Ducktail, an attack on marketing specialists
Last week, Kaspersky Lab specialists
a fresh attack codenamed Ducktail. A group from Vietnam is believed to be behind this cybercrime campaign. A characteristic feature of Ducktail in its latest version is its specialization for marketers. Email “baits” are designed to attract just such specialists, and the result of infecting a computer is the theft of business accounts on a social network.
The most recent cyberattack of this type occurred from March to early October 2023. Its peculiarity was the use of malicious applications written in Delphi, although previous attacks used .NET code. Despite the fact that the cyber attack tools used are basic, this method is not without effectiveness.
In the lives of many specialists, a variety of “briefs”, lists of requirements and other documents are commonplace. Cybercriminals’ calculations are based on the fact that the potential victim is accustomed to receiving archives with different files from unknown sources. The malicious archive looks something like this:

A set of pictures, videos and an executable file with an icon from a PDF document. Cyber fraudsters do not attempt to take advantage of one of the vulnerabilities, for example, in the Adobe Reader, we are talking about pure social engineering. The executable saves several files on the system, including a Powershell script and a normal PDF document. The PDF is shown to the user, and from his point of view, no problem has yet occurred. Meanwhile, along the path C:\Users\Public\Libraries\, the malicious libEGL.dll library is saved and executed. It, in turn, finds all .LNK files that link to browsers built on the open-source Chromium engine. A line is added to the browser launch line that initiates the addition of a malicious extension to it. Browsers, meanwhile, are forced to close so that the user initiates their restart.
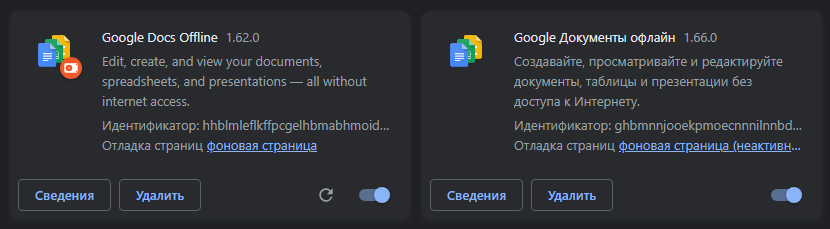
The extension disguises itself as a legitimate Google Docs Offline addon. In the title picture, the malware is shown on the left, with the real Google extension on the right. This extension provides full surveillance of the victim’s web activity – data about all open tabs is sent to the command server. If the malware detects a visit to the social network Facebook, the user account is checked for the presence of business accounts—corporate pages managed by the victim. Access to accounts is intercepted, which is why cybercriminals have tools in their arsenal to steal cookies, access social network APIs, and bypass two-factor authentication.
Most often, attackers attacked users from India. The cybercriminals’ tools are not amazing; they use fairly basic but reliable techniques to steal user data. Despite its simplicity, this tactic works. So, in the spring of this year there was hacked popular Youtube channel Linus Tech Tips. After intercepting the browser session, the attackers gained access to the channel and broadcast a crypto scam video on it for several hours. This attack began in a very similar way: an employee received an offer of cooperation with a document in PDF format.
What else happened:
Another one publication Kaspersky Lab experts examine in detail the behavior of cybercriminal groups from Asia.
According to Microsoft, a zero-day vulnerability in the popular IT infrastructure management software Sysaid is active. used for hacking organizations. Behind the attacks is a group that previously exploited holes in other corporate software and services, including MOVEit Transfer software.
In Google Ads distributed by a malicious version of the popular CPU-Z utility.
Appeared evidence exploitation of the recently discovered Looney Tunables bug in Linux-based OS. A real attack on Linux servers begins with exploiting a vulnerability in the PHPUnit framework, which makes it possible to execute arbitrary code on a system with low privileges. The Looney Tunables bug is then used to escalate permissions.
Microsoft is now blocks suspicious requests in the native Authenticator client. This measure is aimed at combating multiple access requests from the attacker. Constant notifications on the victim’s smartphone can lead to the user confusing a request from an attacker with a real one or simply accidentally clicking on the approval button. Previously, to combat the same phenomenon, Microsoft introduced a requirement to enter a two-digit verification code. Now, suspicious requests will not generate a notification on the smartphone at all. In case of mistaken blocking, the owner will always be able to log into the application independently and approve the authorization request.