Cases for applying network anomaly analysis tools: detecting the spread of malicious code
What’s so hard about detecting malicious code? They put an antivirus and it catches any malware. Alas! If it were all that simple, then you probably could have forgotten about this problem forever, but no … The number of successful malware infections does not get smaller, and all because attackers constantly change their techniques and tactics, modify malware, they use incorporeal malware, they use legal utilities for administering (the same PowerShell) … And this is if we do not consider situations where on individual nodes there is either no antivirus at all (IT specialists do not want to install it because it slows down), or for this platform e about simply does not exist. And maybe there is a situation that I have had to deal with repeatedly in different companies. The top manager picks up malware on his home laptop or tablet and drags it into the company so that local IT specialists figure it out. The device connects to local Wi-Fi and this is how the internal epidemic begins; even in a network isolated from the Internet. In any case, the antivirus is far from always a salvation from modern malicious code, and we need other methods to detect bad guys on our network.
What is characterized by modern malicious code? Are there any signs that can tell us that something is wrong in our network and that we still got some kind of infection? If you do not take into account classical viruses that do not have the function of independent distribution over the network (and you have long seen classic viruses), then among the signs that can characterize the presence of malicious code on the network, I would name the following:
- scanning internal nodes looking for vulnerabilities in operating systems or applications
- scanning of internal nodes in search of open ports through which you can connect to the system
- interaction with well-known command servers
- atypical traffic from the host (previously unmet protocols, exceeding the typical amount of traffic, server protocols at workstations, etc.).
These are network signs, which are almost independent of which malicious code is used. So, you can try to identify them and monitoring tools for anomalies and threats based on Netflow (or other flow protocols) are the best candidates for this. Let’s see how this can be done using the Cisco Stealthwatch solution as an example.
What is the difference between a conventional scan, for example, a security scanner, and a scan performed by malicious code? In the first case, in most situations, iterates through open ports on one computer, then on another, on the third and so on. Such attempts to identify are easy enough. It is easy to determine when the scanner simply checks for only one open port in the address range. The malicious code has a different principle of operation – it scans nodes, finds vulnerable ones, gets over to them, scans again, finds vulnerable ones again and so on.
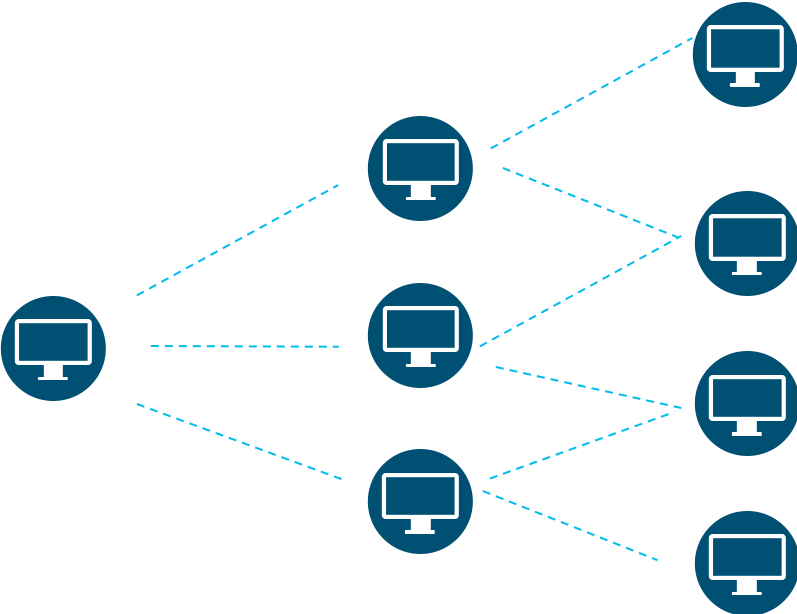
It is such a development that we can recognize with the help of special algorithms embedded in the NTA.
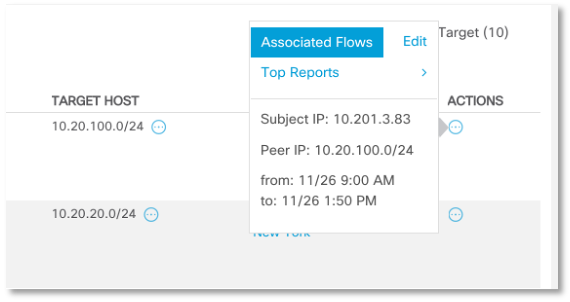
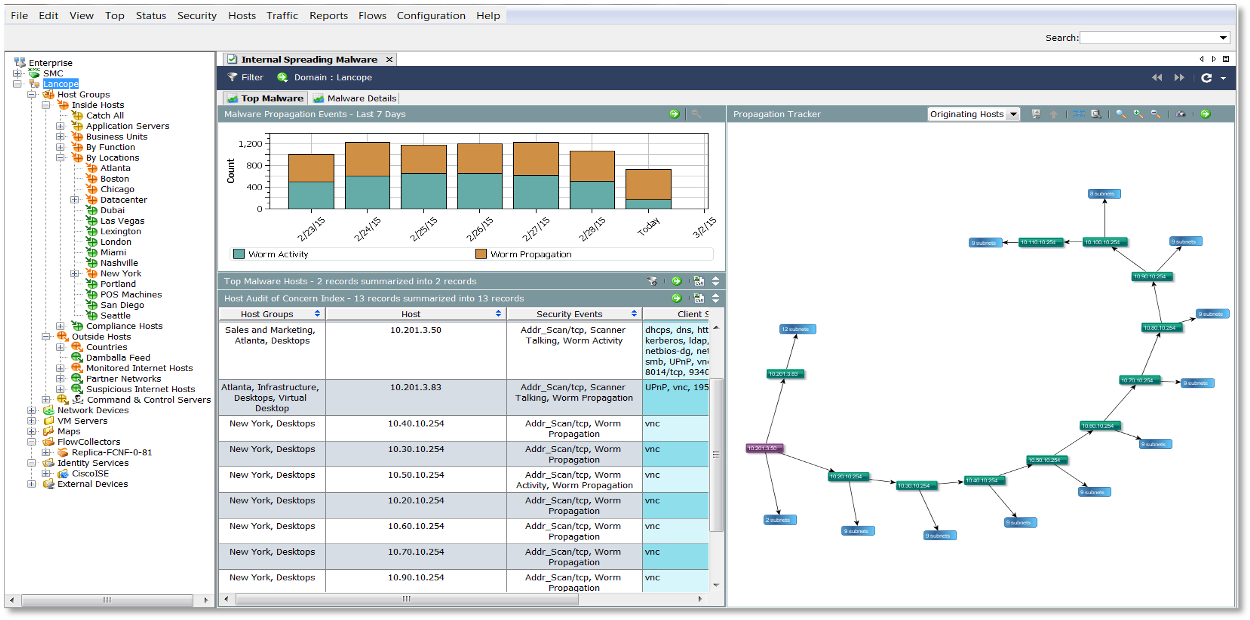
An additional hint to us is the role of the computers from which the scan was recorded – in all cases, these are workstations of sales and marketing employees who scan entire subnets, which are also logically related to the sales division.
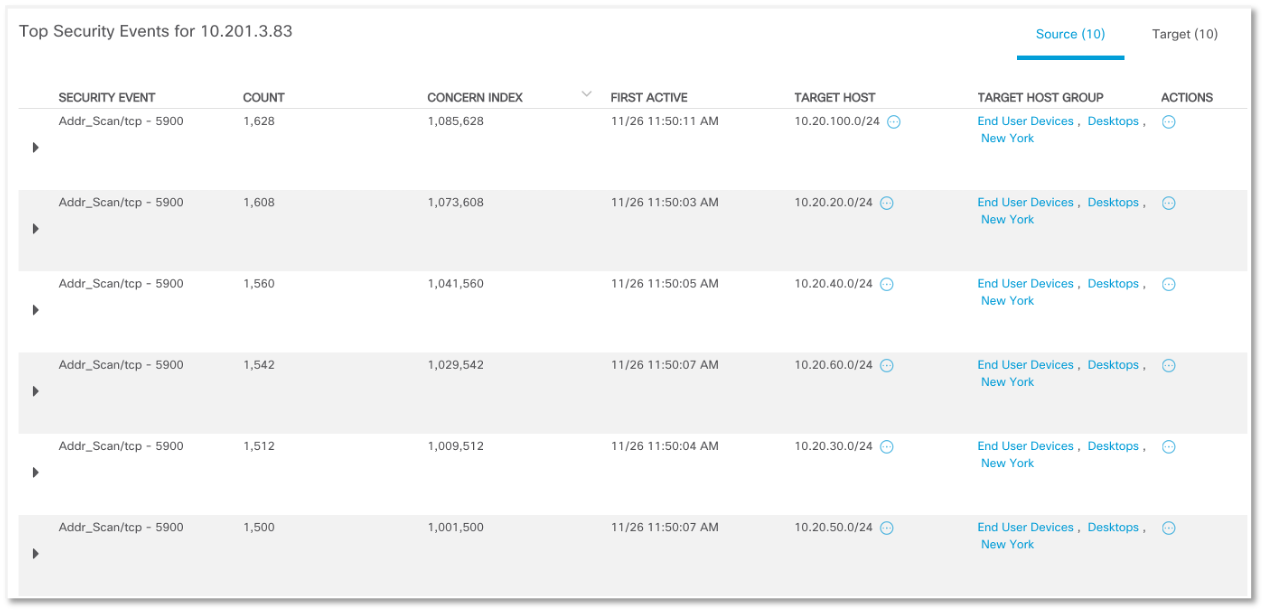
Finding one point of infection followed by the spread of malicious code:
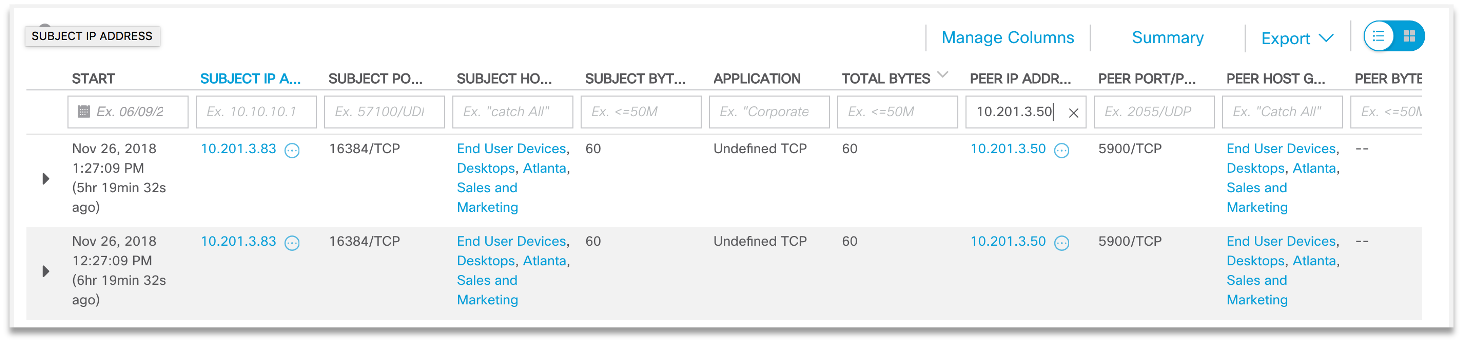
We can try to find other potential victims of malicious code:
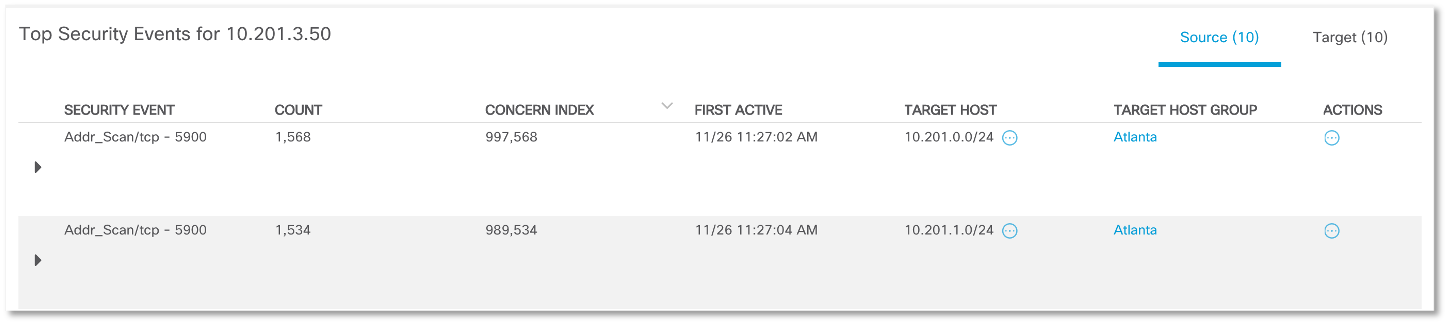
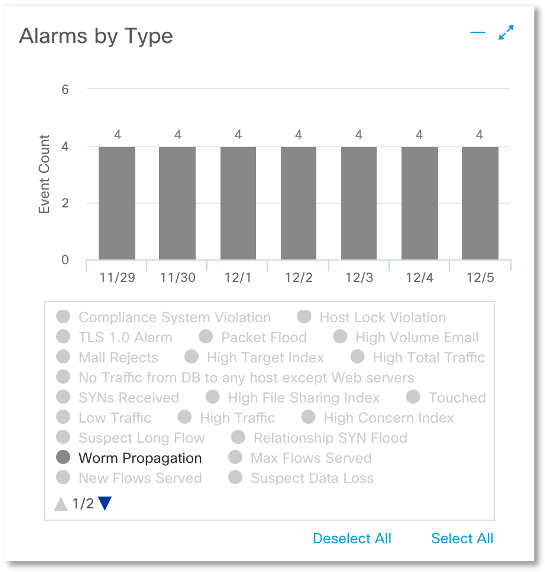
Having correctly configured the anomaly analysis system, the next time we can no longer conduct separate investigations that answer the question, do we have a scan in our network or not? It will be enough just to see the corresponding alarm indicator (recon) on the main console:
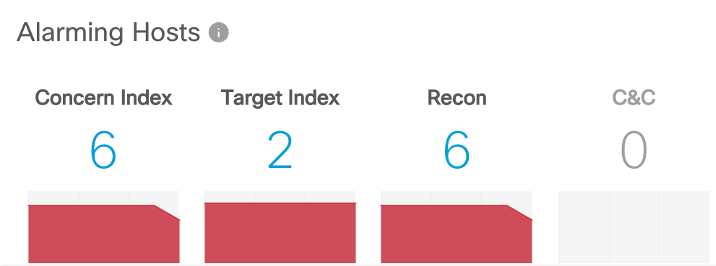
and clicking on it, to get a list of everyone who has been noticed in “illegal” computer actions (by the way, the first illustration in this article shows another way of visualizing the scale of distribution of malicious code).
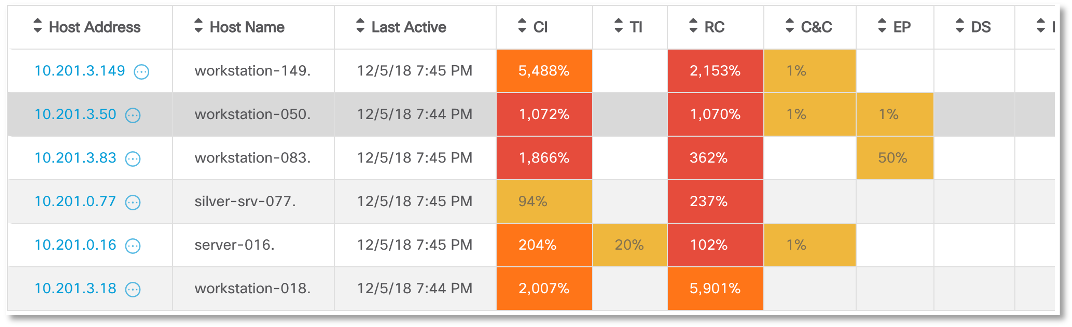
It is worth recalling that a seemingly simple scan may be the first signal for more serious problems. If phishing emails are one of the first steps by which attackers begin their activities, then by infecting one computer, they expand their bridgehead and the main way to do this starts with a scan. This is how WannaCry acted, this is how Shamoon acted, so hundreds of other malicious programs act, resulting in serious incidents.

Having recorded the fact of scanning and spreading malicious code, we are faced with the task of conducting a more detailed investigation and understanding whether a node was already infected, than it was infected, when, etc.? The NTA class solution alone cannot do this, since you cannot answer these questions by telemetry alone. But in the case of Cisco Stealthwatch, a free Cisco Threat Response solution will come to our aid, about which I already talked about integration. It is enough for us to click on the node of interest to us and in the drop-down context menu we will see the possibility of launching CTR, which in turn can collect information about the node of interest to us from various systems – Cisco AMP for Endpoints, Cisco Umbrella, Cisco Talos, etc.

Here’s what the picture might look like that the free Cisco Threat Response displays, relying on its capabilities to enrich and visualize security events:
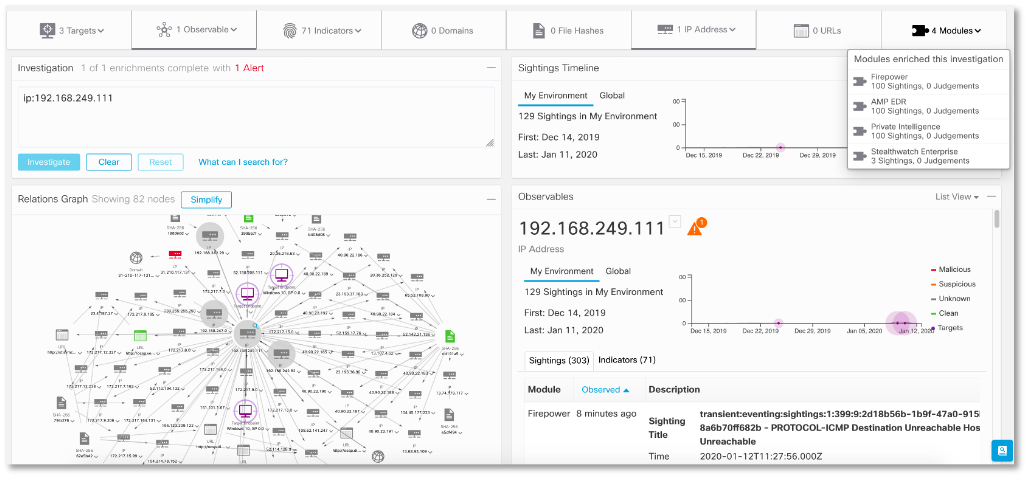
CTR can show us the malicious files associated with the host we are interested in, which we can check through the Cisco Threat Grid sandbox or the VirusTotal service. Having data on one node, we can see who he interacted with or is interacting with in the framework of the incident, where the attack started, what malicious code was involved in it, how the network penetrated, and answered many other questions that interest information security analysts.
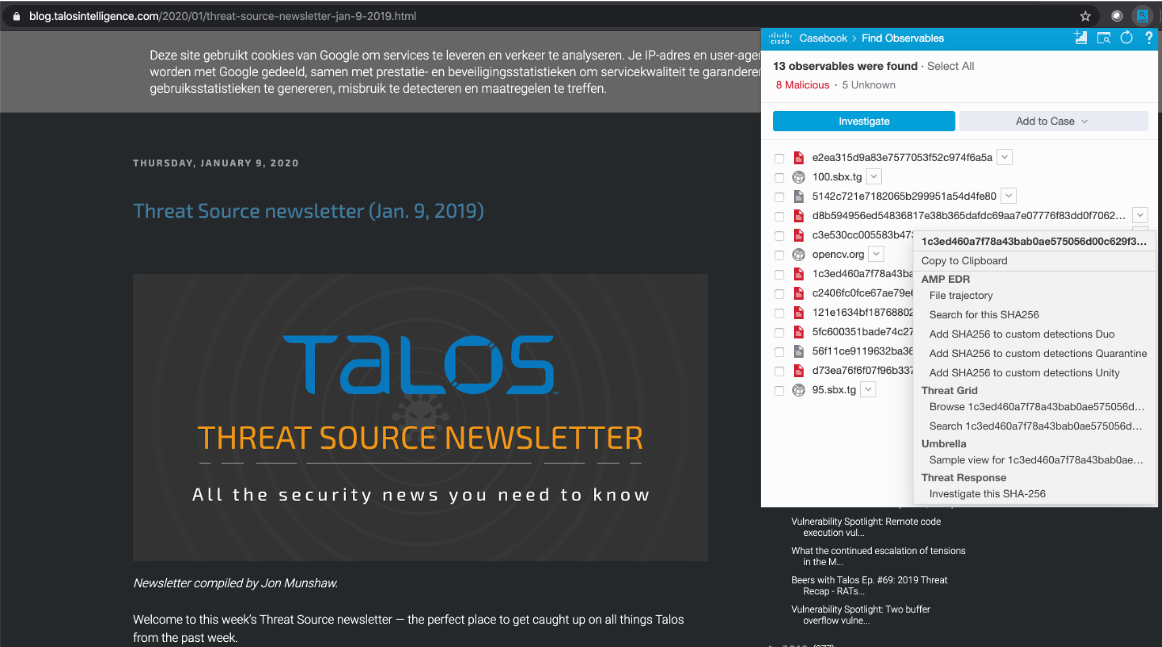
And then we can already conduct additional verification of the received artifacts using external Threat Intelligence services, which can provide us with more indicators of compromise, more information about the attackers, more information about the techniques and tactics they use. It all started with a simple network scan detected by a solution to analyze anomalies using Netflow (or another flow protocol).