new method of eavesdropping on keyboard typing
Last week, researchers from three UK universities published
, in which they proposed an updated technique for “eavesdropping on keyboards” – recognizing typed characters by the sound of pressing the keys. The authors of the article refer to successful experiments with such acoustic keyloggers carried out in the 1950s and other similar works. The achievement of the new study was the extremely high accuracy of determining the keys pressed, as well as an automated method of analysis using neural networks.
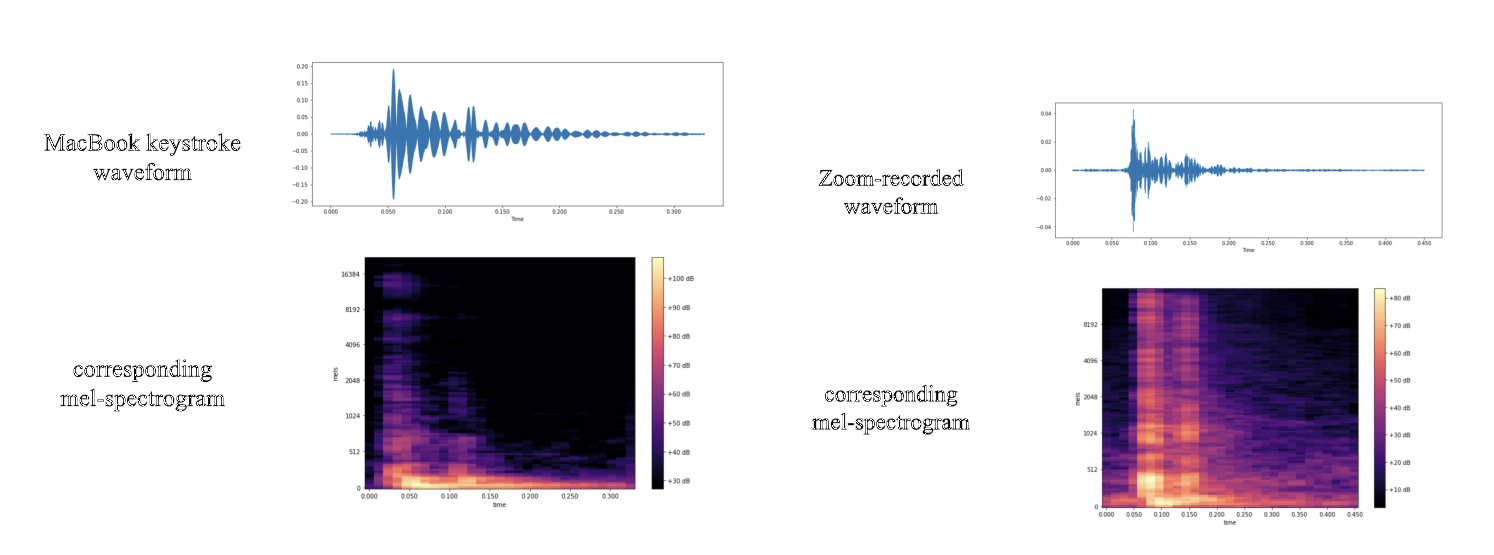
An interesting technical point of the article is the fact that neural networks were trained to analyze images. Since the work explores the sound of keystrokes, this is rather unusual. It turned out that this approach provides a higher recognition accuracy. The images were a modified spectrogram of sound samples as shown in the illustration above. In all experiments, text and numbers (without punctuation marks and special characters) were typed on the keyboard of an Apple Macbook Pro 16 2021 laptop. Two scenarios of “eavesdropping” were studied – direct recording of sound on a smartphone located next to the laptop and remote listening to clicks via the Zoom teleconferencing service.
The authors of the work take credit for the use of a fairly modern laptop, since in theory the recognition of keystrokes on such a device is more difficult than on a desktop keyboard. The sound is quieter, the key travel is small, which somewhat worsens the quality of the collected data. A separate difficulty was recording using Zoom: in this service, keystrokes are forcibly muffled. The researchers made their job a little easier by setting the conferencing client to “minimum muting” of the keypad, but this feature cannot be turned off completely. The results are as follows: when directly recording sound on a smartphone next to a laptop, the detection accuracy was 95%. Through Zoom, the correct sequence of characters typed was determined in 93% of cases.
It makes sense to compare these results with previous work on this richly studied topic. The authors refer to two works: 2017 And 2021 years. Earlier work investigated eavesdropping via Skype, with an accuracy of 91.7%. In the work of 2021, keystrokes were identified correctly in 91.2% of cases. This indicates some progress.
The authors devoted a large section of the study to methods of protection against such listening. Breaking a neatly built recognition scheme is really easy. Firstly, the neural network was trained for a specific user typing in the usual rhythm on a specific keyboard. Even a simple change in the typing speed significantly reduces the accuracy of the typed text. Obviously, the main purpose of this technology is to intercept passwords. Complex passwords that use special characters or even uppercase and lowercase letters are much more difficult to recognize – pressing two keys at the same time (for example, Shift + symbol) has not been studied at all. Although here, too, the authors note the possibility of improving the recognition technique: all erroneously defined characters were 1–2 keys from the one that was actually pressed. This gives a chance to develop an error correction system.
Finally, you can make life difficult for the listeners by adding noise to the recording, for example by turning on music. Or just speak while typing the password. Two-factor authentication appears in a new light, which in principle reduces the risk of password leakage. A simpler conclusion suggests itself: you should not type passwords during a conference call.
What else happened:
A recent publication from Kaspersky Lab experts analyzes new opportunities for malicious software distributed on the black market for money.
Big Cyber Threat Trends Report published Google Cloud team. In more than half of the incidents analyzed, weak passwords were the root cause of the breach. Only in 7.1% of cases was the data leak for accessing the service to blame. Of particular interest is the analysis of the methods of “dragging” malicious code into applications available in the Google Play online store. In most cases, the malicious element is delivered from a third-party server after a successful initial audit.
Canon warned owners of home and office printers about the need to double reset the settings before selling or transferring the device for service. As it turned out, simple initialization of the printer does not delete the saved data about wireless access points. You need to reset it to factory settings, turn on Wi-Fi and reset it again.
The BlackHat conference is taking place this week in the US. Among the announced studies are jailbreak multimedia system in Tesla cars. By modifying the bootloader, developers from Germany were able to gain root access to the system and copy the keys used for authorization on the manufacturer’s servers. In theory, this method allows you to modify the functionality of the multimedia system and bypass regional restrictions.