Exploring the dark side of Shodan
Shodan is a search engine that allows users to search for different types of servers (webcams, routers, servers and so on) connected to the network Internetusing various filters.

Once you enter a search query on the Shodan website, it will begin scanning any device with an IP address that is connected to the Internet, such as a laptop, server, printer or other device. This can be incredibly useful in identifying misconfigured devices that may be exposing sensitive data.
The interesting thing is that most of the devices listed on Shodan have default credentials. So, it’s quite easy to just log in to the device.
Obviously, now you might be wondering that if I connect my home computer to the Internet, my device will appear on Shodan and hackers will try to take advantage of my system. Oh no. It doesn’t work that way. Shodan will probably list your router, but will not be able to list the private IP device. Or if someone, for example, has port forwarding enabled on their device, then their device can appear on Shodan.
TOP 5 search terms I encountered with Shodan
Request on FTP port 21 with anonymous login enabled:

"220" "230 Login successful." port:21Selected a search result at random and logged into the FTP server as an anonymous user.

I even found a file called “client_package.zip”. The download was later interrupted.
Another ftp server I logged into –

2. Webcams:

"Server: IP Webcam Server" "200 OK"I picked a random search result and it showed open ports 80 and 8080.
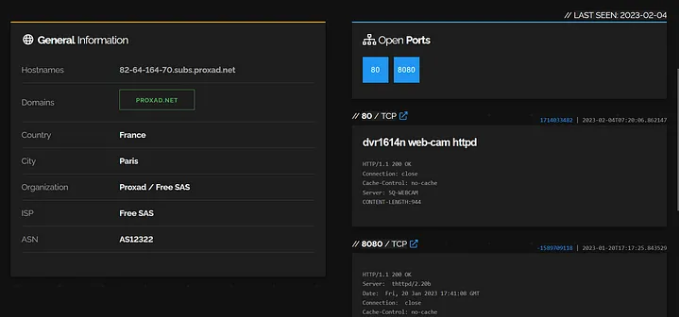
Allows you to access the website via port 80.
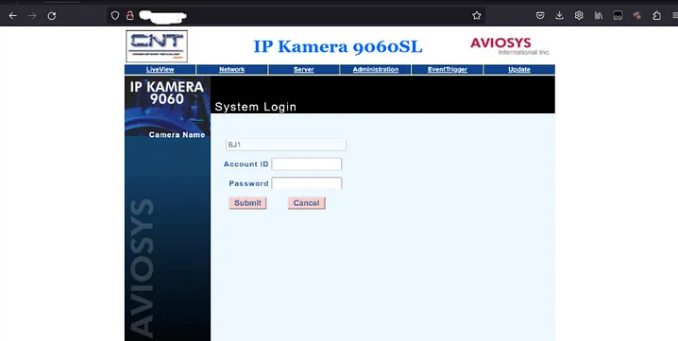

Now you just have to find that company’s default credentials and hope they don’t change them.
Another way to search for webcams:
cgi-bin/guestimage.html
3. SMB Disabled Authentication:
"Authentication: disabled" port:445
I even found a host vulnerable to the Eternal Blue SMB vulnerability.
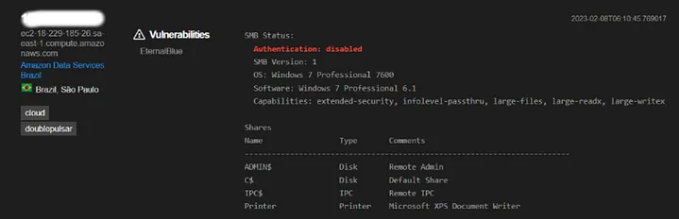
Look at the number of ports open on this computer.
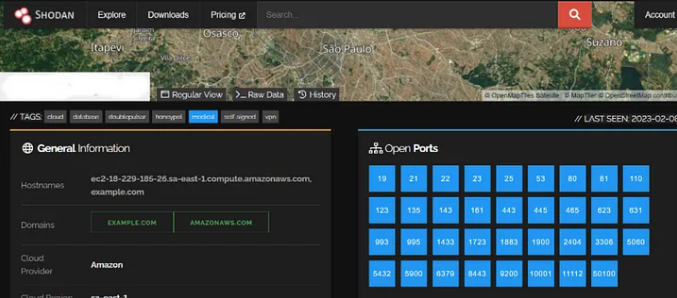
Running his website on port 80 shows that it is running apache tomcat.
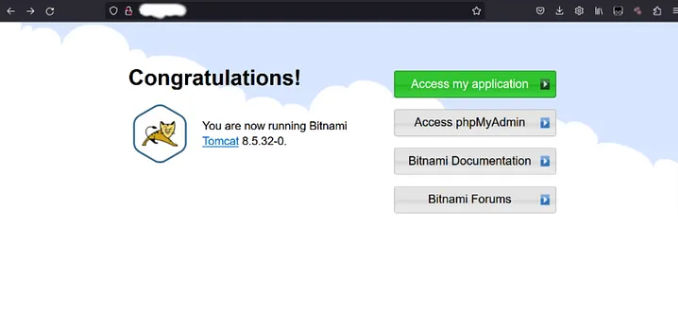
4. Jailbroken Ubiquiti Devices
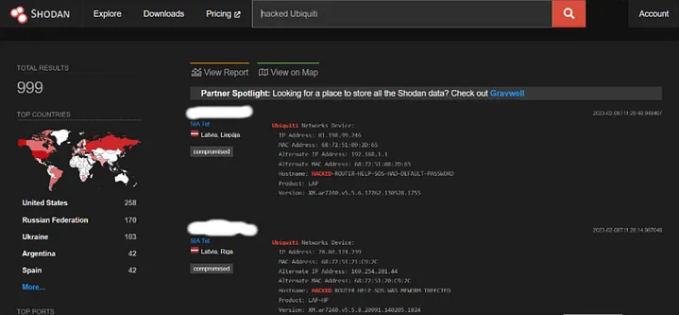
hacked UbiquitiCompromised Ubiquiti devices are listed here.
You can see by the hostname of the first one that it has a default password.
5. Finding compromised VMware ESXi servers

html:"We hacked your company successfully" title:"How to Restore Your Files"A global ransomware attack has hit thousands of servers running the VMware ESXi hypervisor, and many more are expected to be affected, according to national cybersecurity agencies and experts around the world.
This search query reveals those VMware servers that are vulnerable.
I opened his website on port 443. It looks like it has already been hacked and the hackers are demanding btc in return to remove their ransomware.

In conclusion, Shodan is an insanely powerful search engine that can be used to identify potential security vulnerabilities in connected devices.
It has the potential to cause significant damage if used incorrectly and it is important to understand the risks associated with its use.
For this reason, it is important to remain vigilant and aware of the potential risks associated with using Shodan and take all necessary measures to ensure the security of connected devices before connecting them to the network.