DEFCON Conference 27. Your car is my car. Part 2
At the end of the video, you heard a click – it worked the unlocking of the mechanical steering wheel lock, which we cannot bypass electronically. It is necessary to use something mechanical, to break the lock cylinder manually or to do something similar, which I was not going to do with her car. All the firmware demonstrated in these videos will be available on GitHub after my presentation, so you just go to the address indicated on the slide and download the OpenRemoteStart file.
Let’s talk about what exactly happens when we add the Internet to this system, because this should be beneficial, right? As I said, I purchased a remote alarm control module called MyCar. It is available in various versions, I had a Linkr LT-1 model.
MyCar is just a brand, and such modules are sold under the names Linkr LT-1, MyCar KIA, Visions MyCar, Carlink (CL6), etc. As it turned out, for some time KIA dealerships in Canada installed this system on cars or, at least, an application called MyCar KIA. Interestingly, this application is no longer available for download on the AppStore. I also want to note that I opted for Fortin and MyCar products, but according to user reviews on the topic forums of freelance car alarms, other systems behave no better and have similar problems.
I had an important question: why is a product with security problems being sold on the secondary market for car alarms, and does it bother anyone? Therefore, if any of you are interested in remote starter systems, pay attention to a couple of important circumstances. Firstly, as I mentioned earlier, if the DS system is not installed correctly on a car with a mechanical transmission, it is quite possible that after a remote engine start, the car will simply go without a driver if some gear is in the gearbox. This is really dangerous. The second danger is that if someone parked the car in a garage attached to the house and his engine accidentally remotely turned on, you could suffocate from the accumulated carbon monoxide. So if you have a DS system and an attached garage, you should definitely have carbon monoxide detectors.
If you use a DS system, never try to start the machine engine without knowing exactly where it is, because the consequences can be disastrous.
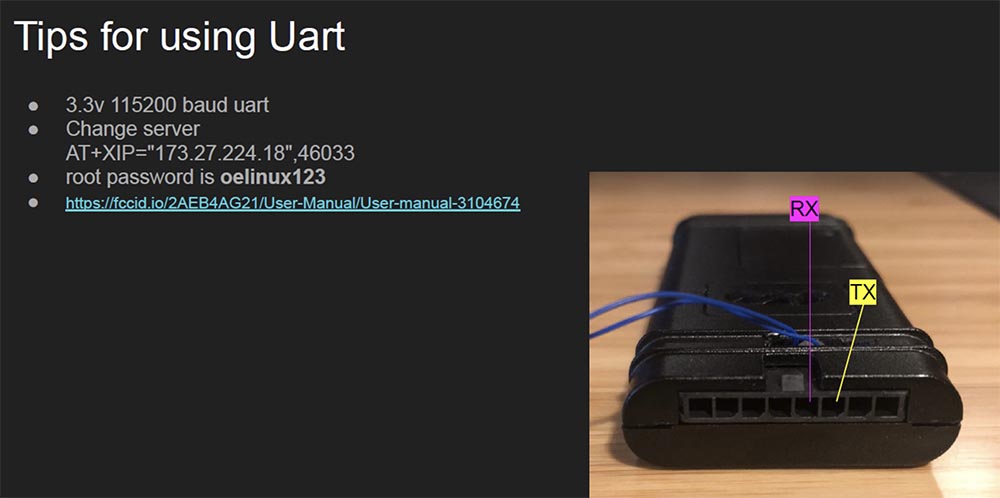
MyCar, a small black box with two wiring coming out of it, has 8 ports, two of which are for the debugger interface. Connecting to this interface showed that the device is running Linux, which the manufacturer is silent about. It’s easy to get into the firmware shell using the oelinux 123 password, but you can use the AE Engine without logging in, which allows you to enter AT commands from the command line, including the command to change the IP address of the device that this module communicates with.
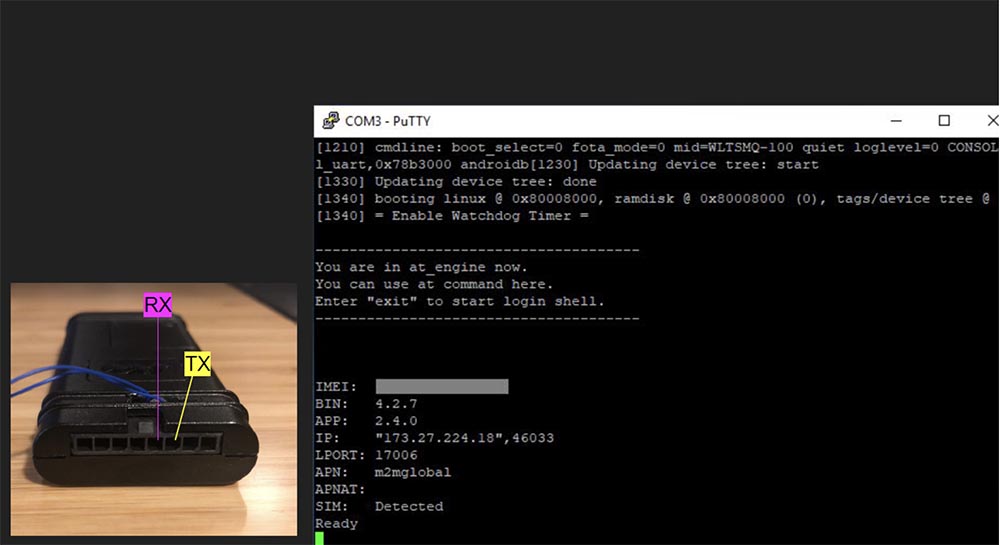
If we look at the lines below, we can see the IP address of the server from which the MyCar module receives firmware updates. The device is equipped with an L-port, which allows you to “listen” to the commands received by the module. Using the AE Engine and changing the IP of the paired device, I was able to determine that this device communicates with the DS using the unencrypted UDP protocol.
I did not particularly delve into this, but I think that this is a rather significant and interesting fact. If you are interested in additional information about this device, take a look at this slide – it shows the voltage 3.3V, data transfer rate 115200 baud, server address for updating the firmware, root password and a link to the user manual.
The device may also be “tolerant” of a higher supply voltage.
As I said, it can be quite cold here. About a month after I gave this system to my girlfriend, I decided to pull the unit out of the car and work with it properly. The fact is that all this month I drove from myself thoughts about the vulnerability of this device. The next week they promised frost to -30F °, so I had to rush. I connected to the shell and made it work, but since the cellular connection in my home laboratory is not very good, I decided to work with the unit on another computer. The FTDI device that I use has a short cord, so I found another one, longer, connected it to the DS unit, connected it to the computer, and as soon as I turned on the power, my module began to smoke!
From this we can learn a lesson: if you are engaged in hardware hacking, have a spare block ready! My girlfriend stated the moral of this story: if your soulmate is a hacker, don’t let him play with your Christmas presents! Now, let’s look at the software, I think nothing will smoke here.
I launched a man-in-the-middle proxy server, turned off SSL checking on my phone, and began to watch what traffic the application sends to the server side. When registering, I noticed that the system takes my email address and sends it to the web service to make sure that this address is associated with an existing account. Interestingly, in doing so, the system used basic authentication because I had not created an account yet. I did not know what to do with this information, so I just wrote it in a notebook and moved on. I created my account and logged in, and the first thing the application does when logging in is calling a web service to check the current user. So I just called this web server using the credentials that I saw earlier, and which were used to check if my email address exists, and in response received Mycar Admin access.

I doubted that this was the account of the real administrator of the system, because, despite the loud sound, it had low privileges. In the end, we all know such people.
Therefore, I create another request – the EngineStart team, to start the car from this account, click “Send”, I get the status of the command – “200 OK” in response, and after about three seconds my car starts to move.

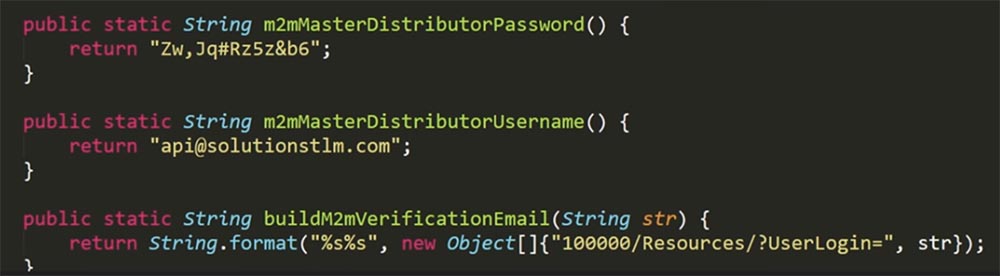
As it turned out, the Mycar Admin account was really an administrator account, hard-coded into the mobile application. But that is not all. In one of the previous slides, you saw such a thing as an API key. Again, from monitoring the traffic of my fake proxy server, I found out that these API keys can be used instead of a username and password. If you use “API” and one of these keys as the username, you can authenticate the user.

So I copied the contents of the “APIKey” line, pasted it into the Password line of the POST application and clicked the “Send” button.
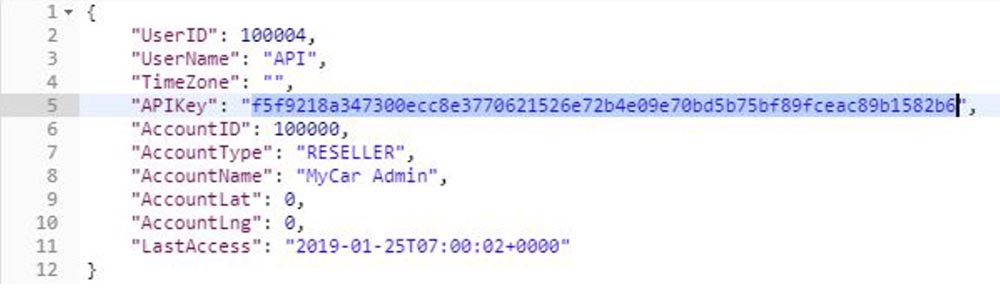
However, this did not work, and for a long 5 minutes I could not understand why. Finally, it dawned on me that I forgot to cut out the quotation marks and comma in the copied API key, which I was informed about: “You made a mistake in the SQL syntax.” It became clear to me that you can simply use basic SQL injection to bypass the entire login process and become an administrator or any user you want. I don’t think anyone tried to steal a car using SQL injection, so let’s try to do it.
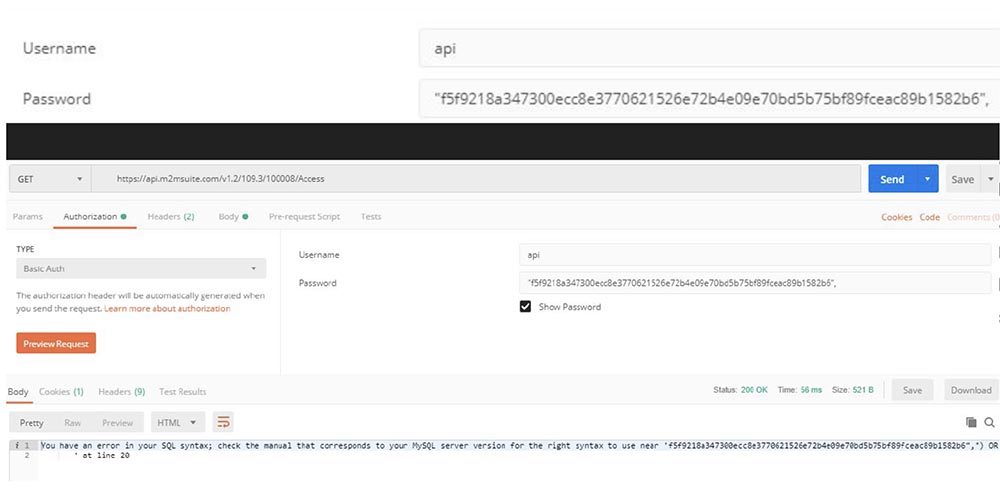
In general, I logged in with my account, clicked “Send” and received the status “200 OK” in response. This time I realized to record a video. It’s a little dark because I shot late at night from my office window. So, I enter the command, and you see through the window that at the bottom in the courtyard of the car headlights flash. At first, their light is weak, but then the headlights begin to shine at full power – this turned on the engine. So, I started the car using SQL injection (audience applause).
But that is not all. SQL injection can be used not only for authorization, but also to replace other parameters, such as URLs, query string body parameters, etc. In fact, this system uses SQL injection everywhere. Looking at the error messages, you can see that what we enter as a password is compared directly to the password column in the database.
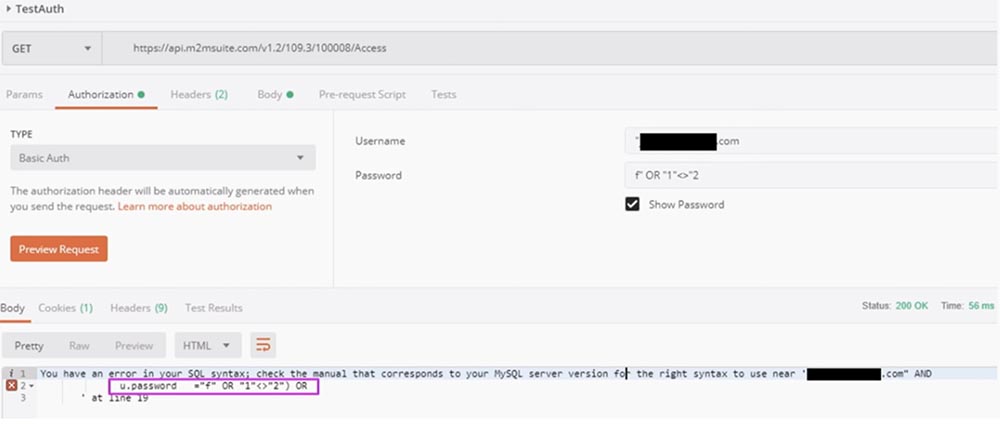
This means that they use simple text passwords in SQL injections. As the saying goes, “this is not at all good, but even very bad!” But enough about SQL, let’s see what else can be done to remotely start a car. You simply send the “EngineStart” command and in return you get an integer identifier, which is the identifier of this command, in this case ID = 3. Knowing the identifier, you can “pull out” a service that reports the status of this command.
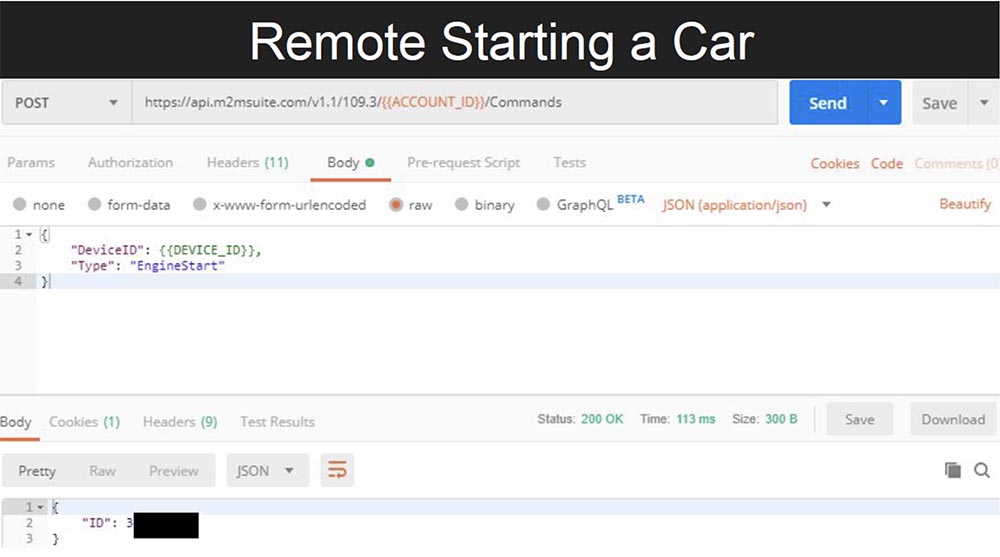
Thus, increasing or decreasing the ID value, I “pull out” the status of any team that has ever been sent to this system.

However, this is not particularly interesting, and I wonder if there is a direct indication of an object that I can use to start my car. Therefore, I launched the EngineStart command on behalf of a legitimate user from my account, and then tried to call it through another user’s account, which should not have access to the system. In response, I received an error message: “This account is outside the context of the hierarchy.” So, perhaps, this hacking method will not work. However, if you look at this API, you will see that it duplicates the information – the user’s email address is comparable to his account ID.
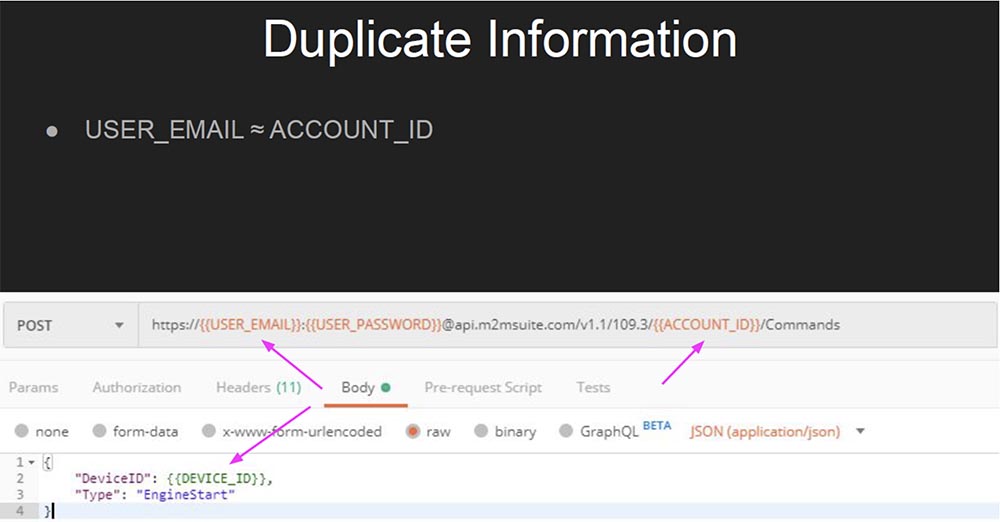
If you are developing an API or hacking an API, such duplication of information that we see in this URL can be a source of errors. In this case, API bugs can manifest themselves in four different ways.
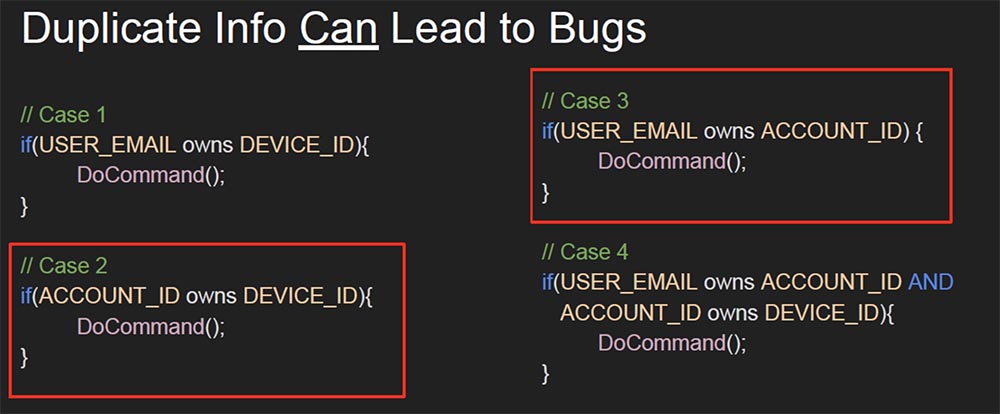
If you look at cases 2 and 3, circled in red, you can see direct links to the object. In both cases, the system does not check whether you are authorized to execute this command. I tried case 2 and it did not work, but what about case 3? Here we just have to replace the account identifier USER_EMAIL in the URL, as it is directly linked to the account identifier ACCOUNT_ID. Previously, we used the victim account ID, and now we use the attacker account. Therefore, I used the identifier of the hacker account and the identifier of the victim’s device, sent the command and, as expected, received the status of the “200 OK” command and gained control over the MyCar application.
Thus, using three different attack vectors, we were able to do everything that a legitimate application user can do. This means that you can find any car in the city, set its make and model in the application, and then remotely unlock the car and start it. We can turn off or on the alarm, make changes to the service menu of the car and check the status of any team. And all this can be done in three different ways.

Obviously, the MyCar developers tried to somehow fix the system bugs. So, in the case of hard-coded passwords, they simply put a reverse proxy server in front of the application to hide the credentials that are used for authorization. The problem is that reverse proxies are not magic and are not able to fix all problems. They saved the SQL injection in a third-party service, so even without a password, I can still use it through the user verification procedure.
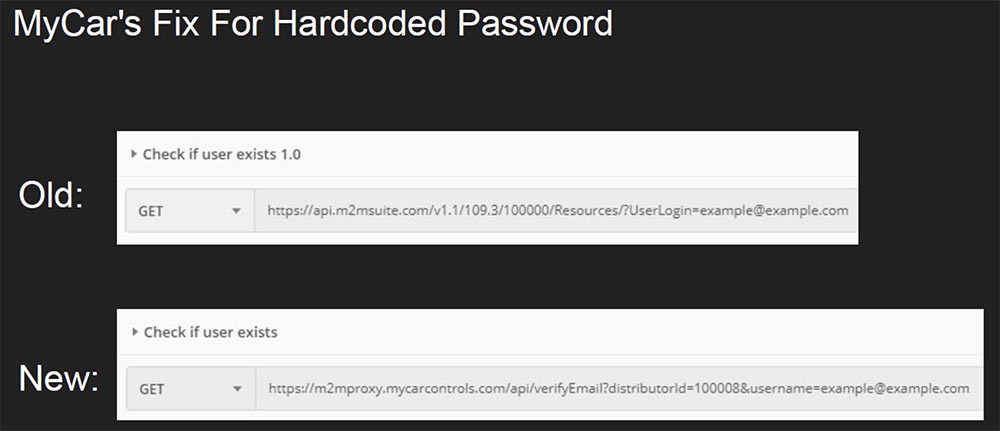
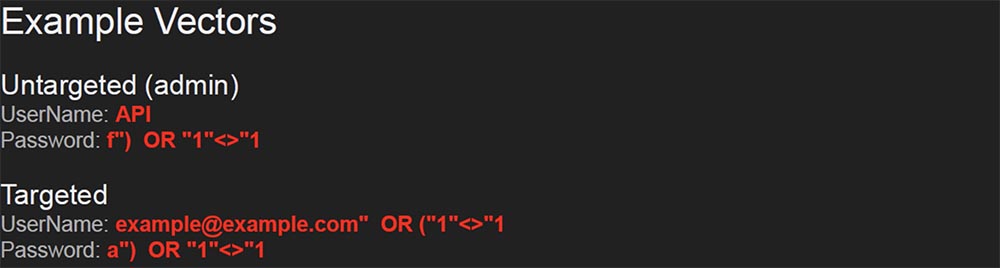
I decided to take a closer look at the structure of the URL. You may have noticed that all addresses used by the system contain m2m. Having decided that this is some type of internal interaction for the authorization mechanism in the MyCar application, I entered these letters in Google and discovered the M2M Suite website. The only thing left for you to do when you see this form is to insert a couple of single quotes there and see what happens. And what happens is that you get the right SQL injection (audience applause).
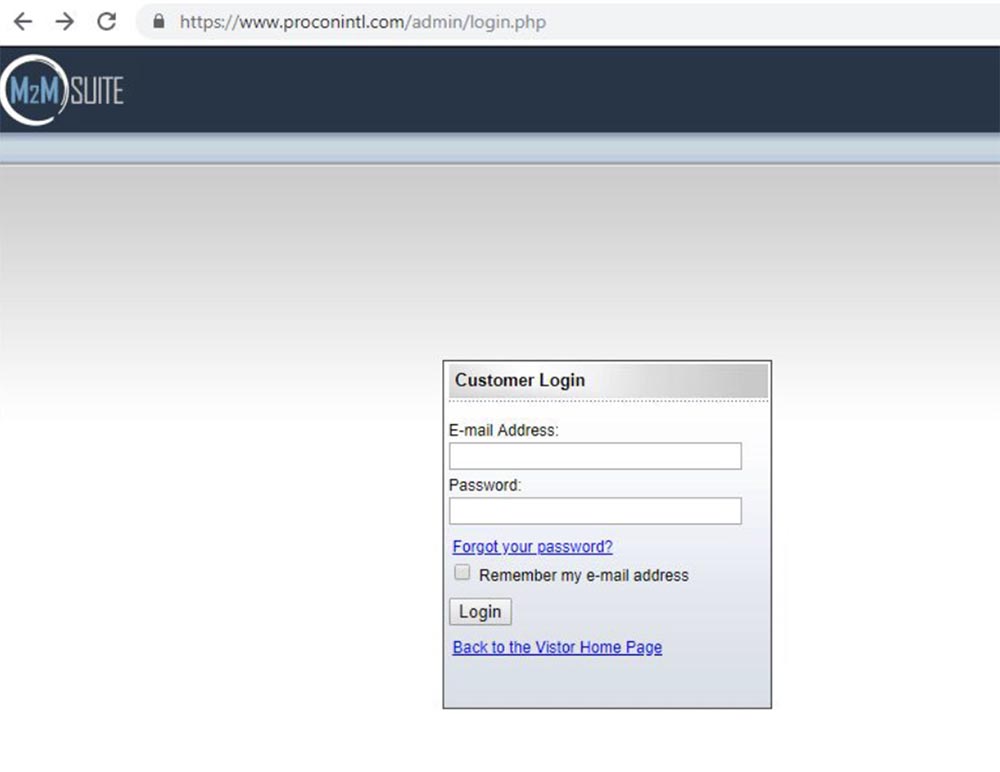
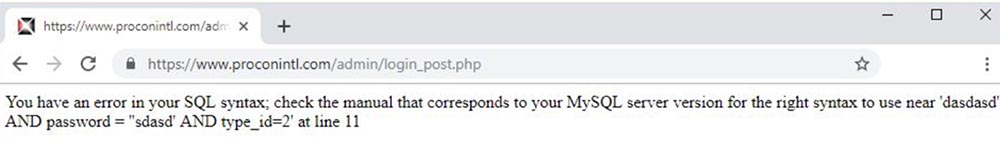
And this happens a few months after the developers reported a problem with SQL injection. If the application has such problems, they need to be fixed as soon as possible, but as you can see, the developers did nothing. Such a disregard for users, I find it offensive.
The MyCar module has a GPS unit, so it can track the location of your car and display it in the application. But, as it turned out, they store not only the current location of cars. They store a hell of a lot of information, much more than necessary in order to track the current location of the machine. In my case, for 13 days of using the application, they accumulated a little less than two thousand geolocation points of places where my car was. The privacy policy of the MyCar developer does not say a word about this collection of information.
However, further it gets worse. You may argue that this is just a side effect of the implementation of the geolocation service. But the fact is that instead of simply creating a list of places in which your car is, they use another API that analyzes this data and determines the places in which your car is most often. Again, as far as I know, in the privacy policy there is no hint of such a function. Perhaps this is not so surprising, because after a bunch of searches, I found the parent company MyCar called Procon Analytics, went to their site and visited the FAQ section. Here I came across the question: “How do you ensure data security?”. The company’s response was: “Unlike public cloud environments that fight for storage priority, Procon Analytics uses its own virtual cloud, which is used exclusively for users of our application and is protected from other users. This is a special cloud environment with a high degree of protection, which provides easy availability and speed of service delivery. By working with Procon Analytics, you can be sure that your data is well protected. ” I don’t even know what to say …
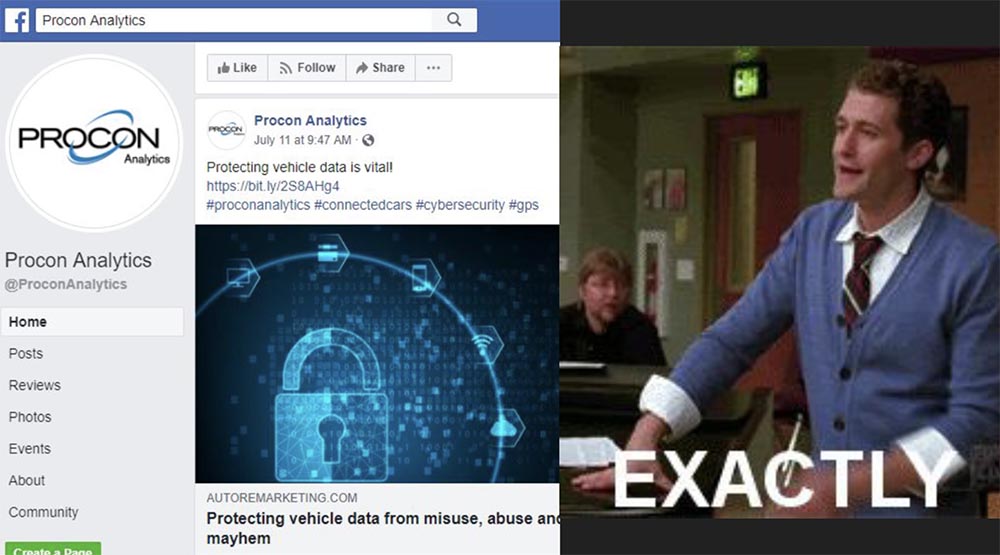
If you go to their Facebook page, you can find out even more interesting. Here they directly write: “Protecting information about your vehicle is vital!”. Well, I can only agree with this statement.
So, back to the question I started with: “How does this happen and how can this be avoided”? And more importantly, how can we, as a community, prevent this?
This is the end of my report, but I can still answer a couple of questions (audience applause).
Are you asking if they have fixed everything? At the moment, I think that they have fixed all the bugs that I reported to them, except for the shortcomings of the privacy policy, which I mentioned at the end of the speech. The last time I checked it, everything was unchanged. To the question, can I edit the parameters of the ECU electronic engine control unit in this way, I’ll answer that my task was to edit the car’s parameters only in the MyCar application. It stores the digital representation of the car, which is edited using direct access to the object, SQL injection, or another attack vector.
The last question is: do I have a keyless engine start system in the car with the Start button, and how is the situation with locking the steering wheel in this case? My answer is that MyCar has such a button, so this system does not have a steering wheel lock. I suspect that if you install this system, you definitely cannot rely on a lock to lock the steering wheel.
A bit of advertising 🙂
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to your friends, cloud VPS for developers from $ 4.99, A unique analogue of entry-level servers that was invented by us for you: The whole truth about VPS (KVM) E5-2697 v3 (6 Cores) 10GB DDR4 480GB SSD 1Gbps from $ 19 or how to divide the server correctly? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper at the Equinix Tier IV data center in Amsterdam? Only here 2 x Intel TetraDeca-Core Xeon 2x E5-2697v3 2.6GHz 14C 64GB DDR4 4x960GB SSD 1Gbps 100 TV from $ 199 in the Netherlands! Dell R420 – 2x E5-2430 2.2Ghz 6C 128GB DDR3 2x960GB SSD 1Gbps 100TB – from $ 99! Read about How to Build Infrastructure Bldg. class using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?