Providing network security in conjunction with network packet brokers. Part one. Passive safety devices

With the rise of cloud computing and virtualization, today’s computer networks are becoming more vulnerable and constantly evolving, bringing with them new risks and uncertainties. Long gone are the days of fun hacking, hackers are financially motivated and more sophisticated than ever. Some have formed hacker groups such as LulzSec and Anonymous to share experiences and work together. Information security professionals struggle to keep up by trying to use passive (to detect) and active (to block) network security tools. While vendors develop and provide network security tools in a timely manner to protect against the latest cyber threats, the implementation of these tools is an ongoing challenge for various reasons. In this series of publications, we will describe the most basic network security tools that combat cyber threats, discuss common deployment problems and how to solve them with network packet brokers.
Passive safety devices
Passive network security tools are used to monitor and analyze network traffic. These tools work with a copy of traffic received from SPAN ports, network traffic taps (TAPs), or network packet brokers (NPBs). Passive monitoring does not introduce time delays and additional service information into the network. Passive security features such as IDS, Network Forensics, NBA and NTA are widely used today.

Intrusion detection system (IDS)
The Intrusion Detection System (IDS) is designed to monitor network traffic for malware, exploits and other cyber threats by using a large number of threat signatures (sometimes called rules). IDS software can be deployed on purpose-built appliances, user-supplied hardware, and in some cases as virtual appliances for VMware, Xen, and other virtualization platforms.
Currently, in the vast majority of cases, IDS is the mode of operation of the Intrusion Prevention System (IPS) tools. In other words, today it will be quite problematic to acquire a solution that can only perform passive monitoring. IPS are more complex and expensive devices, however, as a rule, they support active IPS and passive IDS configurations in one solution. In addition, companies usually deploy IPS only for passive IDS monitoring, especially in the core of the network.
In the space of IDS solutions (as a configuration of passive monitoring of the IPS system) products of Positive Technologies, Security Code, Infotex, Smart-Soft, Info Watch, Stonesoft, Trend Micro, Fortinet, Cisco, HP, IBM, Juniper, McAfee, Sourcefire, Stonesoft are presented , Trend Micro, Check Point.
Network Forensics
Network forensics (forensics) refers to technology that monitors, records and analyzes the traffic of a computer network in order to collect information, legal evidence, and detect and analyze threats to internal corporate network security. This technology is often described as a network video recorder that records (literally) all the packets passing through your network. Network forensics software is most often deployed on vendor-supplied network devices with large amounts of memory, but some vendors provide it as a software solution only so that customers can choose the hardware to support it.
Solution manufacturers in this space are MicroOLAP, Garda Technologies, AccessData, NIKSUN, RSA (NetWitness), Solera Networks.
Network Behavior Analysis (NBA) and Network Traffic Analysis (NTA)
Most network security devices are placed around the perimeter (behind the firewall) to check for threats coming from the Internet. However, mobile devices that are brought into the office every day “in your pocket” may contain malware that perimeter security may never see.
Network Behavior Analysis (NBA) systems detect threats that the network faces from the inside using NetFlow and other flow standards (cFlow, sFlow, jFlow, and IPFIX) to provide a baseline for normal network traffic and detect anomalies such as distribution of malware. Network Traffic Analysis (NTA) systems are designed to intercept and analyze traffic, as well as to detect complex and targeted attacks. With their help, you can conduct a retrospective study of network events, detect and investigate the actions of intruders, and respond to incidents. NTAs can be an excellent data source for Situation Centers (SOCs).
Manufacturers in the space of NBA and NTA solutions – Positive Technologies, Kaspersky, Group-IB, Garda Technologies, Arbor Networks, Lancope, Riverbed Awake, Cisco, Darktrace, ExtraHop Networks, LogRhythm, Flowmon, RSA, TDS and others.
Typical Network Security Deployment Problems
IT companies face many challenges when deploying firewall tools, especially over large, complex and geographically dispersed networks. Sounds familiar? Below are the cases in which common problems of monitoring and information security systems are solved by implementing a network packet broker (NPB).
Case No. 1. Optimization of information security network infrastructure
The modern approach to building information security systems is focused on reliable and cost-effective solutions that allow already implemented security tools to track more network segments, increasing its visibility. At the same time, the newly implemented security means must have access to the existing points of traffic pickup.
The methods used to mirror traffic using SPAN ports or network traffic taps (TAPs) have their limitations and drawbacks. The traffic of SPAN ports has a low priority and, when the load on the switch increases, it starts to be lost, and when the priority is set, “combat” traffic begins to be lost, which leads to more dangerous consequences. Using TAP allows you to have a 100% copy of the traffic, but there is a limit to the number of possible TAP installation points on the network infrastructure. With an increase in the fleet of information security tools, each of which needs to be supplied with traffic from the same network segments, the issue of their implementation into the existing infrastructure arises.
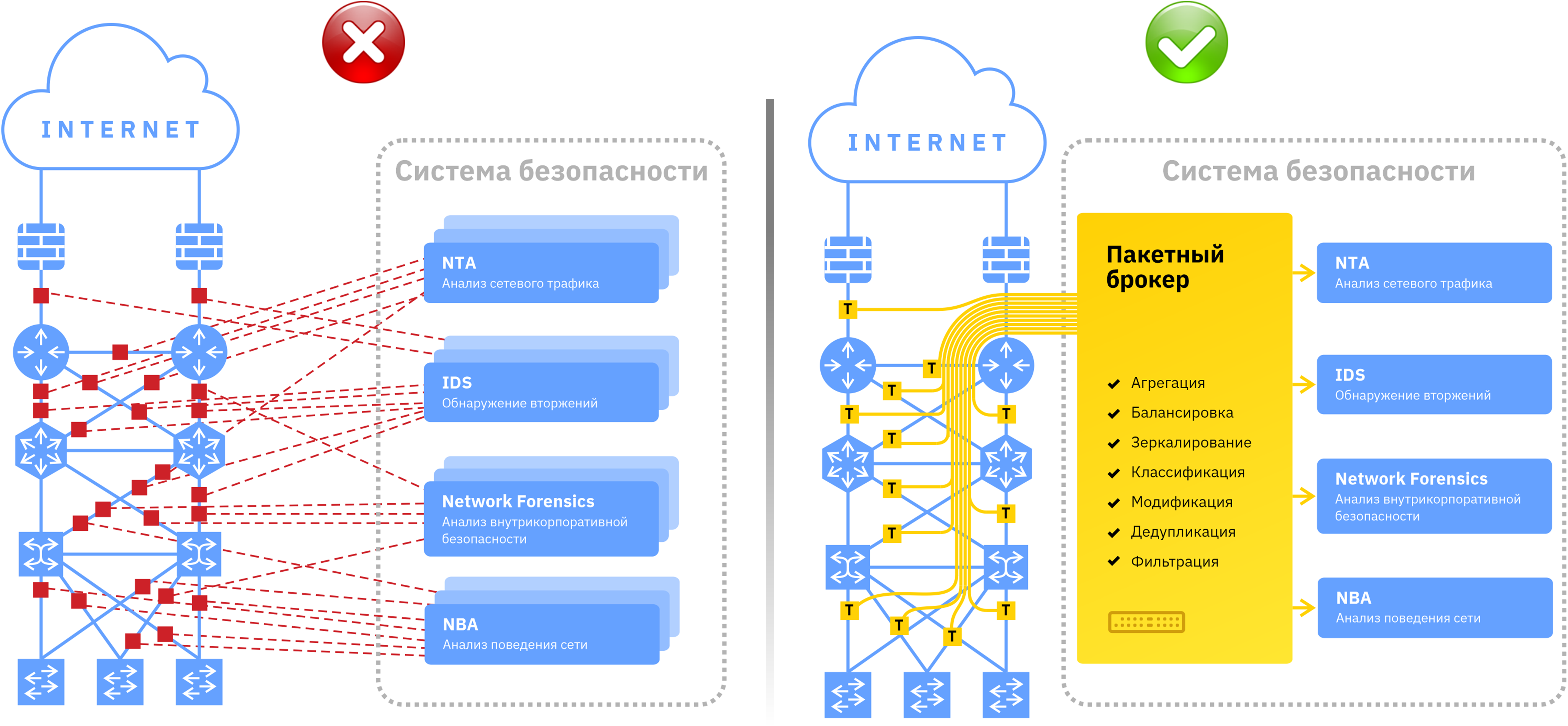
Task: A company with intrusion detection systems (IDS) and network behavior analysis (NBA) deployed Network Forensics and NTA. To get the maximum visibility of traffic, capturing is done not through SPAN ports, but through TAP. Traffic from the TAP of the corresponding network segments must be delivered and distributed between four types of information security systems.
Decision: This task is easily solved by a network packet broker, using which you can aggregate traffic received via TAP from network segments, optimize (apply filtering, classification, deduplication, modification functions) and mirror it, balancing it on the appropriate information security systems.
Case No. 2. Optimizing the use of information security tools
Standard network security devices come with a fixed number of interfaces to monitor multiple network segments simultaneously. However, after these interfaces are fully populated, companies are forced to buy additional units of security products.
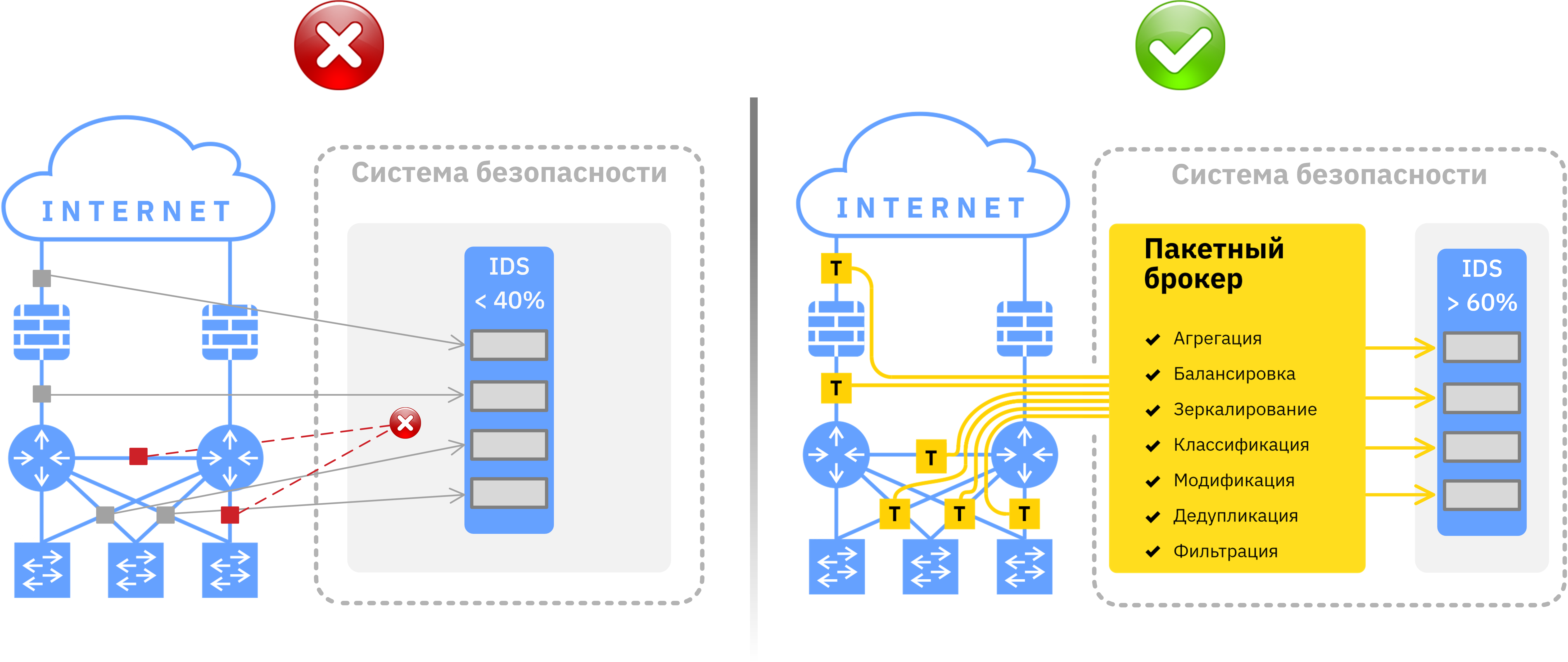
Task: The company has an intrusion detection system (IDS) with four 10GbE interfaces. Traffic for monitoring is removed from four network segments, while the peak load on IDS is no more than 40%. Over time, the network infrastructure has grown and it became necessary to additionally monitor two new segments.
Decision: With the expectation of further development of the network and refusal to purchase additional IDS in view of 40% load of the existing system, it is more rational to solve this problem using a network packet broker. In this case, the use of a batch broker is also dictated by the reduction of problems associated with resolving issues of allocating space in the rack, providing power and air conditioning. Network packet brokers can aggregate traffic from multiple network segments, and then optimize (filtering, classifying, mirroring, balancing, deduplicating, modifying) this traffic before routing it to IDS. Network packet brokers tend to be cheaper than security tools, allowing companies to use money and material resources wisely while improving the resiliency and performance of the tools.
Case No. 3. Using 1G security tools in modern networks
The 10 Gigabit Ethernet (10GbE or 10G) computer networking standard was first published in 2002, but reached critical mass by 2007. Since then, 10G has become the backbone for large computing network infrastructures and backbones. Already, 40G / 100G standards are widely spread, and 200G / 400G standards will come in the near future.
Almost every major computer network has dozens, if not hundreds, of 1G fiber security monitoring tools. These devices, depending on the model, may be able to check more than 1 Gbps of traffic, but tools equipped with 1G interfaces cannot physically connect to 10G / 40G / 100G networks.

Task: The company is modernizing its network infrastructure to increase the channel capacity by introducing new network equipment and communication lines. 10G / 40G / 100G interfaces are replacing 1G interfaces. The existing information security system consists of facilities with 1G interfaces. It is necessary to ensure the functioning of the existing information security system on the new infrastructure.
Decision: Network packet brokers address this challenge by aggregating, load balancing, and traffic optimization (minimization of non-targeted traffic and deduplication) from 10G / 40G / 100G networks to existing 1G security tools. This solution not only extends the life of existing 1G tools (which postpones the cost of replacing them), but also maximizes their performance and resiliency.
Thus, the use of network packet brokers solves the following tasks:
-
increasing the number of control / monitoring points;
-
the ability to connect the required number of traffic control / monitoring tools;
-
optimization of the use of information security tools;
-
elimination of the influence of information security tools on network fault tolerance;
-
ensuring the compatibility of interfaces in the information security infrastructure;
-
increasing network visibility for information security facilities.
The above cases clearly show how easy it is to solve the problems that are so often encountered in building information security systems, the delivery mechanisms and increase the visibility of traffic are brought to a new level, the performance and fault tolerance of the entire system as a whole are increased when using network packet brokers. In the next part, we will talk about active means of ensuring network security, as well as analyze typical cases for their integration into the company’s network infrastructure.