Hackers can remotely hack into smart garages around the world

A security researcher has discovered a number of vulnerabilities in Nexx smart garage openers. And now it can remotely find the necessary garages, and then open them at any time via the Internet. Another hello to smart technologies!
According to the findings of security researcher Sam Sabetan, who published on Medium, hackers can remotely connect to and control any garage door opener due to a number of security vulnerabilities that Nexx stubbornly fails to patch. Sam has been contacting the company since January, by any means possible, but they refuse to answer.
At the same time, vulnerabilities pose a serious danger to Nexx users: attackers can see their address and open their house or garage, and they will remain completely unaware of this.

Nexx says it sells “easy-to-use products that work with the things you already have.” That is, neither the garage nor the doors have to be changed. The product simply connects to an existing garage door opener – and allows it to be activated remotely via a smartphone app. “Life is complicated. You don’t have to worry about leaving the garage door open either. Get peace of mind!” the company advertises on its website.
Nexx also hosts successful campaigns on Kickstarter, promising “convenient and smart security”. They write that “All Nexx products are secured with the latest encryption technology running on US cloud servers and backed by a US company. The Nexx app was developed by our US engineers and is regularly updated to meet the latest security standards for IoT devices.”
In the meantime, as it turns out, her Smart Garage controllers can be searched and opened by email address, device ID, or just name and initials. All Nexx devices are affected by the vulnerabilities described below, up to and including the doorbell. It is estimated that more than 40,000 devices located in both residential and commercial premises are affected. In Russia, Nexx devices are also sold, turn on top lists, plus you can easily buy them on Aliexpress for $80.
How to hack a garage in 5 minutes
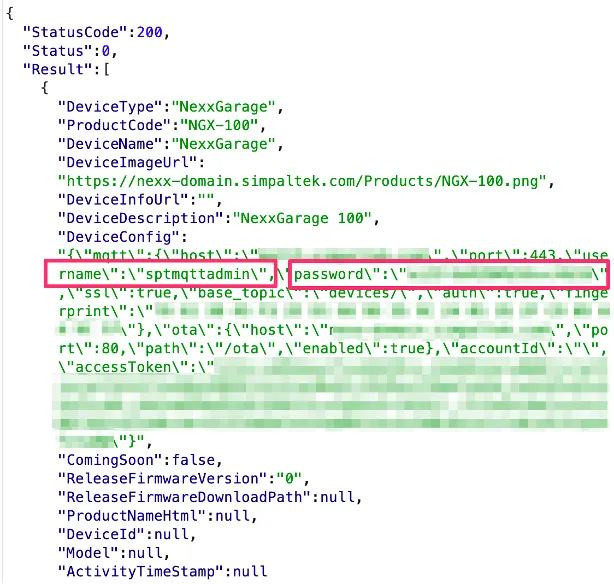
Mobile application Compatible with both Android and iOS, Nexx Home helps users set up their new devices. Everything happens through the Nexx Cloud, a cloud that verifies the smartphone and gives it access to devices by sending the password from them. The request to the cloud to get the credentials is just an API call in the mobile application, and the password for a specific user is returned via MQTT.
MQTT (Message Queuing Telemetry Transport) is a lightweight messaging protocol designed for resource constrained devices and networks with low bandwidth or high latency. Ideal for garages and IoT! MQTT helps ensure a reliable connection between the device, the user, and the cloud. For example, a garage door opener regularly sends messages such as status updates, alerts or notifications to a central system. And she then collects statistics and distributes information among subscribed clients.

In MQTT-based IoT devices, it is critical to use unique passwords for each specific device to ensure a secure communication environment. However, in the case of Nexx, all devices appeared to be using a universal password, compromising the overall security of their system. Moreover, it was sent back to the user’s smartphone via MQTT, and it could be easily intercepted.
The use of a universal password for all devices is a significant vulnerability because unauthorized users can gain access to the entire ecosystem by obtaining this common password. In doing so, they can compromise not only the privacy but also the security of Nexx customers by controlling their garage doors without their consent. Imagine if the garage door suddenly closes abruptly when you pass under it!
In addition to being widely available in the Nexx API and in forwarded messages, the hardcoded password is also available in the firmware shipped with the device. In general, only the blind can not find it. It is strange that all this has not exploded in the years that Nexx has been in the market.
To make sure he wasn’t dreaming, Sam Sabetan used the credentials he found to access the Nexx MQTT server. Upon gaining access, he discovered that all MQTT messages are broadcast to all devices, including even those messages that were intended for other clients and devices.

User email addresses, device IDs, and names with initials are sent in the “garageDoorOpener” message. One can easily identify the company’s customers based on the unique information contained in these messages. However, the real danger is that by playing the “garageDoorOpener” message, an unauthorized user can send a command to the customer’s garage door to either open or close it.
What’s more, this security vulnerability extends beyond garage door openers to the Nexx Smart Plug ecosystem. By playing messages on the same MQTT server, unauthorized users can turn on and off smart plugs connected to various household appliances, including even CCTV cameras. The possibilities for evil trolling are almost unlimited.
No answer
Sabetan filmed video evidence of this entire hacking process. They show him first opening his own garage door, as expected, using the Nexx app. Then enters the tool to view the messages sent by the Nexx device. Closes the door using the application and captures the data that the device sent to the Nexx server during this action.
At the same time, Sabetan receives not only information about his own device, but also messages from 558 other devices that do not belong to him, but sent data at about the same time. Now he can see the device IDs, email address and name associated with each one.
Sabetan then plays the command back to open the garage through the software instead of through the application, and his door opens again. With such a simple technique, he was able to remotely open the garage doors of other users. And even control their smart plugs and all other devices that receive information from Nexx cloud servers.

Hackers can randomly open doors and control electronics around the world, endangering the lives and property of users. In order to somehow counter this, Sabetan wrote to the company’s technical support, and then in general to all the addresses that he could find, but did not receive a response. He also says that the U.S. Cybersecurity and Infrastructure Security Agency (CISA) told him that it also tried to contact with the company, seeing a potential threat. But the company has not yet responded to them and has not been able to fix the vulnerabilities. All of them are still available to hackers if they want to use them.
After another email to Nexx’s security team went unanswered, Sabetan contacted the company’s support team again – only this time saying he needed help with his own product. This time the support staff responded. But when they found out what the situation was, they stopped communicating. So far, the situation remains unresolved.
At the end of his post Sam Sabetan recommends that if you are a Nexx customer, turn off all your devices immediately and contact the company so they can advise you on the next steps. And in general – less use of smart devices that protect your doors and garages until the situation with this and other products clears up.




![[Пятничное] 10 Surprisingly Spectacular Simplest Cellular Automata](https://prog.world/wp-content/uploads/2023/02/a42616afa8838c3108c409c28b518099.gif)