Sality Analysis
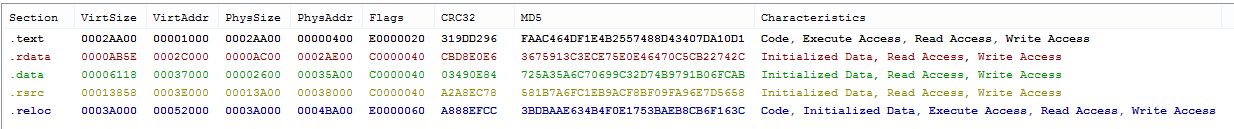
Our analysis begins with a screenshot of a Windows Defender service file infected with malicious code. Pay attention to the malicious code embedded in the last section of this file. (picture 1):

Figure 1: The last line shows the read / write executable
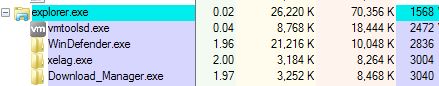
Sality creates three copies of itself. The first copy is saved in the folder %AppData%localtemp (figure 2) and embedded in the conductor process (figure 3):

Figure 2: The first copy of Sality is saved in the folder %temp% With name xelag.exe

Figure 3: A malicious process is introduced into the explorer process (xelag.exe)
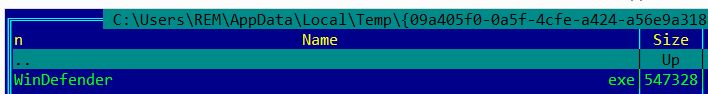
A second copy of this malware is stored in the folder %AppData%localtemp%random_folder_name% With name WinDefender.exe (figure 4):

Figure 4. Second copy of Sality named WinDefender.exe
The third copy of Sality is stored in the virtual memory of the remote process in the folder %APPDATA%MicrosoftWindowsStart MenuProgramsStartupDownload_Manager.exe (Figure 5):

Figure 5: Third copy of Sality saved with name Download_Manager.exe.
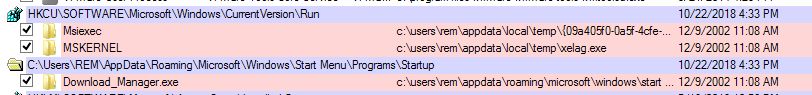
To ensure sustainability, Sality modifies the registry (figure 6):

Figure 6: Sality is written to the system registry.
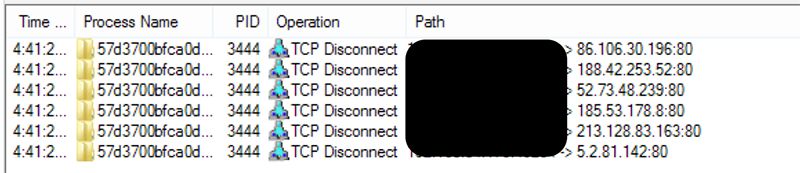
The virus then attempts to establish a P2P connection to download additional malware. (Figure 7):

Figure 7: Sality accesses suspicious IPs for more malware
When the victim restarts the computer, all three copies of the malware are embedded in explorer.exe (figure 8):

Figure 8: All three copies of Sality are embedded in the explorer process.
Why is Sality important and why should I be bothered?
Sality made its debut the same year that Apple opened the iTunes store, and cinemas put together a box office at King’s Return. He remains a threat today. Only one longevity of the Sality virus is evidence of its effectiveness, adaptability and adaptability. Any malware that is still viable a decade and a half after its initial detection should not be out of sight of users and security professionals.
Compared with Nemucod, Sality is a more complete and mature malware example. It has a long history of changes that point to a diverse set of use cases with the ability to deploy Sality depending on the objectives and complexity of the attack. Comparing Sality’s capabilities with the categories of MITER ATT & CK tactics, this malware is able to play a role at every internal stage of the attack chain after execution, which means that Sality needs a delivery method on the environment before it can get to work.
If necessary, Sality can act as the main operational agent, providing the attacker with a basic set of functions for performing various actions on the goal, aimed at maintaining and expanding access. It also has the ability to modular download additional features as needed by an attacker. The flexibility offered by this basic feature set makes Sality suitable for a wide range of offensive campaigns.
The flexibility afforded by common malware such as Sality offers more sophisticated attackers the ability to hide the activity and intent of a targeted attack under the guise of a broad, indiscriminate campaign. An attacker can use the capabilities of Sality in the first wave of the target attack, setting a foothold in the environment. Thanks to this access, an attacker can open up more sophisticated or destructive malware after he assesses operational risk based on the defensive position of the target.
Cylance Stops Sality
Users CylancePROTECT will be happy to know that we detect and prevent Sality before its launch. By preventing Sality from launching, we protect our customers from this masticatory malware and the many other threats it seeks to deploy. Sality may or may not be long-lived, but it will not survive on machines protected by CylancePROTECT.
Get a discount on the course.