How to screw up phishing: tips for pentesters
Hello, my name is Dmitry Semyanov, and I am a penetration testing specialist at Innostage. Our team regularly conducts phishing mailings for our company and our customers. Over a long period of work, we have accumulated a lot of big shots, both our own and those of others, overheard on the sidelines (these stories are included with the approval of the owners). We will be happy to give you bad advice so that you can get the same ones. Of course, these are not all the troubles that a specialist may encounter when carrying out phishing, but we have touched on the most basic and unpleasant ones. Good pentesters are prohibited from reading!

Lose some of the valid accounts by composing them from the found names
The preparation of a phishing campaign is based on open source intelligence (OSINT) techniques and tools. We strive to organize a campaign so that its preparation process is similar to the actions of a potential attacker. Therefore, we transfer the names that we found as part of the work to the mailboxes to which letters will be sent in the future.
Problems arise due to the fact that the Russian alphabet has as many as 7 more letters, and the pronunciation of some sounds can be phonetically represented in English by no less than two or more letters. How would you transliterate the name Chichikov? And Erokhin? Or Gushchin?
What to do? It is worth considering this nuance, especially when working in regions where phonetically complex surnames or given names are often found. It is better to pre-select the email format for employees of a certain company, so that you can then translate the employees’ full names into English without errors.
The same surname can look different in different companies, for example, the surname Ismailov will look like this:
Company A: Ismagilov | Company B: Ismayilov | Company B: Ismailova |
And the last name is Valiakhmetov:
Company A: Valiakhmetov | Company B: Valiachmetov | Company B: Valiahmetov |

OSINT does not end with mail search: it continues in the mind of the analyst, who, based on the goals of OSINT, must not only collect information from various sources, but also conduct analysis, as in the current example with transliteration of names, and pass it on to the rest of the team for use.
Come up with a great phishing domain and not use it
I’ll tell you a secret, you won’t be the only one who will come up with the perfect phishing domain by changing one letter in the name of the resource being copied.

With the increase in the quantity, quality and volume of leaks, the trend towards more frequent phishing attacks develops naturally. Before registering a domain with your chosen broker, I strongly recommend checking the presence of the domain in spam lists – you will be surprised how many like-minded people you have.

But that's not all. In addition to the fact that the rented domain may be banned, you may be unlucky when ordering a virtual server: they are often used by not the most respectable people with not the best intentions, for example, for spam mailings. Such virtual servers will not lead us to successful phishing, but to loss of time and money. Unfortunately, you will be able to find out this after payment, when you receive the IP.
Check the IP address for blacklists immediately after receiving it, not after you have configured the entire infrastructure.
In addition, you need to check whether the provider is blocking any ports by default before renting, so that there are no unpleasant surprises. Pay special attention to ports 25, 465 and 587, as these are the ones that are required for the mail server to function properly and send phishing messages.

Send a lot of emails and get them back
The phishing technique differs depending on the context of the work. If we are testing employees for resistance to various socio-technical manipulations, then it is important to make sure that the malicious letter and/or attachment reaches the recipient’s mailbox and does not get stuck in the email security information.
Conducting phishing while fully informing the party being tested is not the same as carrying out the same work while simulating the actions of attackers (for the purposes of this article, we’ll call it RedTeam). These works have slightly different final goals, despite similar methods of implementation. It is worth remembering: we are not trying to penetrate the perimeter of the company to develop an attack inside. With RedTeam, you won’t be able to ask to add a mail server and domain to the white-list on the receiving side, see how the letter is displayed in the inbox, whether it has a warning about an external sender, and whether it’s included in “Unwanted Messages.”
Therefore, if you are carrying out phishing for a client, and there is an opportunity to do all this in advance, then you should do this without hesitation. It will be a shame if the local admin, afraid of an attack, blocks you, and the work will be completely failed.

Fly to the ban at the speed of sound
Of course, before the premiere, you want to check everything yourself, make sure that everything works correctly and does not arouse suspicion. And then the thought immediately comes to mind: “I need to send myself a letter and see what it looks like.” You can directly to your personal gmail, mail or icloud. And if you don’t understand the catch now, then I have bad news for you:

Unfortunately, in this case one can only sympathize. Laundering a domain will be much more difficult than registering a new one and setting up a new mail server. You can start.
Until recently, it was possible to send a regular letter from a mail server to even gmail, check availability and correct settings. Now you can get banned for a regular letter with a greeting, even without spoofing the sender.
Flying on red
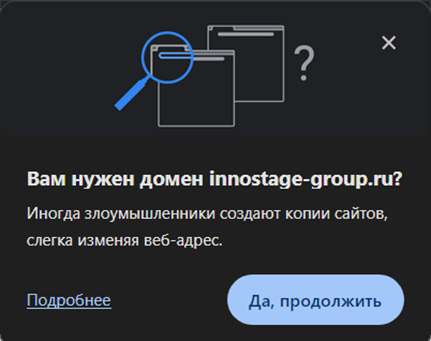
When conducting attacks with a fake page and an authentication form on it, you can seriously scare users with such a canvas.

The fact is that by completely copying a site with all its elements, we can lay a mine for ourselves. Google recognizes the substitution using its Safe Browsing system; the browser warns users that they are facing a dangerous site. And believe me, this is not a scenario in which everything will go smoothly for you.
Domains maneuvered and maneuvered…
During its operation, Google Chrome checks the domain name you are visiting with your browser history and uses regular expressions to look for matches. When it finds a match, it can either issue a notification that the user may not notice, or it can give away the phishing domain entirely. The use of a third-level domain partially saves you from this, but at this stage a lot depends on chance.
Today I tried to guide you through the dangerous quicksand of the world of corporate phishing. We have offered you some harmful tips that, of course, should not be used. However, despite the humorous tone, each of them carries a grain of useful experience and pain.
I hope that my experience and the experience of my colleagues will help you avoid many troubles. Remember, as in life, it is important to learn from the mistakes of others to make your path easier and more interesting. Be careful and professional in your work. Remember that where comfort begins, safety ends.