Reb, Blue, Yellow Team. Confrontation or partnership in cyberspace
Introduction
As they say, good afternoon! Today I want to talk to you about the so-called teams in the field of information security. Basically, this article is intended for those who are just starting their journey in this direction or simply have not yet decided which of the “teams” they want to join. The entire classification is quite arbitrary and only you yourself can determine what you will do. To back up your words, you should refer to the “command palette”
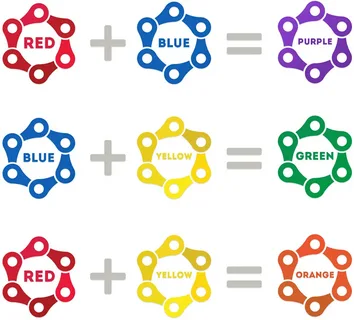
A little later, explanations will be provided for each of the main teams, but based on the above image we can conclude that the teams and their joint activities only complement each other and create new teams.
Briefly about the main thing
Red, Blue, Yellow Team are terms used in the information security field to refer to various teams of specialists dedicated to protecting computer systems from cyber attacks.
Red (from the English Red Team) is a team that simulates the actions of attackers and conducts penetration testing of the system. The goal of the Red Team is to find vulnerabilities in the system and suggest ways to eliminate them.
Blue Team is the team responsible for protecting a computer system from real cyber attacks. She is involved in system monitoring, threat detection and prevention, and security incident response.
The Yellow Team is a team that works to improve an organization's security processes and policies. Its goal is to develop and implement measures to improve the level of information security.
All of these teams play an important role in ensuring the information security of organizations. They help identify weaknesses in systems, develop security strategies, and train personnel in the safe use of information technology.
History of origin

Red Team appeared in the mid-20th century in the context of military strategy. These were groups of specialists who simulated enemy actions and conducted exercises to test the readiness of troops to repel an attack. Over time, the Red Team concept was adapted to the information security field.
In the 1970s, with the development of computers and networks, the first cyber attacks began to appear, and the need to protect against them became obvious. At the same time, the first Red Teams began to form, which were engaged in penetration testing of systems and searching for vulnerabilities.
In the 1980s, Red Team began to be actively used in military and intelligence structures to train personnel and test the effectiveness of security systems. At this time, the first methods and standards for conducting Red Team exercises were developed.
In the 1990s, with the development of the Internet and global networks, the number of cyber attacks increased significantly, and Red Teams became an integral part of the information security of many companies and organizations. Specialized Red Team training centers were created and new techniques and tools were developed for conducting penetration testing.
Currently, Red Team continues to develop and improve. With the advent of new technologies and threats, new methods and techniques of Red Team work appear. Today they are used not only in the military sphere, but also in business, government administration and other areas where a high level of information security is required.
Blue Team arose later, at the end of the 20th century, when information technology began to actively develop and the first serious cybersecurity threats appeared. Blue Teams have begun to form in large corporations and government agencies to protect their computer systems from real-life cyberattacks.
In the early 1990s, with the development of the Internet and global networks, the number of cyber attacks began to increase, and companies realized the need to create special teams to protect their systems. At this time, the first Blue Teams began to form, which were engaged in monitoring systems, detecting and preventing threats, and responding to security incidents.
In the 2000s, with the development of cloud technologies and mobile devices, the number of cyber attacks continued to increase, and Blue Teams became an integral part of the information security of many companies and organizations. During this time, new methods and tools were developed to detect and prevent threats, as well as to respond to security incidents.
The Yellow Team began to develop in parallel with the Blue Team, but its main task was not directly countering threats, but working to improve processes and security policies in the organization. This was due to the understanding that effective protection requires an integrated approach and continuous improvement.
In the early 2000s, with the development of cloud technologies and mobile devices, companies realized the need not only to protect against threats, but also to improve their security processes. At this time, the first Yellow Teams began to form, which were engaged in analyzing vulnerabilities, developing security policies and training staff.
In the 2010s, with the development of social networks and Big Data, the number of security threats increased significantly, and Yellow Team became an integral part of the information security of many companies and organizations. During this time, new methods and tools were developed for vulnerability analysis and security policy development.
To summarize, we can draw the following analogy. The red team is a team that imitates enemy actions, the blue team is a team of defenders who constantly fight against attackers, and the yellow team is a team that sets up security policies and works directly with staff.
What's the difference?

Red, Blue, Yellow Team have their own differences in goals and methods. Let's look at each of these aspects in more detail.
First of all, it is necessary to note the obvious difference in the work goals pursued by each of the teams. They are aimed at various aspects of the information security of the system, which allows for full coverage of the range of possible threats.
Methods:
Red Team: Uses various techniques and tools to simulate cyber attacks and test systems for penetration. This may include social engineering, exploits, and other hacking techniques.
Blue Team: Uses threat monitoring and detection techniques such as intrusion detection systems (IDS), antivirus software, and other security tools. They also conduct log analysis and respond to security incidents.
Yellow Team: Uses methods to analyze vulnerabilities, develop security policies and train staff. They can conduct security audits, assess risks and develop plans to improve security. All three teams play an important role in information security, using different methods and approaches to work.
A brief excursion into related teams
Purple team is the synergy of red team and blue team. In a purple team, both teams work together to achieve a common goal – keeping the organization safe.
A purple team may include cybersecurity specialists such as analysts, security engineers, penetration testers, and other experts. They use a variety of tools and techniques to analyze system vulnerabilities, develop security strategies, and conduct regular security audits.
The main goal of the purple team is to increase the level of security of the organization by identifying weaknesses in the security system and developing effective measures to counter possible cyber attacks.
The Green team is a specialized cybersecurity unit that focuses on ensuring sustainability and the organization's practices comply with industry standards, regulations and compliance requirements.
Green team tasks include:
Continuously monitor the organization's security posture: Team members monitor the organization's current security posture by analyzing its systems and processes to identify potential vulnerabilities and risks.
Conducting Audits: The Green team conducts regular audits to assess the organization's practices against industry standards and compliance requirements. This helps identify weaknesses in security systems and suggest improvements.
Compliance and Risk Mitigation Recommendations: Following the audit, the Green team provides compliance and risk mitigation recommendations. This includes suggestions for process improvements, staff training and the introduction of new technologies to enhance security.
The Orange team consists of cybersecurity experts who have experience in threat intelligence and proactive threat hunting. Their job is to collect data from various sources, including cyber threat intelligence channels. This data helps the team understand the tactics, techniques, and procedures used by potential adversaries.
The Orange team uses this data to proactively adjust security measures and proactively identify potential threats before they become real risks. This allows an organization to be prepared for possible attacks and take appropriate measures to protect its assets and information.
In addition, the Orange team can conduct attack simulations to test the effectiveness of security measures and identify possible security weaknesses. This helps an organization improve its security and prevent possible information leaks or damage.
Examples of successful operations
Red Team: In 2017, Facebook's Red Team conducted penetration testing of the system and discovered a vulnerability that could allow attackers to gain access to user accounts. Thanks to the timely discovery of this vulnerability, the company was able to fix the problem before it led to serious consequences.
Blue Team: In 2014, Target's Blue Team successfully thwarted a major cyberattack that could have exposed sensitive data to millions of customers. Thanks to a quick response and effective protection measures, the team was able to stop the attack and protect customer data.
Yellow Team: In 2018, Google's Yellow Team implemented a new security policy that reduced the number of data breaches by 50%. This policy included security training for employees, regular systems audits, and updated data access policies. These are just a few examples of successful Red, Blue, Yellow Team operations. Each team has its own unique achievements and successes in the field of information security.
Conclusion
Collaboration and interaction between the Red, Blue, Yellow Team plays a key role in ensuring information security. Here are a few reasons why this is important:
A complex approach: Each team has a specific role and focus, so working together leverages each team's strengths to create a comprehensive approach to information security.
Resource optimization: Collaboration optimizes the use of resources such as time, money and human resources. For example, the Red Team can work together with the Blue Team to identify the most critical vulnerabilities and prioritize remediation efforts.
Information exchange: Collaboration between teams allows information to be shared about current threats, vulnerabilities, and information security best practices. This helps all teams stay up to date with the latest trends and develop their skills.
Increased efficiency: Coordination between teams improves the performance of each team. For example, Blue Team can use Red Team testing results to improve their threat detection and prevention techniques.
Education and development: Collaboration between teams provides opportunities for learning and development. Teams can share experiences, conduct training and seminars to improve their information security skills and knowledge. Thus, cooperation and interaction between the Red, Blue, Yellow Team is a prerequisite for ensuring effective information security in organizations. I hope this article helped you decide what specific teams are doing and, based on the facts presented in the material, make a choice in which direction to develop.