How much damage do DDoS attacks cause and how to protect yourself from them
Hello, this Oleg from DDoS-Guard! I have been writing about information security for many years. Of course, you are aware that the number of DDoS attacks is growing every year, and you need to protect yourself from them. It costs a penny to order such an attack today, but the losses can amount to six figures. Why don't so many companies enable DDoS protection? How do they explain this to themselves? Let's figure out whether such “savings” are justified – with facts, figures and examples.

Quick jump to basic questions
Is the increase in the number of attacks all that bad?
In short, yes. There have never been as many DDoS attacks as there are in 2023, both according to our data and according to the data of any other cybersecurity provider.
Fact from our analytical report: in 2023, the DDoS-Guard filtering system recorded a record number of 2,266,198 attacks. This is 80% more than in 2022; 1224% (!) more than in 2021.
An increase in the number of attacks is inevitable due to the increase in the number of smart devices connected to the network (TVs, smart cameras, even washing machines – the main “raw material” for recruitment into botnets) and the general reduction in the cost and simplification of organizing DDoS.
How much does a DDoS attack cost today?
By data Statista for 2023, the cost of a DDoS attack varied depending on whether the site had protection, as well as the power of the attack itself, within such limits – one month of continuous DDoS attack on an unprotected site cost $850, and on a site with professional protection it cost about $6,000 ( $200 per day).

At the same time, at the end of 2022, in popular thematic hacker communities on Telegram, one could find advertisements for a DDoS attack lasting a day for an average of $40 (power is not specified). Compared to 2021, the price has decreased by approximately 20%. The decrease was probably due to the simplification of interaction between customers and performers – this was facilitated by the growing popularity of the Telegram messenger.
CloudFlare provides a similar figure, noting that the cost of DDoS attack services on popular platforms is only $30 per month. These low-cost options likely won't do much harm to a company as long as it has at least some protection and resource capacity to handle the increased load.
However, a 24-hour strong attack on a selected target will cost only $200 – this is also relatively small money, but the damage from such an attack can be much more serious. But for just a thousand dollars on some services you can order a whole week of continuous DDoS attacks! For a business with little or no security, this will have catastrophic consequences.
In 2023, Russian companies are faced with a new type of DDoS attacks that are carried out continuously in the background. By data Servicepipe, in some cases, continuous DDoS attacks can continue for months and even years, and, curiously, this is not about hacktivism, but about completely commercial motives. It is not difficult to see the reason for this trend, first of all, in the reduction in cost of organizing long-term DDoS attacks.

Dmitry Nikonov
Head of DDoS protection at the web application level at DDoS-Guard
The trend of stealth involvement in hacktivism, which allows hackers to carry out sustained attacks, we observed back in 2022: some sites using special scripts under harmless cover — for example, online games – generate malicious traffic to disable the victim. Users of such sites, without knowing it themselves, unwittingly participate in the attack — in the background.
The question also arises of what is considered a continuous attack. As you can see in the heat map, some of our clients are attacked every day even after enabling protection.
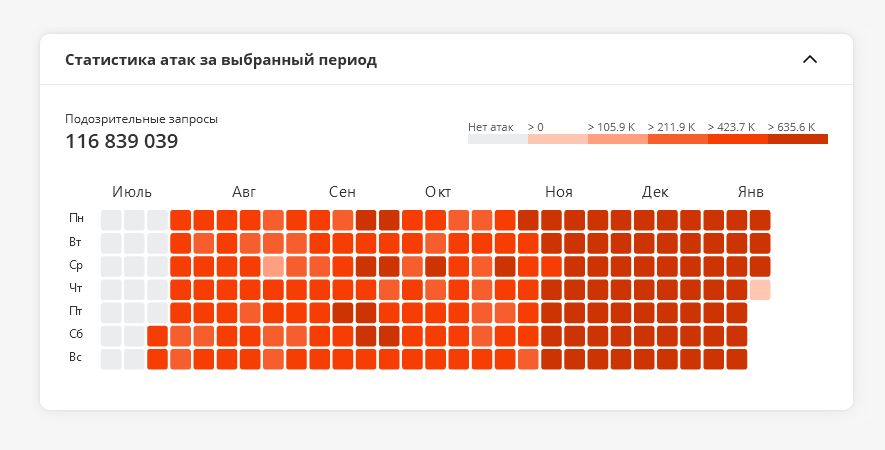
Thanks to protection, they do not notice the impact of DDoS. But if one wave of attack is immediately followed by another, is this considered one continuous attack? It all depends on the method of data analysis.
According to our data, the vast majority of attacks involve short-term bursts of traffic—up to 20 minutes. There are 1.3 million of them out of a total of 2.2 million attacks that DDoS-Guard recorded over the year.
What is a successful attack and downtime
The number of DDoS attacks is growing faster than the number of companies protected from cyber threats, and the attacks themselves are becoming more sophisticated. This leads to the fact that the percentage of successful (damaging) DDoS attacks increases.
An attack that is successful for an attacker is, first of all, downtime for the victim, that is, a situation where the infrastructure (site, network, service, all at once) “lies” – does not function and does not work as usual.
When work processes are forced to stop, the business begins to lose money and reputation. The longer the downtime lasts, the greater the losses, and some of them cannot be recovered – for example, customer trust.
The amount of losses can vary significantly depending on the scale and specifics of the company or organization. Only one thing can be said for sure: the larger and more serious the system that suffers downtime, the more serious the consequences.
Downtime should not be underestimated, since in the era of high-speed Internet, clients have become much more demanding – they expect sites to open as quickly as possible. According to research Aberdeen Group, even a simple one-second delay in page load results in an 11% decrease in page views, a 16% decrease in customer satisfaction and a 7% decrease in conversions. By the way, an increase in download speed by 1%, on the contrary, increases conversion is about the same (6.7%).
IN report Oracle on customer experience says that 89% of customers leave for competitors if they receive a negative user experience.
How much do affected companies lose?
The most serious known downtime incident occurred in October 2021, when the entire Meta* ecosystem, including Facebook*, Instagram* and WhatsApp, collapsed. The cause was not a DDoS attack, but a technical oversight, but the result was clear – the giant infrastructure was down for about six hours, which brought $60 million in direct losses and $47.3 billion in share price losses.
In September 2022, the servers of the video game publisher Activision Blizzard were disabled for 4 hours. Analysts estimate this could have caused hundreds of thousands of dollars in losses. As a rule, the amount of losses is not publicly disclosed by the company itself. The Ponemon Institute estimates that a DDoS attack can cost up to $22,000 per minute of downtime (while Gartner indicates figure of $5,600 on average per minute, probably the actual total depends on the size and specifics of the company).
Downtime seems to be the most expensive for cloud systems. According to a survey of corporate executives conducted by Parametrix, more than 50% of respondents said cloud downtime would cost them $100,000 per hour or more. More than 5% of respondents said that cloud downtime would cost their employers more than $1 million per hour.
In the corporate sector, the cost of downtime “can range from $1 million to $5 million or more, excluding legal fees, fines and penalties.” According to Franklin Electric, in the telecommunications industry, downtime can cost $11,000 per minute per (!) server. In the banking, transport and financial industries, one-hour downtime will cost several million dollars.
What about Russian companies? In the first half of 2023, according to survey “RTK-Solar”, the average damage to domestic companies from hackers' actions increased by 30%, to 20 million rubles. on an annualized basis. This is quite a lot, considering that all of these attacks could have been prevented. Especially when you consider that organizing such an attack costs many times less.
How to calculate the cost of downtime
Difficult. It's difficult to calculate. Determining the exact amount of losses for a specific company in the case of a specific downtime is a headache, since we are talking not only about direct financial losses, but also about lost benefits (in the case of, for example, marketplaces), reputational losses and other things.

The cost of lost sales can be roughly calculated by multiplying the site's average revenue per day/week/month by the number of days/weeks/months the site was unavailable to users. In turn, the cost of lost customers is calculated if you multiply the average revenue per customer by the number of users who were unable to access the site during the attack. Please remember that the final figure will still be an estimate, as some factors may not be obvious or their significance may be difficult to objectively assess.
How much do companies spend on protection?
The reasons for DDoS are primarily financial. The larger the company’s turnover and the more expensive its processes, the wider the coverage, the more desirable a target it seems for an attack by a competitor or hacktivist who will try to destroy these profits.
To find out how much companies in the Russian Federation spend on DDoS protection, I turned to a colleague who works in procurement for help. He examined data from the Unified Information System in the field of procurement zakupki.gov.ru.
What can we highlight from this entire data array:
In terms of volume – sharp growth
In 2022, 85 government procurements were published specifically for DDoS protection in the amount of 243 million rubles. As a result of these purchases, 79 contracts worth 211.4 million rubles were concluded.
Now we look at 2023: 117 government purchases worth more than half a billion, as a result, 114 contracts worth 454 million rubles were concluded.
Thus, in just a year we see double growth in this area.
By area – change of priorities
In 2022, half of the costs (49%) for protection against DDoS attacks fell on information technology companies, followed by universities (13%), and only in third place were government-owned management companies.
In 2023 the picture is completely different. The share of IT companies among customers decreased to 31%, at the same time, purchases of protection by the energy sector increased sharply (to 29%), and MFCs burst into third place in the ranking (immediately 22%).
This correlates with the dispersion of DDoS attacks across a wider range of industries observed in our statistics.
Physical protection is becoming more popular
In 2022, there was almost parity between the popularity of purchasing physical and cloud solutions – in terms of the pure number of purchases, physical connections were significantly in the lead, but in terms of money the distribution was almost 50/50.
In 2023, we are already seeing a clear significant increase in the number of purchases and contracts with a physical connection to the customer’s infrastructure. The absolute indicators of cloud solutions decreased by 15% in money terms.
Procurement competition has increased
If in 2022 23% of the financial volume of purchases of DDoS protection were carried out in a non-competitive way (that is, from a single supplier), then in 2023 this figure is only 5%. Thus, all bona fide DDoS protection providers today have a good chance of competing for the tender.

How many companies are actually protected?
Based on the results of 2023, one thing can be said with confidence: companies in Russia are not spending enough money to ensure their cybersecurity perimeter. Over the year, the number of attacks on the Russian telecommunications sector has increased several times, significant damage was caused to clients of attacked Internet providers, which exposed the need for professional protection at the level of not only backbone, but also local providers.
At the level of the companies themselves, everything is even worse: according to data from June 2023, almost a third of the top Russian companies by revenue did not provide an adequate level of website protection from DDoS attacks. The energy sector (26%) turned out to be the most defenseless, as well as, oddly enough, financial organizations (16%). Manufacturing and transport enterprises do not have professional protection against DDoS attacks in 12% of cases.
Statistics show that the absolute majority of DDoS attacks (up to 90%) both in the world and in Russia occur at the L7 level according to the OSI model, that is, they occur when web applications are disabled. Preventing such attacks requires increased resources and more sophisticated filtering algorithms.
At the same time – and this is the most striking trend – almost half of the companies from the Russian top 100 do not have professional protection at all, precisely at the L7 level (data Stormwall), although at the network level (L3-L4) the situation is already noticeably improving. Thus, any sufficiently large-scale attack at the application level could theoretically bring down the infrastructure of the largest market participants.
The most vulnerable according to L7, ironically, are precisely those who have the greatest risk of being subject to a DDoS attack – the telecommunications sector (38%), energy (26%), financial institutions (16%).
Apparently, it will take some kind of large and serious local incident (like the aforementioned fall of Facebook, banned in Russia), for Russian companies to start taking seriously the prospect of protecting against attacks at the application level.
Such incidents are not far off, as new serious cyber threats are constantly being recorded. For example, in November 2023, domain name registrar Reg.ru reported a three-day attack with a capacity of more than 40 GB/s, which involved a botnet of 40 thousand unique IP addresses. And there will be more and more similar cases.
Why don't companies enable DDoS protection?
It is reported that many companies are in no hurry to install professional protection against DDoS attacks, preferring to include these costs in the price of their services. As the number and strength of attacks grow, the cost of downtime can significantly exceed the cost of installing protection – and for some industries it already exceeds.
According to a survey conducted during AM Livewhere our expert Dmitry Nikonov participated, almost 20% of company owners did not bother with DDoS protection at all.

At the same time, 65% of respondents rated the likelihood of a personal attack on their company as high or very high.

The main reasons for reluctance to install DDoS protection are the high cost and complexity of setup:
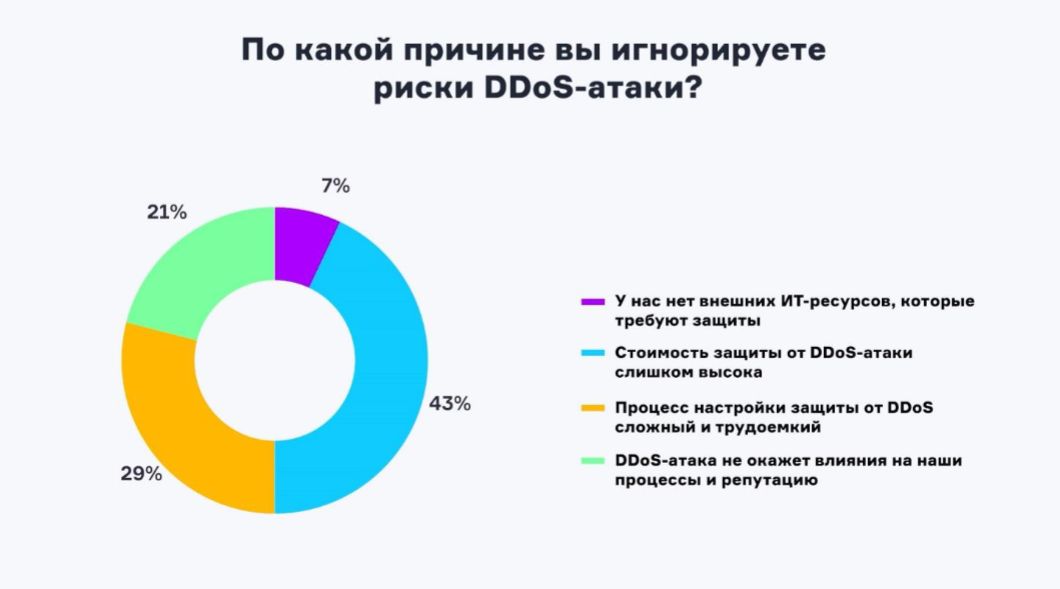
Comments are probably unnecessary. I wonder what the results of a similar survey from the same companies would look like, but which had already suffered a serious DDoS attack?
Which protection scenarios are most effective?
Since it is impossible to predict at what level (according to the OSI model) an attack will be carried out on your company, it is logical to connect protection at all main levels. Based on the above statistics, first of all you need to take care of application protection, at the L7 level.
There are, of course, various preliminary measures that can be taken to optimize the load and other things (some of them will also help with increasing the overall productivity of processes, which, as we remember from the examples above, in itself increases conversion), I sorted it out them on our corporate blog.
In the event of a really serious DDoS attack, however, I’ll be honest – none of this will help. So there are two options left – either pray and hope that hackers will bypass you (every year and even month the probability of such luck decreases sharply), or stop saving on your own digital health and enable DDoS protection.
Prospects
Back in 2016, according to IDC, the DDoS protection market in Russia was about $20 million. Now it is several times larger and continues to grow: according to the RuVDS company, the demand for cloud services and secure hosting in Russia in 2023 increased by 17.5% against 6% a year earlier.
MTS RED, a subsidiary of MTS in the field of cybersecurity, reports that the volume of the Russian market for protection against DDoS attacks in 2022 amounted to 762 million rubles. In 2023, growth was projected to be around 60%, and by 2025 – 250%.
In January 2024, Deputy Chairman of the Government of the Russian Federation Dmitry Chernyshenko said that the digital maturity indicator in Russia exceeded 74%, and also noted that digital transformation has become one of the five national development goals of the country until 2030.
I would like to believe that DDoS protection will become one of the priority areas on which the budget of this megaproject is planned to be spent.
What do you think about this problem and ways to solve it?
* The Meta company is banned in Russia and is recognized as extremist, as are its social networks Facebook and Instagram.