Security solutions for corporate and industrial networks: an overview of Positive Technologies products

Colleagues, good afternoon!
This article is the starting point for a series of articles on products Positive Technologies… The first part will focus on MaxPatrol 8, and today, within the framework of this article, we will talk about the variety of Positive Technologies products and solutions and their joint use.
Positive Technologies has a whole arsenal of solutions for protecting corporate and technological networks. A simplified example of product collaboration is shown in this figure.
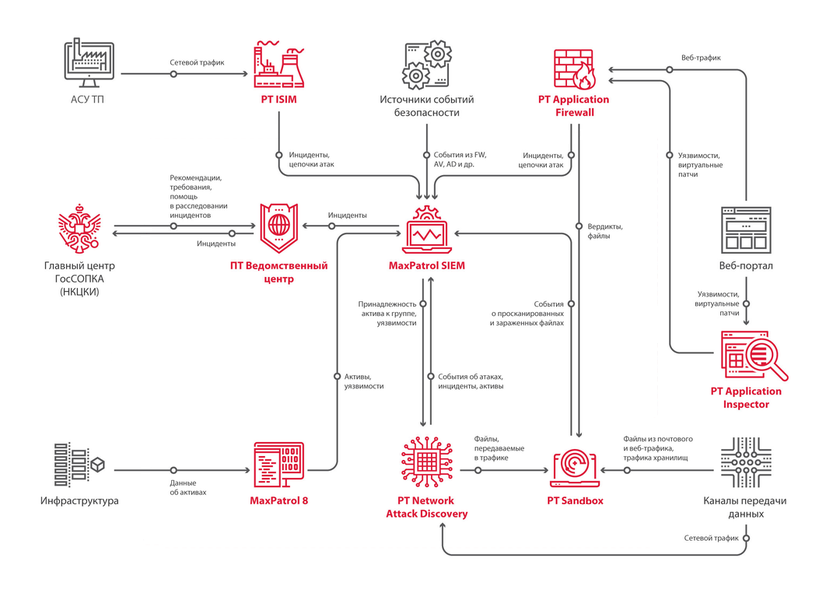
Now let’s talk about each product separately:
MaxPatrol 8 – the security analysis and compliance system can operate in the following modes:
- Pentest – black box infrastructure testing
- Audit – white box check for vulnerabilities
- Compliance – testing for compliance with major standards (ISO, PCI DSS and CIS)
The product can also assess web applications, inventory networks, check network perimeters and issue reports of various types based on scan results. All this is necessary for the timely detection of vulnerabilities and prevention of attacks using them.
MaxPatrol SIEM– a system for identifying information security events. MaxPatrol SIEM provides complete visibility of the IT infrastructure, allows detecting information security incidents in real time and significantly reduces the speed of response to these incidents.
The product supports over 300 data sources for monitoring, including a wide range of Russian software.
Together with MaxPatrol SIEM, companies receive knowledge on detecting modern threats in the form of regularly updated expert packages in the Positive Technologies Knowledge Base (PT KB). PT KB is part of MaxPatrol SIEM.
PT Industrial Security Incident Manager (PT ISIM) Is a system of continuous traffic analysis of industrial networks of enterprises (ACS TP). Provides a search for traces of information security violations in technological networks, helps to identify cyberattacks, malware activity, unauthorized actions of personnel (including malicious ones) at an early stage and ensures compliance with legal requirements (Federal Law “On the Security of Critical Information Infrastructure of the Russian Federation” dated 26.07. 2017 N 187-FZ, orders of FSTEC No. 31, 239, requirements for interaction with GosSOPKA).
The tool works with a copy of traffic and protocols in the ICS segment. Cyberattacks are detected at an early stage through the use of a proprietary Industrial Threat Identifier (PT ISTI) database, as well as a combination of signature attack detection methods and a behavioral analysis engine.
PT Application Firewall – application layer firewall. The system allows you to accurately detect and block attacks on web resources, including threats from the OWASP Top 10 list, WASC, L7 DDoS and zero-day attacks. PT Application Firewall ensures continuous protection of applications, users and infrastructure and helps to meet security standards.
PT Application Firewall can operate in one of three modes:
- Breakaway work – all traffic goes directly through PT Application Firewall. Can be installed using transparent proxy, reverse proxy, and L2 network bridging models
- Monitoring mode – the router turns traffic to the PT Application Firewall, which detects incidents and alerts security systems
- Offline mode – the product examines system logs for traces of attacks, which can be used when investigating incidents
PT Application Inspector – a system for analyzing source code, detecting vulnerabilities and errors in application code. PT Application Inspector can be used both at the stage of application development (in this case, the cost of correcting code errors is reduced tenfold), and in cases when you need to protect an already running application.
The product can automatically upload the analysis results to PT Application Firewall, which applies rules to block attacks on the vulnerable application while the code is being corrected.
The solution combines static, dynamic and interactive methods (SAST, DAST and IAST).
Based on PT analysis
Application Inspector provides data on the line number and type of vulnerability, and also generates safe test exploits necessary to confirm or deny the existence of a vulnerability.
Thanks to the dynamic analysis module, these exploits are launched on any test bench, including in automatic mode, which significantly reduces the labor costs of experts.
PT Network Attack Discovery (PT NAD) Is a traffic analysis system for detecting attacks on the perimeter and within the network. PT NAD knows what is happening on the network, detects malicious activity even in encrypted traffic, and helps with investigations.
The system stores raw traffic and 1200 parameters of network sessions. This helps to identify traces of compromise, confirm an attack, conduct an investigation and collect evidence.
Of the features should be highlighted:
- The tool defines 80 protocols, 30 of them parses up to the L7 level
- Has its own rules for detecting threats on board
- It is possible to filter sessions by 1200 parameters for an accurate search
- Defines techniques and tactics from the MITER ATT & CK model
- Stores attack data within the company
- Reveals attacks and their consequences even in encrypted traffic
- Integration with SIEM systems
PT Sandbox – sandbox with the ability to customize virtual environments. Provides comprehensive file scanning, which includes static and dynamic analysis. Static analysis is carried out using the unique rules of the expert center PT Expert Security Center (PT ESC) and several antiviruses. Dynamic analysis, which also uses PT ESC rules to search for threats, provides for a full-fledged file launch in a virtual environment and the study of all its actions, generated artifacts, and network activity.
Key features worth noting:
- The ability to flexibly configure virtual environments. PT Sandbox allows you to load specific software and its versions that are used in a company into a virtual environment. This allows you to identify targeted attacks on specific software and 0-day vulnerabilities
- Detection of malicious network activity. The product detects threats in traffic generated during file analysis (including encrypted ones). This helps you see dangerous network activity that is not externally associated with a specific file
- Revealing new threats and the hidden presence of malware through retrospective analysis. Automatic recheck starts after updating the knowledge bases of anti-virus engines. This ensures prompt detection of the latest threats that were not yet detected at the time the file was scanned.
- Knowledge in the product that is relevant for Russia. PT ESC rules for file analysis are created by experts who constantly investigate the activities of hacker groups and investigate incidents in large companies.
Let’s consider several cases of interaction between Positive Technologies products within the same customer security system to ensure countermeasures against modern threats.
Case 1: PT NAD + PT Sandbox + MaxPatrol SIEM
Suppose PT Sandbox finds malware on file storage and reports the incident to MaxPatrol SIEM. You, as an administrator, only observe incidents in SIEM, as it consolidates data from all security systems into itself. You see this incident in SIEM, look through the logs of the objects of this incident there and find that the malware got there from one of the users’ workstations. Next, you view the traffic of this workstation on the network using PT NAD. When analyzing traffic, you find that the AWP was sending malware not only to file storage, but also to several other assets. You go back to SIEM and review the logs for new assets involved in the incident and take the necessary action.
Case 2: PT Application Firewall + PT Application Inspector + MaxPatrol SIEM
Let’s assume you already have a web application in use. To analyze the security of its code, you use PT Application Inspector, which detects errors and vulnerabilities in it. The application is operational, it is not possible to stop its operation at the moment, therefore PT Application Inspector automatically uploads the analysis results to PT Application Firewall, which in turn applies rules to block attacks on the vulnerable application until the time when the application code becomes possible. You observe the progress of the process itself through MaxPatrol SIEM.
Case 3: MaxPatrol 8+ MaxPatrol SIEM
Suppose that in the MaxPatrol SIEM interface you see hosts with a wide variety of software and vulnerabilities. To fix the situation, you build a process for identifying and eliminating vulnerabilities on MaxPatrol 8. Thanks to this process, over time, the configuration of the hosts is corrected, the software is updated and the vulnerabilities become much less. In SIEM, you see a decrease in the number of vulnerable hosts, critical assets and non-updated software.
Subsequent articles will be of a technical plan and primarily devoted to a detailed acquaintance with the product. MaxPatrol 8… In this series of articles, we will tell you how to get started with the product and analyze its features.
If this topic is interesting to you, then stay tuned in our channels (Telegram, Facebook, VK, TS Solution Blog)!