vulnerability in Intel, Lenovo and Supermicro server motherboards
Last week, Binarly researchers
about the discovery of a vulnerability in server motherboards from at least three major vendors: Intel, Lenovo and Supermicro. A vulnerability was discovered in the Baseboard Management Controller module, used for remote server management. BMC is designed for managing a fleet of servers, it simplifies operating system installation and other operations, and works even when the server itself is turned off. BMC requires a web server to operate, and a number of controllers use the open source lighthttpd project to do this. A vulnerability in this web server can be exploited to read data from RAM outside the allocated range (out of bounds read).
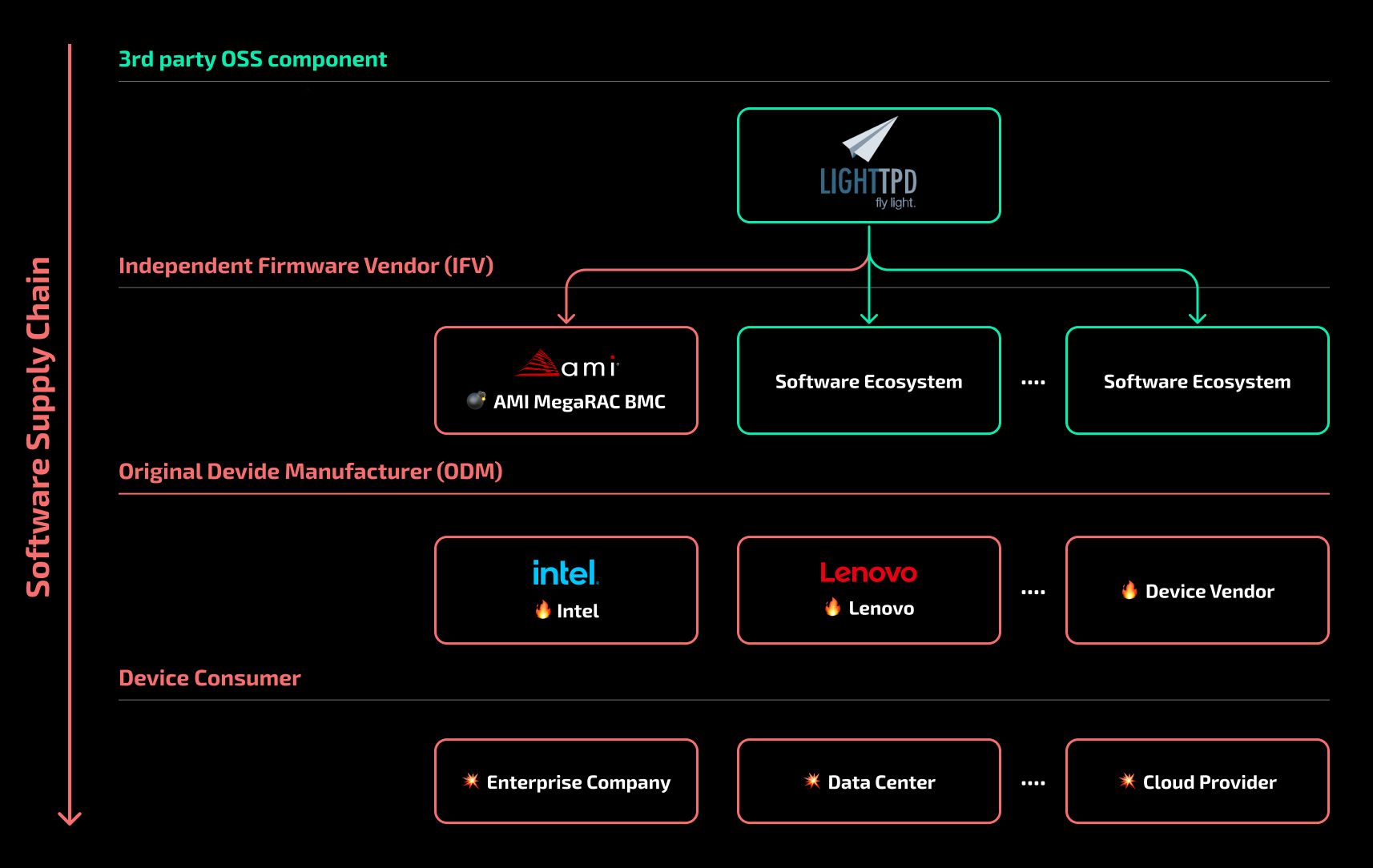
As noted in the Binarly report, this vulnerability reveals a series of shortcomings in the supply chain. The vulnerability was discovered and fixed by lighthttpd developers back in 2018. BMC controller manufacturers, despite this, continued to use the vulnerable version – it was found in a number of controllers from at least two suppliers, AMI and ATEN. The controllers were installed on motherboards, for which firmware updates were released for some time. Accordingly, it was possible to fix the vulnerability for already released devices. But this was not done: the report provides an example of an Intel board, the most recent controller firmware update for which was dated February 2003. The vulnerability in this case has not been patched. And after Binarly reported the problem to motherboard manufacturers, Intel and Lenovo announced that they would not fix the error because the affected devices were no longer supported.
A separate interesting point in this story is how the lighthttpd developers fixed the vulnerability. This was done in August 2018, with a comment that “some use-after-free scenarios have been addressed.” The errors were not classified as vulnerabilities and were not assigned a CVE identifier. Most likely, this led to the fact that the developers of the BMC controllers did not pay attention to the message. To be fair, we note that the Binarly report does not show dangerous scenarios for exploiting the vulnerability. The ability to read sensitive data from RAM is already a problem, but, for example, intercepting server control is only possible if this vulnerability is combined with some other one. There is an opportunity for this: a potential attacker could exploit the vulnerability by sending crafted http requests to the server, ultimately obtaining enough data to bypass the standard ASLR protection system.
In any case, using six-year-old code in a commercial product, in one of its most critical components, is not the best practice. As well as the refusal to update the firmware of “outdated” devices that are widely used by customers. The latter will have to deal with a difficult task: determining the presence of vulnerable servers, which depends both on the version of the motherboard used and on the model of the installed controller. This is not the first problem discovered in BMC controllers. In 2023 the same Binarly found There are a number of critical vulnerabilities in the modules used by Supermicro. That report provides useful statistics. Despite (obvious) recommendations to limit access to the BMC, more than 70 thousand controllers were accessible from the Internet. The important thing about this new problem is that it could have been solved many times over the past six years.
What else happened
Critical vulnerability has been in use in Palo Alto firewalls since mid-March of this year. Patches for different versions of the PAN-OS operating system started releasing from April 14.
Two detailed analyzes of the xz-utils backdoor, which we wrote about earlier, have been published. Kaspersky Lab researchers they tell in detail, how backdoor elements were hidden in the project’s source codes, taken by distribution maintainers. IN report Binarly provides many pieces of malicious code. The most important development in this story was the clarification of the functionality of the backdoor: it provides both bypass of the authentication system and the ability to execute arbitrary code with the highest privileges.
Last week, Microsoft released its next monthly set of patches. Among them were closed two serious vulnerabilities used in real attacks. In total there were corrected 150 bugs, making this the largest patch set since 2017. A set of patches as well released for Adobe products, it, among other things, closes vulnerabilities in the platform for online stores Magento.
US cybersecurity agency warns hacking infrastructure of Sisense, which provides companies with business intelligence services. The danger of this incident is that Sisense clients trust the company with the most sensitive information, which, as a result of hacking, could fall into the hands of attackers.
Ars Technica edition writes about the dangers of global autocorrect. Social network X/Twitter last week tried to replace all links leading to twitter.com. The displayed links changed, and not the “real” ones, to which the user is transferred after clicking, according to the pattern *twitter.com -> *x.com. Which has led to a situation where the link to the netflitwitter.com website appears as netflix.com. This creates ideal conditions for phishing, as has been confirmed by the massive registration of domains ending in twitter.com.
Lastpass, the developer of the password manager of the same name, reported about an attempt to attack his own employee, during which he received calls and voice messages allegedly from the general director. The attackers tried to reproduce the voice of the real CEO of Lastpass using machine learning technologies. This is an interesting development of a fairly common method of attacking a business, which once again reminds you that if your boss calls you and asks you to do something urgently, perhaps you shouldn’t rush.
Researchers from VU Amsterdam showed a new variant of the Specter attack on Intel processors.
Serious vulnerabilities discovered in LG smart TVs running on the WebOS platform. They allow you to bypass the PIN code authentication system and gain full control over the device.





