Who reads your SMS

I heard this story from my friend from fintech. I liked the story because we all try to protect our personal data, observe digital hygiene, but at the most basic (I would say, fundamental level) everything is simple.
Welcome under the cut, there will be a little story below.
So there is a consumer loan and credit card application website. The client visits the site, drives in his personal data and receives a loan decision. The simplified architecture looks like this:
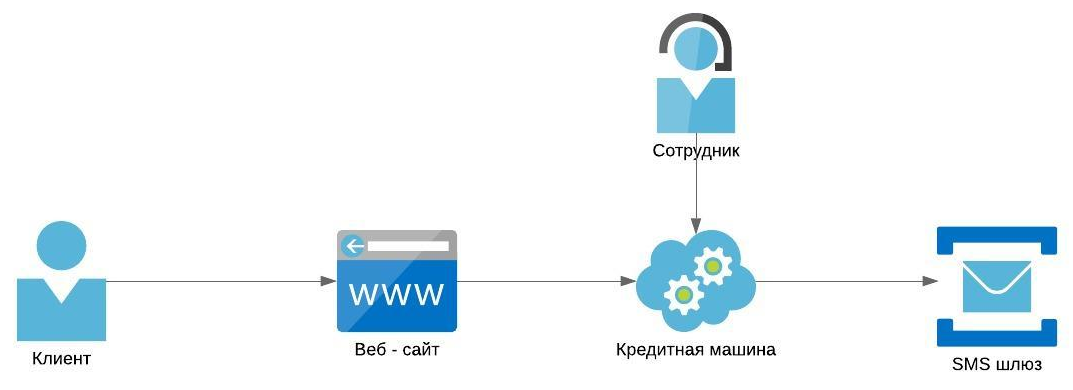
A client submits an application for a loan, it gets into the credit machine, the bulk of applications is processed automatically, about 10% of them belong to the “gray zone” and go for manual processing: the employee looks at the application and decides whether to approve or reject. If approved, the client receives an SMS “Congratulations on loan approval!”
At one of the working groups for analyzing customer requests, fintech employees see frequency tickets of the form: “did not have time to submit an application, immediately started calls from banks and brokers with a proposal to take out a loan“,”you drain my cock“,”what a trash heap, did not have time to get approval, there were calls from other banks“. At first, employees decide that this is either just a “blowout”, or such calls are not frequent, or it is someone’s joke. A month later, they look at the statistics of customer requests again, and they realize that it “didn’t seem to”. This is a problem that needs to be dealt with seriously. An investigation is required, and fintech is starting it.
First step. Check for yourself
A fintech employee applies for a credit card on his website, keeps his phone with him and waits for left-handed companies to call him with a proposal to take out a loan. But no one called. So there’s no problem? Fintech again looks at the statistics of calls: there are customer complaints about calls from third-party companies.
Ok, let’s move on.
Second step. Check on the control group
A team of 10 people is assembled. Everyone applies for a loan on the fintech website. Everyone agrees that they will answer calls for two days, despite the warnings from WhoCalls, and try to memorize (write down) the information they are told.
Bottom line: about 30% of participants in the control group received calls from serious and legal organizations with a proposal to take a loan from them. Someone received a call from a robot, someone from a call center employee of a reputable bank.
So there is a problem. Ok, let’s move on.
Third step. Analytics and localization of contours
So, what fintech has at the moment:
Indeed, there are calls to clients of their company with a proposal to take out a loan from competitors.
Calls come from well-known companies, which means that the latter receive data legally, but it is not yet clear how.
Not all customers are called.
They call after the loan has been approved by fintech.
Fintech splits the application submission into multiple circuits:
The very form of applying for a loan… What is there? So, there is “Yahu. Metrics”. Purely theoretically, there is a counter with the included web visor and some kind of bot collects the client’s personal data under the account of one of the fintech employees. This hypothesis was postponed. What else? Someone takes the data from the backend of the application (before transferring it to the credit machine) and transfers it to third-party companies under the guise of legal “leads”.
Credit machine… Any credit machine has integration with several credit bureaus (hereinafter – CRI). This means, purely in theory, bureaus can transmit information about clients. Also, the credit machine has integration with one of the mobile operators to check customers’ phone numbers, whether they are issued for real people, and not for “drops” (check for fraud).
Employee… An employee has access to information on approximately 10% of applications that go into the gray zone.
SMS gateway. Fintech sends each client an SMS “Congratulations on loan approval!”
Okay, it’s time to move on.
Fourth step. Check each circuit
1 circuit… The application form itself. Fintech IT generates fake applications on behalf of 20 people, but does not transfer them further to the credit machine, but leaves applications on the back-end. They wait two days. There are no calls. The contour is clean, let’s move on.
2 circuit… Fintech IT pushes applications into the credit machine, which knocks on the BCH and the mobile operator. The hypothesis is tested that the data is merged by an employee who makes decisions on 10% of applications. Bottom line: there are calls, but they exist both for the requests that the employee looked at, and for those on which the system made a decision automatically.
The verification loop has narrowed, which means that the data is leaving the following sources:
BKI,
Cellular operator checking numbers for fraud,
SMS gateway.
But what was atypical about this story was that not all customers received calls.
Fifth step. Parsing external integrations piece by piece
BKI… Fintech asks BKI if they have a service “get the data of customers who applied for a loan”, to which they receive an answer that the latter think about it, but the service has not yet been launched and, in principle, it’s great that they asked, let’s conduct a pilot with you. The request was at the end of 2019. At the end, I will write what the essence of the BKI service is.
SMS gateway… Fintech simply generates an SMS congratulating the loan, and bingo! – there are calls from other banks to the subscriber numbers of the same mobile operator with whom fintech has an agreement to check for spam. Calls from reputable banks. Interesting.
Sixth step. Completion of the investigation
Since the company has a direct contract for checking numbers for fraud with one of the mobile operators, and there were calls to its subscribers, fintech simply asks the question: “Guys, what is this? Why are you transferring our clients’ data to third-party banks? ” The mobile operator honestly and openly answers that there is such a business model, and it works like this:
The mobile operator “reads” thematic SMS from its subscribers. In this case, about loan approval. On-line, the operator enriches information about the subscriber with data from other sources (for example, e-mail), and legally transfers these events to companies who are interested. According to a completely formal agreement. What about customer data transfer consent? Well, firstly, they transmit only a phone number (and sometimes email), and secondly, when concluding an agreement with a cellular operator, the client has already given all his consent (but there is a gray area, if you take up this issue, then the operators will be wrong , there is no agreement).
Triggers are triggered for about 20% of subscribers for whom the event is triggered.
Fintech agreed with a cellular operator that for its customers such a threshold for triggering triggers will be SIGNIFICANTLY reduced or removed altogether, the cellular operator has met halfway.
In conclusion, about the BCI – the model for transferring client data is as follows:
Citizen Ivanov took a credit card from the RUS bank. The bank sent this fact to the BKI.
RUS subscribes to the BCI for an event that if, according to Ivanov, a request came to the BCI to check the credit history from other banks (for example, Ivanov decided to take a consumer loan), then immediately inform Bank RUS of this.
The Bank has all of Ivanov’s personal data (remember that he took a credit card from RUSSIA), after receiving the event, he begins to offer Ivanov to come to him for demand.