What is a blockchain bridge and what risks does it carry?

In early April 2022, the Ronin cryptocurrency network discovered a breach in its system through which hackers withdrew ether (Ethereum) tokens and the USDC stablecoin in the amount of $540 million. Without a doubt, this is one of the biggest robberies in the history of cryptocurrencies. It was caused by a vulnerability in the Ronin Bridge service. And this is not only a problem of the Ronin network, because there are other cases of attacks on blockchain bridges. For example, a little earlier, in February 2022, an attacker withdrew $326 million worth of tokens from Solana. He was helped in this by a vulnerability in the Wormhole (wormhole), the Solana blockchain bridge. What are blockchain bridges and what are they? Why has the bridge become the “Achilles’ heel” for many blockchains? How is their vulnerability solved? This article is devoted to these issues.
Blockchain bridges (Blockchain Bridge), also known as cross-chain bridges (Cross-chain Bridge), or network bridges, are applications that allow you to move digital assets from one blockchain to another. The ether documentation says that bridges are necessary because all blockchains have their own isolated ecosystem, specific rules and their own consensus mechanism. Without bridges, blockchains cannot communicate with each other. On the Ethereum blockchain, you cannot pay with bitcoins, but on the bitcoin blockchain, you cannot pay with Ether tokens. Bridges solve this problem by enabling cross-chain transactions, but spawn many others.
Types of cross-chain transactions
Bridges enable cross-chain transactions, the main types of which are lock-and-mint, burn-and-release, and burn-and-mint.
Lock and Mint
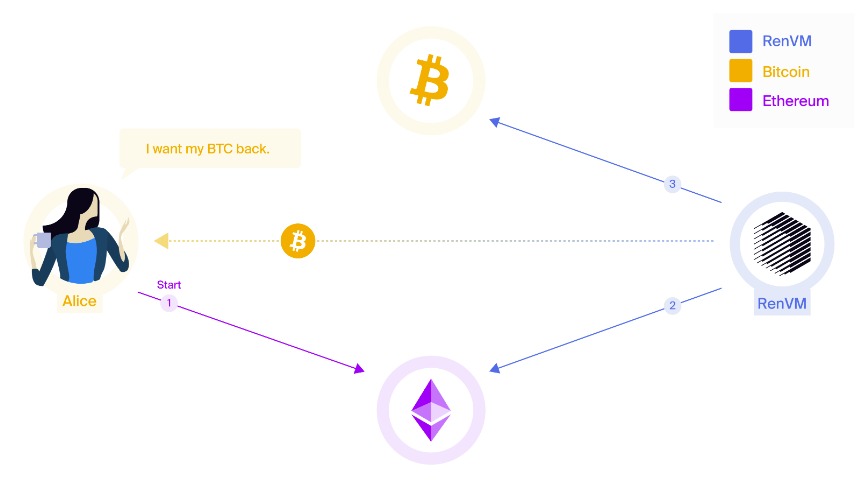
A Lock-and-Mint transaction is a type of transaction that involves locking tokens on the outgoing blockchain and creating/issuing new tokens of equal value on the receiving blockchain. To carry out this transaction, an intermediary is almost always needed, which would asynchronously ensure the blocking of the cryptocurrency, accept the consent of the sender to create new tokens in the receiving network and, in fact, create them.

In the figure above, all the arrows are numbered according to the sequence of Alice’s actions. First, she needs to carry out a transaction that blocks part of the bitcoins (1), then notify the Ren application (2), which will check the blocking of tokens (3) and give permission to issue new tokens on the ether network (4), which Alice will do (5). More precisely, the bridge (in this case, Ren) will do all this for her, except for the first step.
Burn-and-Release
Transaction Burn-and-Release (burn and let go) is an addition to the Lock-and-Mint transaction, allowing users and smart contracts to send assets back to the original blockchain. The name of the transaction directly reflects the essence: tokens that were created earlier and have their counterparts in the original blockchain are destroyed, and the original assets are no longer blocked, i.e. released or released. The picture below shows Alice’s actions that do not require additional explanation.
Burn-and-Mint
The Burn-and-Mint transaction also serves as a continuation of the Lock-and-Mint transaction. Using this kind of transaction, users and smart contracts can “burn” pegged assets on the receiving blockchain and create the same amount of pegged assets on another blockchain without touching the assets locked on the source blockchain. In other words, if capricious Alice wants to have assets equivalent to her original tokens in the third blockchain (Polkadot in the figure), the bridge will simply liquidate her tokens in ether and issue new tokens in polkadot.

A little about the complexity of bridges
In some Russian-language articles on the topic of bridges, it is written that it is incredibly difficult to implement the protocol. The technical part of this technology is so confusing that it is better not to go into the details of the functioning of bridges, but simply to know about their existence.
It may have been true a year ago, but a lot has changed since then. Large frameworks involve programmers in the development of new simple cross-chain applications, creating platforms, documentation and source protocols for them. For example, this is what the contract looks like simple bridgedeveloped by Connext.
pragma solidity ^0.8.15;
import {IConnext} from "@connext/nxtp-contracts/contracts/core/connext/interfaces/IConnext.sol";
import {IERC20} from "@openzeppelin/contracts/token/ERC20/IERC20.sol";
/**
* @title SimpleBridge
* @notice Example of a cross-domain token transfer.
*/
contract SimpleBridge {
// The connext contract on the origin domain.
IConnext public immutable connext;
constructor(IConnext _connext) {
connext = _connext;
}
/**
* @notice Transfers funds from one chain to another.
* @param recipient The destination address (e.g. a wallet).
* @param destinationDomain The destination domain ID.
* @param tokenAddress Address of the token to transfer.
* @param amount The amount to transfer.
* @param slippage The maximum amount of slippage the user will accept in BPS.
* @param relayerFee The fee offered to relayers. On testnet, this can be 0.
*/
function xTransfer(
address recipient,
uint32 destinationDomain,
address tokenAddress,
uint256 amount,
uint256 slippage,
uint256 relayerFee
) external payable {
IERC20 token = IERC20(tokenAddress);
require(
token.allowance(msg.sender, address(this)) >= amount,
"User must approve amount"
);
// User sends funds to this contract
token.transferFrom(msg.sender, address(this), amount);
// This contract approves transfer to Connext
token.approve(address(connext), amount);
connext.xcall{value: relayerFee}(
destinationDomain, // _destination: Domain ID of the destination chain
recipient, // _to: address receiving the funds on the destination
tokenAddress, // _asset: address of the token contract
msg.sender, // _delegate: address that can revert or forceLocal on destination
amount, // _amount: amount of tokens to transfer
slippage, // _slippage: the maximum amount of slippage the user will accept in BPS
"" // _callData: empty because we're only sending funds
);
}
}As you can see from the presented code, the bridge class has only one function – xTransfer. The address (recipient), the destination blockchain id (destinationDomain), the address of the token (tokenAddress), the number of tokens to transfer (amount), the maximum price of the actual execution of the contract (slippage), as well as the relayerFee (payment to the intermediary) are passed into the function.
Examples of Popular Blockchain Bridges
Now there are a huge number of various blockchain bridges. We will only touch on the most well-known so that the reader does not get the impression that we are talking only about the internetwork protocol. Modern blockchain bridges are still frameworks with their own technology stack. Companies that provide cross-chain transactions are interested in maintaining bridges between blockchains, so they are doing everything possible to increase their trust and optimize this technology.
Connext is a modular interoperability protocol that allows you to create secure cross-chain applications (xApps). At least that’s what it says on the front page of their website. Unlike most other bridges, Connext provides transfers without any trust conditions or external validators, making it more secure than systems that use external validators.
Synapse is a framework that allows you to create bridges for blockchains. Synapse Developers assure users that it is their the product is absolutely safe to use. However, it is difficult to find at least one company supplying cross-chain solutions that would admit to the vulnerability of its applications.
Wormhole V1 was created in 2020 and was conceived as a traditional blockchain bridge between Ethereum and Solana. However, the Wormhole system quickly moved beyond Solana and token transfers. As early as August 2021, Wormhole V2 was launched as a decentralized common interoperability protocol for multiple blockchains with initial support for Solana, Terra, Ethereum and Binance Smart Chain. Now Wormhole has grown into a full-fledged ecosystem and has acquired its own platform for developers.
Ren Bridge – one of the few technologies whose developers in their own documentation admit the impossibility of ensuring the complete security of cross-chain transfers. The technology itself is represented by an application for the universal transfer of digital assets between any blockchains. At the same time, the developers claim that their application works with any type of cross-chain transactions.
Polygon PoS Bridge is a blockchain bridge that is part of the Polygon system. Polygon has its own ecosystem, which includes a wallet, several types of bridges, and other blockchain products. The distinguishing features of the Polygon bridge include the ability to transfer not only tokens, but also NFTs to another blockchain (namely, to the ether).
Blockchain bridge vulnerabilities
The first blockchain bridge appeared in 2018. Just 4 years ago! If blockchain is a young technology, then the blockchain bridge is very young. The “fragile” architecture of blockchain bridges is fraught with problems, some of which are exploited by attackers. Of course, we will not be able to describe all the vulnerabilities in this article, but we will touch on the attacks associated with the cases described earlier.
Attack 51%
In 2022, Vitalik Buterin published fast explaining his pessimism about the future of blockchain bridges. The main obstacle in the use of bridges, he called the irreversibility of the negative consequences of a 51% attack. Thus he writes:
“Now imagine what happens if you move 100 ETH to Solana to get 100 Solana-WETH and then Ethereum gets hit by a 51% attack. An attacker puts a bunch of their own ETH tokens into Solana-WETH and then reverses that transaction on the Ethereum side once the Solana side confirms this.The Solana-WETH contract will no longer be fully supported, and your 100 Solana-WETH will now turn into just 60 ETH.Even if there is a perfect ZK-SNARK-based bridge that fully confirms the consensus, it is still vulnerable to theft due to such attacks 51%”.
Attack on smart contract
It is believed that most blockchain hacks are carried out using vulnerabilities in smart contracts used by bridges to provide Lock-and-Mint transactions. For example, in the withdrawal of funds from Solana using Wormhole mentioned at the very beginning, the attackers managed to create 120,000 WETH tokens without freezing them in Solana. The creation of tokens is carried out through a smart contract, i.e. without an attack on it, the release of tokens would not have been possible.
Network attack
In the Ronin Bridge service, also mentioned at the very beginning of the article, a hacker took control of five of the nine validator nodes that process transactions. Part of the hacker’s success was due to the architecture of the blockchain bridge: one of the employees of the developer company had access to four of the nine nodes. The hackers did not need to know machine language or any other hard skills: they gained control of these nodes with the help of social engineering. An employee with access to the sites was interested in a job offer on LinkedIn and opened a document containing spyware.
To burn or not to burn blockchain bridges?
There is no consensus on the future of blockchain bridges. However, the majority of media faces of cryptoeconomics give a negative outlook. Buterin believes that the coexistence of different blockchains without bridges between them is most justified. If there are tokens in Solana, or in Bitcoin, or in Ethereum, then they should be stored there. Bridges destroy the isolation of the blockchain ecosystem, making them vulnerable to hacker attacks.
Tech journalist Tomio Gueron opined that the issue of bridges is the main obstacle to the development of blockchain technology. In his opinion, the point is not even the vulnerability of blockchain bridges to hacker attacks: the interaction mechanism is fraught with many pitfalls. One small mistake in the smart contract can leave the user without his crypto-savings and no one will return them. If there are bridges, then users should not notice them.
Many companies are already working on simplifying the architecture of blockchain bridges and increasing the reliability of their operation. Most likely, blockchain bridges will continue to exist in the near future, but who knows what will happen if someone decides to attack the blockchain through the bridge again. Perhaps the patience of miners, blockchain owners and other stakeholders will eventually come to an end and they will burn all the bridges, marking the beginning of a new period in the history of blockchains.
Sources: