Why the new .zip and .mov domains are Google’s gift to scammers
In recent years
.zip and .zip: confuse indistinguishable
The zip and mov files have been around for decades: zip is the de facto standard for archives, and mov is one of the most popular video containers. The mov and zip domains are designed by Google for techies, but basically anyone can acquire them for any purpose.
Thus, now, having met a mention, for example, update.zip, only by context can one understand whether it is a question of a site or a file. But the context is understood by people, computers usually cannot. Therefore, such a mention can cause problems in a wide variety of applications, for example in this example of Kaspersky Lab on Twitter:

It is clear that this tweet refers to the files, but Twitter turns their names into links to websites. If you register the test.zip and movie.mov domains, then those who click on the link to the file can expect, for example, thematic phishing.
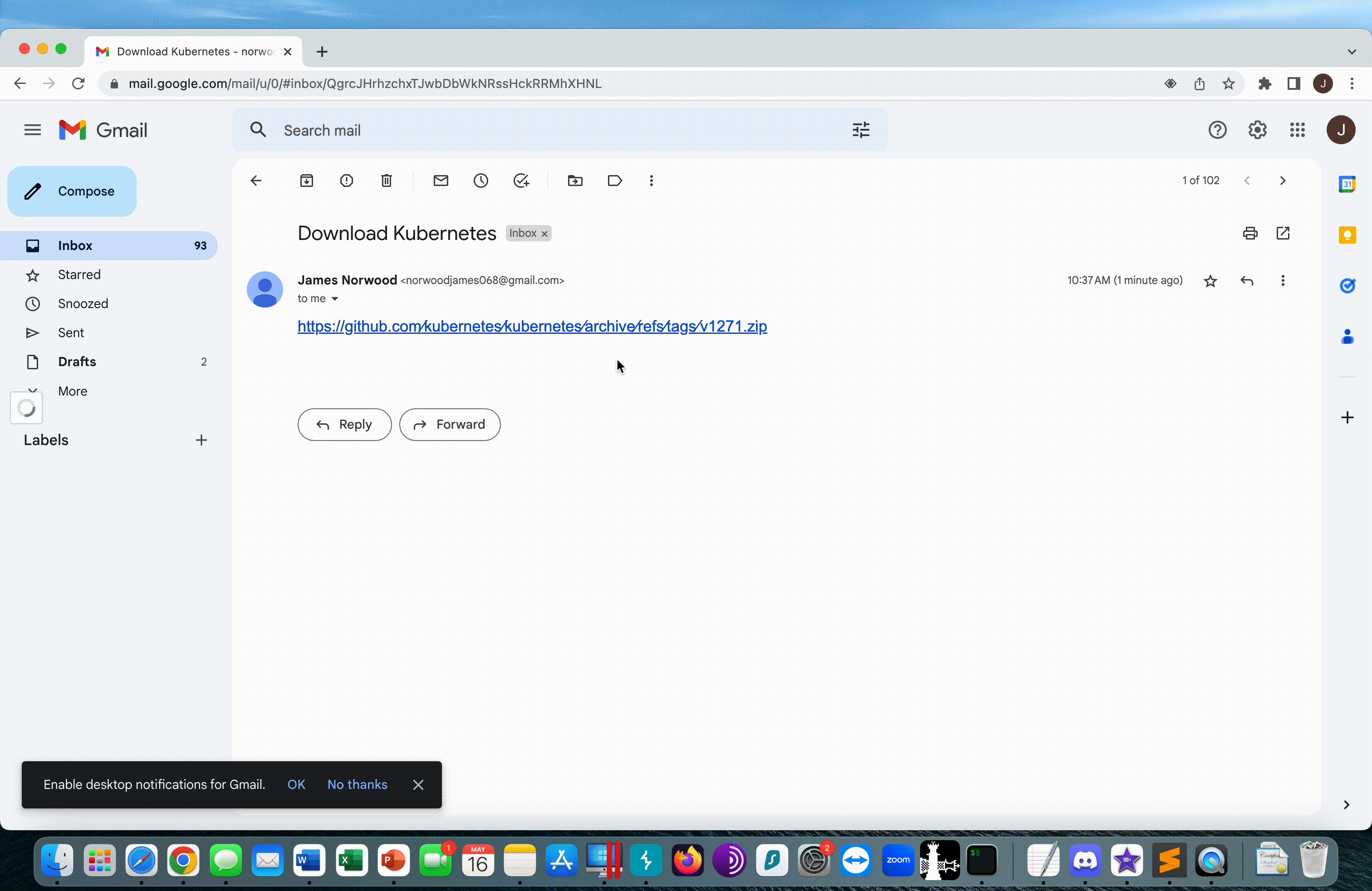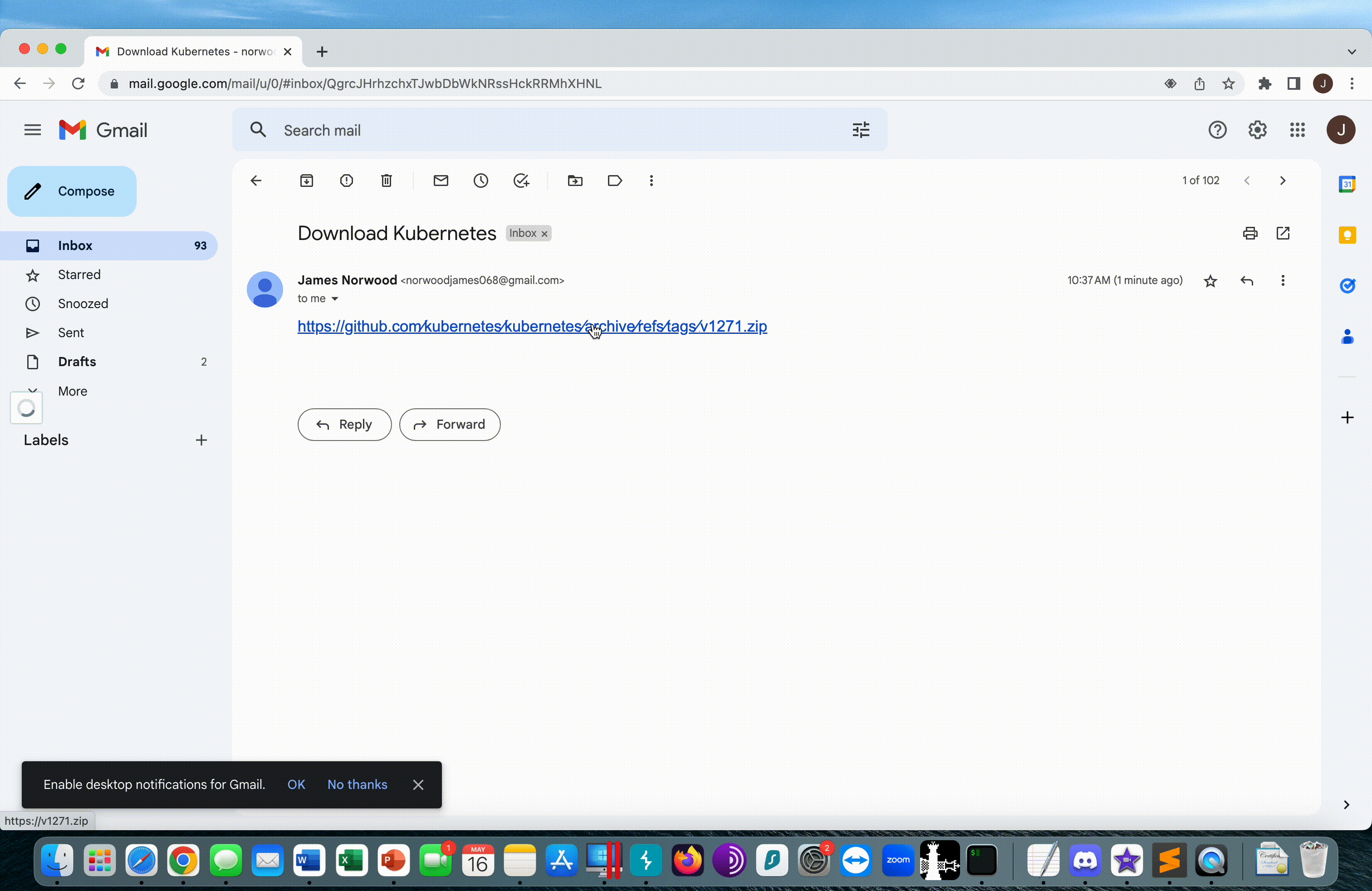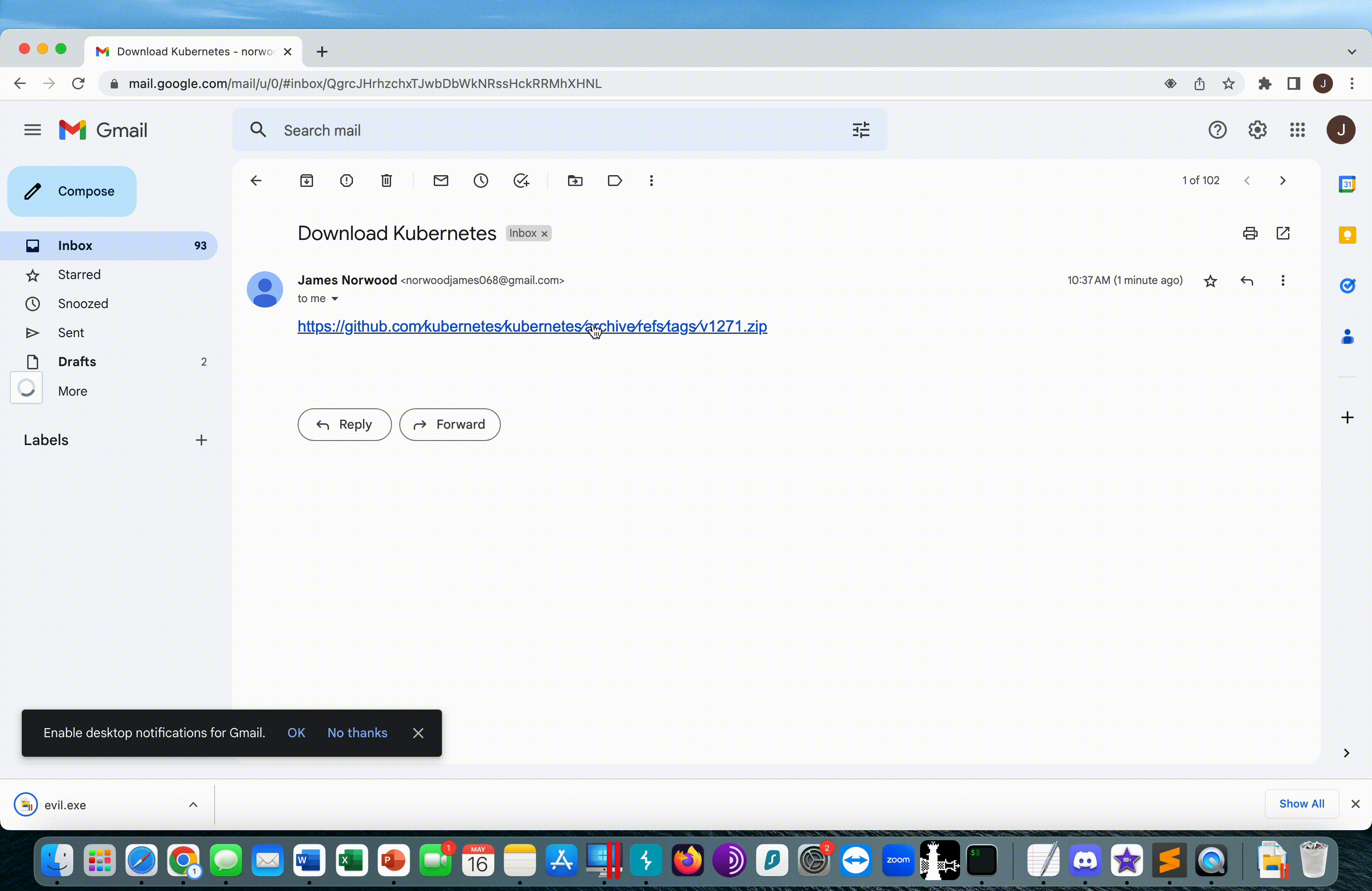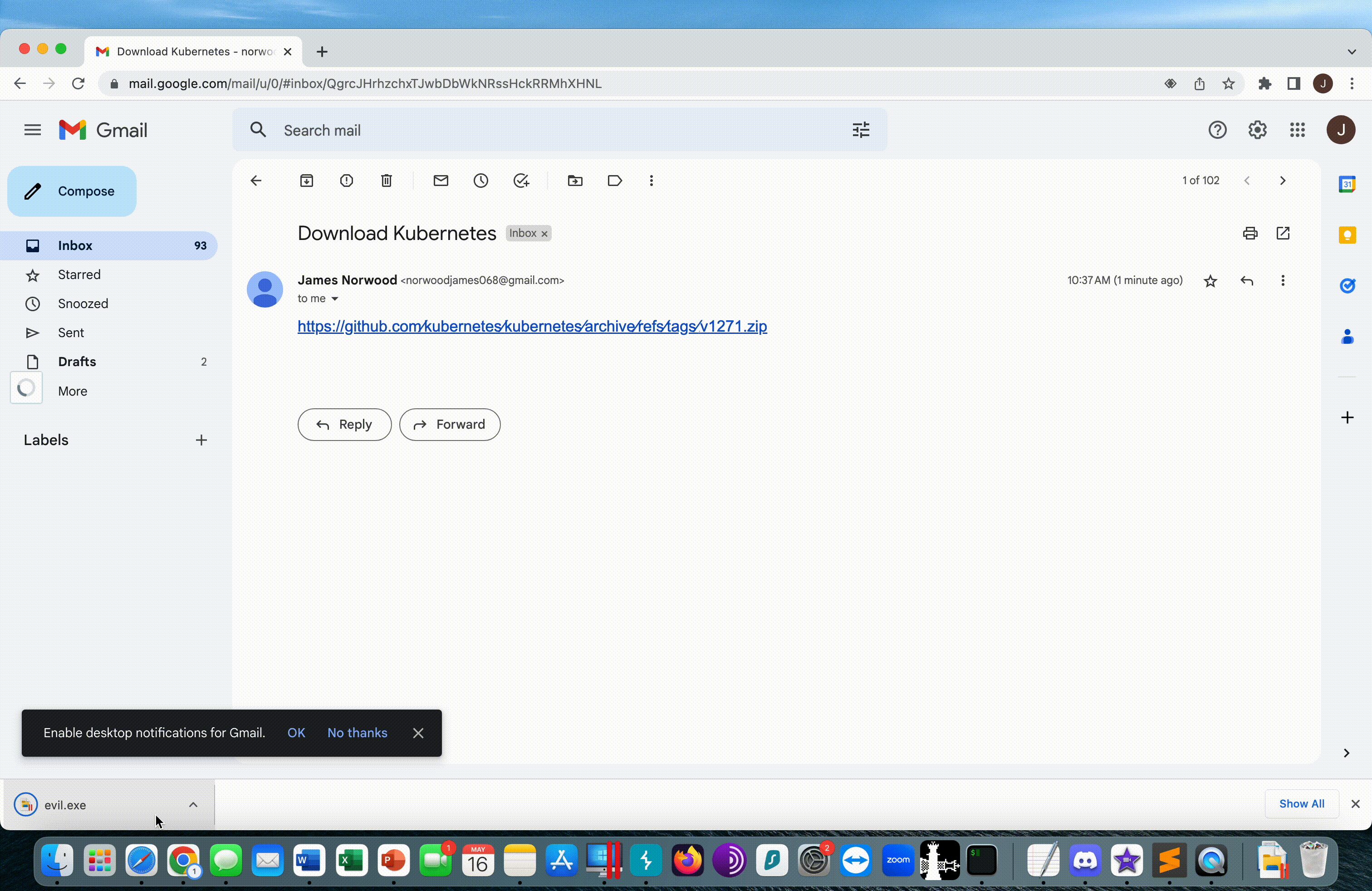
Will you be able to quickly determine which of the URLs below are legitimate and which are malicious phishing URLs that are dropping evil.exe?
https://github.com∕kubernetes∕kubernetes∕archive∕refs∕tags∕@v1271.zip
https://github.com/kubernetes/kubernetes/archive/refs/tags/v1.27.1.zip
This is an example from the popular article on Mediumwhich detailed how an attacker could use this TLD in combination with the @ operator and the Unicode character ∕ (U+2215) to create a very convincing phish.
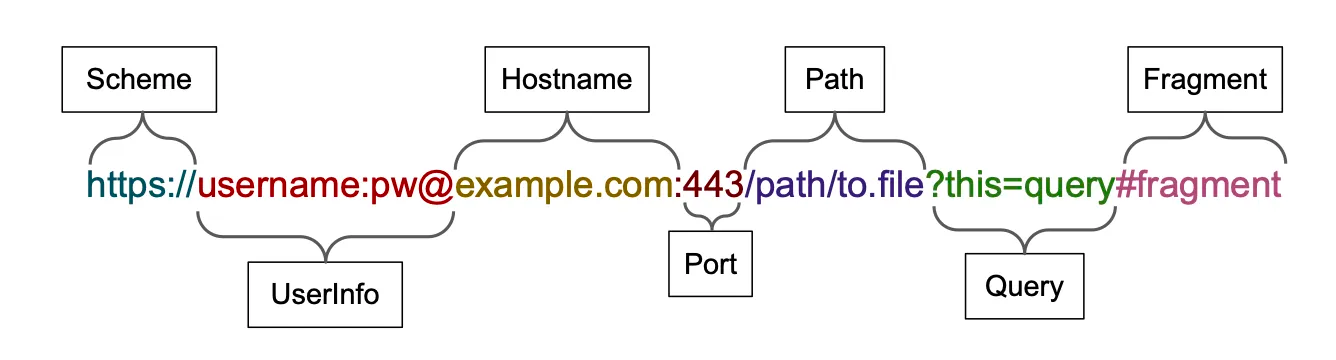
As you can see in the URL breakdown below, anything between the https:// scheme and the @ operator is treated as user information, while anything after the @ operator is immediately treated as a hostname. However, modern browsers like Chrome, Safari, and Edge don’t want users to accidentally authenticate to websites with a single click, so they ignore all the data in the user info section and just direct the user to the hostname part of the URL. For example, URL https://google.com@bing.com will actually redirect the user to the site bing.com.
However, if we start adding a forward slash to the URL that comes before the @ operator, for example https://google.com/search@bing.comour browser will start parsing everything after the slash as a path, and now the URL part bing.com will be ignored and the user will be redirected to google.com.
So let’s say we wanted to create a phishing URL containing a forward slash in front of the @ operator to make it look like the victim is visiting the path of the URL google.combut we wanted it to guide the victim to bing.com.
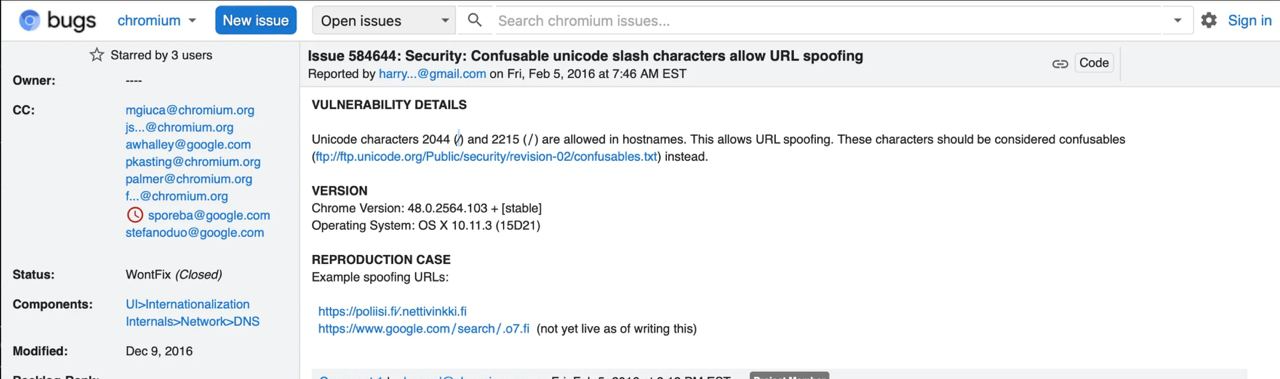
According to this report on Chromium bugs from 2016, Unicode characters U+2044 (⁄) and U+2215 (∕) are allowed in hostnames but are not treated as slashes by the browser. Both of these Unicode characters resemble the legitimate U+002F slash character (/).
If we create a URL like:
it will direct the user to bing.combecause the forward slash U+2215 is treated as part of the user information of the URL, not as the beginning of the path.
If you don’t know what you are looking for, then you can ignore the overly “slanting” slashes. Using this, a very convincing fake of a legitimate .zip file can be created with the new Google .zip TLD.
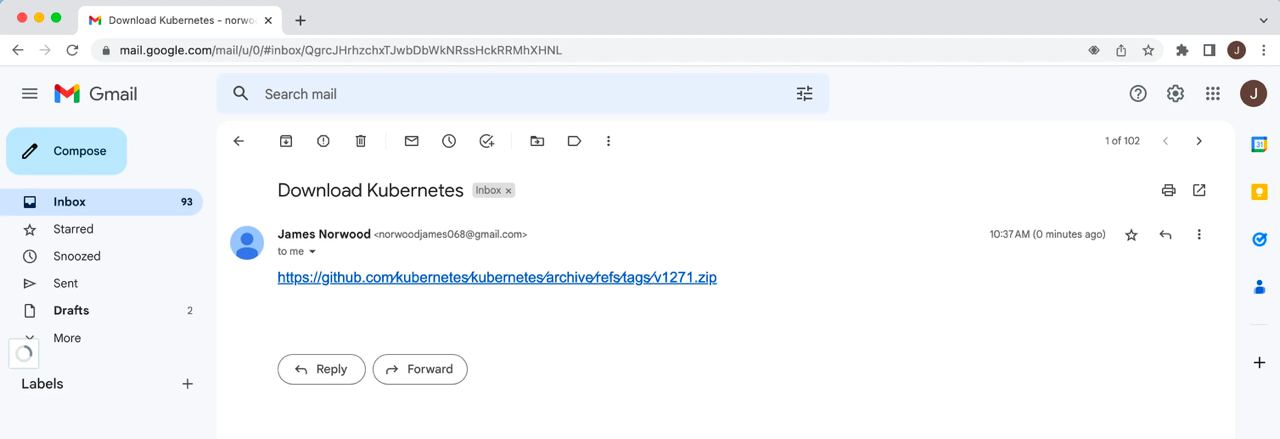
Let’s take the Github code package as an example. If a user wants to download a copy of the Kubernetes open source software, they must visit the Github releases section and download the URL from:
https://github.com/kubernetes/kubernetes/archive/refs/tags/v1.27.1.zip
Take the URL above and replace all slashes after https:// with U+2215 slashes (∕) and add an @ operator before v.1.27.1.zip.
https://github.com∕kubernetes∕kubernetes∕archive∕refs∕tags∕@v1.27.1.zip
Visiting the above URL will take us to the hostname part of the URL, v1.27.1.zip. Unfortunately, the 1.zip domain has already been claimed, but we can claim the similar URL v1271.zip for $15.
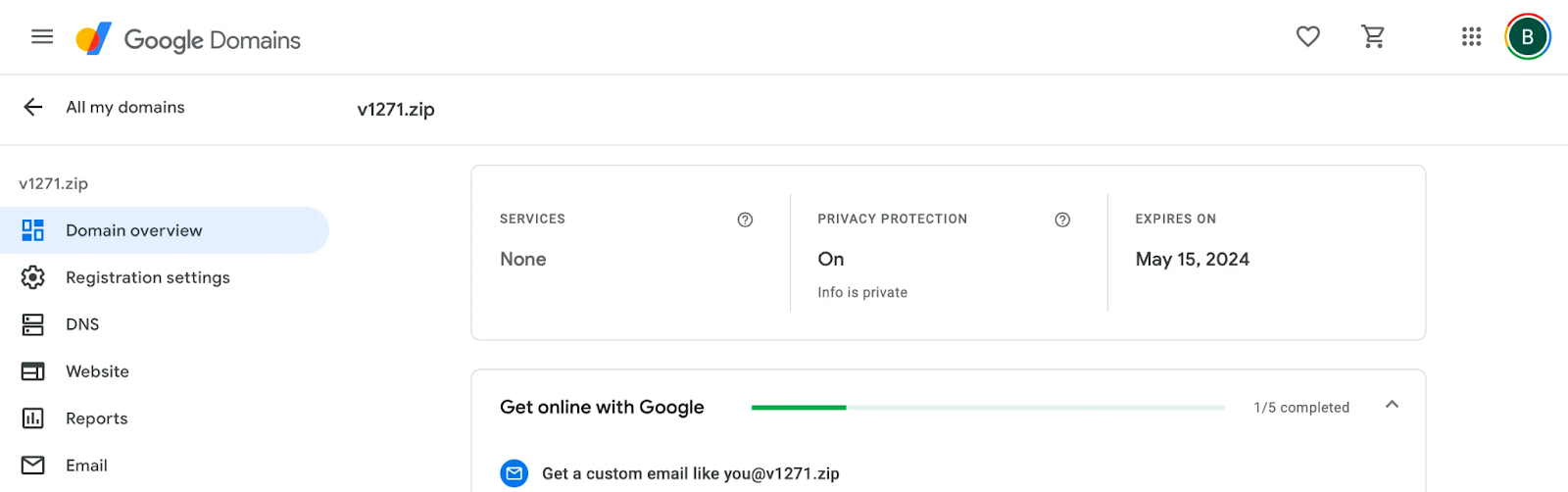
We can deploy EC2 with a simple Python Flask application and point the v1271.zip DNS entry to our EC2. The Flask app will respond to any web request with an evil.exe attachment
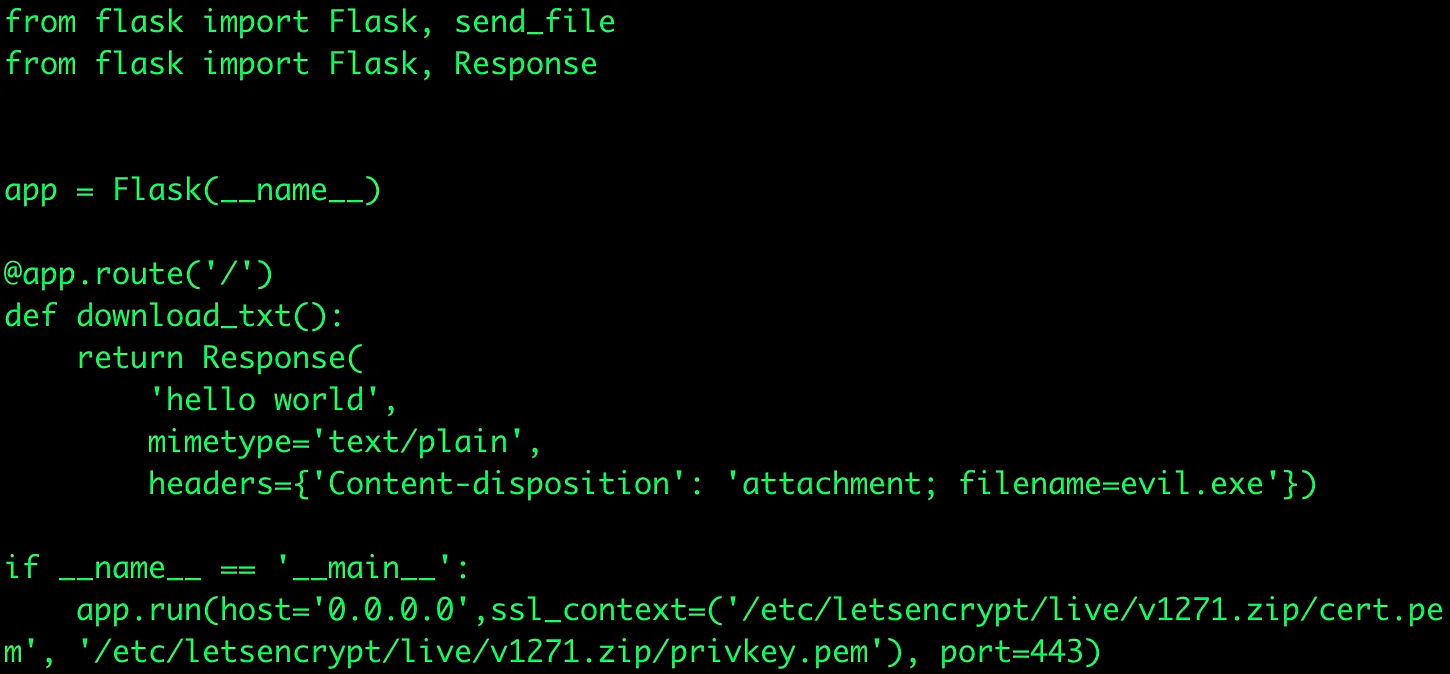
Sample Flask App running on an EC2
Our malicious URL below looks almost indistinguishable from a legitimate URL:
malicious:
https://github.com∕kubernetes∕kubernetes∕archive∕refs∕tags∕@v1271.zip
legitimate:
https://github.com/kubernetes/kubernetes/archive/refs/tags/v1.27.1.zip
Only the oddity of the typeface makes it remarkable to the human eye. In the email client, we could make it even more convincing and change the font size of the @ in address 1, making it effectively invisible to the user, but still present as part of the URL.
Here we see a demonstration of how the user gets the phishing example and evil.exe is immediately downloaded from the v1271.zip server.
On the Kaspersky website tellswhat security researcher mr.d0x found another way to use .zip domain for phishing. The technique he described was called the archiver-in-browser and involves the use of sites that mimic the interface of programs for working with archives.
The user, believing that he is opening a .zip file, gets to the site of the same name and instead of a list of files, he sees, in fact, links. Anything can be hidden behind them – a link to download an executable malware, or a request to enter working credentials to access a document. The mechanism of delivering a malicious link using Windows File Explorer, described by the same author, is also interesting. If the attacker manages to convince the victim to start searching for a non-existent .zip file, then File Explorer will automatically open a site with an imitation of an archiver hosted on the domain of the same name.
Strictly speaking, the possibility of phishing using top-level domains existed before:
one of the oldest domains, .com, is also a legitimate executable file extension in MS-DOS (and older versions of Windows)
the Saint Helena domain (.sh) matches the Unix script extension,
the Montserrat island domain .ms is the same as the Windows executable file extension,
.download domain, available since 2015is used as an extension for unfinished downloads of files from the Internet.
All of them allow you to do similar phishing schemes:
https://github.com∕kubernetes∕kubernetes∕archive∕refs∕tags∕@v1234.download
https://github.com∕microsoft∕office∕archive∕refs∕tags∕@v1234.ms
As well as the ability to simply make links absurdly long, hiding anything in them, a possibility that is only exacerbated in email newsletters.
However, the appearance of the .zip domain still means a new quality to these risks, because it allows web links to pass off as one of the most common file formats known even to the most unsophisticated users. You might as well create .torrent, .exe, .dmg, and .html domains.
No longer a theoretical threat
Found the first phishing sites in the .zip zonethat exploit the theme of Microsoft Office updates.
Detection
Check domains for U+2044 (⁄) and U+2215 (∕) characters. as you can see even in the examples in this article, they are quite striking if you know what you are looking for.
Watch out for domains containing @ operators followed by .zip files.
Always be careful when downloading files from URLs sent by unknown recipients and hover your mouse over the URLs before clicking to see the URL’s extended path.
How to solve this problem globally?
To do this, you need to go back to its origins: all the problems of .zip and .mov domains come down to the fact that someone in 2014 decided that it would be cool to launch new first-level domains from recognizable abbreviations – and no one for the next almost 9 years before them the actual launch did not stop them.
Launching such domains is a good marketing ploy: many will want a creative eye-catching address for their project for the price of a regular domain. For a conditional flight search engine, the ability to launch a site in the .aero zone is an informational occasion, equivalent to updating the site itself, only much cheaper. But now the pursuit of the marketability of such addresses has already entered the territory of digital security threats, where there is no place for entertainment. Not everything has to be bought and sold.
Probably the most reliable and sustainable solution would be to have ICANN separate the .zip and .mov domains and impose strict restrictions on all new “fun” domains, excluding the intersection with existing file formats.
Text: @EgorKotkin
Illustrations: Anton Dmitriev





