Cyber Files 9.0: discussing new items

Cyber Files 9.0: what's new
We position Cyber Files as a universal, secure and easy-to-use solution for collaboration and file sharing in organizations. It belongs to the Enterprise File Synch and Share (EFSS) class, or, in another classification, to the Content Collaboration class. The Cyber Files Server is deployed directly on the organization’s network, and thanks to a special client application (by the way, there is also a version for Android), users are able to synchronize and securely access shared files on their computers. Placing a server on an internal network does not in any way interfere with the key task of sharing files with external partners. At the same time, if desired, Cyber Files can be used exclusively for internal file exchange, if you do not “release” the server to the Internet.
In version 9.0, it became possible to deploy the main Cyber Files server on domestic operating systems, in particular Alt Server, RED OS Server and Astra Linux Server. This allows companies to implement secure file sharing and synchronization across import-independent infrastructures and confidently use the system across multiple platforms. By the way, CentOS is also next in line – we listen to the requests of our customers.
The issue of information security was one of the key issues in the work on this release. The main thing in the new version is integration with the corporate DLP solution Cyber Protego. Now the Cyber Files server can directly transmit file exchange data to the Cyber Protego web server, which allows you to build a consolidated audit of file transfer operations, and therefore increase the level of control over confidential information.

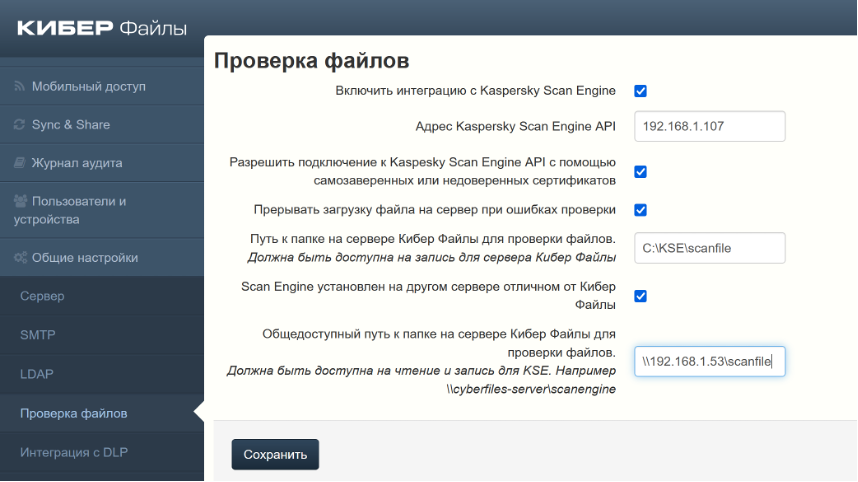
In addition to this, it has become possible to use the Kaspersky Scan Engine solution to scan all Cyber Files uploaded to the server through synchronization clients, a web client or a mobile data application for cyber threats. If they are detected, the download operation of such files may be blocked. Thus, if your company uses this service, you can integrate it with Cyber Files.
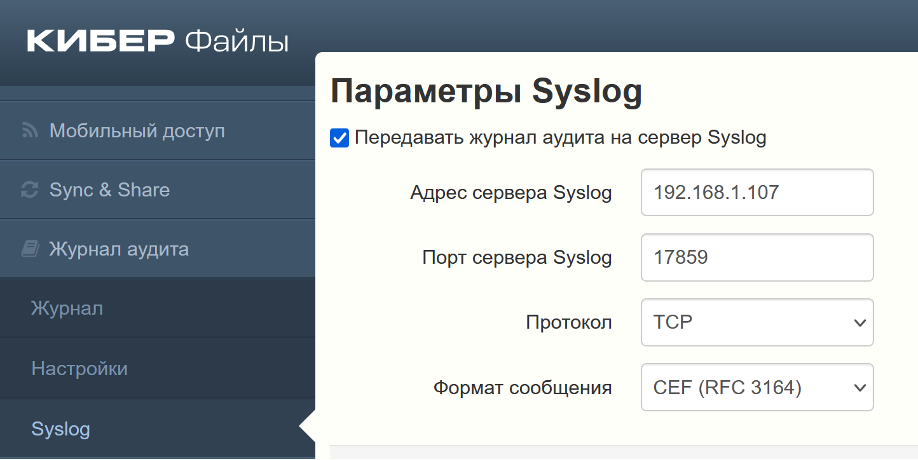
Also implemented is the function of transferring events from the audit log to SIEM systems using the Syslog protocol for those who monitor security incidents on the corporate network using such systems.
The choice of tools for collaboration with documents has become wider. Added the ability to integrate with the Russian solution “MyOffice Collaborative Editing Server (CSR)”. This is a system that allows you to view and collaborate on documents, while data storage and access control are provided by Cyber Files. Let us remember that a similar integration with the P7-Office system was previously implemented – we wrote about it here. So if you use server solutions from the MyOffice or P7-Office family, you can connect them to Cyber Files. Integration with Microsoft Office, for those who are interested, is still valid.

Separately, we note that all these integrations do not require additional licenses, as is common with a number of manufacturers of similar products.
In addition, the ability to upload folders with files to the server via a web client has been implemented, the process of memory consumption by server services has been optimized, and the speed of downloading large files has been improved.
Controlled file sharing
As part of ensuring the collaboration of Cyber Files and Cyber Protego, we are developing the concept of a controlled, secure file sharing environment (we call it “Cyber Perimeter”). What does the integration of two products provide?
A DLP system can provide control of most file sharing web services with the ability to leave only those necessary for operation. This means that during file exchange the following reactions of the DLP system are possible:
Blocking or allowing a file to be sent based on the results of checking its contents
Alarm alert, information alert
Logging of user actions, shadow copying
Record screen, keyboard input, process information
Considering that files can be uploaded or downloaded not only from those work computers where the DLP system agent is installed, but also, for example, from mobile devices or home computers, as well as (most importantly!) by third-party users – partners, contractors and etc., we imported the audit of file operations (events for generating links, downloading files, etc.) from the Cyber Files log itself into the general DLP event log.
Thus, a consolidated analysis of file exchange operations and other data transfer operations, as well as data transfer events from DLP, brings us closer to the implementation of a full-fledged secure file perimeter.
Further development of the integration of Cyber Protego + Cyber Files
The development of integration of the two products planned for future releases will make it possible to obtain a cross-platform solution that implements the Cyber Perimeter concept. The main thing we plan to do in terms of integration is to provide server-side content analysis on the side of the DLP solution. In this scenario, the integration of Cyber Files and Cyber Protego will allow, when downloading or providing links to files, to first redirect them to the DLP server to check the content. This will make it possible to expand the detection and control of sensitive data. In addition, further integration of the two products will ensure that data storage is controlled in accordance with company policy.
Find out more
We recently held a webinar dedicated to the release of Cyber Protego 10.2 and Cyber Files 9.0. At the event they not only talked about new products, but also showed many scenarios for sharing products. Registration available Here.





