how we found key wolf ransomware ideas

A new threat has been detected: the Key Wolf group is distributing malware among Russian users that starts file encryption. It is worth noting that the attackers are not doing this for ransom. Our experts were the first to detect the spread of malware. We tell you how it works and what to do
As part of the cyber incident, two types of malicious files were used. They had names Информирование зарегистрированных.exe And Информирование зарегистрированных.hta and presumably distributed via email.
In the first case, the file is a self-extracting archive that contains two files − gUBmQx.exe And LICENSE.
In the second case, the file gUBmQx.exe downloaded from a Zippyshare file sharing service using BITS (Background Intelligent Transfer Service).
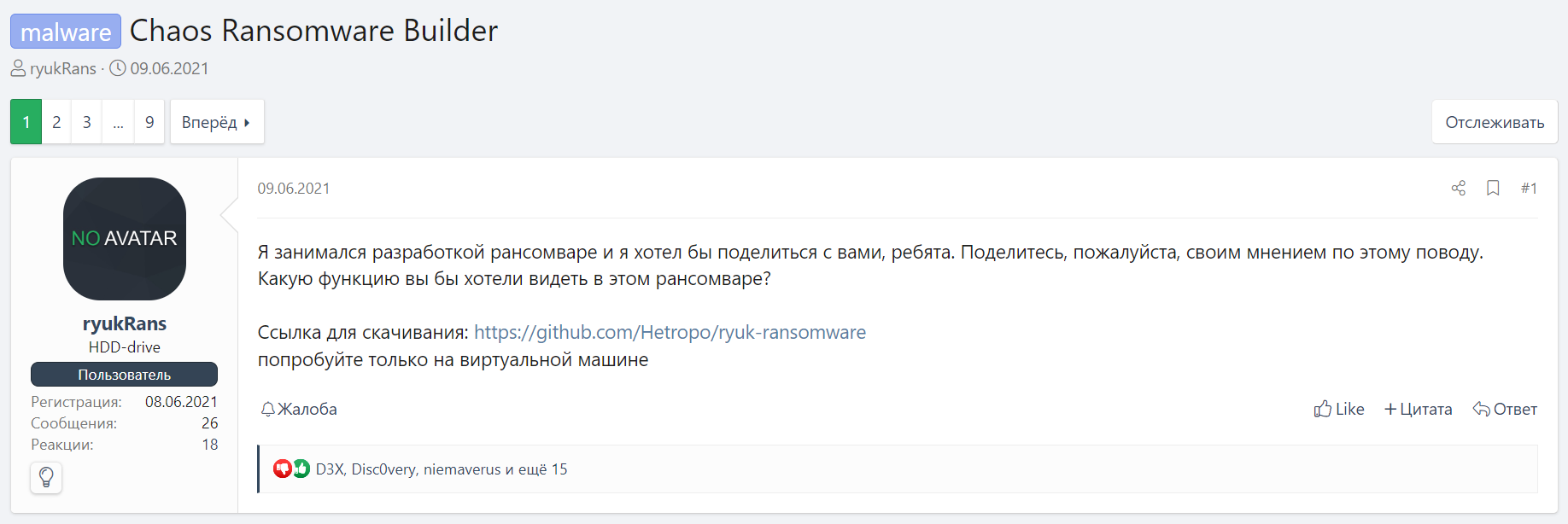
The file is Key Group ransomware, which is based on another malware called Chaos. Information about the Chaos ransomware family first appeared on one of the popular shady forums in June 2021. User ryukRans published a message in which he said that he was developing ransomware, and even posted a link to GitHub (Fig. 1).
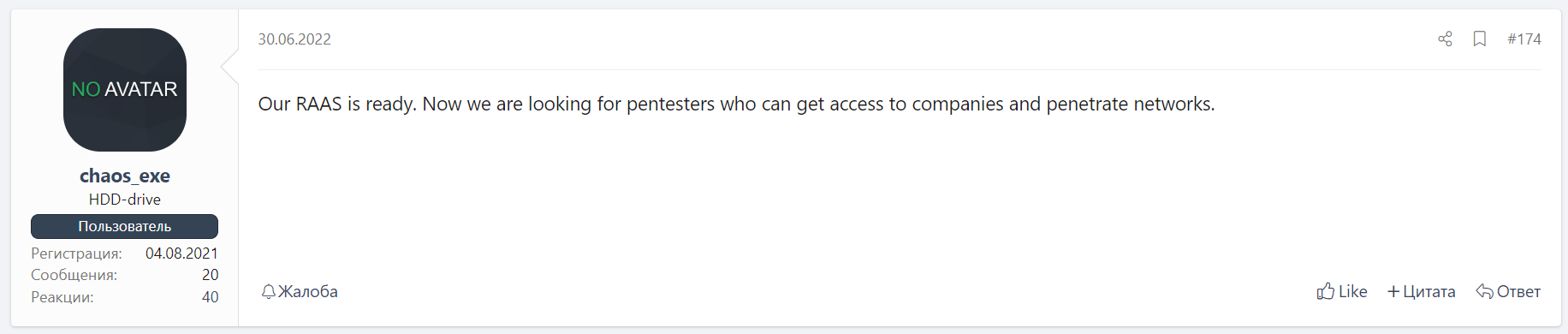
During the year, several versions of the builder of this malicious program were released, and already in June 2022, the so-called partnership program was announced, in the context of which penetration testing specialists were invited to cooperate to organize attacks on corporate networks (Fig. 2).
It is worth noting that the Key Group ransomware was created using the Chaos builder version 4.0.
Ransomware Analysis
After starting, Key Group performs the following actions:
-
Checks if there is a process with the same name in the list of processes. If there is, it stops its work.
-
If the configuration field
checkSleepistruethen if the launch directory is not%APPDATA%waitingsleepTextboxseconds. -
If the configuration field
checkAdminPrivilageistruecopies itself into%APPDATA%and run as administrator usingrunas. If the operation is rejected by the user (UAC), the function is restarted. If the names match and the program was launched from%APPDATA%the function does nothing (thus no infinite recursion on startup). -
If the configuration field
checkAdminPrivilageisfalseButcheckCopyRoamingistruedoes the same as forcheckAdminPrivilagebut does not elevate rights withrunas. -
If the configuration field
checkStartupFolderistruethen creates in%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startupan Internet link to a malicious file, which allows it to be automatically downloaded. -
If
checkAdminPrivilageistrueThat:-
If
checkdeleteShadowCopiesdeletes shadow copies with the commandvssadmin delete shadows /all /quiet & wmic shadowcopy delete. -
If
checkDisableRecoveryModeturns off recovery mode with the commandbcdedit /set {default} bootstatuspolicy ignoreallfailures & bcdedit /set {default} recoveryenabled no. -
If
checkdeleteBackupCatalogremoves all backups with the commandwbadmin delete catalog -quiet.
-
-
If the configuration field
checkSpreadistruethen copies itself to all drives except C, with the filename specified in the configurationspreadName(in this casesurprise.exe). -
Creates a note in
%APPDATA%\<droppedMessageTextbox>and opens it. The note contains the following text:We are the keygroup777 ransomware we decided to help Ukraine destroy Russian computers, you can help us and transfer money to a bitcoin wallet. -
Puts on the background of the desktop the picture shown below (Fig. 3).

-
Recursively encrypts every drive except C, as well as the following folders:
For each file in the directory, it is checked whether it has one of the correct extensions and whether it is a note. Further work depends on the file size:
-
The file size is less than 2,117,152 bytes. The contents of the file are then encrypted using AES256-CBC. The key and IV are generated using the function
Rfc2898DeriveByteswith some password and salt[1, 2, 3, 4, 5, 6, 7, 8]. The password, in turn, has a size of 20 bytes, has a charsetabcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890*!=&?&/and is generated using the standard functionRandom(). After encryption, the password is written to the file in the XML tag<EncryptedKey>which is RSA1024-OAEP encrypted and Base64 encoded, followed by the Base64 encoded encrypted file itself. -
The file size is greater than or equal to 2,117,152 bytes, but less than or equal to 200,000,000 bytes. A size of / 4 random bytes is generated and placed in the file in the same format as in the first case, with a random encrypted password, making the file theoretically unrecoverable.
-
The file size is greater than 200,000,000 bytes. A random number of bytes is generated between 200,000,000 and 300,000,000 and placed in a file in the same format as in the first case, with a random encrypted password, making the file theoretically unrecoverable.
If the directory contains subdirectories, the same operation is performed for each of them.
The ransomware also has additional functionality: it checks whether a bitcoin address is on the clipboard and replaces it with one of the attackers.
Indicators of compromise and detection rules are available to clients BI.ZONE ThreatVision.
How to protect yourself from such malware
Ransomware is usually distributed through the mail. Specialized solutions will help prevent attacks involving them, which will prevent a malicious message from reaching the user’s mailbox.
One of these solutions is the service BI.ZONE CESP. It saves companies from the problem of illegitimate emails by inspecting every email. The service under the hood has more than 600 filtering mechanisms based on machine learning, statistical, signature and heuristic analysis. This check does not delay the delivery of secure emails.