How to recognize a fraudulent letter. Memo for security specialists for training users in the basics of information security
I continue to share my experiences and advice from my own experience. Previously, I talked about training users in the basics of cyber literacy regarding passwords and phishing sites. Now it’s time for phishing emails. The material will be useful to everyone who patiently trains employees not to poke at interesting attachments, suspicious links and other oddities.
I don’t think it’s worth explaining why phishing emails are a “hug and cry” situation. But if you still need it, here are the company statistics Egresswhich deals with email security and anti-phishing: 94% of the companies they surveyed were victims of phishing.
BUT! Before diving into the world of “fishing”, under the spoiler there is a small reminder of the obvious.
Obvious-incredible
You can always say: “User, don’t follow bad links, it will be bad!” Walk only on good paths, then everything will be fine (for both you and me).” Oh, if only everything were so easy… The stumbling block here is that employees do not understand which letters are good and which are bad. Actually, this is the point of phishing, and this is why it works.
When telling and showing employees the various tricks that scammers resort to, don’t expect them to remember everything. Clearly define the minimum level of knowledge that should remain in the employee’s head. After all, as they say, in a critical situation you will not rise to the level of your expectations, but will fall to the level of your preparation.
It also needs to be said that there is no point in making “IS champions” out of employees who understand your level. It will be long and difficult. However, an information security friend zone can work. This is when in each department/team the most knowledgeable employee in information security gives advice to his colleagues.
How to understand that they want to hook you?
Basic signs:
Inspiration to action. The user is aggressively pushed into action so that there is no time to think. It looks something like this: “Urgent! Today is the last day to change your password. Follow the link or you won't be able to *insert as appropriate*“;
Surprise. The letter arrives suddenly. Surprise goes hand in hand with the Urge to action. (BEC attacks are an exception in this regard. They use already built social connections. The victim receives a letter from a person he knows.)
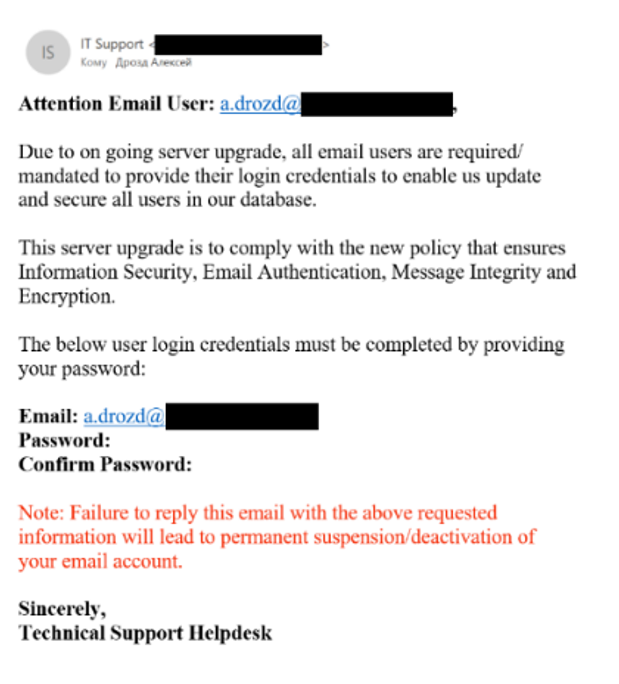
There is no personal address and/or official signature. This may indicate that the scammer was lazy or couldn’t find your name. Or he saves money and tried to compose the most universal text in order to “hit the squares.” Sometimes there is a strong feeling that the text has been passed through a translator.

Please note that in this section on “basic features” there is no “base” in the form of the sender’s address, links, etc. Why? Because in emails all this can be faked. It just so happened.
However, we will continue to look through the user’s eyes step by step to look for anything suspicious in the incoming letter.
Sender's address
Often a phishing email gives away the sender's address:
The sender's mailbox is unclear\the mailbox name and address do not match. If the address or name of the sender of the letter looks like some kind of disgrace, then this is a reason to think about it.
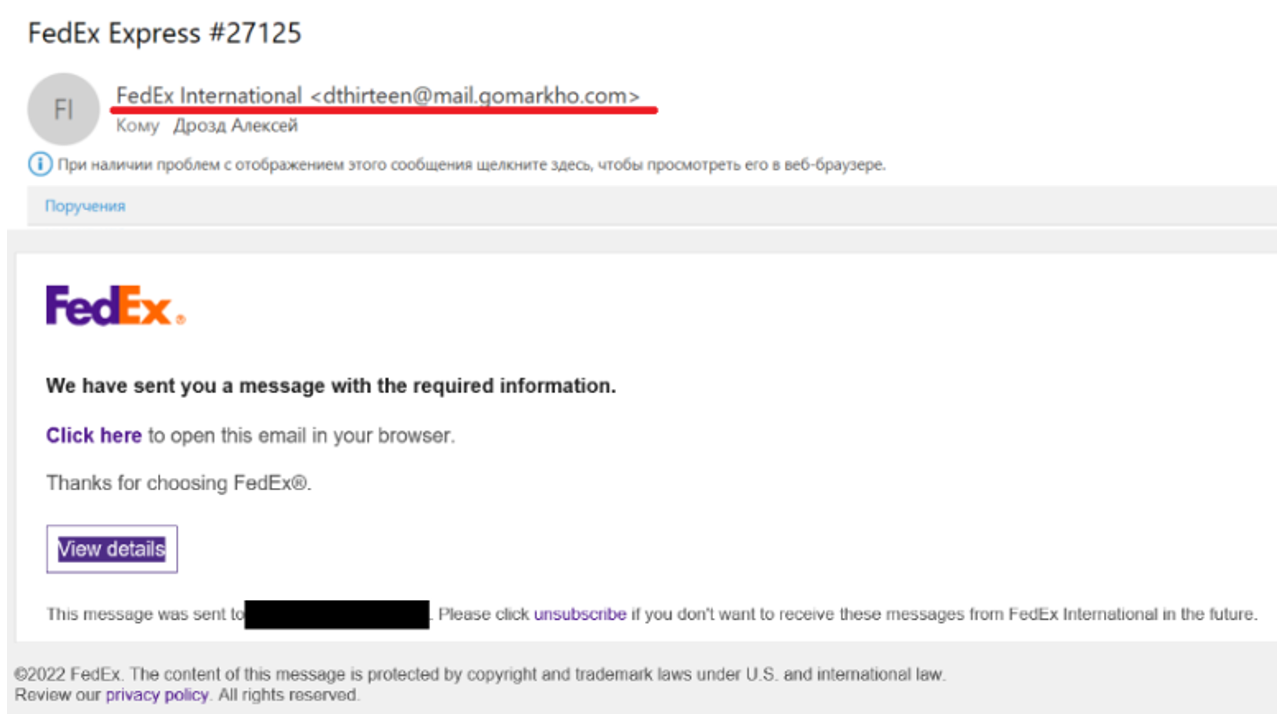
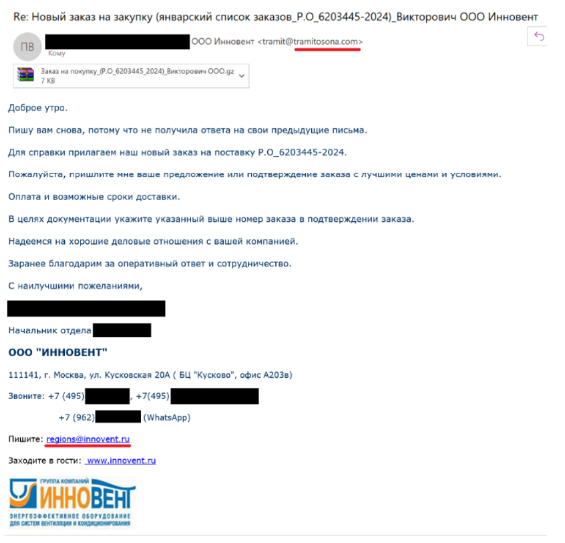
Sometimes, in targeted attacks, in order to disguise the sender’s address as something legitimate, scammers register a similar domain in advanceusing the following techniques:
Homoglyphs, i.e. graphically similar characters: 0 instead of o, I (capital “ai”) instead of l (lowercase “el”). Example: searchinf0rm.ru;
Missing or mixed up letters: sarchinform.ru; saerchinform.ru;
Name variations: searchimform.ru, search-inforn.ru;
Connection with other related words: searchinform-dlp.net, searchinform-IB.ru;
Using subdomains: searchinform.kazan.ru;
Non-standard domain zones: instead of the usual .ru or .com domains, .py (national domain of Paraguay), .co (national domain of Colombia) is used.
Then emails are sent from a similar domain. How can I not remember attack to Russian banks from the fake FinCERT. Then the attackers created a fake domain “fincert.net” and sent phishing emails from it. At the same time, no complex techniques such as homoglyphs were used, since the fake was similar to the real mail of the structure – “fincert@cbr.ru”.
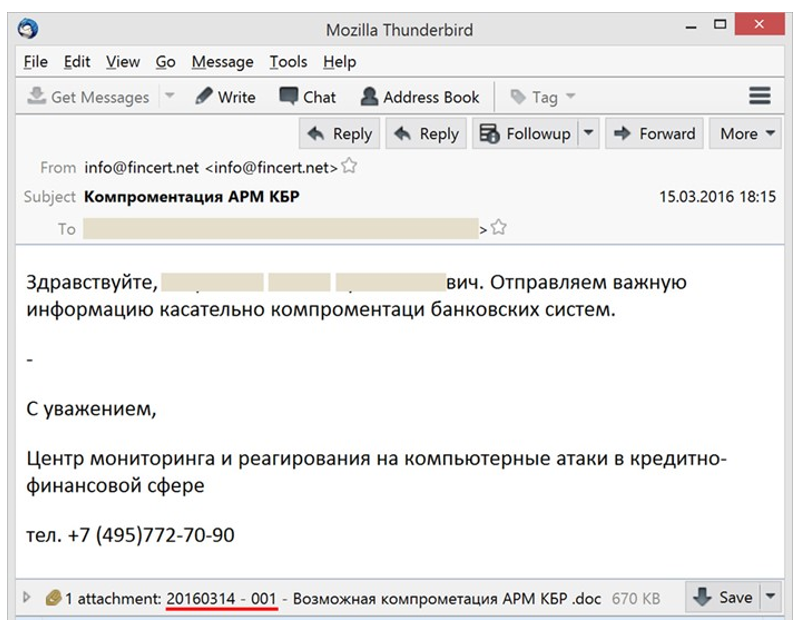
Finally, the box may be captured. That is, the sender is real (here is
JohnnyBEC attack). In this case, you need to remember the basic signs: motivation, surprise, personal appeal. In addition, you need to analyze the contents of the letter and pay special attention to links and attachments (if they are present, of course).

Content
You can also identify a phishing email by its content. The text is used to give credibility, to convince the victim of the need for action (following a link, sending some data, opening an attachment). It is worth paying attention to:
grammatical errors;
threats;
implausible promises;
careless design (lack of the usual logos, inscriptions in the “basement”, etc.).

Links
All the details about phishing links were discussed in the previous article. Therefore, now I would like to emphasize just a couple of points:
There are links to websites on the Internet. Before clicking on a link from an email, you need to check it. The easiest way to check is to right-click on a link, copy it and study it in a text editor or “feed” it to someone service for checking links.
Attackers can also mask or shorten hyperlinks. That is, write one thing and at the same time put a link that leads to another place.
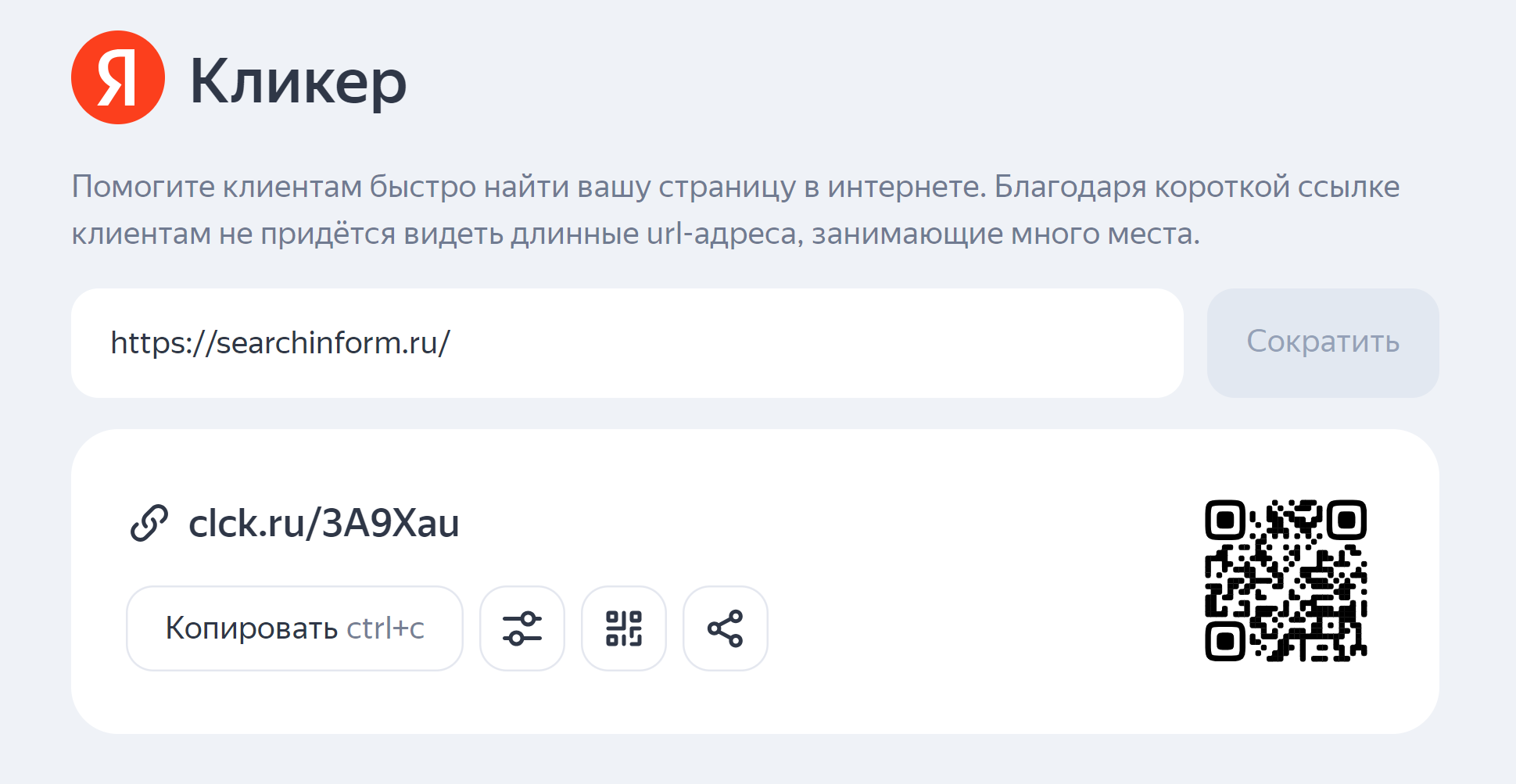
Fraudsters love to use shortening services, especially if they do not monitor security. But fortunately there are others Serviceswhich can decipher short links.
Attached files
In theory, the file can be anything, but traditionally preference is given to archives, office formats and mimicry of them. Mainin my opinion, something else – the text of the letter tries to convince the victim to open the file.
Documentation. Attackers like to send viruses in “documents” disguised as standard papers: commercial proposals, invoices or reconciliation statements.

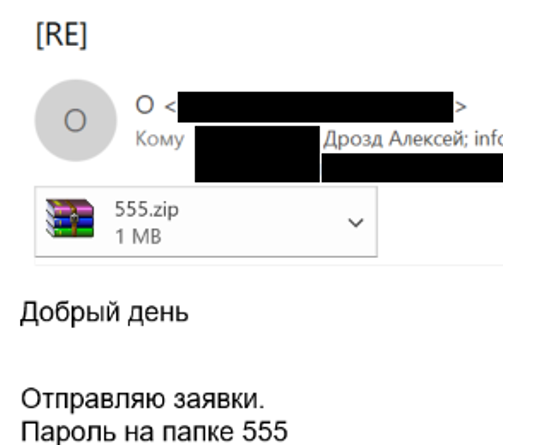
Password-protected archives. Sometimes (lazy) attackers put passwords on attached files. The password for them is written in the body of the letter. This is necessary so that security tools cannot scan the archive, since it is password-protected, and find a virus.

A limiting case reminiscent of the famous “Moldovan virus”
Conclusions and recommendations
Phishing is extremely effective (here, for example, statistics) and therefore there is every reason to believe that “this music will be eternal.” Efficiency is determined by the relative low cost and ease of implementation. In addition, the human factor will always be relevant.
Only constant practice and training can protect you from phishing. We have already managed to learn, but it is important to remember that we also need to undergo testing. Because if there are no tests and no one checks how the employee listened to the material, then the effectiveness of training will be low. Finally, I’ll give you some tips/advice on how to protect yourself from email phishing:
Use specialized information security tools, for example, spam mail cutters.
Build a layered defense system. It involves the creation of several security levels, each of which has its own security measures. If the attacker manages to overcome one level, then he will encounter the next, and so on.
Try implementing an information security friend zone. I wrote about it at the beginning of the material in the spoiler. In essence, an information security friend zone is a proxy, when used, all simple everyday questions regarding information security are addressed to a knowledgeable person within the department, and not to security specialists.