Shadowsocks FAQ
This article is a collection of various questions and answers to them that were voiced in the comments to my previous articles (Modern technologies for bypassing blocking: V2Ray, XRay, XTLS, Hysteria, Cloak and all, all, all, Bleeding-edge bypassing blocking with complete camouflage: setting up the XRay server and client with XTLS-Reality quickly and easily and others from the same series) and in private messages.

Miscellaneous
I use a proxy, and some services/applications somehow determine that I am using a proxy, how do they do this?
There are not many classic ways to identify proxies/VPNs, the most famous are:
1) the difference between the time zones of the client in the browser and in the location of the IP address from which it connects (for example, in the browser the Moscow time zone, and the server is in London and there is a different time zone) – it’s easy to get around;
2) detection by MTU – unreliable, relevant for OpenVPN/L2TP/Wireguard/SSTP, not relevant for XRay and similar proxies, because they work on a different level;
3) scanning the client’s IP for open standard ports (for example, 443) – can be bypassed with a chain of two servers with a tunnel between them;
If you are using a mobile device, then the banking (or any other application) can see whether the VPN interface is active in the system, or compare the geolocation of the device and the location by IP address. Some particularly stupid Russian services by default believe that “any access from abroad means VPN is enabled.” And some other services (such as Open AI) by default prohibit access from non-residental IP addresses (that is, 99.9% of VPS hosts).
I’m setting up a server with XTLS-Reality, how can I do this as correctly as possible?
The essence of Reality is to disguise itself as some popular site, so when you decide to do this, you need to ensure that your IP (the IP of your VPS) behaves completely identical to the real server that you are pretending to be. If that “real” server is listening on port 80 (plain HTTP), then you also need to configure nginx or a firewall rule to forward HTTP requests to the original server. If the “real” server doesn’t listen for SSH connections on standard port 22, then yours shouldn’t either. If your hoster provides reverse-DNS records for an IP address, make sure that there is no default value left there (usually with the hoster’s domain), but rather set the reverse-DNS that is visible for the IP address of the resource you are masquerading as.
Why is it recommended to avoid visiting the RU zone through a proxy?
According to Yarovaya’s law, we have long been recording all the metadata of Internet activity (where, when, where connections were from, what volumes of data were transferred, etc.). In theory (but judging by how often this advice is found on Chinese sites, this is no longer a theory for them) the following is possible: you accidentally (even just by going to some ordinary site that downloads a script or content from another server) through your proxy you make a request for a conditional Yandex/Mail/VK/Government Services. The metadata logs show: a connection from you to some external IP, and at exactly the same moment a connection from this IP to a service within the country (which, of course, is also controlled), the volumes of data transferred are the same (taking into account the protocol overhead) – and after a number of such coincidences, we can definitely say that a proxy is working at this address.
Or another option: you connect to the service, the service responds by scanning the popular ports of the IP address from which you came, and sees port 443 open there – also very suspicious, it is very likely that it is a proxy, you can ban it. Therefore, there are two options: either make a chain of two proxy servers or one server with two different addresses (it will be much more difficult to compare), or create rules so that traffic from the client to local sites goes directly, and is cut off at the proxy server for reliability.
Well, or the mobile application on your phone (which has access to geolocation or the name of the active cellular network) sees that you seem to be inside the country, but at the same time the connection to their server comes from some foreign address – also a mistake 🙂
Is there any solution with VLESS to create, for example, 3 users, but not let them into the Internet, but give them access to different internal grids on the circuits? It seems that 3X-UI and similar panels do not know how to direct users to different private networks.
3X-UI doesn’t seem to be able to do this, but naked XRay seems to be possible to configure.
Make the Routing settings in the config, and depending on the user ID, if the destination IP matches the address of the network allowed to it, then send it to the corresponding outbounds for this network, and send all other requests to block.
and in outbounds you can set the sendthrough option (https://xtls.github.io/en/config/outbound.html#outboundobject) so that traffic goes through the correct interface.
Are delays of 1100-1800 ms for a Dutch server normal for XTLS-Reality? The speed doesn’t drop.
Yes, OK. Two important differences from other technologies: 1) unlike VPN, where a connection to the VPN server is established once and that’s it, in the case of a proxy, for each outgoing connection from the client software a new connection to the proxy server is established (unless multiplexing) 2) since it is impossible to send an ICMP ping through a proxy, most clients measure the delay not by ping, but by making an HTTP request.
Just consider: when you run a test, a TCP connection with the proxy server is first established (at least one, or even two round trips). Then a TLS handshake (another round-trip) occurs on top of it, and during this process the proxy server also establishes a TCP connection with the reality-dest server and requests a certificate from it. Then the proxy sends a request to establish a TCP connection with the server used for the test. Then, if the URL is specified as HTTPS, another TLS handshake occurs with it. Then the client makes an HTTP request and waits for a response. And only after the answer you see the test result, and the “delay” is the total time of the entire process described above.
Is it possible for XRay/Sing-box itself to wrap connections in a corporate proxy to bypass Internet restrictions in an organization?
XRay and Sing-box can create proxy chains.
In Sing-box, for example, you can set “detour” (a different proxy) for each outbound, and thus reach your VLESS or Shadowsocks server through a corporate HTTP/SOCKS proxy. If you use Nekobox, then you need to create one HTTP or SOCKS connection in Nekobox (for the corporate proxy with its address). Then create another connection separately, VLESS for your server.
And then create a third connection of the Proxy Chain type, and add the first two to it in the required order.
If the corporate proxy is harsh (re-encrypts TLS with certificate substitution), then pure VLESS most likely will not let you through, but the option with websocket transport may well work.
What is port-hopping?
Users in China have reported that when GFW bans connections to their proxy, the restrictions often only apply to the specific port being used. As a workaround in this situation, you can use port hopping, where a proxy server listens on hundreds of ports at once, and you can connect to any – this can be very useful when using Shadowsocks.
You can do this using iptables DNAT:
iptables -t nat -A PREROUTING -i eth0 -p udp --dport 20000:50000 -j DNAT --to-destination :555
ip6tables -t nat -A PREROUTING -i eth0 -p udp --dport 20000:50000 -j DNAT --to-destination :555In this example, the server listens on port 555, but the client can connect to any port in the range 20000–50000.
How can I understand that I am using Shadowsocks-2022, and not the old classic Shadowsocks with vulnerabilities?
In the client and server configuration, you need to use a method that begins with “2022-“, for example 2022-blake3-aes-128-gcm and 2022-blake3-aes-256-gcm (these are standard), or 2022-blake3-chacha20-poly1305, 2022-blake3-chacha12-poly1305, 2022-blake3-chacha8- poly1305 (this is extra).
This is all too complicated, can there be something simpler?
If all this is too difficult, then I advise Amnesia VPNit can be installed on any server with two clicks in a clear interface, there are clients for all platforms, and they are also actively working on protection against detection and blocking.
Well, or move yourself to a jurisdiction where there are no blocking protocols.
Setting up routing and clients
How to set up access to Russian servers and sites directly, without a proxy?
Shadowrocket on iOS
On the main screen, in the Global routing item, select Config:

Next, go to the Config tab, there we go to General:

Scroll down to Skip Proxy and add a new item “*.ru” there:

Save. All is ready.
If you also need GeoIP, then it’s a little more complicated.
Go to MaxMind Geolite2 and register there: https://dev.maxmind.com/geoip/geolite2-free-geolocation-data
How to register and log in – click Manage License Keys -> Create License Key. It will generate a new license – it is important to immediately save the Account ID and License Key, the entire key is shown in the interface only once, then it will no longer be possible to view it again!
In Shadowrocket we go to Settings, there we look for Geolite2, and fill in our data:

Click Update – it should update the current database.
Then, as in the previous point, on the main screen we select Global Routing – Config, go to Config, and there not in General, but in Rules:

Click the plus sign and create a new rule with type geoip, policy = direct, and country/area write “RU” (be sure to use capital letters, otherwise it won’t work):

We save and use.
Nekobox on Windows/Linux/MacOS
GeoIP is activated in the standard way in Nekobox (don’t forget to set sniffing mode to “used for routing!”):

Nekobox doesn’t know how to use suffix rules, but the sing-box at its core can do them, so click “Custom” and enter
like this
{
"rules": [
{
"domain_suffix": [
".ru"
],
"outbound": "direct"
}
]
}
After this, all traffic to .ru domains and Russian IP addresses will go directly.
If you need to block completely, then in the first window, instead of Direct, insert it into Block, and in the JSON code, correct direct into block.
Nekobox Android
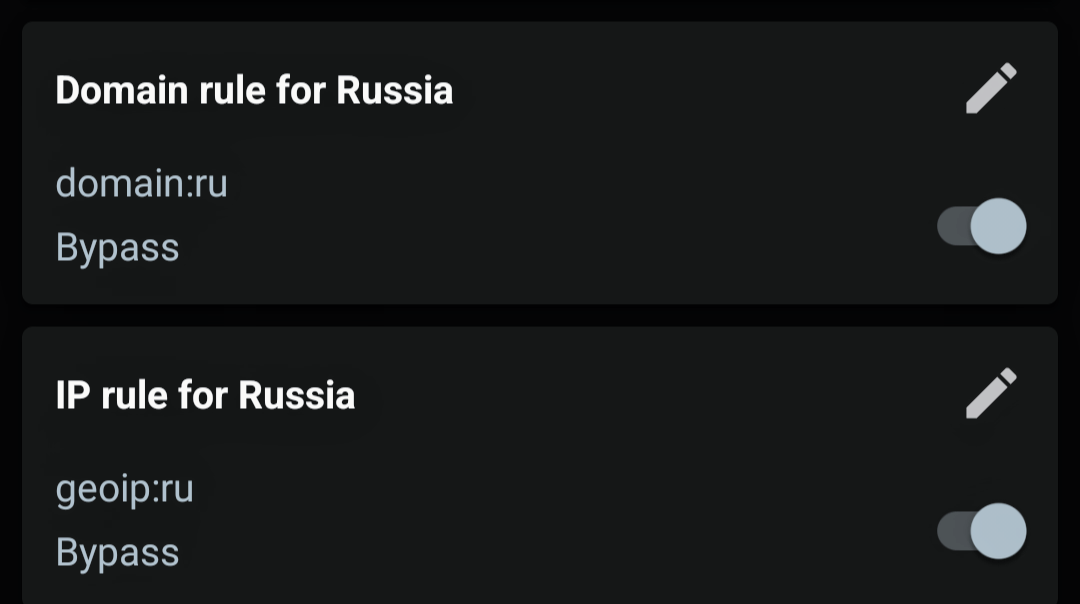
In Nekobox Android, just a couple of rules are enough (separate, not two conditions in one rule!), one for domains, the other for group.
And don’t forget to check that sniffing is enabled in the settings:
Wings X / FoxRay iOS


You can only use category-ru-gov, or vice versa, do not use it, but write down the rules for all .ru domains and Russian IPs as below


v2rayN Android
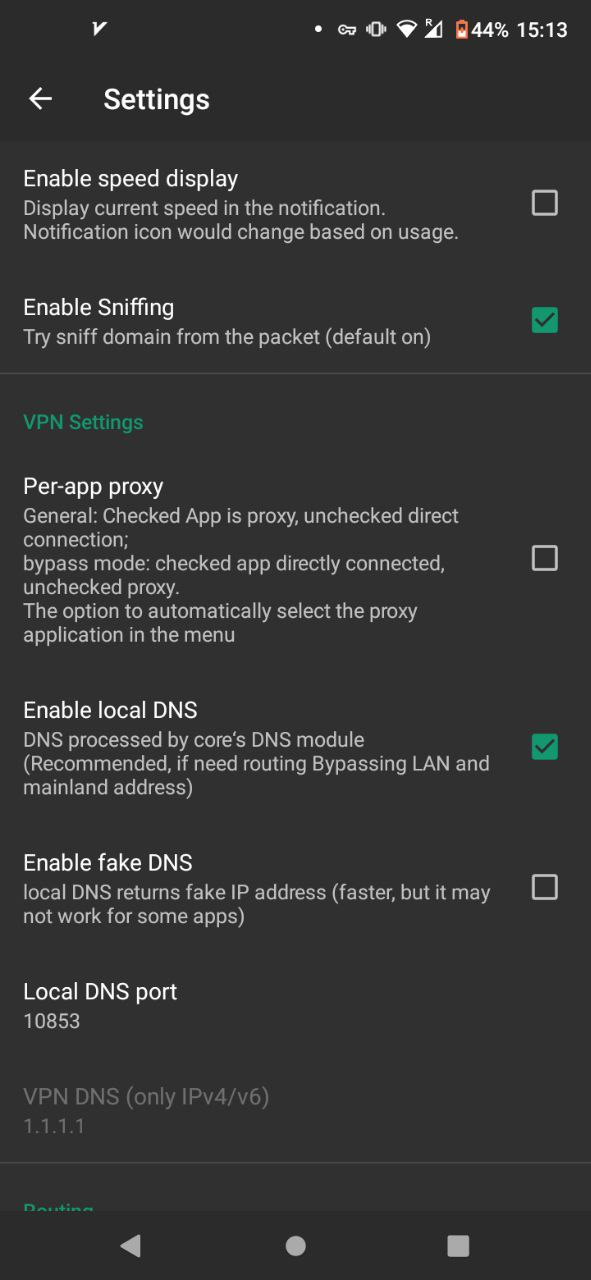
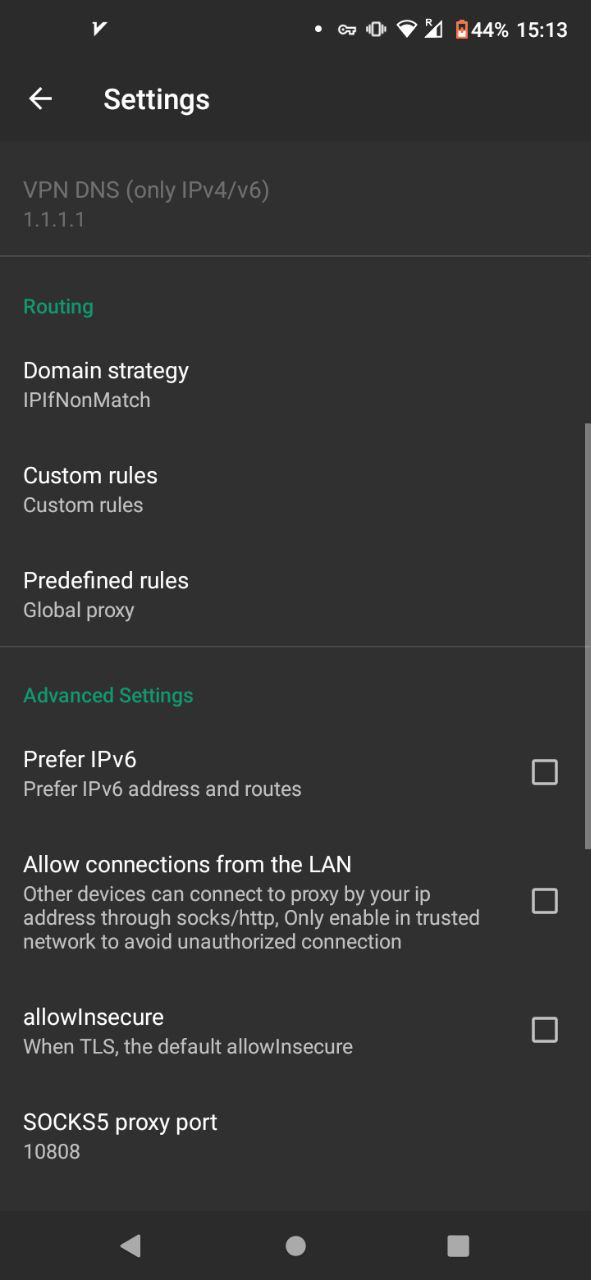
and in Custom rules enter this:
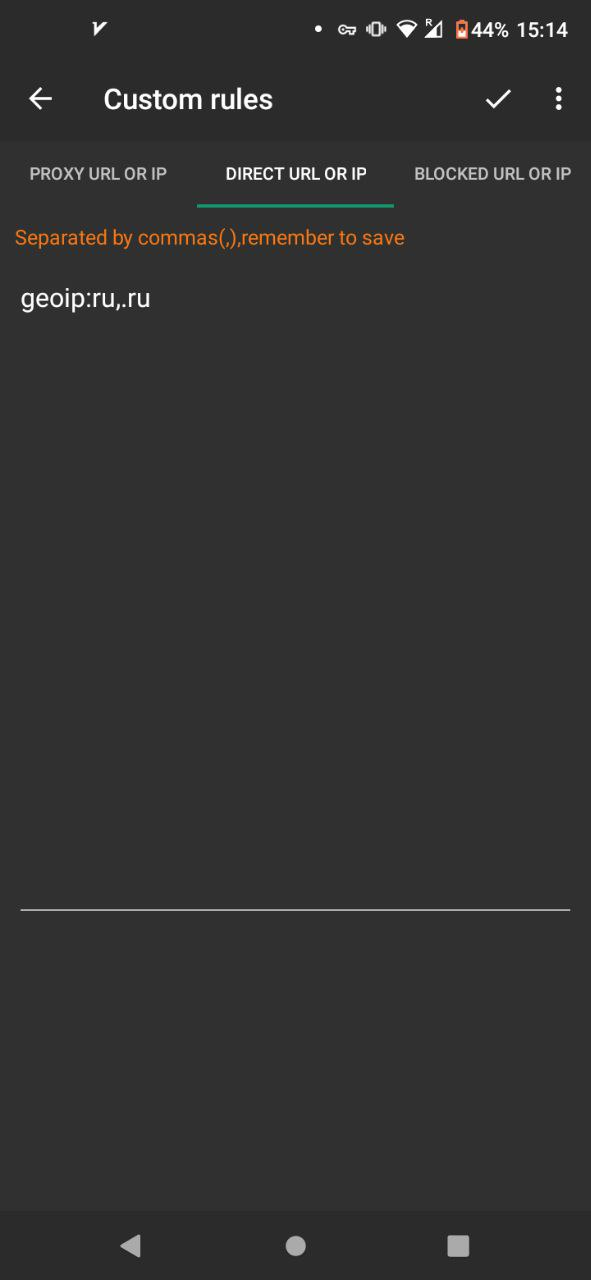
perhaps the domain option may lead to false positives for addresses like www.rust.org, then you can leave only geoip, for most cases this will be enough.
Is it possible to automatically use Anti-Prohibition lists in a proxy client?
It’s possible, yeah. Download geoip.db and geosite.db from here: https://github.com/L11R/antizapret-sing-box-geo
And you slip them into your client. After this, configure routing as usual, for example, select bypass (direct) as the default route, and allow IP addresses by tag through a proxy geoip:antizapret and domains by taggeosites:antizapret
There are also very interesting lists on https://github.com/v2fly/domain-list-community
I encountered a problem that only browser traffic is proxied; terminal traffic, for example, goes past the proxy
This depends on the client’s operating mode.
In system proxy mode, a system parameter is set, but whether to use it or not depends on the application itself – browsers use it, but some programs do not know how to do it and do not want to.
TUN mode stops all system traffic, you can try it, it should help.
I have configured routing rules in the client, but they do not seem to work – the traffic still goes either all directly or all to the proxy, depending on what is specified by default.
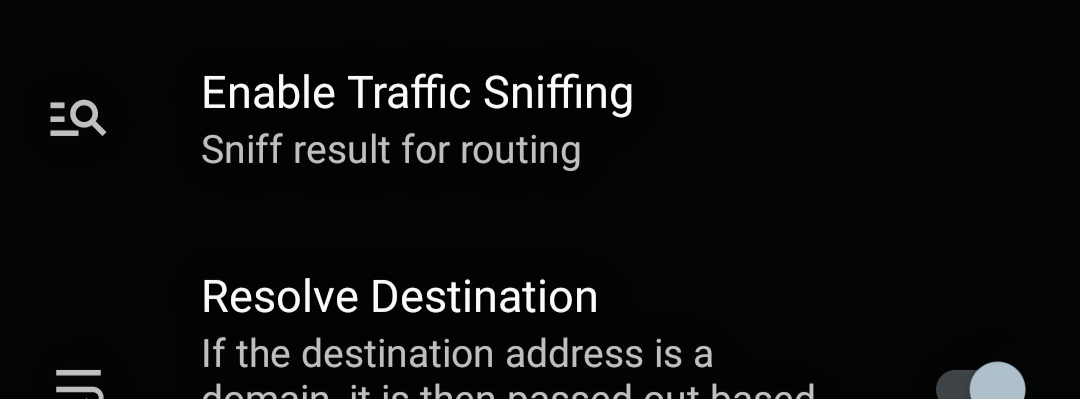
You need to look at the sniffing settings in the client – firstly, it must be enabled, and not AsIs, but something like “Sniff for routing” or “Resolve Destination” (depending on the client):

Everything is enabled, but routing still doesn’t work as it should. The config was written manually.
XRay has specifics, where if the conditions are specified under which a particular route will be used (for example, destination IP from such and such a subnet, inbound such and such, protocol such and such), then it will apply this route only if All the conditions will be met.
Well, the rules are applied from top to bottom, that is, the first rule that completely matches will be used
I don’t use any routing rules, but some sites still determine my real location, not the proxy location!
If TUN mode is used, IPv6 is not enabled in the client (it doesn’t matter on the server), and IPv6 is provided by your provider – there is a possibility that traffic to IPv4 resources will go through a proxy, and to IPv6 resources – directly.
This is not a problem specifically for V2Ray/Xray/SS, it will be for any proxy/VPN working through TUN. Solution: enable IPv6 in the client (even if the server does not support it), or disable IPv6 on the network device (LAN or WiFi).
There are no more Nekoray builds for MacOS on Github 🙁
There are unofficial builds for Mac:
https://github.com/aaaamirabbas/nekoray-macos/releases
Which proxies/VPNs can be installed without administrator rights in Windows?
Most of the console and GUI clients of Shadowsocks/Trojan/VLESS do not require installation (just drop the files into a folder and run) and do not require administrative access. But there is one caveat: you won’t be able to work through the TUN interface (administrator rights are required to install the driver and configure the network), only through a local proxy. Proxy settings in Windows, as far as I remember, can be changed even by an unprivileged user, and even if admins have prohibited this, you can use a browser that is not tied to system settings (for example, Firefox can do this).
Problems, errors, diagnostics
Audio-video calls in messengers and online games do not work with the proxy enabled
Audio and video calls, like most games, typically use UDP data transfer. VLESS/VMess/Shadowsocks support XRay, but they have problems maintaining the port number when implementing NAT, which can cause problems. To solve these problems, the XRay developers came up with XUDP – a special protocol extension that will give you full-fledged Full Cone NAT.
How to make it work:
If you have both a client and a server based on the latest versions of XRay (1.8.3 and later), then everything should work automatically.
If you have a client based on Sing-box (for example, Nekobox), then you must explicitly select XUDP in the “Packet encoding” parameter in the connection settings.
If you have a client based on XRay and a server based on Sing-box, then there is a risk that nothing will work, you need to change the client or server.
The FoxRay client on iPhone crashes periodically, what should I do?
In the FoxRay settings in the Toolbox menu there is an option “reduce memory usage”, which might help.
Why do clients now have all their offers on YouTube? At least reset all settings in your browser, Tehran shows. WTF?
This is the mystery of the black hole, which we have puzzled over for a long time and have never completely solved.
XRay absolutely does not route traffic through any servers either in Iran or anywhere else – it’s not even impossible, but it’s definitely technically meaningless. There is nothing like this in the XRay code.
There was a suspicion that the author of the panel added some kind of gag to XRay – we checked, in the docker image it is assembled from sources from Git, there are no suspicious patches there, and then someone else in the comments to one of the old articles complained about the same thing, not about Iran, but about China 🙂
To be sure, we looked at netstat and wireshark for quite a long time, the verdict is that no left connections are being made.
There was a theory that perhaps somewhere in the code or configs some regional DNS servers were hardcoded (a regional server, resizing the conditional Google and YouTube, could give its addresses to regional mirrors and Google and YouTube would think that you are from there) – again , nothing like that was found in the code and configs.
But there is another theory. Nekobox (maybe other clients too, haven’t checked) uses an address from such a reserved range as an “internal” IPv6 address (ULA), where they must be generated randomly, and the probability of two random addresses matching is negligible. That is, such an address must be unique, but in Nekobox, on the contrary, it is hardcoded one for all cases, and as a result, some services that can somehow receive and analyze local client addresses (for example, Google with its telemetry in Chrome and Android) , consider all clients with such an internal address… to be the same client, and then compare them either with geolocation, or with other internal addresses, or with both, and as a result, in some cases, all users Nekobox (and possibly other clients) to Google look like users from somewhere in Iran, China or Azerbaijan, to the point that over time Google begins to consider the public address of the proxy server also Iranian/Chinese/etc, and this leads to some pretty funny effects.
Solution options: do not use TUN mode (aka VPN mode), or in the routing rules of the client or server, prohibit access to Google via IPv6, or patch the client so that it uses some other internal address.
My FoXray does not read the QR code (Shadowsocks-2022), it writes incorrect settings. At that time, the same QR flies into V2Box with a bang. What could be the problem that I missed?
If you are trying to scan a QR from the X-UI panel, you can first try adding a connection from there via a link to the local Nekoray, and then search the QR from there. Well, check that there are no extra characters in the config name and parameters (Cyrillic, ampersands, questions, dots, extra slashes, etc.)
In the client settings I specified my DNS server to adguard home. As a result, I have checks on sites dnsleaktest.com In addition to my DNS resolvers, Google’s ones also light up from somewhere…
Check what you have in /etc/resolv.conf 🙂
I’m setting up Shadowsocks, when I start the client or server it says “illegal base64 data at input byte 3”
There’s something wrong with the key. You can regenerate it again in the panel (if you are using a panel), or with ‘openssl rand -base64 16’ or ‘openssl rand -base64 32’ (depending on the length of the cipher used).
I’m trying to start the server, when I start it says “Failed to start: app/proxyman/inbound: failed to listen TCP on 443 > transport/internet: failed to listen on address: 0.0.0.0:443 > transport/internet/tcp: failed to listen TCP on 0.0.0.0:443 > listen tcp 0.0.0.0:443: bind: address already in use”
Well, the error speaks for itself: “address already in use” = some other process is already running on the server on port 443. You can see with the command ‘netstat -nlp’ from root, it will show which process is listening on which port.
I do netstat -nlp, and apparently the proxy listens only on IPv6, why?
In Linux, a netstat output like “tcp6 :::2323” usually means that the socket is accessible over both IPv6 and IPv4.
I’m trying to run Nekoray on Windows, but I’m complaining about some errors in the Qt libraries
If you have an old version of Windows, then you need to use older versions of Nekoray – the new ones no longer support Windows 7 (and Windows 8, it seems, too).
The latest version is 3.17, the file is called “nekoray-3.17-2023-08-17-windows7-x64.zip“.
How can I determine exactly why my client is not connecting to the server?
Alas, no way. In 99% of cases when something does not connect, it will be some kind of configuration mismatch between the client and server. The protocol itself is designed to be as undetectable as possible, so if the server doesn’t like something (for example, the user’s key does not match, or something else), then in response it will not send any errors so as not to unmask itself, but will remain silent or break the connection – and all that remains is to guess from the logs.
I did everything according to the instructions, it started on the server without errors, but the proxy did not work. Nekobox says: “No connection could be made because the target machine actively refused it”
Well, actually the client tells it like it is – he cannot connect to the server. Either the process is not running on the server, or the firewall on the server is blocking connections, or the firewall on the client is blocking connections, or something is wrong with the settings.
You can start your investigation with the command “netstat -nlp”, which will show whether your proxy server is really listening for incoming connections, on which IP and on which port.
Plus, check the firewall configuration according to the instructions for your distribution; some distributions/hosters have rules by default that close all ports except those explicitly allowed.
Also make sure that the local antivirus and its firewall are not interfering with you (for example, some complained about problems with Kaspersky on the client machine).
The following errors are visible in the client:

It looks like the system root certificates are rotten due to a very old OS without updates. As an option, try changing the remote DNS in the client from https://8.8.8.8 to just 8.8.8.8 or 1.1.1.1 (without https).
In NekoBox 3.18 on Macos mode
sing-boxTun Mode is not activated
https://github.com/abbasnaqdi/nekoray-macos/issues/36 -> ‘sudo /Applications/nekoray_arm64.app/Contents/MacOS/nekoray’
Subscriptions started working on Android with v2rayNG, but not with FoxRay on iOS
Without an SSL certificate and an https subscription link, nothing will work on iOS.
I have a server with XTLS-Vision or XTLS-Reality, when connecting from a desktop everything works, but not from a mobile device, what could be the problem?
Check your uTLS settings. For some reason, for many clients, when installing uTLS as “android”, the connection fails, but when installing uTLS as “chrome”, everything works. It’s not entirely clear whether this is a bug on the client or server side, but it’s an interesting bug.
I use Shadowsocks/Trojan/VLESS, and somehow the speed is not at all pleasing…
Set up BBR on the server, it will become much more fun:
echo “net.core.default_qdisc=fq” >> /etc/sysctl.conf
echo “net.ipv4.tcp_congestion_control=bbr” >> /etc/sysctl.conf
sysctl -p
or a more complete tuning option
net.core.rmem_max = 67108864
net.core.wmem_max = 67108864
net.core.netdev_max_backlog = 10000
net.core.somaxconn = 4096
net.ipv4.tcp_syncookies = 1
net.ipv4.tcp_tw_reuse = 1
net.ipv4.tcp_fin_timeout = 30
net.ipv4.tcp_keepalive_time = 1200
net.ipv4.tcp_keepalive_probes = 5
net.ipv4.tcp_keepalive_intvl = 30
net.ipv4.tcp_max_syn_backlog = 8192
net.ipv4.tcp_max_tw_buckets = 5000
net.ipv4.tcp_fastopen = 3
net.ipv4.tcp_mem = 25600 51200 102400
net.ipv4.udp_mem = 25600 51200 102400
net.ipv4.tcp_rmem = 4096 87380 67108864
net.ipv4.tcp_wmem = 4096 65536 67108864
net.ipv4.tcp_mtu_probing = 1
net.ipv4.tcp_slow_start_after_idle=0
On some systems the bbr module may not be loaded by default if
# sysctl net.ipv4.tcp_available_congestion_controldoes not show in the bbr list:net.ipv4.tcp_available_congestion_control = reno cubic hybla vegas yeahyou need to add and reboot:
echo “tcp_bbr” > /etc/modules‑load.d/modules.conf
When using SS/VLESS, Google periodically stops working and displays “That’s an error.Your client does not have permission to get URL / from this server. That’s all we know.”
This is a known problem on Google’s part when accessing from some VPS via IPv6. It’s worth trying to disable IPv6 in the client, if enabled (usually in the TUN mode settings, if you use it), and also select PreferIPv4 in the DNS/routing settings if there is such an option. If all else fails, then the last method is if you are using TUN mode, then try the regular proxy mode, and vice versa.
Panels
Forgot your 3X-UI login or password, how can I recover it?
If a telegram bot is connected, you can make a backup of the config and database, open the .db file with notepad and look for possible parts of the password or login combinations.
How to update X-UI? Installed via Docker
A: 1) Go to the cd x-ui folder; 2) Then stop the container: ‘docker-compose down’ 3) Update, ‘docker-compose pull xui’; 4) And run back docker-compose up -d
Ready. At the same time, the settings in the docker file are already stored in a separate volume, so nothing will be erased.





