Types of biometrics in the mobile application
Let’s talk about three main ways to “find out” a user, whether intruders can really trick the camera, “like in a movie,” and what authentication and the game “Find 10 Differences” have in common. We hope that these observations will be useful for those developers who are starting to explore the possibilities of iOS and Android.
The main types of biometrics
User identification is required in many applications that process personal data, such as online banking. So, in Russia since 2018 Unified biometric system (EBS), through which customers can use the services of banks remotely. According to the recommendations of the Bank of Russia, in 2020 all banks should be able to collect biometric data of users.
According to a Spiceworks study, more than 60% of companies Europe and North America use biometrics to protect data and believe that this method is more reliable than a pin code or a combination of username and password. 10% of respondents are sure that only biometrics is enough for identification, while other companies insist on using additional methods.
Popular methods of biometric identification, according to research:
- Fingerprint scanner – 57%
- Face geometry scanner (face ID) – fourteen%
- Other methods: iris scanners (IRIS) and hand geometry (3-5%).
There are other methods of authentication, for example, voice biometrics – however, their reliability is lower, so they are used less often.
Let’s consider the features of several of the listed methods.
1) Fingerprint scanner
In order to “recognize” the user by his fingerprint and securely store his data, each manufacturer of mobile devices offers its own capabilities. For example, on Apple devices, a fingerprint sample is passed through a hash function before being saved to a secure computing module. All the processes associated with Touch ID take place in this module, and it is impossible to extract such data.
On Android devices, the degree of security depends on the manufacturer, the approaches and solutions they use. As a rule, work with fingerprint scanners is regulated by separate documents, including Google specifications. Leading smartphone manufacturers such as Samsung use reasonably reliable and accurate capacitive sensors and provide a high degree of data security. However, individual small companies may use less reliable sensors and store prints on the device, sometimes even freely available.

2) Face geometry scanner (face ID)
If the application identifies the user by face, scanning is performed using a capacitive camera. Compared to the previous method, an even more complex algorithm is required here, which requires high accuracy of image capture and distribution of more than 30 thousand control points over the user’s face image. In turn, this determines higher requirements for the smartphone camera.
Basically, a capacitive scanner examines the user’s face, building a geometric model and converting it into computational results that can be stored. During authorization, the calculation result (taking into account the error) for a specific user is compared with the result stored in memory.

However, not all devices provide full capabilities for face recognition. There are times when manufacturers are limited to 2D scanning with a conventional camera. As a rule, a face is highlighted in the picture, which can be compared with other images in the database – as in the game “Find 10 Differences”. If the application cannot find a difference, then the user can be recognized as the owner. In this case, there is a risk that a potential attacker will be able to unblock the application simply by scanning the owner’s photo.
3) Iris scanner (IRIS)
It is important to remember that IRIS is not a retinal scanner. In simple terms, this technology scans the iris that surrounds the pupil, while the retina is located inside the eye on the back wall.
The scanner determines certain features of the user’s appearance and the geometric shape of the iris using capacitive cameras.
While this method of biometric protection may seem promising, it has its own vulnerabilities. On the one hand, to unlock it is not enough to find and present the owner’s photo, because the camera determines the volume of the image. However, this risk is higher with the simultaneous use of photography and contact lenses. A retina scanner may be safer in this regard, since the owner’s data cannot be obtained from open sources or guessed.

How recognition works
When using any of the listed biometric scanners, as a rule, 100% accuracy is unattainable. When a user scans a fingerprint, the resulting pattern depends on the force of pressing, displacement by a fraction of a millimeter to the right or left, the presence of minor skin injuries. As a result, multiple scans of a face or fingerprint of the same user always contain differences.
At the same time, for authorization by face or fingerprint, a fuzzy search method is used.
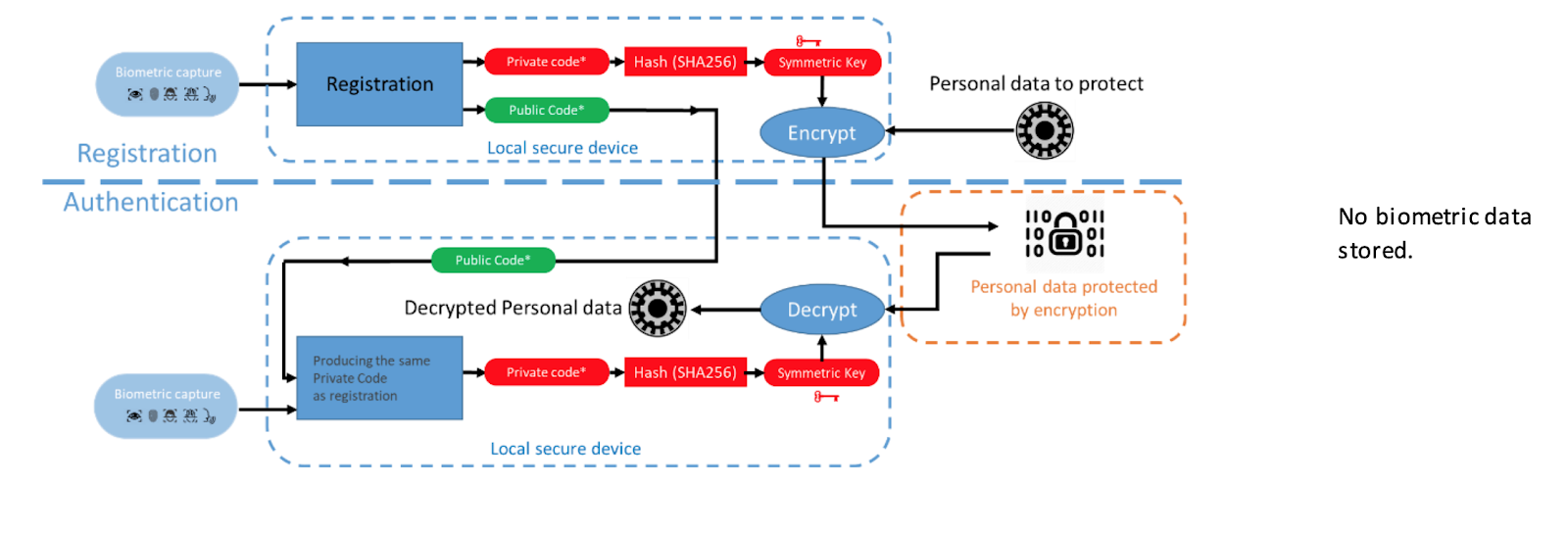
Block diagram with symmetric cryptographic keys (source)
In this case, the application is not looking for completely matching elements, as in password hashing, but the entities that are most similar to each other. For example, if you log in with your fingerprint, then a 90% coincidence of the picture is a very good indicator that actually confirms the identity of the owner of the fingerprint.
However, 10% of the fingerprint consists of other data. This means that we get a different hash and lose the ability to securely store data. In addition, the entire data has to be stored, because the hash function with the return of close values for similar character combinations is not safe enough.
Let’s see how the registration process will look like:
- Biometric scanning captures an image.
- The algorithm extracts stable and reproducible vectors from the image.
- Open and closed code is generated, and the closed code is hashed.
- Symmetric or asymmetric cryptographic keys are issued for the generated biometric hash code.
- When using asymmetric cryptographic keys, the public key is saved and the private key is removed from the system. Biometric data is not saved in these cases.
Verification takes place as follows:
- Biometric scanning captures an image.
- The algorithm extracts the same stable features as it did when registering.
- The public code tells the system “where are the functions” for finding the private code.
- The same private code is generated, the same cryptographic keys and hash are issued for authentication.
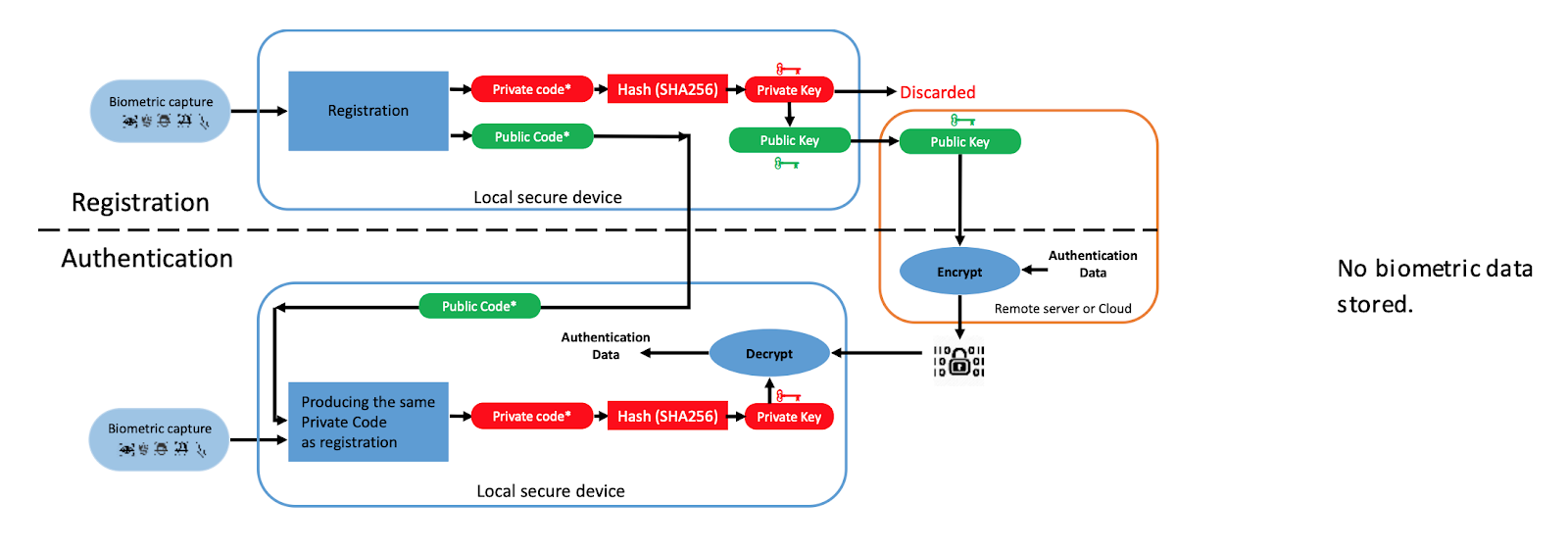
Block diagram with asymmetric cryptographic keys (source)
For the conversion to be repeatable, the biometric signal must be properly registered before it can begin. This problem has been partially solved using a number of methods described in the scientific literature.
Summing up
In this article, we have analyzed the most popular ways to identify a user and their features, which, in our experience, can be useful not only for novice developers, but also simply for those who are interested in this issue from the side of execution mechanics.