How we learned to bypass VPN blocks in China to be ready for RKN
On Monday, August 7, many VPN users in Russia noticed problems connecting to servers. The picture was contradictory: subscribers of one operator could have a VPN, or maybe not, in one region some users had difficulties connecting, while others did not experience technical problems. This is the second significant wave of blocking this year.
According to the information collected in social networks and Telegram, the restrictions affected the most common VPN protocols OpenVPN, L2TP, PPTP and WireGuard. Clients of mobile operators complained about failures in the operation of VPN services – Megafon, MTS, Beeline, Tele2, Yota, Tinkoff Mobile.
Deputy Chairman of the State Duma Committee on Information Policy, Information Technologies and Communications Anton Gorelkin commented to the mediathat “the use of VPN services is not prohibited, but Roskomnadzor is obliged to restrict the work of those who violate the law” – that is, it allows access to sites and services blocked in Russia, the list of which currently includes not only political and news resources, but also the largest social networks.
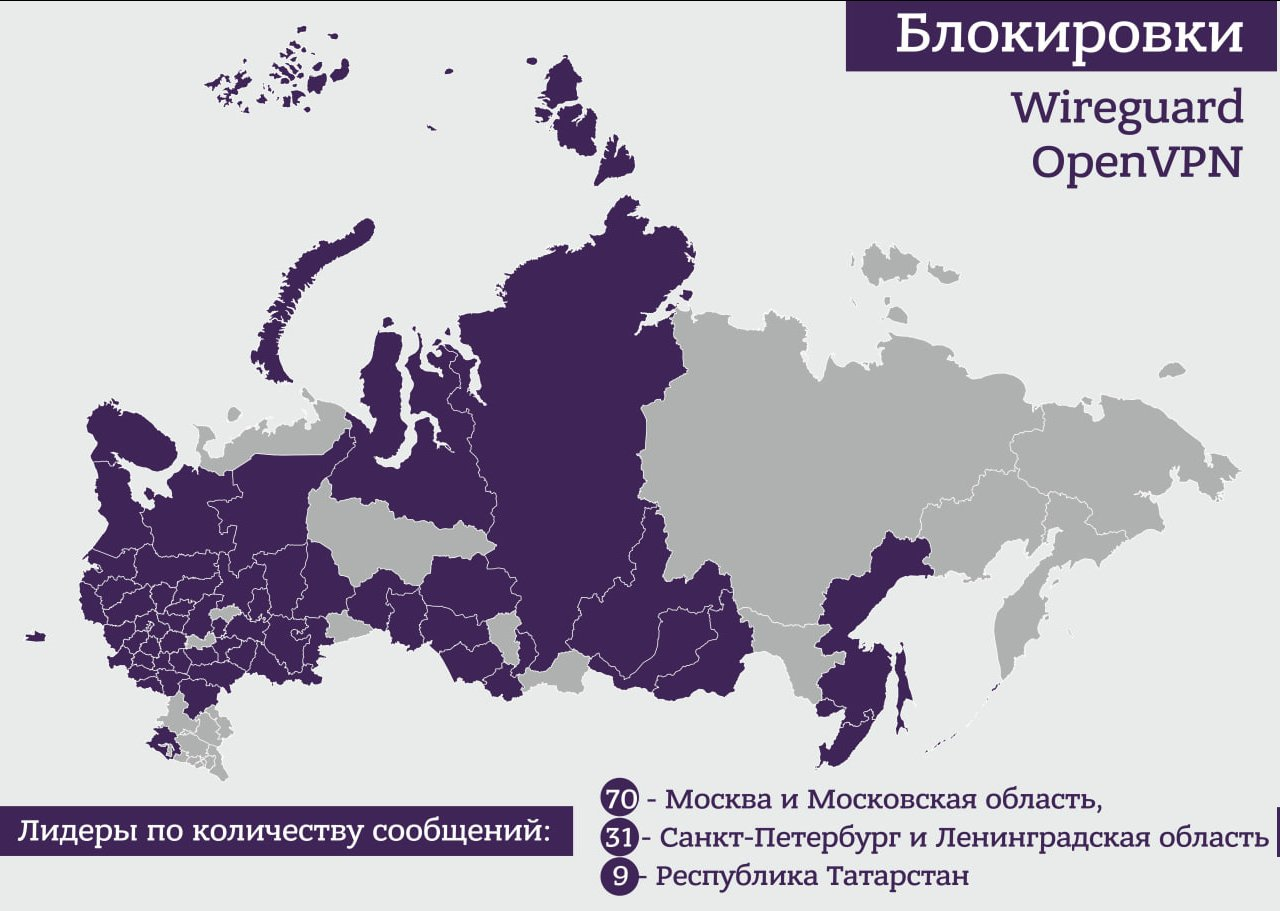
On the same day in the evening, the creator of the AntiZapret lock bypass service @ValdikSS told, that connections from Russia to servers abroad are mainly blocked for subscribers of mobile operators, and that these blockings are noticeably different from what they used to be. This time, it was not popular commercial services that were available to everyone who came under attack, but private servers that users independently configured from foreign providers. The nature of the blocking has also changed: now Roskomnadzor, using DPI and TSPU, evaluated the type of traffic and immediately blocked it if it determined it to be a VPN connection. The popular protocols WireGuard, L2TP and OpenVPN are blocked. According to the technical director of Roskomsoboda and the founder of Privacy Accelerator Stanislav Shakirov, these were “not stupid blocking”. In his opinion, the censors are trying to make sure that the VPN blocking affects only individuals, but does not affect the work of corporate clients.
On the same day, a huge number of tickets fell on Xeovo, but by the evening, when information about a new wave of VPN blocks was still spreading across the Russian Internet, and the media were still collecting the statistics that we present here, we had already closed most of them and the connection of our clients was restored. How did we do it? We were preparing for this.
About a year ago, Xeovo faced the task of not only providing classic VPN protocols, but also adding stealth proxies. They disguise VPN traffic as plain HTTPS, allowing you to bypass DPI.

There were two reasons for this:
Sooner or later, more and more countries will start blocking them. They block very easily.
In some markets, we use the slogan “Silence censorship. Protect your privacy and bypass restrictions with Xeovo” in advertising – which does not work when you cannot provide services everywhere 🙂
The WireGuard protocol is blocked very easily. OpenVPN is a little more complicated, but in general, both options are amenable to blocking without much difficulty. To date, the leaders of VPN blocking are Russia, China, Uzbekistan, Iran, Egypt and Turkmenistan. The last one stands out in particular: they simply blocked everything and introduced whitelists – here we have lost so far, you can compete for other markets. But we will return to the issue of Turkmenistan.
Will work in China – will work everywhere
As a milestone, we decided to set ourselves a difficult but understandable goal: Xeovo VPN should work in China – and if we can achieve this, then there should be no problems with other countries.

In part, this turned out to be true: our experience of bypassing the “Great Firewall of China” really prepared us for a heavy wave of blocking in Russia this week. On the other hand, each market still has its own nuances – not all the experience of fighting Chinese censorship is transferred to other countries, and other countries require their own specific solutions.
For a successful start, we decided to take as many available and proven protocols as possible (Shadowsocks, VLESS, VMess and Trojan).
Because of such a large arsenal, the first problems began with testing working client GUIs and compiling user instructions for each operating system. There are a lot of clients and most of them work about the same, but there are still exceptions, for example, clients like Clash and Surfboard. The VLESS protocol on MacOS had particularly poor support at first, but now the situation has improved and Nekoray has appeared.
It’s a big hindrance that there are constantly many new protocols that need to be reviewed / tested every year, because they are no longer supported and simply abandoned in the end. Although the trend of new protocols constantly appearing is annoying, this is because censorship finds ways to block new protocols. So this battle continues: if one head of the hydra is cut off, two will grow, and then we will deal with all this zoo.
The second problem was with the documentation. Sometimes we just wasted time reading the broken English documentation for a particular protocol, when initially it was necessary to immediately start with the Chinese version. For the most part, the documentation is either incomplete or not updated, there have always been problems. At some point, we even planned to hire a programmer with knowledge of Chinese to make life easier, but we managed somehow ourselves through DeepL Translate.

After all the testing and launch phases, we have already begun to optimize our generator. It was very important to add a subscription for each client, a file that can fetch all new servers that we add and works in all popular clients. This is a particularly handy and important feature if IP addresses are often banned.
After all the bug fixes and features, we ran into good difficulties: our IP addresses began to be blocked by GFW like hot cakes, great firewall of china. It was a sure sign that our service was working as it should – a direct feedback that we were ready for.
The first strategy we decided to try was to change the IP addresses for the exit nodes. In the end, this turned out to be an ineffective and costly strategy (which we still sometimes use).
In the beginning, it worked well and IP addresses lived for weeks, got quarantined and left the block after a couple of weeks. Then it turned out that GFW uses a rather clever approach to blocking IP addresses and they rarely stay in the bath forever. The more often an IP address is quarantined, the longer it will stay there.
We solved the solution of blocking IP addresses with the help of CDN: in short, the IP address is hidden behind the CDN and does not fall into the block. China avoids blocking large CDN providers. The only disadvantage of this method is the connection speed and stability in general. So it’s still not a panacea, but so far the most effective method we’ve found. If you are interested in more technical details, we advise you to read Great Firewall Report (how exactly blocks China).
The next dilemma with China was the separation of protocols. All the protocols we provide can work in China, but not all of them are designed for mass use. The more users connected, the more likely that GFW will detect that there is a connection to the proxy and block the IP address. The region and provider also play a role. Some regions track VPN usage much more passively and worse than others. Users from some Chinese regions even reported that WireGuard worked for a while 🙂 As a result, for users who connect from China, we left VLESS and VMess.
After that, we discovered another difficulty – a positive difficulty, which can be perceived as an exam and a test of your service: during political events / elections Communist Party turns on as much as possible censorship machine. Roughly speaking, everything and everything flies into the block – even users who individually deploy proxies. We could not cope with this problem, and we call such incidents black days. Here it’s already as lucky – it can carry it through and the proxies will work, but with a 90% probability they will block everything, including the CDN.

A more serious and difficult problem was the selection of a suitable hosting provider, because we have our own minimum standards and many of them did not fit. Most of the suitable providers are underground, about which there is zero information and trust. There is no need to talk about standard security practices at all. In addition, we do not take servers in China/Hong Kong for obvious political reasons.
The second point is Chinese providers. Roughly speaking, you need a CN2 network for a comfortable connection if you are in the Russian Federation. For ourselves, we have found the best suppliers in South Korea, Taiwan, Japan and Singapore.
The final issue is the cost of fighting censorship in China. Traffic is more expensive for us than we expected, because we do not limit it – users are limited only by the speed of the channel and how much they can squeeze out of it. In addition to traffic, an additional cost is the frequent change of providers / IP addresses / payment for CDN.
The cost of traffic in South Korea with an optimized channel for China for clarity
In general, this product turned out to be unprofitable for us, but we continue to work in China and optimize costs. We see our fight for the Chinese user more as an investment than a loss.
Other countries followed China. The biggest activity was from Iran. In general, the practices are the same as in China, but their processes are much worse delayed and they often blocked everything. Well, in any incomprehensible situation, the ayatollahs can simply turn off the Internet in the country.
We will work in Turkmenistan – we will work everywhere
The next milestone that we have set for ourselves is to open the Internet to users from Turkmenistan. Turkmenistan is the endgame in terms of Internet censorship, the country has whitelists in fact. This situation is more difficult than in China, than in Russia, than in the Arab countries – than anywhere else on the planet, with the exception of the DPRK, where an intranet operates instead of the Internet.
For some time, we had stealth proxies in Turkmenistan, but then a rather little-known provider got banned with its entire ASN – and now we are looking for ways to resume work and help people bypass the blocking. All we can say is that the methods will be non-standard, out of the box, we will go beyond our borders. And we will also work and fight censorship in the Russian Federation.
Xeovo VPN also plans to increase the infrastructure for the proxy. Now we are testing XTLS Realitywhich will be very useful for users from Iran.
It also plans to develop its own monitoring of IP addresses for blocking in China, Iran, the Russian Federation and other countries.
And we are working on a modified Raspberry Pi, which we plan to send free of charge to our customers. This will help you respond faster to blocking.
Text author: Xeovo,@EgorKotkin
Illustrations: Anton Dmitriev






