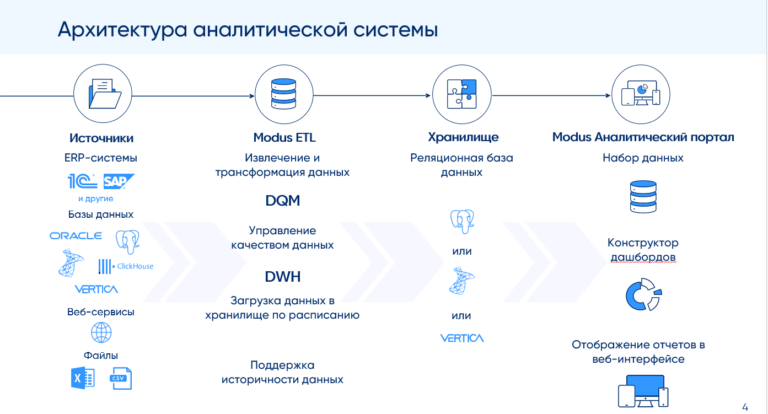
Classification of secure messengers. New projects
Nowadays it is difficult to imagine a normal life without a reliable, secure connection. Previously, secure encrypted messengers were used mainly in business, the army, the financial sector and other sensitive areas, but now they are in demand absolutely everywhere, up to ordinary citizens who want to calmly communicate with each other on any topic, without fear that someone will accidentally see the messages – an outsider.
The standard features of secure messengers are confidentiality, integrity, message authentication and protection from strangers, i.e. from forging, deleting or inserting messages.
The most advanced tools support perfect forward secrecy (session protection with ephemeral keys), including reverse message protection and post-compromise protection.
Roughly speaking, reverse message protection means protecting the data that was exchanged before the private key (device) was lost, and post-compromise protection means that security can be restored after an attack.
All this is done in the end-to-end encryption (E2E) mode, which allows you to securely transfer data even through an insecure server that is not trusted, including through open channels.
List of secure messengers
All existing messengers can be called protected to some extent and classified according to different criteria. For example, only end-to-end encryption is important to someone, while decentralization is also important to another. Someone will also take into account ease of use, because a program with a complex interface will not be available to a wide audience, which means that you will not see all colleagues, friends and relatives in it.
Here is one of the options for subjective classification based on this list:
Level 1. For beginners
- signal. The most famous messenger with reliable end-to-end encryption, uses advanced cryptographic protocols, many functions, a clear interface, open source. The main disadvantage is the binding to a phone number during registration. Another drawback is that all traffic goes through a central server in the US jurisdiction (since the company is registered in this country) with all the ensuing circumstances.
- Molly. An independent fork of Signal for Android that does not require SMS to register. At the same time, the client is compatible with the Signal network, that is, it allows you to exchange messages with users of a standard messenger.
Level 2. Better protection, but centralized
- threema: easy to use open source messenger from Swiss developers. Does not require a phone number or email address when registering. Of the minuses – the lack of direct secrecy and automatic deletion of messages.
- blackberry messenger: Canadian messenger, paid, focused on corporate users.
Level 3. P2P, decentralized
- twin.me: P2P communication where only a signaling server is needed for coordination, but the messages themselves are sent directly from one device to another. Registration does not require any data, but the ID is tied to a specific device. Of the minuses – the inability to transfer the account (keys and messages) to another device.
- Snikket (XMPP): more advanced option for users who can raise the server. The XMPP server itself is based on Prosody, the Android client is based on Conversations, and the iOS client is based on Siskin. Group chats are supported. Messages are stored on the server so that they are not lost if the client device is lost, although this can be regarded as an additional security risk. The OMEMO protocol is used for encryption.
Level 4. Alternative networks
- Briar. A peer-to-peer messenger that connects devices via the Tor network. Each device has a unique onion address, so the whole system works without central servers or other infrastructure. Among the shortcomings – less functionality than other messengers, the presence of clients only for Linux / Android, the inability to transfer an account to another device.
- OnionShare: another secure messenger (chat server) that works through Tor. The server can be raised under any OS, and the Tor browser is used as a client to connect to the server.
Level 5. Experimental (for enthusiasts)
- session: decentralized private network running on top of onion routing network Lokinet, uses the Signal protocol for encryption. The project is new, experimental, but promising.
- SimpleX Chat. A new project that meets all the criteria for secure decentralized communications, except for peering through a proxy server. Other than that, it’s a highly paranoid system. It is positioned as the first messenger without user IDs, even without random numbers, which “drastically improves privacy”, since an outside observer (for example, an ISP or an advertising agency) cannot deanonymize users and associate them with social media profiles even after long-term monitoring of traffic. Eat console client and other pleasant surprises.

- Cabal: new messenger on the protocol Dat. You create a “group” (cabal). In fact, this is an encrypted database that is copied by everyone to whom you give the public key. The project is still at a very early stage, so it is not known how well the protection will be implemented.
On such a subjective four-point scale, only two of the listed messengers meet all security criteria: this
And
.

This subjective review did not include some well-known projects, including Element/Matrix, which according to some criteria is considered the best in its class. Therefore, we have added the sixth, highest level of secure messengers/protocols.
Level 6. Best messengers
IN
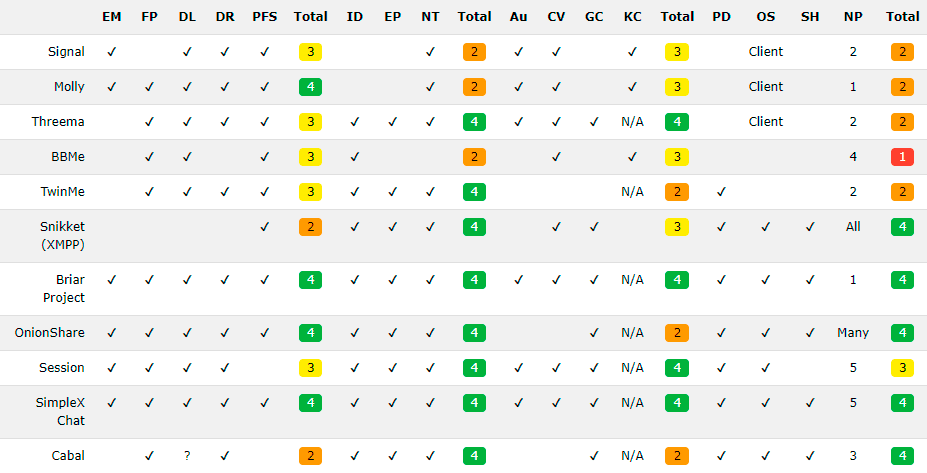
you can find a more complete classification of all known instant messengers and communication protocols. Here the estimates are binary: YES/NO. According to this scheme, the top ten messengers / protocols are as follows:
Fragment of the general table:
To the above classification, one can add the recently published report with an analysis of seven possible attacks on Threema cryptographic protocols. The authors emphasize the importance of their research in light of the fact that this Swiss messenger is used by the Swiss military and some officials, including German Chancellor Olaf Scholz.
Even before we started our work, we knew that Threema had neither reverse message protection nor post-compromise protection. Study showedthat some other security properties also fail. The work highlights the difficulties that developers face when creating secure messaging systems, since it is in principle very difficult to defend against all possible threats, including unknown.
We add that the German public services use as a standard messenger
,
and a similar client has been developed for the Bundeswehr
.
Practice shows that end-to-end encryption is becoming an increasingly popular option for IM. Perhaps this useful practice will be implemented in the future by the most popular instant messengers, including Telegram (so far it has been implemented there only for special “secret” chats), Viber and WhatsApp.
Hubs: Information security, Decentralized networks, Messengers, Cryptography
Tags:
Cover for social networks: