Pentest Enumiration for macOS
Hello, Khabrovites. On the eve of the start of the course “Pentest. Practice of Penetration Testing” we invite you to sign up for an open lesson on the topic “Windows ad: collecting information, escalating privileges”…
And also we want to share with you another author’s article from our expert – Alexander Kolesnikov.
Typically, the infrastructure is built on Linux and Windows operating systems. And it would seem, why bother with the problems of other operating systems? It’s simple. Pentest is a constant development, the study of new technologies. In addition, machines in the infrastructure that run on the macOS operating system are no longer such a rarity.
The article does not claim to be complete information on the MacOS platform, but only demonstrates mechanisms and data that, in the opinion of the author, can be useful.
MacOS
MacOS is an operating system that is perceived in Russia as a proprietary system for Yabloko computers and laptops. This operating system, from the user’s point of view, is at the same time similar and different from Linux. how approves documentation, the operating system runs on the XNU kernel (X is Not Unix). Which suggests that something must make this operating system unique. The architecture of the operating system, according to the documentation, looks like this:
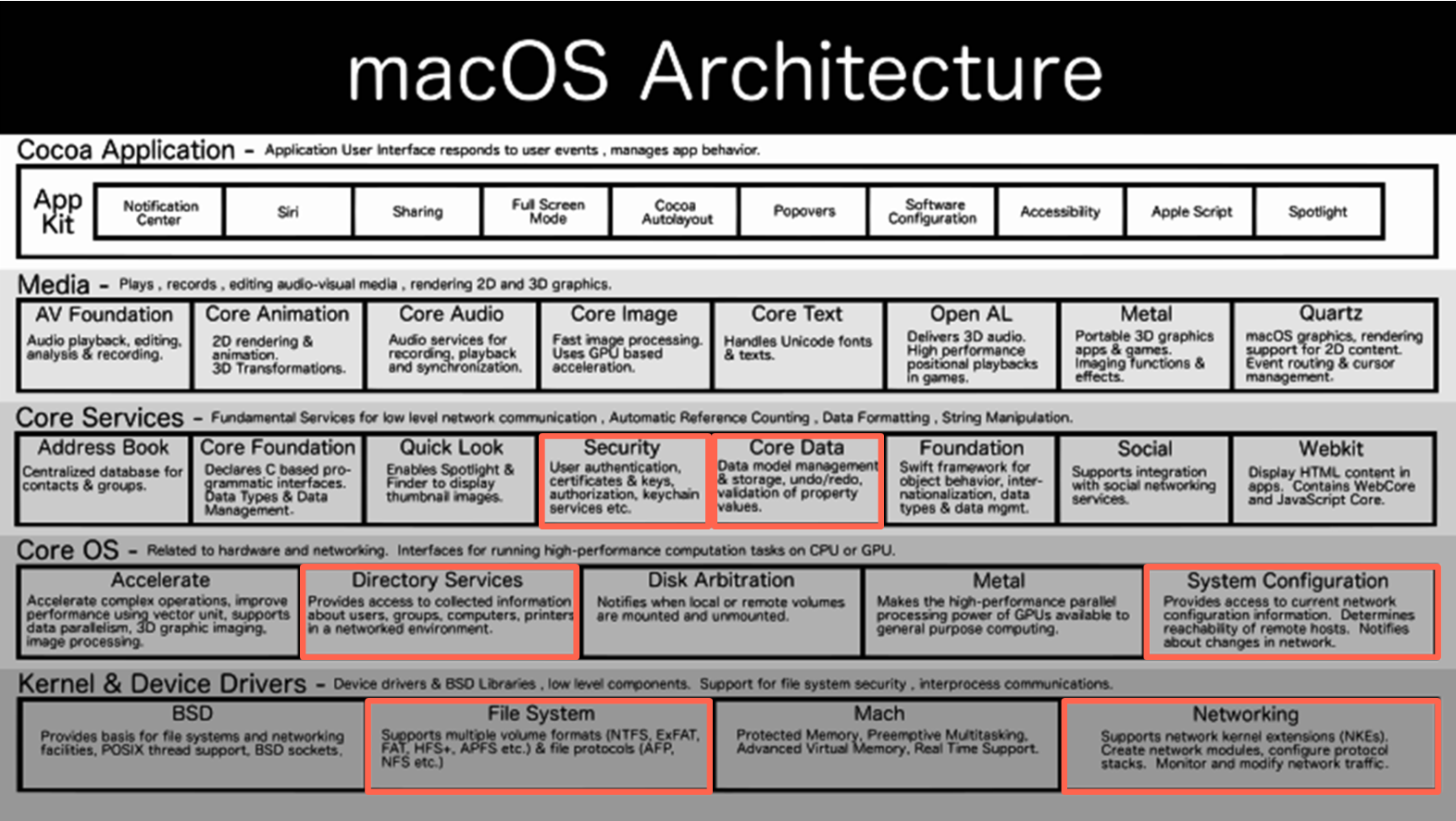
Potentially interesting subsystems for penetration testing are highlighted in red. In this article we will look at collecting information through “Directory Services”. The diagram shows that there is a lot under the hood that cannot be found in other operating systems. First of all, the abundance of frameworks used by the operating system is striking; there is also a part of the BSD project libraries inside the operating system. The most unusual thing that can also be found in some versions of the MacOS operating system are fragments of the Darwin operating system, which generally exists as an Open Source project.
The macOS operating system exists in 2 versions:
MacOS – custom version, pre-installed on all Apple appliances.
MacOS Server – a separate version, which is installed additionally from the application store and provides server functionality.
The server can be used to manage a fleet of Apple machines, or it can serve as a provider for integration into other infrastructure services. In terms of managing devices and credentials on the corporate network, macOS has an MDM and OpenDirectory set of services available in the Server version. In order for this to work, you may need additional snap-ins from the app store. A set of services that macOS Server can provide:
Open Directory – fromService, analogous to Active Directory in OC Windows.
Profile Manager – service for managing user profiles on devices.
Xsan – service for sharing directories.
Very similar to what we see in Active Directory. In general, systems running MacOS, according to the developers, can be integrated into any infrastructure, in particular, in Windows AD. MacOS also has its own set of Open Directory services – analogue of Active Directory.
MacOS users and groups
Like any other modern operating system, macOS provides a multiuser interface. And, just like other operating systems, it includes regular and system users. Let’s find out which users can be created from the macOS interface (System Preferences-> Users & Groups):
Standart user – a regular user cannot configure the operating system.
Administrator – a user who can install new software, configure the system, manage other accounts.
Sharing Only – a user that can be created to be able to share directories and operating system resources.
Groups – grouping users, just like in Linux / Unix operating systems, a group has its own set of privileges that each user in the group gets.
In the vastness of the documentation, there was also root, but Apple did not recommends include this user. It looks like it’s not just Windows that likes to hide additional users. We could not get more information from the user interface, but among the commands that are available from the terminal there is the dscl command – a terminal tool for working with “directory” services, in other words, this tool allows you to collect information about the configuration of the operating system and the infrastructure where it runs.
For example, this is how you can see what users are in the system, the key point is ALL users, including system users:
dscl . ls /UsersThe figure above shows only a fragment of the list of users, in fact, in a system in which 1 user works, this list consists of 141 users. This is where the catch of all these “simple” users who are created from the operating system interface was.
We got the list of users, now we need to find out about the privileges. Data stored in macOS is very similar to how it is stored in Windows AD. Each user is an object that has its own set of “property” values. To show these values, you need to replace the ls command with cat:
dcsl . cat /Users/daemonJudging by the output of the tool, we have a user who does not have a command shell and is used for the system. Let’s try to look at a more “live” user, for example – root:
The data is more than exhaustive, the output contains a list of user rights and characteristics in the plist format – the file format with which iOS and macOS describe objects and assign rights. It also has “Property” which is used to “integrate” into Active Directory. This can be seen by SMBSID, RecordName and UniqueId. You can use this data at the stage of network exploration. In general, the dscl tool can do much more:
dscl . ls /The picture shows additional objects that can also be studied in the process of collecting information and interacting with Active Directory from a compromised macOS. For an analogy, in the Windows operating system for some of the actions for collecting information, there is a command net users/net groups…
MacOS Active Directory
Let’s transfer from the local version of the operating system to AD. Let’s say we managed to compromise a macOS machine. What can be done now, how to collect data? How do I list objects via LDAP? How do I get domain configuration information? How to collect data about computers on the network?
Let’s get a list of users:
You can get even more data that will contain more information:
This is how you can collect information on machines in a domain:
Command for examining data about a domain in general:
From the command output, you can set the domain, domain settings, and password policy data.
Conclusion
The study of a large number of technologies still bears fruit. Knowledge of operating system mechanisms other than those used in a corporate environment can increase the complexity and thoughtfulness of penetration testing. This article has demonstrated how it is possible, without resorting to third-party tools, to collect information about the infrastructure, having access to a regular user in macOS. How much more can you do to test successfully? On attacks on the macOS operating system, I recommend taking a look here…
Learn more about the course “Pentest. Practice of Penetration Testing”.
Sign up for an open lesson on the topic “Windows ad: collecting information, escalating privileges”.
Read more:
How privilege escalation exploits work in Windows




