We are building a personal account for the SaaS service for security
In the era of rapid development of SaaS, the lack of a personal account for a cloud service is already considered simply indecent. But there is another important reason for bot protection services and other cyber threats: they do not look like such popular services as cloud storage (such as Azure, AWS), virtual server rental (DigitalOcean) or version control system (GitHub, Gitlab) for that the reason that customers here are often hard to understand why they pay money for. Only advanced statistics and visual graphs can clearly answer this question. Therefore, the process of creating a personal account in Variti had its own characteristics.
Why do I need a personal account for an anti-bot solution user?
Work transparency
When we launched Variti, we wanted to make the service as simple and understandable for the user as possible. Our goal was to create something more like a consumer subscription application than a user interface of a powerful product like Azure, because customers often do not care how protection works technically. It is important that it works, and the costs of protection cover possible losses from its absence.
In other words, transparent statistics should be available to the client, according to which you can verify all of this.
Technical Support Unloading
Our security service has many settings and options. For example, adding security domains, editing whitelists, enabling filtering at the L7 level, CDN integration, adding support for TLS 1.3, and much more.
Some simple settings can be switched with the usual On / Off toggle switch, for example, automatic redirection from the “www subdomain” to the main domain (www.example.com -> example.com). Some – with the help of our Telegram bot, which we recently wrote about. But more complicated settings require more action from the client and technical support. For example, we have Bot Mitigation – the option of constant filtering, which constantly blocks all bots that will knock on the protected resource. But there are some nuances here, because not all bots are bad. For example, clients may have their own “white” bots (for database synchronization, settings with Telegram Bot, search robots, etc.) All such scenarios must be discussed with the client so that they do not inadvertently disrupt business processes.
In principle, all these issues can be immediately resolved with the help of technical support. But her resources are finite, and in the case of complex settings, when speed matters, she may not have time to solve all the problems on the fly.
For example, imagine that hackers launched a botnet attack with the goal of parsing. Customers see the growth of requests on the graphs and at this moment they ask to enable protection against bots (Bot Mitigation). We described above why this option can be time consuming. Meanwhile, another client needed to turn on a simple setup or get statistics on requests for a certain period.
Therefore, we made it possible to connect as many options and settings in your account as possible and continue to add them. For example, recently in LC there was an opportunity to turn on and off the balancing mode with the user’s binding to the server (Service Iphash).
Main tabs
So, here is what we have in your account.
1. Dashboard

Here is a list of client resources. For each of them, 7 tabs with detailed statistics are available. Here are the most popular ones:
Request Analytics – detailed information on resource requests. Displays the participants in the request flow:
- humans – requests from users;
- good bots – requests from search engines or instant messengers;
- bad bots – blocked bot requests;
- requests from the “white list” – requests from verified resources, which the client independently adds.
Bandwidth – contains information about traffic that has already passed our clusters and is filtered. The key indicator is the 95th percentile of the use of the width of the packet channel, and it is also the basis for calculating billing. At no extra cost, the user can exceed the bandwidth by 5% of the rate set (for the period of the entire time the channel is used). For example, if there were rare bursts of traffic, then they are smoothed out in this way, and you can see a more real picture of traffic usage. Within a month, the used bandwidth is measured at a certain interval, for example, once every 1 minute. Then, at the end of the month, subtract 5% of the maximum values, that is, bursts of traffic. From the remaining 95%, the maximum number is selected, which is used to calculate the payment.
Responses Times and Responses Codes – These indicators show the distribution of time and the distribution of response codes of the client’s resource server. This information is used to determine the moment of “degradation” of site performance.
Request Geography – statistics on the geographical distribution of incoming requests. For example, if a client provides services only for Russia, and a group of requests came from Brazil, then it is highly likely to talk about a bot attack.
2. Services

In this section, you can configure services yourself.
For example, the first tab displays the main traffic filtering options. Here are the most interesting of them:
- Bot mitigation – continuous filtering of illegitimate automated resource requests
- Web application firewall – protection service against targeted attacks such as XSS or SQL injection
- Global whitelist – permission to access the site for search engine bots and systems for site preview
Tab Aliases allows you to add aliases for your resource, for example, domen.example.com or example.net. On the Origins tab, you can configure a list of IP addresses to which filtered traffic should be sent.
Whitelist and Blacklist contain a list of IP addresses. Requests from the “white list” must always be skipped to the site, and from the “black list” it is always impossible. It can be used for resources in which you are sure that they are yours or precisely belong to your competitors.
3. Traffic markup
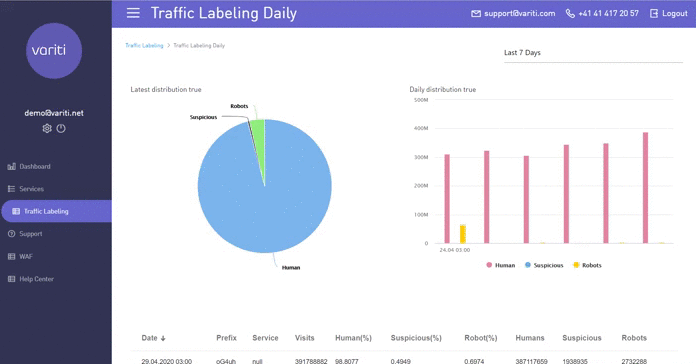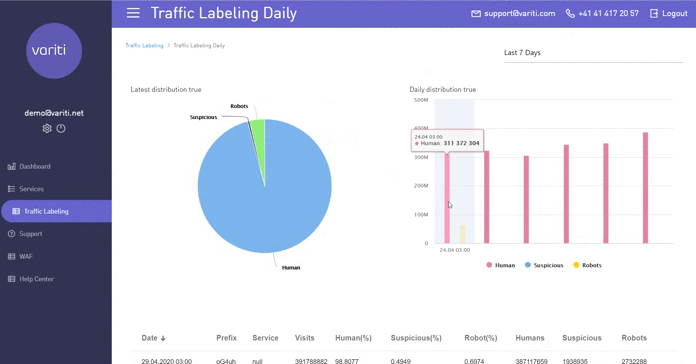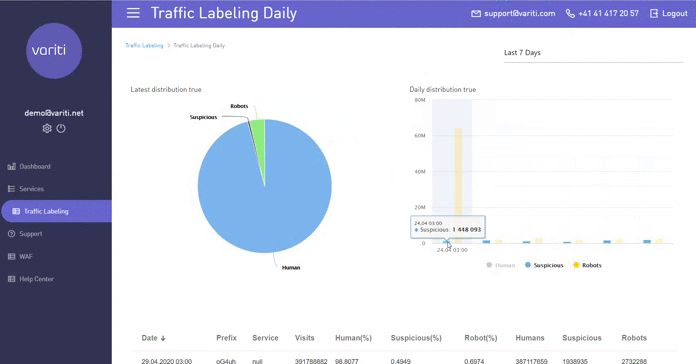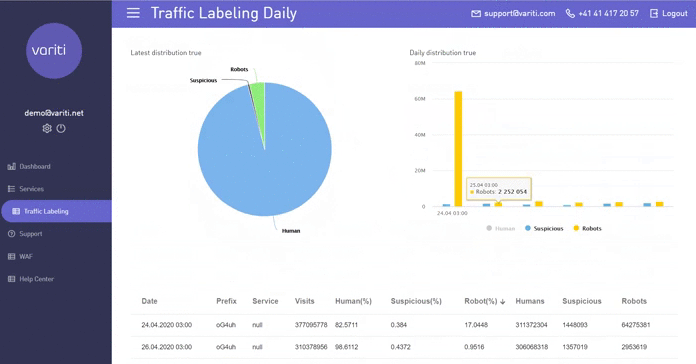
When marking traffic technology is used Active Bot Protection. She checks traffic for “quality”To pre-marked URLs. For example, you are offered to place an advertising banner and promise to drive traffic via your link. If you come across a scammer who, instead of real people, simply drives the necessary amount of bot traffic there and reports statistics on the achievement of the result, then in this tab you can see who came to you: bots or people. Also, this information can be viewed in the context of one day.
4. Technical Support and Help Center
In addition to phone, email and Telegram, technical support can be contacted in the Support section: create a new request, communicate with specialists and track the status of previous requests. Help Center brings you to the FAQ page with answers to frequently asked questions.
Making your personal account more convenient
Your SaaS service dashboard in 2020 should be a fast, convenient and easily scalable web application. No compromises, because all the tools for this are available. Based on these considerations, in 2019, we rewrote the service of your personal account to a modern framework Angular.
This is one of the top tools for creating SPA applications (Single Page Application). SPA is an architecture that allows you to update and add information “invisibly” to the user: he does not need to refresh the page to see, for example, a new status or connection of a new service. From a technical point of view, the page is loaded once, and then dynamically updates the content depending on user actions or scripts. For example, on the Dashboard tab, the graph and statistics on requests are updated in real time without reloading the page. The same thing happens when you go to other pages of the site: only the necessary part of the page is updated. This approach helps to get data faster and reduce the load on the server.
This year we have planned several major updates in your account. All updates lead to one thing: transparent and flexible management of traffic filtering service. Transparent means getting maximum details on reports, up to single requests. Flexible management – to configure any traffic conditions, for example, exclude specific URLs or allow requests for origin traffic to a specific limit.
findings
The main conclusion is quite simple and non-original: SaaS services should improve the quality and functionality of your personal account as soon as possible, as this gives an impetus to the development of the SaaS service itself. For example, after we rewrote and expanded the functions of our personal account, three times more customers began to use it. In addition, they often connect additional services, because it is fast and convenient.
The second is that modern UI frameworks (React, Angular, Vie) can be easily implemented and scaled. At the start, most likely, there will be a certain MVP for receiving feedback from the first customers. It is important that as soon as the development plan is visible, you must immediately do everything “wisely” from scratch.
And, finally, you need to constantly receive feedback and prioritize: first of all, add functions that are in demand, and not which were invented during the development of the roadmap. A simple thing, which, however, is not always obvious on the development side.
In our company, a constant expansion of functionality allows us to cool down the load on technical support. It also makes it clear to customers that we are not standing still.





