Vulnerabilities of an invulnerable Linux
Among ordinary users and even IT employees, there is a widespread belief in the increased security of the Linux operating system in comparison with the “leaky Windows” and “pop macos”. However, how showed our research, open source does not save Linux from bugs and vulnerabilities that pose security risks. In this post, we’ll take a look at why Linux has become an attractive target for attackers and discuss the main threats and risks associated with this operating system.

According to the Linux Foundation, back in 2017, 90% of the client resources of all cloud providers were running Linux, and in nine out of ten cases, the cloud provider itself used Linux as the main OS. But the cloud is not limited to: 82% of all smartphones released in the world also use Linux, and among supercomputers, Linux accounts for 99%.
As businesses and organizations move data to the cloud, where Linux reigns supreme, attackers’ focus shifts to the vulnerabilities of this family of operating systems: vulnerabilities, misconfigurations and security gaps, and malware.
Vulnerabilities
One of the most common methods of infiltrating a system is exploiting vulnerabilities. The lack of procedures for managing and tracking vulnerabilities, not to mention the absence of well-built patching processes, can lead to the fact that systems will be defenseless after the discovery of the next vulnerability and the publication of an exploit for it. An exploit is often published within hours of its discovery. For Linux, this problem is more critical, since open source allows you to quickly find the problematic function and write code to exploit the error.
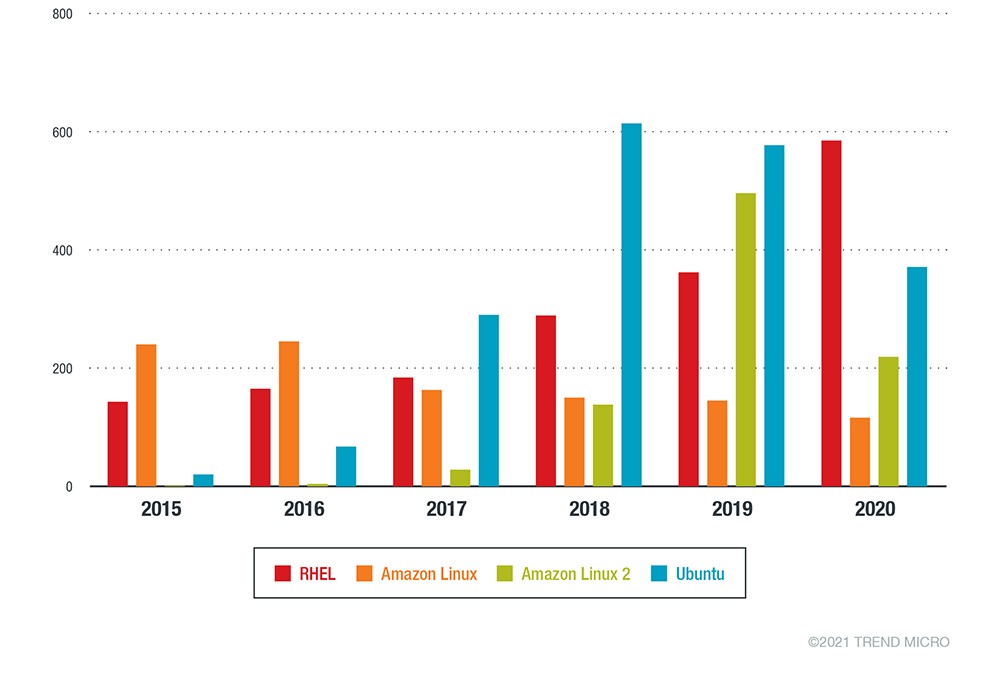
It is important to note that a significant number of vulnerabilities in a service or platform does not necessarily mean that these vulnerabilities necessarily pose a significant risk.
Each Linux distribution vendor has a different vulnerability handling procedure. While patches from vendors come at different times, upstream patches, be it the original package or the source code of a utility, appear first. Linux vendors are responsible for patching vulnerabilities in components such as the kernel, utilities, and packages. In 2019, Red Hat patched over 1,000 CVEs in its Red Hat Enterprise Linux (RHEL) distribution, according to their Product Security Risk Report. This is over 70% of the total number of vulnerabilities fixed in all products.
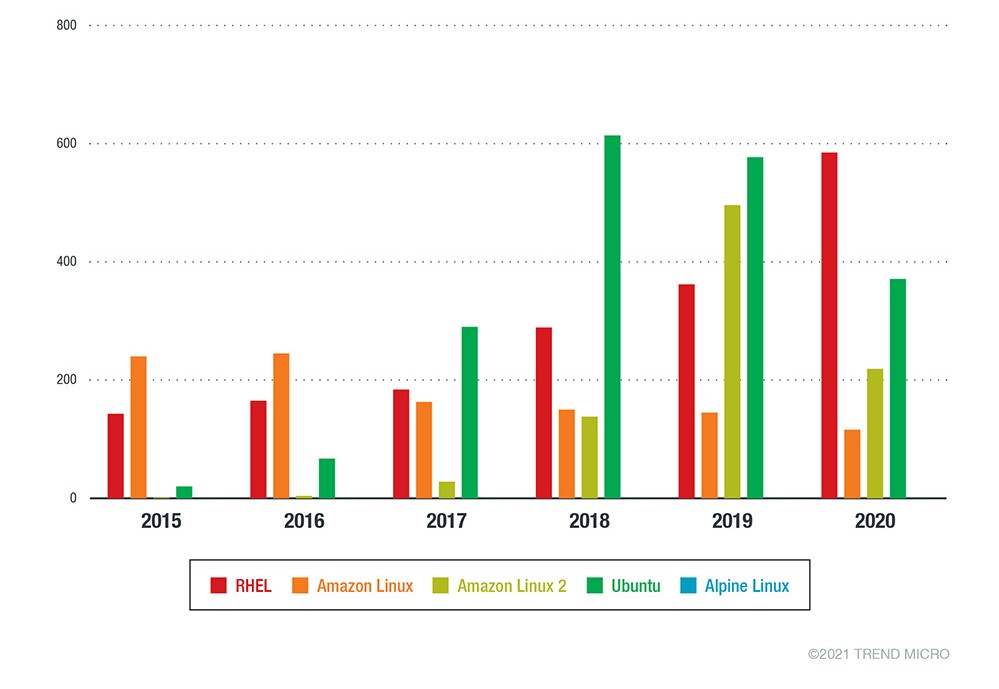
Vulnerabilities in applications running Linux have been the cause of several serious incidents. For instance, sensational data leak in Equifax occurred as a result of the exploitation of the CVE-2017-5638 vulnerability in Apache Struts. Then hackers penetrated the corporate network of Equifax credit bureaus on May 13, 2017, but the security service noticed suspicious activity only at the end of July. Cybercriminals spent 76 days on the network, having managed to download personal information of 148 million Americans from 51 databases during this time – this is 56% of the US adult population. In addition to American citizens, the information leaked from 15 million Equifax customers in the UK and about 20 thousand Canadian citizens. Equifax’s total costs resulting from this incident were more than $ 1.35 billion over the next two years, and include costs for strengthening security systems, customer support, legal fees, and legal claims.
Public application vulnerabilities are part of the MITER ATT & CK framework (ID T1190) and are also listed in the top 10 OWASP vulnerabilities and are the most popular vectors of penetration into Linux systems.
Configuration errors
Insecure settings are fairly common and have always been a critical security issue. The first version of OWASP Top 10 Web Risks from 2004 included Insecure Configuration Management; in the 2017 version of the list, the name has changed to Security Misconfiguration.
As businesses began to massively migrate to the cloud for operational and economic resilience during the COVID-19 pandemic, misconfiguration became even more serious: as businesses and organizations moved to new ecosystems, they inadvertently introduced configuration errors for cloud infrastructure, containers, and serverless wednesday
The following are the most common security issues in Linux configuration.
Weak Linux passwords are widespread
The use of default passwords or weak passwords is still surprisingly common, with even the most popular distributions not doing better.
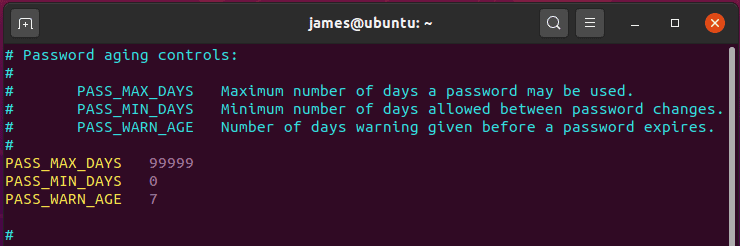
For example, in Debian / Ubuntu distributions, the default password lifetime is 99,999 days, and if you need to force the password complexity, you will have to install the libpam-pwquality package or its equivalent.
A notorious example of abuse due to lack of authentication occurred at Tesla, when attackers gained access to the administrative console control panel, were able to hack the working Kubernetes subsystem, and get AWS Tesla credentials to run a cryptocurrency miner…
November 2020 FBI issued warning that attackers misuse misconfigured instances of SonarQube, which detects errors and security vulnerabilities in source code. Due to the fact that some organizations did not change the default system settings, they were available on port 9000 using the admin / admin credentials.
The same problem is massively present among IoT devices running Linux, the manufacturers of which often do not bother with secure password settings. Many IP cameras and routers also come without passwords or with default passwords, which can be easily found in the publicly available default password database (Default Passwords Database). Moreover, in some cases, passwords are hard-coded and cannot be changed.
Vulnerable Internet Services
The development of specialized search engines has led to the fact that a vulnerable open port on the Internet can be regarded as an invitation to attack. For example, using the specialized search engine Shodan, we discovered over 8 thousand vulnerable Redis instanceshosted in a public cloud without TLS encryption and even without a password. Later it turned out that they were all already used by someone to mine cryptocurrency…
Open file shares on Linux servers
Publicly accessible FTP, SMB and NFS shares, permitted directory listing on Linux web servers, Amazon S3 open cloud storage and Azure Blob pose a potential risk of unauthorized access. With the help of Shodan, we have discovered over 3 million vulnerable public FTP servers.
Malicious software
There are many types of malware under Linux: ransomware, cryptominers, rootkits, worms, backdoors, and remote access Trojans (RATs). Criminals successfully use them for financial gain, espionage, sabotage, hacktivism, or simply to prove that systems can be compromised.
The following are the most common types of malware in the Linux ecosystem.
Ransomware
It is by far the most financially successful malware category in recent memory. Given the growing popularity of Linux, ransomware attackers see the operating system as a very promising target.
An example of Linux ransomware is RansomEXX / Defray7777, recently ported to this operating system. It was used by the Gold Dupont cyber group, which attacks organizations from the healthcare and education and technology industries.
Another ransomware, Erebus, first spotted in September 2016, in June 2017, Erebus infected 153 Linux servers of the South Korean hosting company NAYANA and disabled 3,400 client sites.
Cryptominers
A relatively new motive for cybercriminals is the penetration and abuse of computing resources for cryptocurrency mining.
Many malicious cryptominers not only infect Linux systems, but also cleanse them of the presence of competing miners, and also seek to take over the most powerful systems with almost unlimited computing power, such as Docker or Redis containers.
To penetrate the system, miners use common vulnerabilities. For example, the coinminer program detected by Trend Micro as Coinminer.Linux.MALXMR.SMDSL64 exploits the SaltStack Authentication Bypass (CVE-2020-11651) and SaltStack Directory Bypass (CVE-2020-11652) vulnerabilities.
Malicious scripts
Command interpreters are present on all UNIX machines, so cybercriminals actively use it, especially since it is much easier than using compiled malware.
Reasons for the popularity of malicious scripts for attacks on Linux:
they are easily loaded as text files;
they are small in size;
they are less likely to be easily detected;
they can be created on the fly.
Web shells and backdoors
A web shell is a script installed on a web server that executes the attacker’s commands and provides him with direct access to the compromised system. For example, in August 2020, we came across Ensiko, a PHP web shell targeting Linux, Windows, macOS, or any other platform that PHP is installed on. In addition to remote code execution with Ensiko, attackers can execute shell commands and damage websites.
Rootkits
A rootkit is a set of malicious programs that are introduced into a Linux system, partially or completely replacing standard system utilities, drivers, and libraries. The main purpose of a rootkit is to hide its presence from the administrators and users of the compromised system, providing the attacker with full or partial control.
In the course of our research, we came across several families of rootkits. Most often they were Umbreon, Drovorub or Diamorphine.
Recommendations
Enterprises continue to adopt Linux, and the use of this OS is not limited to server tasks. Large enterprises are actively install a free OS on users’ desktops… Obviously, when cybercriminals notice this trend, they will increasingly target the Linux environment for financial gain.
Here are some guidelines for securing Linux systems:
introduce as a compulsory principle “Infrastructure as code»(Infrastructure as Code, IaC), which ensures that systems are created properly, and their configurations correspond to the tasks being solved;
use the principle of least privilege and the shared responsibility model;
control the integrity of the operating system so that suspicious changes cannot occur unnoticed;
track the network perimeter, monitor all devices, systems and networks;
replace the default passwords with strong and secure passwords, always enable multi-factor authentication whenever possible;
Install updates and bug fixes regularly.