Securing the GRUB Boot Loader on Linux
GRUB Boot Loader Security Value:
GRUB (Grand Unified Bootloader) is a key element when booting the Linux operating system. This process begins by executing BIOS code, which then transfers control to the GRUB boot loader. In the event of a bootloader security breach, attackers can gain access to the system solely by bypassing authorization, changing the configuration, or launching special modes, which can lead to serious consequences, including complete control over the system.
Securing the GRUB boot loader helps prevent such attacks by providing user authentication and protection against unauthorized access to the system at boot time. This approach provides reliable protection for the Linux operating system and helps maintain data integrity and confidentiality.
When the computer starts up, the first code to run is the BIOS.
This happens very quickly and a self-test is performed.
It then executes code in the Master Boot Record sector of the disk where the boot loader is located.
The bootloader then loads the kernel, which initializes the entire system.
Today, all major Linux distributions use GRUB 2 as their boot loader. A hacker can modify GRUB and boot the system into a special operating mode (called single user mode) where root logs in automatically without a password. An attacker can also use the GRUB editor interface to change its configuration or collect system information; or if it is a dual boot, the attacker could select a different operating system during boot that ignores access controls and file permissions.
To address these security issues, we will protect the GRUB boot loader with a password. Please note that people with physical access to the computer may be able to access files through other methods that GRUB cannot prevent.
One such method is to boot the system from another medium, such as a USB drive.
It's also worth setting a BIOS password and setting the system to automatically boot from the partition on which Linux is installed.
In fact, the first layer of protection you should consider is the physical protection of your computer.
To make the GRUB boot loader require a password to start the system, we must generate a hashed password using a specific command.
I am doing:
grub-mkpasswd-pbkdf2PBKDF2 is a password-based key derivation function.
And I enter the password.
And it generated a hashed form of the password.

After generating the hashed password, the next step is to edit the main GRUB configuration file and add the password hash.
This way your actual password is not visible in GRUB scripts and a possible hacker cannot see it.
The main GRUB2 configuration file is located in /boot/grub/grub.cfg
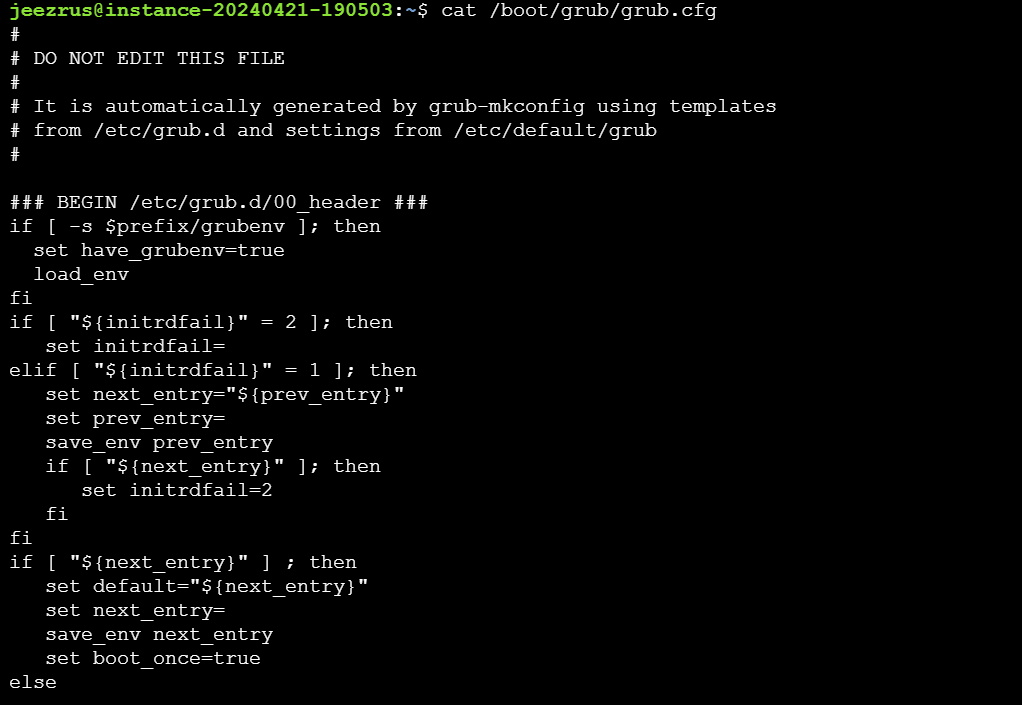
However, this file is not directly modified by the user. It is overwritten by certain GRUB updates when a kernel is added or removed, or when the user issues the GRUB 2 update command.
So, in fact, GRUB uses a series of scripts to build this configuration file, they are located in /etc/grub.d
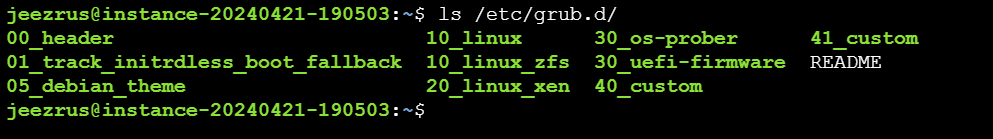
So we change the files in this directory and then run update-grub2.

This command, based on the contents of these files in /etc/grub.d, will generate grub.cfg, the main configuration file.
I prefer to change a custom file like 40_custom because it won't be overwritten even when the GRUB package is updated.
Let's look at the hashed password we just generated.

And I copy this line to the clipboard starting with grub.pbkdf2.
And as root, I open 40_custom, so sudo vim /etc/grub.d/40_custom and at the end of the file I add

set superusers="root"
password_pbkdf2 rootand insert the hashed password.

I save the file and exit.
The next step is to update the GRUB configuration file.
I'm running the update-grub2 command as root. This command will generate a new grub.cfg file.
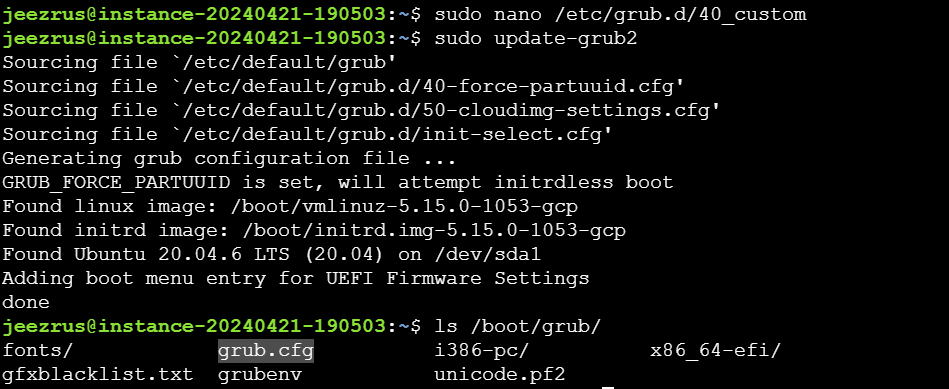
And here he is.
That's all! GRUB now asks for a password at boot; it no longer boots the system directly into the first OS. So I enter the username, which is root, and the password that I set.
And it loads the OS.
Material prepared in advance of the launch specialization “Administrator Linux”.