Security Week 19: bruteforce attacks on RDP
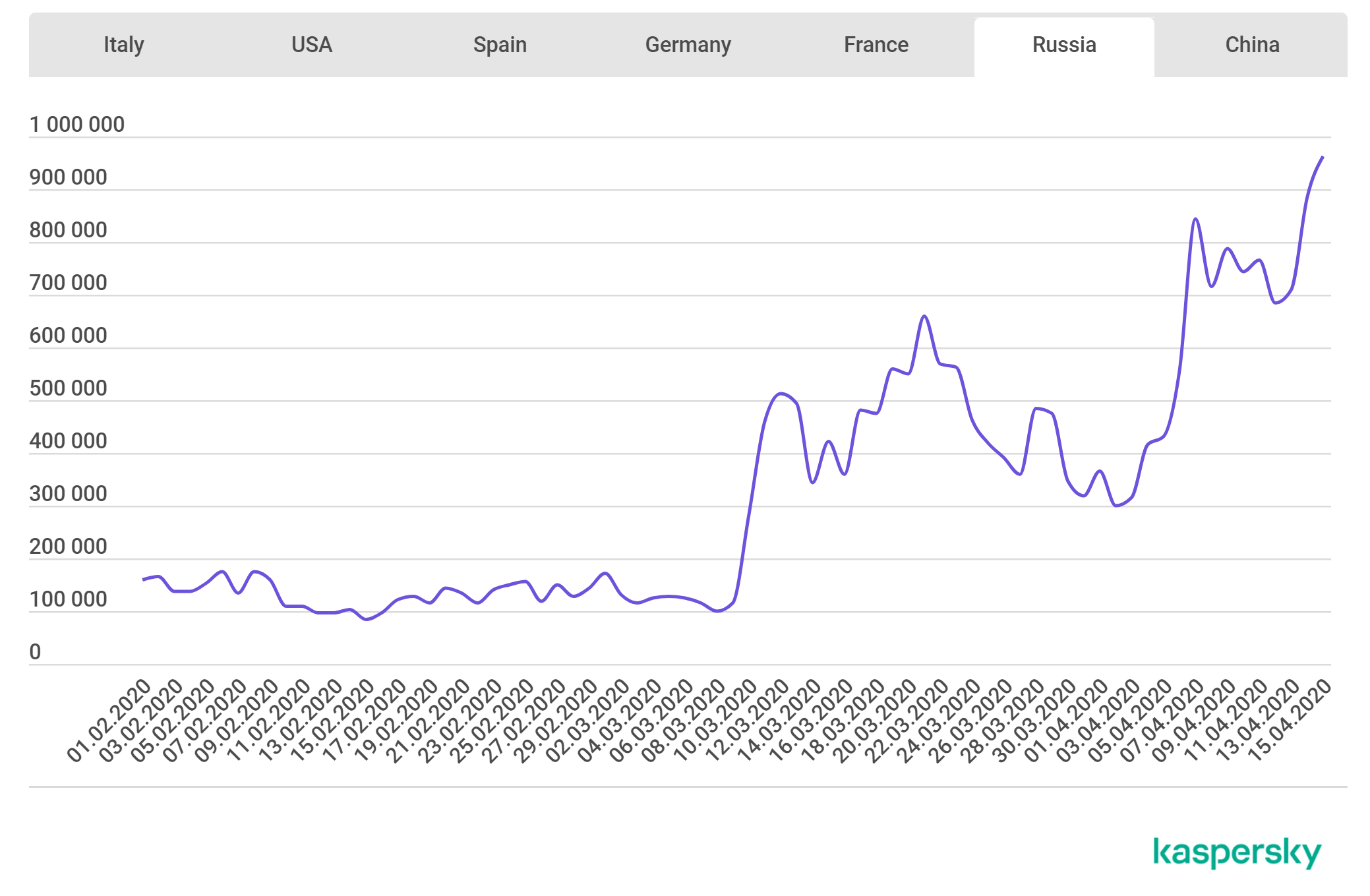
Often, security suffers because of this: access to servers previously open only when working from the office is opened, protection levels for VPN, mail and file storage are removed. Such a difficult situation could not take advantage of cybercriminals. The graph above shows exactly how this happens. It demonstrates the increase in the number of attacks with brute force attacks on RDP servers (by given Kaspersky Labs). This is Russia, the study also shows graphs for other countries, but the picture is the same: an increase in the number of brute force attacks at times.
Attackers use both common default passwords and frequently used code base databases. For a well-tuned corporate infrastructure, this is not a problem, but times are difficult, the load on IT specialists is high, and there are more opportunities to make a mistake. The recommendations are standard: use complex passwords, ideally do not make the RDP server accessible from the outside, use Network Level Authorization. Last year it was the NLA made it difficult exploitation of serious vulnerabilities in the protocol. It is advisable not to include RDP at all when such access is not really required.
What else happened:
Another vulnerability in WordPress plugins. In the Real-Time Find and Replace Extension discovered A CSRF vulnerability that could allow malicious script to be injected into a website. Three plugins with which you can create educational services based on WordPress (LearnDash, LearnPress, LifterLMS), have a number of vulnerabilitiesleading to the disclosure of information, changes in user ratings and elevation of privileges up to complete control over the site.
Databases of hacked Zoom user accounts are freely sold in the cyber underground. One of the first cases of the appearance of a fairly modest collection of logins and passwords registered in the beginning of April. Last week, access was already 500 thousand accounts. Databases are either sold very cheaply or are generally distributed free of charge. Due to the ephemeral nature of newsgroups, the main threat of such leaks is the development of an attack on other network services of the company. But there are other options: the Financial Times last week fired a reporter who wrote about financial issues in competing media. He became aware of these problems after he connected to a poorly protected web conference.





