Fortinet Single Sign-On. Description of technology

Hello! Throughout the entire time of our work with the company’s solutions Fortinet, and in particular with a new generation firewall FortiGate, one of the most interesting questions is the control and tracking of traffic of individual users or groups of users. Today we want to tell you in detail about the mechanism of transparent user authentication on the firewall. FortiGate using Fortinet Single Sign-On technology. This article will be devoted specifically to the theoretical aspect of FSSO, since in this case it is difficult to understand what is happening in practice without theory.
Single Sign-On (SSO) is a mechanism that allows authenticated users to access various resources on the network without re-authentication. When working with the FortiGate firewall, SSO is implemented using FSSO (Fortinet Single Sign On) – a set of software agents that allows the FortiGate device to identify network users and thereby control their access to network resources, as well as monitor the traffic of various users. When a user is authenticated to a domain, the FSSO agent sends the user’s name, IP address, and a list of groups to which the user belongs to FortiGate. FortiGate uses this information to allow or deny this user access to network resources. FSSO is commonly used with directory services such as Windows Active Directory or Novell eDirectory. FSSO depends on the directory service used. In this article we will look at FSSO for Windows Active Directory (AD).
FSSO for Windows AD uses an agent collector. Agents for Domain Controllers (DC agent) can also be used, depending on the mode of operation of the agent collector. There are two main modes of operation: DC Agent Mode (the mode in which DC agents are used) and Polling Mode (in this mode, only the collector agents are used). Also, FortiGate can use Polling mode, which does not require the installation of third-party agents on the server. However, this option is only suitable for simple networks with a minimum number of users.
Let’s start with DC Agent Mode. This mode is recommended for FSSO. It requires:
DC agent installed on each domain controller – if there are several domain controllers in the network, the agent must be installed on each of them;
The Collector Agent is the second FSSO component installed on a Windows server that is a member of a domain. It collects events received from agents for domain controllers and forwards them to FortiGate. He is also responsible for verifying groups and checking workstations for user logout. The agent collector can send information about local security groups, organizational units, and global security groups to FortiGate. Also, the collector agent can be configured to perform DNS queries.
The scheme of FSSO operation in DC Agent Mode is shown in the figure below:
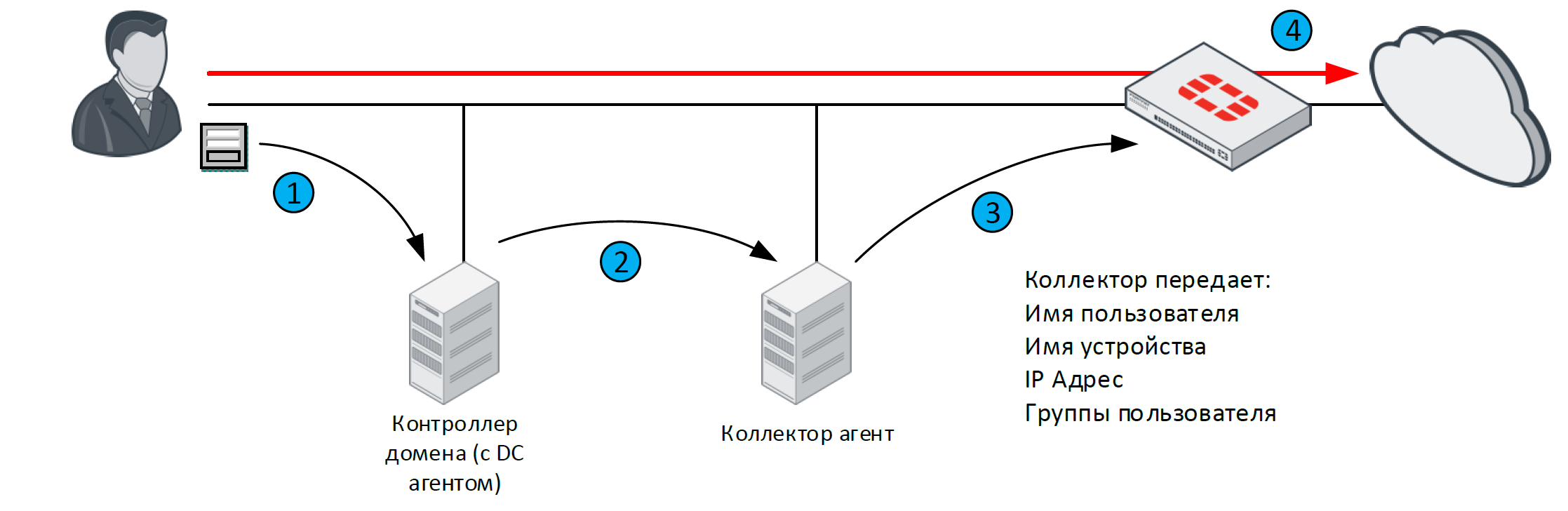
When a DC user is authenticated, the agent intercepts the logon record on the domain controller.
The DC agent then performs a DNS query to determine the user’s IP address and transmits the information to the collector. After the collector receives the information, it performs a DNS query again to determine if the user’s IP address has been changed.
After that, all information about the user is transferred to FortiGate.
After the collector has transferred all the information about the user, FortiGate knows this user, his IP address and the groups to which he belongs. When a user tries to access the network resources of interest (including the Internet), FortiGate compares the source IP address with the IP addresses in the list of active FSSO users. Since the user is already authorized in the domain, and FortiGate contains information about him, the user will not be authorized again. Instead, the access of this user to the resource of interest will be allowed or denied depending on the security policy under which the traffic of this user falls.
Let’s move on to the second mode – Collector Agent-Based Polling Mode. This mode does not require the installation of DC agents on domain controllers. However, the requirements for installing the agent collector on a server or servers belonging to the domain remain. In this case, the collector agent periodically polls the domain controllers for user log-on events. Various methods can be used for this:
NetAPI: The agent accesses temporary sessions created on the domain controller when users log on to the domain and calls the NetSessionEnum function. This method is faster than the others, but it can miss some logon events when the domain controller is under heavy load. This is due to the fact that under high load, sessions can be deleted from RAM before the agent has time to access them and transfer information to FortiGate.
WinSecLog: The agent accesses all security event logs on the domain controller. In this case, it will not miss any user logon events, since security event logs are usually not deleted. However, when transferring information to FortiGate, delays are possible – the main reasons are the large volume of the network, as well as the slow speed of logging. This method is the most common.
WMI: The agent uses the Windows API to obtain system information from the domain controller. The domain controller returns all required domain logon events upon request. This method reduces the load on the link between the collector agent and the domain controller.
The scheme of the Collector Agent-Based Polling mode is shown in the figure below:

The user authenticates to the domain by providing their credentials to the domain controller;
The collector agent periodically (every few seconds) polls the domain controller for user logon events to the domain;
The collector agent sends the received information to FortiGate;
Since the user is already authorized in the domain, and FortiGate contains information about him, the user will not be authorized again. Instead, the user’s access to the resource of interest will be allowed or denied, depending on the security policy under which this traffic falls.
And the third mode that we will look at today is Agentless Polling Mode. Its operation is similar to the previous mode, however, instead of using the agent collector, FortiGate polls the domain controller on its own. Because of this, there are a number of limitations:
Requires more system resources;
Only two events are polled – ID 4768 and ID 4769. The SMB protocol is used for this;
There are no additional features that can be used if an agent collector is available, for example – checking end stations.
The scheme of operation of this mode is shown in the figure below.

FortiGate polls the domain controller for user logon events.
After the user has authenticated to the domain controller, FortiGate receives this event during the next poll along with the following information: username, machine name, IP address. Then, he queries the groups of users about whom he received information.
When a user tries to access a network resource, FortiGate already has all the necessary information about that user, and the user does not need to re-authenticate. Instead, the user’s access to the resource of interest will be allowed or denied, depending on the security policy under which the user’s traffic falls.
Let’s summarize, highlighting the main differences between DC Agent Mode and Polling Mode:
FSSO in DC Agent Mode is more difficult to install. It requires the installation of an agent collector as well as an agent DC on each domain controller that monitors logon events. But at the same time, this mode is more scalable, since the work of capturing input events is implemented by DC agents, which transmit this information to the agent collector.
In Polling Mode, the collector needs to poll each domain controller every few seconds. As the number of domain controllers increases, the number of requests also increases. Even if you use multiple agent collectors, each of them must poll all domain controllers independently.
Also, in DC Agent Mode, the necessary events are collected once and sent to the agents attached to the collector. Therefore, user login events are not missed. And in Polling Mode, some input events may be skipped or delayed in transmission.
For convenience, the main differences in the modes have been summarized in the table:
DC Agent Mode | Polling Mode | |
Installation | Complex – one installation per domain controller. Reboot required. | Simple – one installation or setup on FortiGate |
Is a DC agent required | Yes | Not |
Scaling | High level of scaling | Low zoom level |
Event capture level | All events are captured | Some events may be missed (NetAPI) or may be delayed (WinSecLog) |
This concludes the theoretical part devoted to the FSSO technology. Next time we will highlight the practical aspects of this technology. In order not to miss new materials, follow the news on our channels:



