The story about the hijacking of a Telegram account (partly successful)
And I really liked the fact that it is quite secure – if a cloud password is configured, then the probability of hacking becomes minimal.
This is a story that worked exactly in my case and is not an instruction for all occasions.
I decided to share the text of my client’s Telegram hacking story and conclusions on this topic. This content is also available in video format.
What happened?
A man’s cart was recently hacked (with a simple cloud password) and he reached out to me. I decided to help restore access and tried to restore access, first by logging into my account. I go into a person’s account and do not have time to get to the interface before resetting all devices – the scammer throws me out.
I decided to do it through js script. I wrote a script and first decided to check how the entrance to the telegram goes on my phone number. I tried several times, successfully logged into my account.
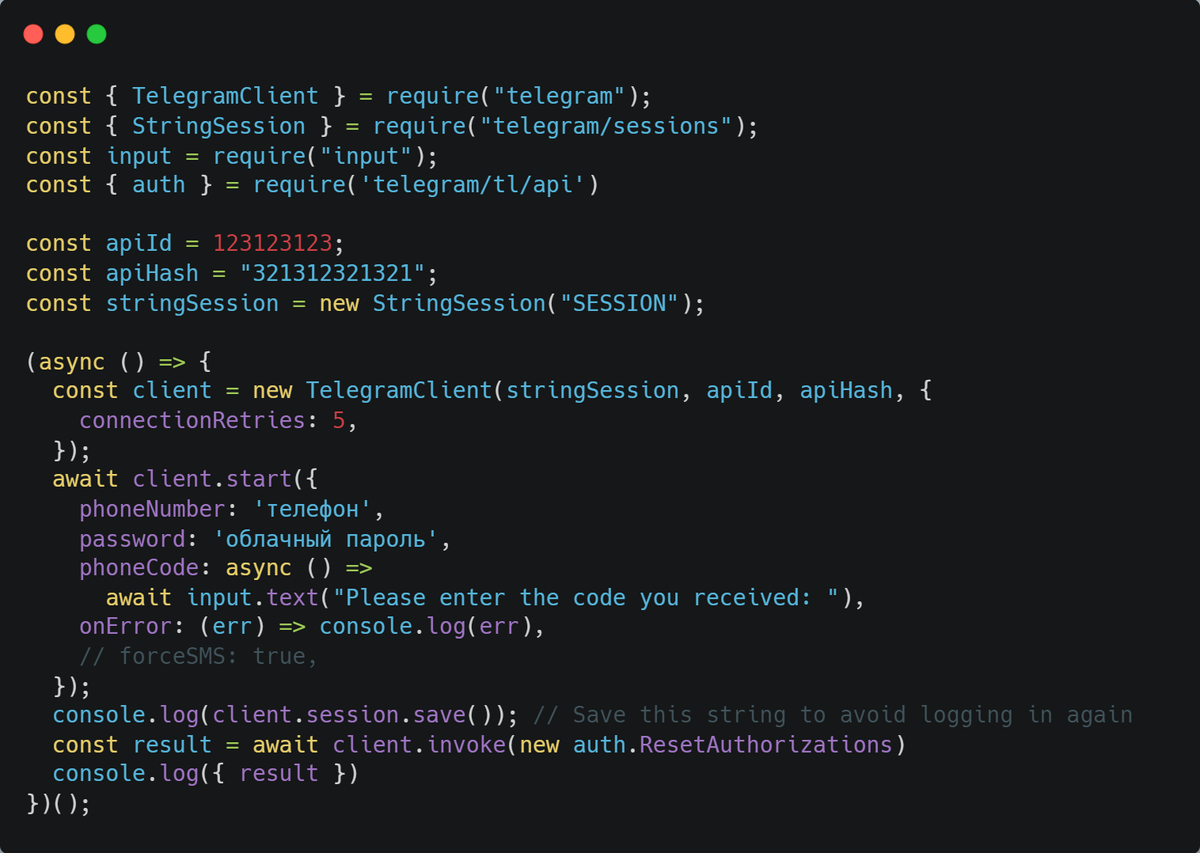
I already decided to check how the exclusion of all devices works and …. And the telegram decided that I was a suspicious guy:
kicked me out on all devices from my account,
allowed to enter the account only from the phone (to receive SMS)
deleted all my messages that I wrote in a private chat to people in the last 2 days.
The whole personal has become such that they write to me, but there are no my answers.

At first I was afraid that the cart had been stolen, but then I realized that this was the protection policy. Then we decided to try to return access to the account of a friend – we go in and get the error “too many attempts – come back in 4 hours.”
BUT! Account scammer not thrown out and now he had 4 calm hours of sitting quietly in the account of a friend, he even has a wonderful conversation with me, on her behalf, throws voice messages with her voice and even copies her manner of communication …
As a result, it turned out:
scammer sits quietly and cheats
host can’t log in to their account for more than 3 hours
I (non-scammer), trying to legally access my account through api, immediately registered as a scammer
digital cloud passwords are easy to crack (as it turned out, it was not the complexity of the password – more on that later)
Preparing for return surgery

It was possible to find out that scammers hijacked a person’s account through a fake link. Moreover, they got access a few days ago and quietly waited … They waited because the telegram has an interesting policy: they do not make it possible to log out third-party connections to telegrams.
The idea is just that the scammer who gained access could not immediately kick the account owner out of the network. The account owner sees the notification “there is a spy entrance” and, in theory, removes this connection in the settings, but not everyone is so attentive.
As a result, there was an interesting situation. There are still 4600 seconds left to wait until the next login attempts, and I planned to make an active attack with my bot so that telegram would also respond to my requests from the bot, as was the case with my account earlier: logout on all devices and the requirement to log in again via SMS.
Until then, even if I get access to the account through the official Telegram application, I won’t be able to throw out the scammer – he’s been online for more than 2 days and now he’s supposedly the “owner”. But he can throw me out easily and simply, and, of course, he will do it right away.
But it was necessary to act quickly and decisively – after some time he will be able to change other settings (phone number, recovery mail) and then you can forget about the account.
return operation
The operation was successful… almost. At first it was necessary to wait for the end of the blocking time. At that time:
I kept in touch with a scammer who threw me a card number (handed over this number to the bank);
The fraudster even threw a drawn card with the initials of the owner (but in the application the card was in a completely different name when trying to transfer money);
The swindler continued to throw voices with the voice of the owner in order to inspire confidence in me.
At the appointed time (when the spam block was removed) I started bombing the account with the field forceSms: trueso that the entrance is via sms and not the code in Telegram (scammers have access to this code).
An error came from the cart server SEND_CODE_UNAVAILABLE, which says that she cannot send an SMS code. I realized that my bot will not receive SMS, but it will come to my native Telegram … But they are immediately thrown out of there after authorization.
Then I did the following:
I go to the official application from a separate phone, request a code via mail, the account owner says the code.
as soon as I enter the cloud password, at the same second, I launch a bot that requires a code from Telegram.
they still don’t have time to kick me out of the session on the phone and I managed to see the code
I immediately enter this code into the bot, the bot comes in and sends resetAuthorizations
all sessions die except for the bot
then we calmly go into the account through the standard procedure on the necessary devices.
Everything seems to be fine, but all personal correspondence on behalf of the account owner was deleted. Apparently, there was a bot on the side of the scammers who regularly cleaned everything up after itself… Plus, a self-destruction timer was set everywhere – literally on every personal chat, and not globally in the settings. For a long time, the account owner was faced with the fact that messages were deleted after a few hours.
How not to get into a similar situation?
I don’t even want to make any conclusion, but please be careful where and how you enter your data. ESPECIALLY if you enter an authorization code, a cloud password – you can only enter it if you enter the official app!
The mechanics of the hijacking was as follows: the owner of the account logged into his account in the custom Telegram application inside the “voting site”. As a result, the scammers got a session through which they only waited when it would be possible to do resetAuthorizations.
As soon as it became possible to do this, the bot removes all authorizations and starts the attack through the existing session. Along the way, of course, the scammer’s bot kills all sessions and attempts to gain access to the account…
As for support: I immediately wrote to support the cart, but the support there comes through volunteers, who did not answer me in 5 hours. That is, it is clearly not worth counting on support ….
I strongly recommend that you regularly enter active sessions and check them for “strange sessions”. Among them, there may be a scammer who is just waiting to be able to kick you out of your account and start his dirty deeds. Go to Settings – Security – Active sessions
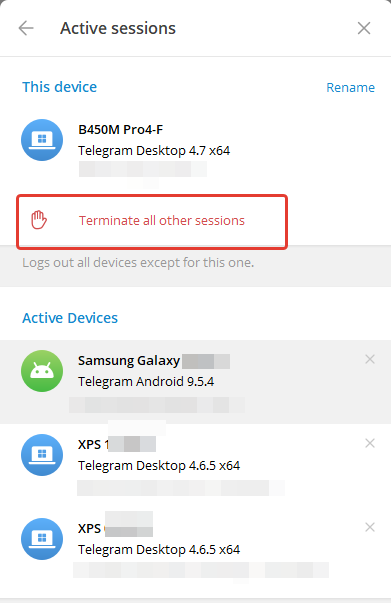
If there is something suspicious, then it is better to remove it and sleep peacefully.
That’s all! Thank you for attention! I will be glad to your subscription here, as well as in Telegram or Youtube. I share different content about IT and not only.