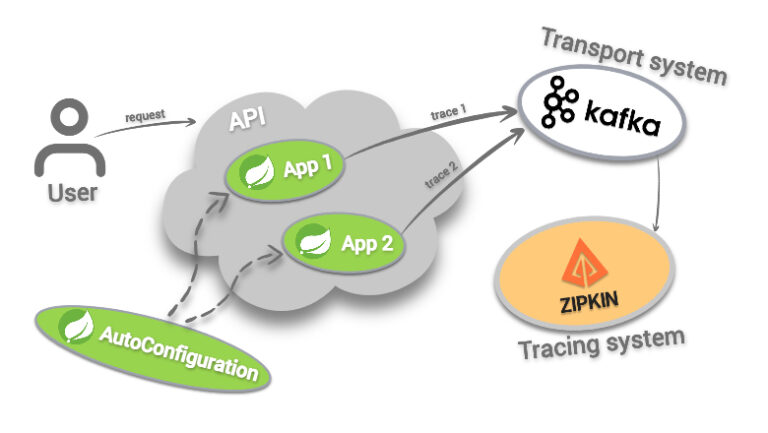
Three cases of workstation inventory in remote work conditions
![]()
In this article we will analyze examples of using the solution for software distribution and inventory of Quest KACE, including for detection on the workstations of the same Zoom. Details under the cut.
How to find and neutralize Zoom
Zoom is insidious, it is not installed in Program Files, instead it is placed in the personal folder of the user who installed it on the workstation (** someuser ** AppData Roaming Zoom bin zoom.exe). You can also find traces of it in the registry, but why complicate things?
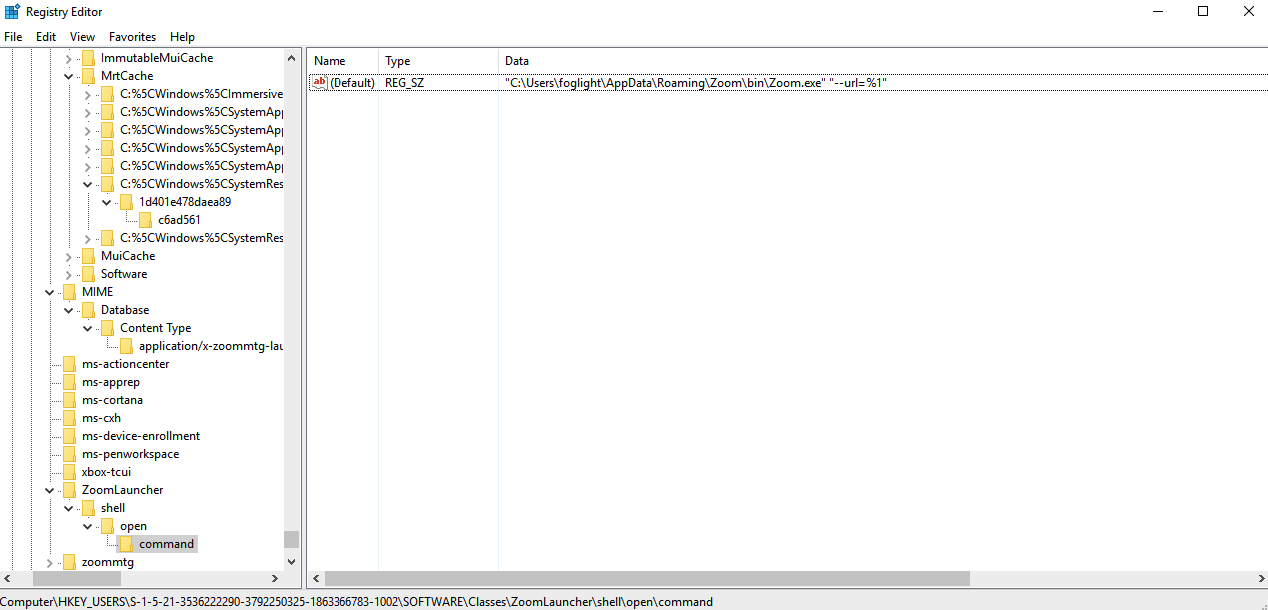
If your corporate policies prohibit installing some software and you know which one, it will be easy to find it by executing specialized shell scripts through installed KACE agents on workstations. KACE has a concept like Custom Inventory Rule. Using it, you can bind additional inventory information to each detected device. For example, knowing where to look, you can recursively search for zoom.exe in all directories of the form c: Users ** someuser ** AppData Roaming Zoom bin zoom.exe.
ShellCommandTextReturn(CMD /q /c for /d %u in (Users*) do (if exist %uAppDataRoamingZoombinzoom.exe echo %u))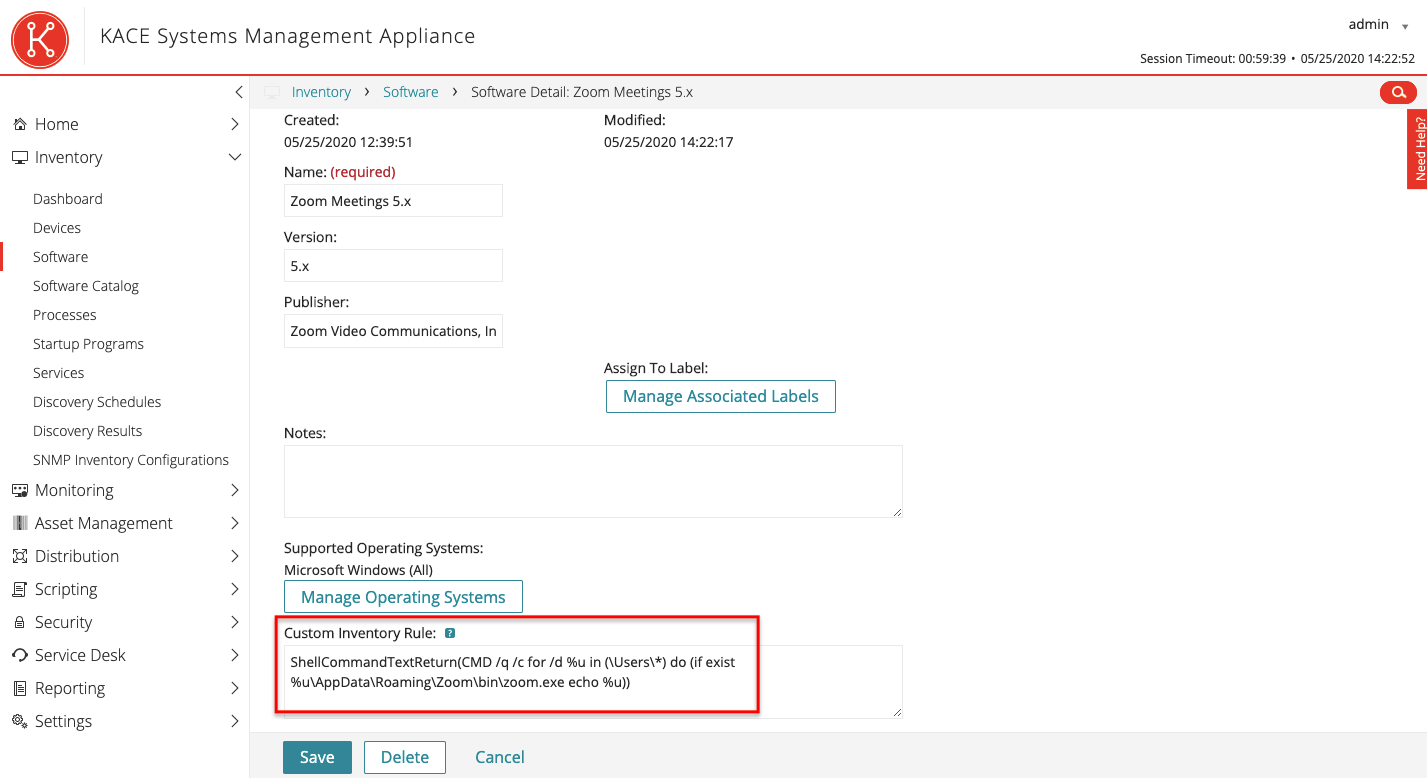
After the next inventory cycle, we will find on each workstation with Zoom installed an entry indicating the user folder.
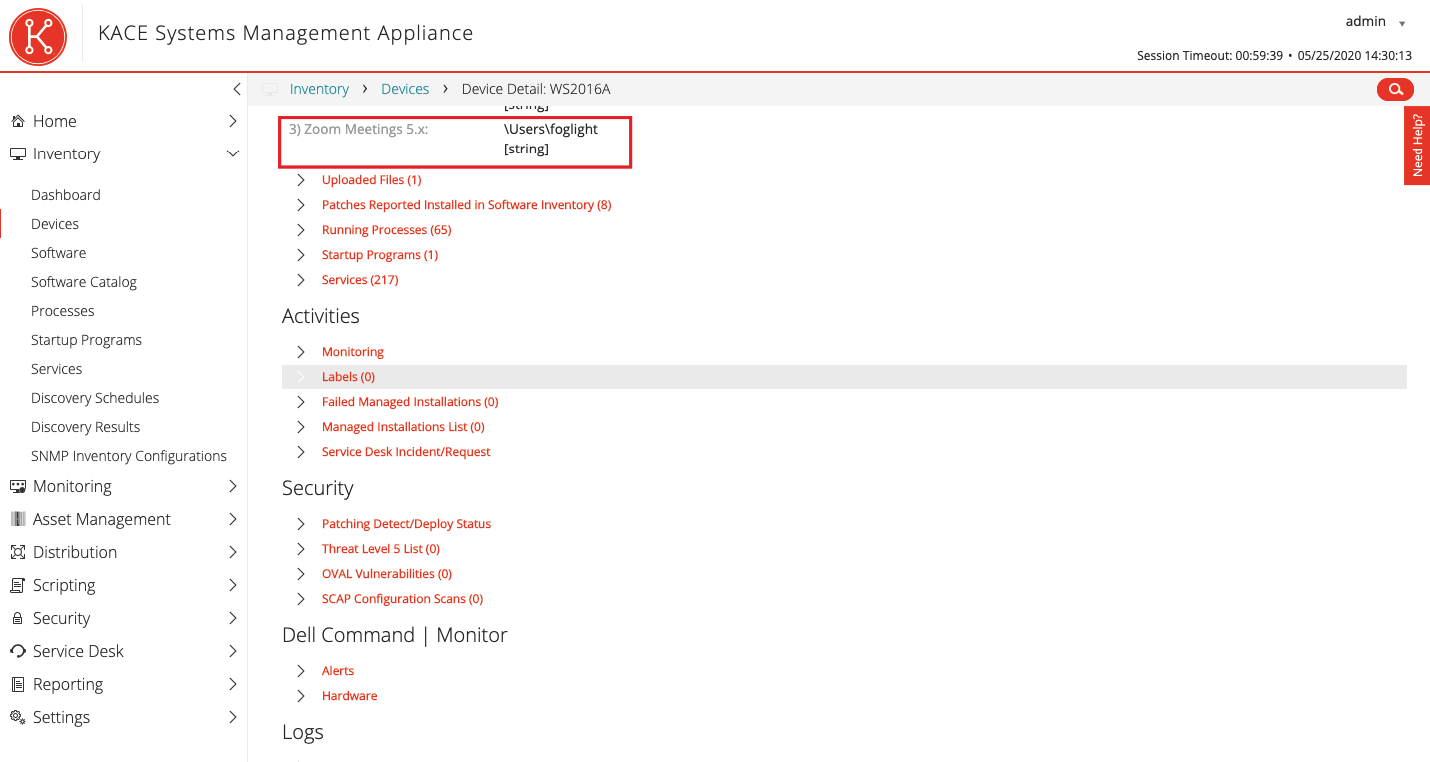
Now it remains to generate a PDF report (txt, csv, html, xls formats are also available) and send it to interested colleagues. Reports can be generated on a regular basis.
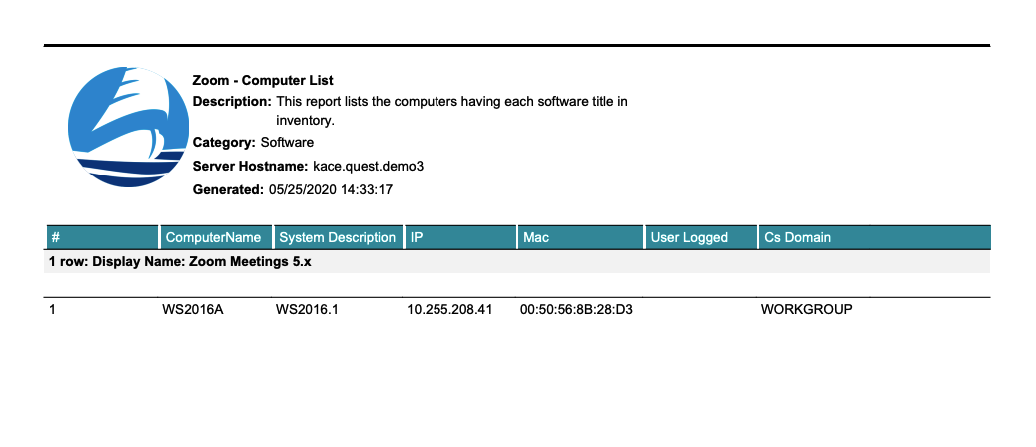
After identifying an unauthorized installation of Zoom, it can also be deleted by a known uninstall command. By the way, in addition to searching the directory, you can ask about Zoom in the Windows registry from the same script.
Checking the external IP address of the user device
Another popular case in a pandemic is to identify the user’s external IP address. It may be useful for compiling a list of locations of remote employees or some other type of reporting.
ShellCommandTextReturn(nslookup myip.opendns.com resolver1.opendns.com)The result for each workstation will be like this. The first address is the resolver address, and the second is the user address.
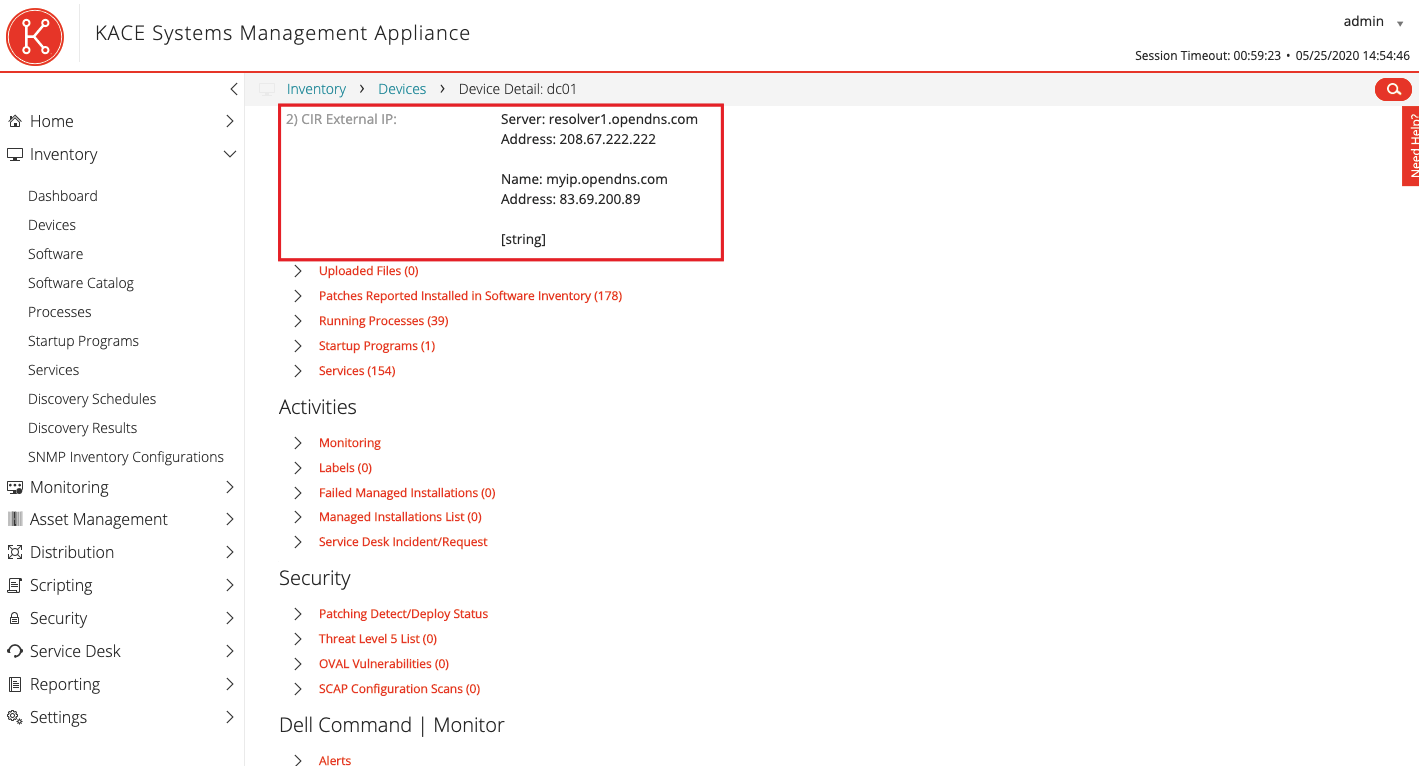
This information can also be issued in the form of a report and sent if necessary. The script can be complicated and requested, for example, geographic location and provider.
Windows License KMS Expiration Check
In a normal situation, there is a KMS server inside the company that activates the operating system. If activation has a deadline and the KMS server is accessible only from the internal network, Windows extension on remote workstations will not be possible. To identify inactive workstations, Windows has a special slmgr.
ShellCommandTextReturn(cscript.exe c:windowssystem32slmgr.vbs /dli) When it is executed, the following output is displayed:
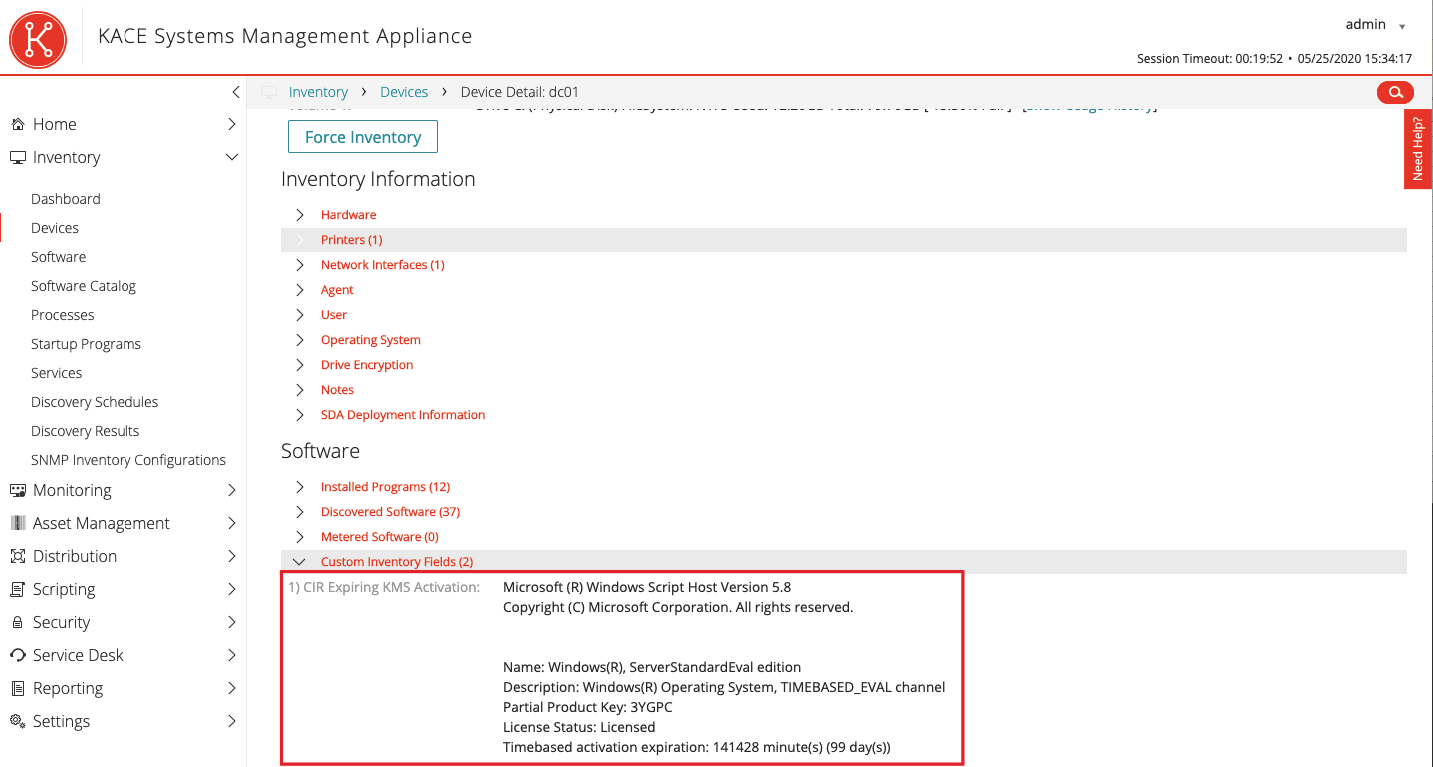
Thus, it can be seen that the system is activated from KMS and administrators can make a decision on switching to MAK activation for each individual workstation.
Tell us in the comments what other tasks you solve at the workstations of remote employees.
Other KACE articles:
Inventory from I to Z. We consider software licenses.
Inventory from I to Z. We consider IT assets.
IT management without knots and with a hitch.
On our site you can see all the features of the Quest KACE platform and send a request for a distribution kit or a pilot project through the feedback form.

![[Подборка] Useful articles about relocation in the USA: choosing a visa, finding a job, salaries and taxes](https://prog.world/wp-content/uploads/2020/09/1599684933_v1-768x403.png)