Security Week 47: Nontrivial Vulnerabilities
Let's start with a relatively simple vulnerability in the Mac OS X operating system that Bob Gendler discovered (news, research). Studying how Siri's voice assistant works on traditional Apple PCs, Bob found a database of his own mail messages in system files.
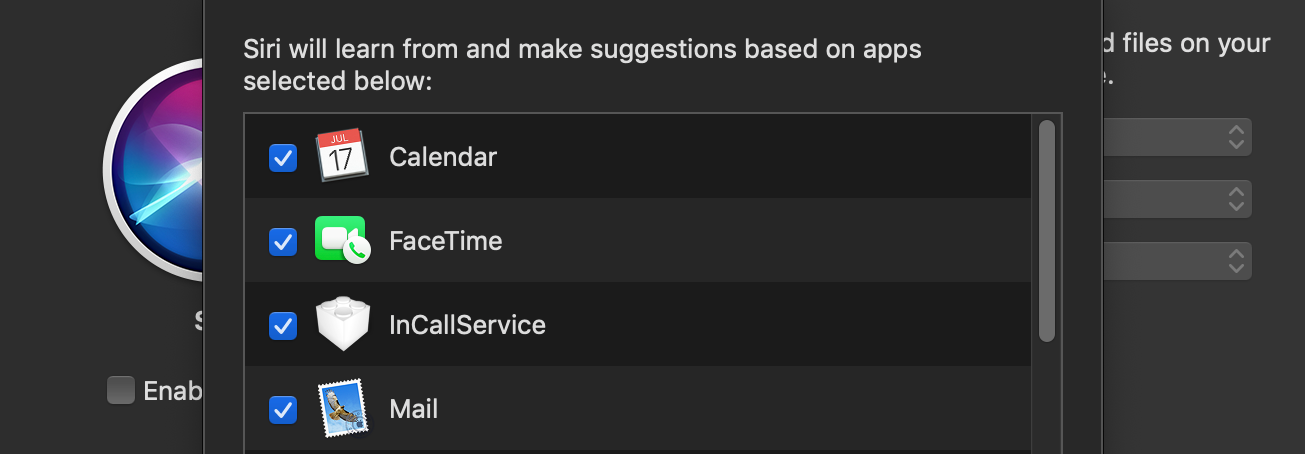
A separate database in the snippets.db file is used by the com.apple.suggestd process. He is responsible for ensuring that not only files and programs appear in the results of a local search (traditional or “Siri, show messages from superiors”), but also appropriate mail messages. In fact, part of the mail database from the Apple Mail program is duplicated there. And this is quite normal, with the exception of one point: Bob encrypts the correspondence, and in snippets.db these same messages are stored in plain text.
The problem exists at least since Mac OS X 10.12 Sierra and is present in the latest version 10.15 Catalina. According to the researcher, he has been chatting about it with Apple for six months now, but the vulnerability is still not closed. Disabling Siri does not affect the replenishment of the mail message database, but you can turn off the collection of information about correspondence in the settings of the voice assistant. Bob gives screenshots showing how deleting a private key makes messages encrypted by him unreadable in the mail client, but text copies remain in the technical database. Such a bug is a classic case of choosing between “convenient” and “safe”. For most users, this behavior is not a problem. But if you paranoid If you want to complicate the life of an attacker, even after gaining access to your computer and data, you will have to refuse hints.
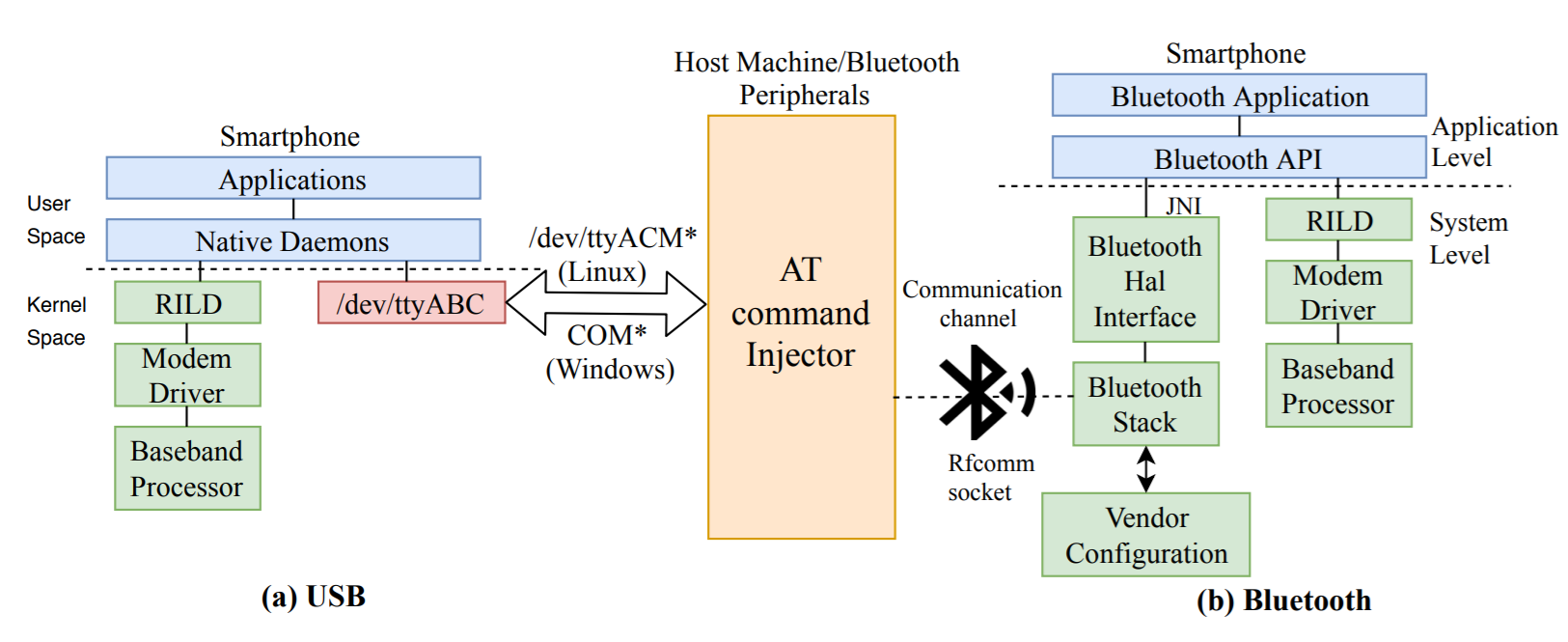
Researchers from two American universities have found a whole warehouse of vulnerabilities in Android phones (news, research), more precisely, in the methods of interaction with the smartphone’s radio module. A radio module is such a state in a state, with its operating system and sophisticated device for communicating with Android itself. The start of the scientific work was laid by two non-trivial ways of interaction between the OS and the module. In a normal situation, only privileged applications communicate with it, although in earlier versions of Android, any program could send commands at all. Over time, the security of the telephone part was improved, but there were two "back doors" available depending on the model of the device and the manufacturer. These are Bluetooth and USB: in the first case, AT-commands for the radio module can be sent by a wireless headset, in the second – from the computer the (not always) possibility of working with the telephone part as with a classical modem is opened.
The authors of the study not only sorted out well-known sets of AT commands, but also wrote a fuzzer, which, using a complex algorithm, sends qualitative nonsense to the radio module. As a result, a wide assortment of potential attack methods came out: from direct control of the phone (call a paid number, see the latest calls) to the theft of IMEI and various ways to suspend the smartphone partially or completely. The scope of the problem is somewhat limited by the need for physical access to the phone: it is necessary to invent a malicious bluetooth headset and connect it to the victim’s device, or at least briefly connect using a cable. In the study, Google Pixel 2, Nexus 6P, Samsung S8 + and some others were used. In the case of S8 +, it was possible to listen to calls and establish a redirection, which is quite serious … if this attack vector can be completed to be more applicable in real life.
What else happened:
Kaspersky Lab investigated popular VNC clients. A review of vulnerabilities (both new and known, with code examples) was made in terms of using VNC to access industrial control systems. Conclusion: there are many vulnerabilities, shining directly on the Internet with such access is clearly not the best idea.
Study of five door bells with video surveillance from AV-Test. The results range from “sufficiently protected” (Amazon Ring) to “poorly protected” (Doorbird). Examples of vulnerabilities: accessibility from the local network without authorization, video transmission to the Internet without encryption, weak authorization in the cloud system.
Vulnerabilities and patches: a very serious hole in the CMS for Magento online stores – installing scripts without authorization. Zero-day in Internet Explorer. Updates to the Adobe Creative Cloud application suite, including those covering critical vulnerabilities in Illustrator and Media Encoder.




