scalable password system so that every user could get their own. Few people thought about safety back then. One of the first known passwords was used to restrict shared access to an IBM computer at MIT in the 1960s. It was a huge mainframe, and time on it was expensive. Fernando Corbato invented enter passwords so that each user has access to and access only their data at his appointed time. However, one of the scientists – Alan Sher – simply printed out a file with passwords and used someone else's credentials to get more computer time. He admitted this decades later, so the issue of password security became relevant after another incident.

In 1988, Cornell University student Robert Morris launched a program on the ARPANet network (the predecessor of the Internet), which, according to the plan, was simply supposed to spread across computers on the network, exploiting vulnerabilities in the mail protocol and selecting passwords from a dictionary. It even worked too well – due to flaws in the code, the program could be launched several times on the same computer, and searches for other computing systems overloaded the network. As a result, the software was called the “Morris worm” and, although it did not contain a destructive part, it actually became the progenitor of a new class of malware.
Analysis of the Morris worm showed how carelessly users treat passwords. After all, the program selected them based on the user’s first and last name and a dictionary of 24,000 words. And the attack was successful – according to various estimates, up to 10% of the network was “infected”. And at that time it consisted of 60,000 computers, not every user could get into it, and the behavior of its participants was most often “decent” from the point of view of information security. The same Morris himself surrendered to the authorities when he realized what he had done. As a result, he was sentenced to three years probation, a $10,000 fine and 400 hours of community service. This was not the worst outcome: Morris initially faced both a longer sentence and a larger fine.
How to protect and break passwords
In order not to store passwords in clear text, a solution was used that was known even before the invention of computers – a hash. Now the vast majority of companies store user passwords not in clear text, but in the form of hashes. But attackers are accustomed to exploiting the weakest link—humans.
For example, in the 70s, Unix became one of the first operating systems to store hashes instead of passwords. However, hackers took the most popular passwords (now you understand that the password 123456 is at least trivial and does not reflect the uniqueness of a person), calculated their hash and then stole the user hash database. If the calculated hash coincides with the user's, then the employee used the corresponding popular password. This password attack later evolved to create huge rainbow tables. Therefore, if user logins and password hashes are leaked, hackers can recover most of the original password values in a few minutes.
The remaining part is simply brute-forced – even the correct complex password can be cracked using a brute-force attack. Suppose the password contains 8 characters, includes letters of different case, as well as numbers and special characters – such recommendations were common among Internet services 5-10 years ago and even satisfied NIST recommendations (National Institute of Standards and Technology) 2017. All possible 8-character passwords are on the order of a quadrillion (million billion) combinations. Once upon a time, it would have taken either a lot of time or a lot of money to calculate the hash of each of them and compare it with the database. But now it’s a matter of 5 minutes and 6 dollars: Hive Systems conducted research and learned that in 2023, the 8-digit password is too easy to break. A brute force attack on rented cloud hardware (those same $6) and with the ability to distributed computing will be very fast.

Next, the creators of Unix modified the system so that users could not set a simple password, and when the hash was first calculated to the original combination added a random number – salt. Password with salt gave new hash value and hackers could not calculate simple passwords using rainbow tables. But since salts were stored with hashes in the same database, hackers learned to pick up this combo.
So why are passwords outdated?
Hive's research does not mean that any password can now be cracked in minutes, or at most hours or days. Firstly, access to the user’s password hash still needs to be obtained, especially when there is a hunt for a specific account, and not a mass selection of passwords. In addition, the study cracked the MD5 hashing algorithm, and there are options that are more resistant to brute force attacks – for example, algorithms of the SHA-2 and SHA-3 families.
The flip side of the situation: computing power continues to get cheaper. In the foreseeable future, it is very likely that affordable quantum computing will appear, which will make it possible to find any password-hash pair in a few seconds. And, most importantly, even without all these high-tech bells and whistles, passwords are stolen using much simpler attacks. Their input can be tracked by a Trojan program on the user’s device, and access to logins and passwords in the cloud database may be forgotten. Even password managers that create correct passwords and hash them securely sometimes hack – this is how user information becomes compromised.
But in most cases it is not yet possible to refuse passwords.
Replacement cannot be left
Perhaps the most important reason for continuing to use the familiar login-password pair is legacy. Users have accumulated vast experience and are simply accustomed to password protection, and a wide selection of tools has been created for developers to use passwords in services. In such conditions, it seems reasonable to leave the usual access system, but to be on the safe side – supplement it with another reliable method of protecting information.
Since the password is difficult to replace, it is supplemented with a second and third authentication factor. The first authentication factor is the “knowledge factor.” Usually this is a traditional login and password, although in some cases this role can be played by a code word, information about recent payments and other data that theoretically only the user should have.
Next, the user is asked for an “ownership factor”—information that only that user should have or receive. This could be a physical token with a one-time password (OTP) generator, or an application where the user first receives an initialization vector and can then generate both time-based (TOTP) and event-based (HOTP) one-time passwords. In the future, the MFA service recognizes users by their logins and knows what value the user must present at one time or another. You can also send an individual one-time code – via SMS, email or, for example, Telegram, but it is more reliable when the one-time code is generated in the application by time (TOTP).
Unlike a traditional password, the “possession factor” is almost impossible to brute force. In a couple of attempts (usually the number is configured in the MFA service), a hacker must guess a 4-5-6-digit number, that is, the chances of success are a fraction of a percent. In case of several errors when entering a one-time code, the system blocks access for some time. As a result, a pick-up attack cannot be completed in a reasonable amount of time. And, if the MFA system is configured correctly, no amount of computing power will help hackers.
The third factor could be biometrics, if there are others. Essentially, it serves to identify the user and is now often used when accessing an application, where a one-time authentication value (OTP) is generated to make authentication more reliable and comfortable for the user. The use of biometrics in conjunction with other factors is a recommendation not only from the Russian GOST, but also from the entire expert community. A password can replace the same OTP (and in some cases OTP is even more secure than weak passwords), but this is only true for systems that do not process sensitive data and are not associated with financial risks.
The idea of multi-factor authentication (MFA) seems obvious. It was included in the NIST recommendations in 2017, but conditions for the rapid growth of this market have only now emerged. MFA is becoming the standard, especially in services where account security is critical. For example, from October 1, 2023, entry to State Services is possible only with two-factor authentication. This is just the beginning of a trend: according to MTS RED analysts, the Russian MFA market will grow by 80% by 2027, to 5.6 billion rubles.
A new alternative is Passkey, a solution based on the FIDO2 standard: access key certificates are stored on the phone, and biometrics are used to access them. So far, FIDO2 has begun to be used primarily on the web (social networks, access to websites), but in the future it may come to the corporate segment.
Wait with a bright future
Microsoft research shows MFA's reliability when using long passwords and one-time codes exceeds 99.9%. The remaining fractions of a percent are the responsibility of hackers who do not give up and come up with ways to bypass the additional authentication scheme. In any case, MFA makes their task much more difficult and is therefore firmly in the top advice of almost all security experts. And the task of establishing a reliable MFA system without obvious shortcomings is completely solvable today. If you are interested in what vulnerabilities hackers find in MFA and how developers combat them, we will tell you about it in the next article.