What is PKI? Key points about public key infrastructure
Imagine that you are a system administrator at Home Depot. As you head home, you notice that your network has just approved a new air conditioner. Nothing special, right? You wake up the next morning to find that terabytes of data, including usernames, passwords, and customer credit card information, have been leaked to hackers. Well, that’s exactly what happened in 2014, when a group of hackers, disguised as a harmless HVAC system, carried out an attack that cost Home Depot over $17.5 million, all because of a misconfigured PKI. In this article, we will cover everything you need to know about PKI.
So what is PKI?
Infrastructure public keys (IOC, eng. PKI — Public Key Infrastructure) is a term that refers to a set of measures and policies that allow you to deploy and manage one of the most common forms of online encryption, public key encryption. In addition to being a key store for your browser, PKI also provides security for various infrastructures, including internal communications within organizations, Internet of Things (IoT), peer-to-peer connectionsth (P2P) and so on. There are two main types of PKI:
• Web PKIalso known as “Internet PKI”, has been defined RFC 5280 and supplemented CA/Browser Forum. By default, it works with browsers and everything else that uses TLS (you probably use it every day).
• Internal (or local) PKI is a PKI that you use for your own needs, namely encrypted LANs, data containers, enterprise IT applications, or enterprise endpoints such as laptops and phones. In general, it can be used for anything you want to identify.
Inside the PKI, there is a public cryptographic key that is not used to encrypt your data, but rather to authenticate the communicating parties. It’s like a bouncer at an elite club: you won’t get in if you’re not on the list. However, without this “bouncer” concept safe online communication will not be possible.
How exactly does it work?
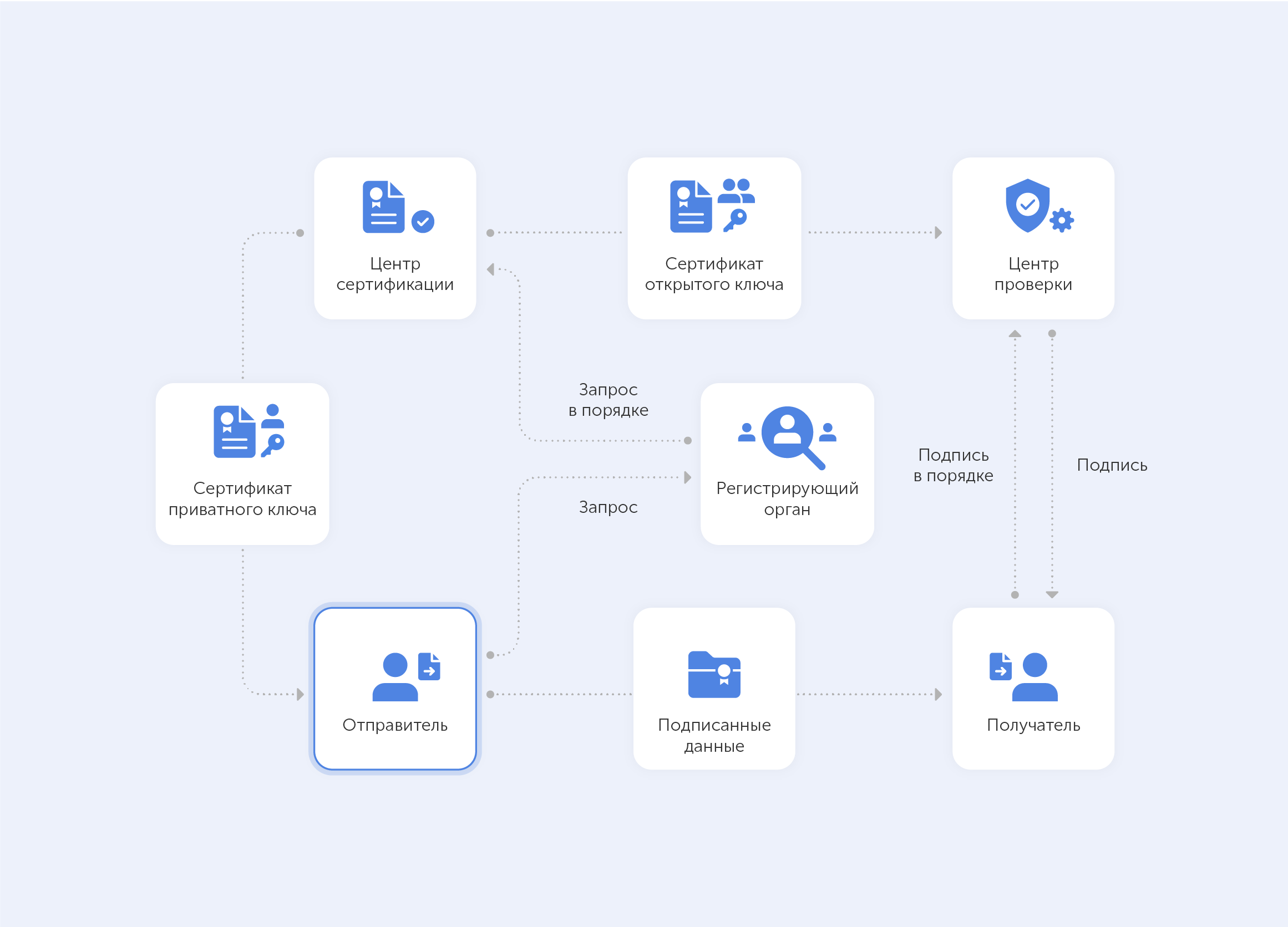
PKI is built around two main concepts − keys And certificates. As in the case of the machineEnigma”, where the settings are used to encrypt the message (or establish a secure protocol), with a key inside the PKI is an a long string of bits used to encrypt or decrypt encoded data. The main difference between the Enigma machine and PKI is that with the latter you have to somehow tell the recipient the settings used to encode the encrypted message.
A public key infrastructure is called that because each party in a secure connection has two keys: a public key and a private key.
The public key is known to everyone and is used throughout the network to encrypt the data, but the data cannot be accessed without the private key, which is used to decrypt it. The two keys are linked by complex mathematical functions that are difficult to reverse engineer or crack by brute force. By the way, this principle is the embodiment asymmetric cryptography.
This is how data is encrypted in a public key infrastructure. But let’s not forget that identity verification is just as important when dealing with PKI, and this is where certificates come into play.
Digital identity
PKI certificates are most often viewed as digital passports containing a lot of assigned data. One of the most important pieces of information in such a certificate is related to the public key: the certificate is the mechanism by which that key is transmitted. Just like, for example, when you give someone your ID.
But in fact, this certificate is not valid unless it is issued by some legitimate authority. In our case, such an organ is certification authority (CA). There is confirmation from a reliable source here that the subject is who he claims to be.
With this in mind, it becomes very easy to understand what a PKI consists of:
• Certification Authoritywhich issues digital certificates, signs them with its public key, and stores them in a repository for reference;
• Registration authority, which verifies the identity of those requesting digital certificates. The CA can act as its registration authority or use a third party to do so;
• certificate database, it stores both the certificates themselves and their metadata and, most importantly, expiration dates;
• Certificate Policy – a description of the PKI procedures (basically a set of instructions that allows you to evaluate how reliable the PKI is).
What is PKI used for?
PKI is great for protecting web traffic: data passing through the Internet can be easily intercepted and read if it is not encrypted. Moreover, it can be difficult to trust the sender’s identity unless some kind of verification procedure is in place.
SSL/TLS (Secure Internet Actions) certificates showcase the most common PKI implementation, but the list doesn’t end there. PKI can also be used to:
• Digital signatures in software;
• Limited access to corporate intranets and VPN;
• Free access to Wi-Fi without a password, depending on the owner of the device;
• Email and data encryption procedures.
The use of PKI is growing exponentially, these days even a microwave can connect to Instagram. This evolving world of IoT devices presents us with new challenges, and even devices that seem to exist in closed environments now require security. Take even that “evil air conditioner” that we talked about in the introduction. Many of the most compelling PKI use cases today center around the Internet of Things. car manufacturers And medical device manufacturers are two more prominent examples of industries that are currently implementing PKI for IoT devices. Electronic system of medical examination Edison is also a great example, but we will save it for future deeper consideration.
Is PKI a panacea?
As with any technology, good execution is sometimes more important than smart design. IN recent study by the Ponemon Institute nearly 603 IT and security professionals across 14 industries were surveyed to understand the current state of PKI and digital certificate management practices. This study identified widespread gaps and problems, such as:
• 73% security professionals recognize that digital certificates continue to cause unplanned downtime and application failures;
• 71% experts argue that migrating to the cloud requires significant changes in their PKI practices;
• 76% say that failing to protect keys and certificates undermines the trust that their organization relies on in their work.
However, the biggest problem is that most organizations lack the resources to maintain PKI. Moreover, only 38% of respondents state that they have the staff to properly maintain PKI. Thus, for most organizations, maintaining PKI becomes more of a burden than a panacea for all ills.
To sum up, PKI is a silent guardian that ensures the privacy of ordinary consumers of online content. However, in the hands of real professionals, it becomes a powerful tool that creates an almost infinitely scalable encryption infrastructure. It lives in your browser, your phone, your Wi-Fi hotspot, all over the Internet and beyond. Most importantly, however, a properly configured PKI is a buffer between your business and a self-appointed air conditioner who wants your money.