The most unusual password rules
Due to the growth of CPU and GPU computing power, password generation rules are periodically reviewed. Experts usually focus on the indicator information entropy (in bits). But in relation to passwords, this is not a universal measure, because the space of possible choices is not uniform, that is, different elements of this space occur with different probabilities. Therefore, there are more effective techniques for cracking password hashes, including dictionary attacks, rainbow tablesand more recently with the use of genetic algorithms and neural networks.
Since there are no uniform password rules, many companies publish their own recommendations, which differ greatly from each other. Sometimes these rules are quite extravagant.
In collection Dumb Password Rules collected several hundred sites with non-standard rules for passwords.
For example, some sites severely limit not only the minimum, but also maximum password length. For example, in 14, 16 or 32 characters:

Others forbid using a sequence of three or more identical characters:

Some require you to enter the password only with the mouse, choosing six of the ten digits:

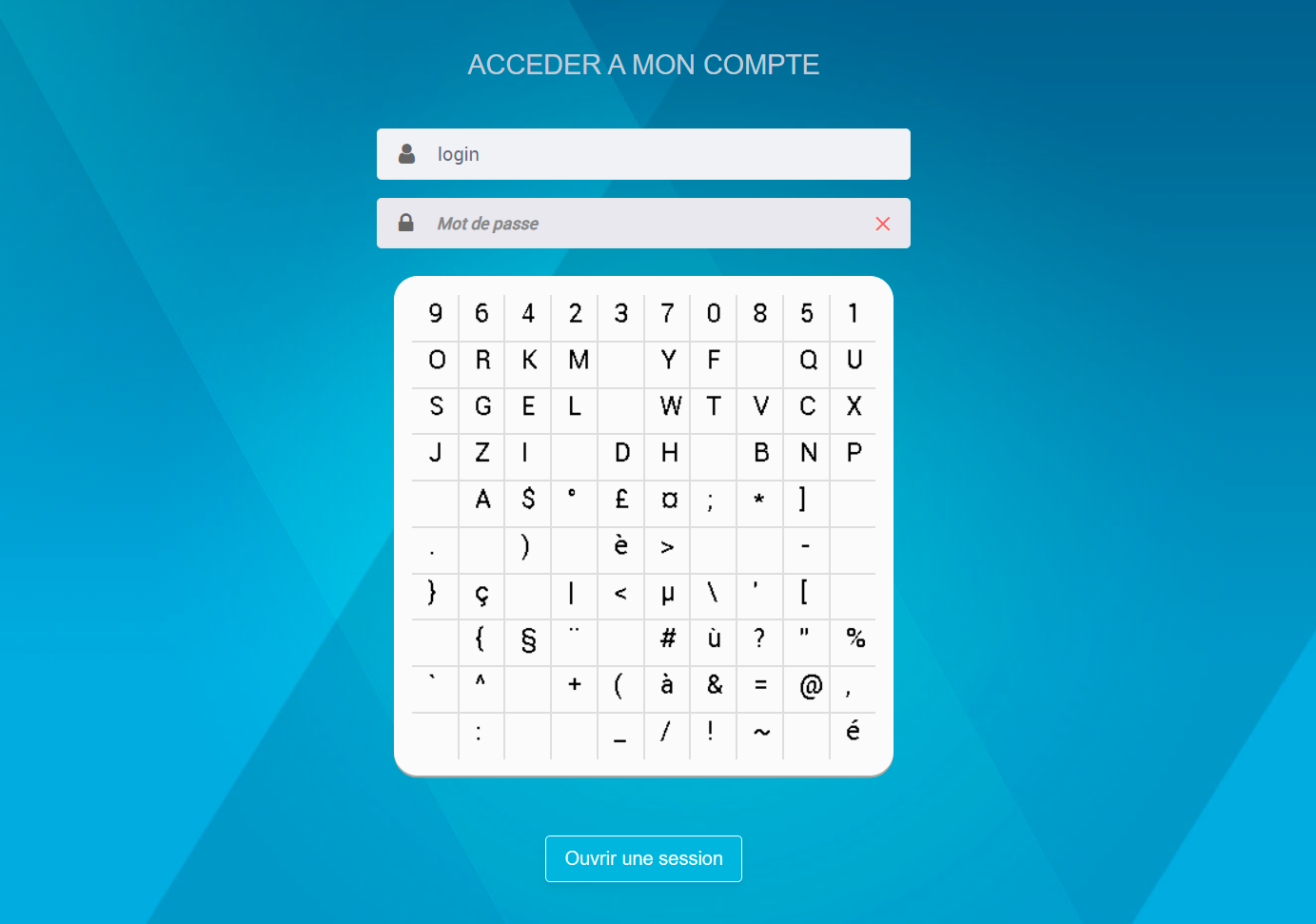
At one of the banks, the password must also be entered with the mouse, choosing characters on a very unusual on-screen keypad (on KDPV).

Note. If your company happens to be in this listyou can apply pull request for deletion.
By way of contrast, below are basic guidelines for generating strong passwords from a few reputable organizations and companies.
Recommendations for generating strong passwords
In 2017, the US National Institute of Standards and Technology (NIST) updated password specifications that are recommended as NIST standards. The new requirements are set out in NIST Special Publication 800-63Bsection 5.1.1.2 “Memorable secret verifiers” (NIST, 2017).
The main requirements of NIST 800-63B for verifiers (companies and organizations) that establish their own password policies:
- Verifiers should not set password rules, such as requiring a combination of different types of characters or prohibiting consecutive repetition of characters.
- Verifiers should not require random or regular password changes, such as the previous 90-day rule. On the other hand, changing the password should be mandatory in case it is compromised.
- Passwords must be at least 8 characters long.
- Password systems should allow subscribers to choose passwords of at least 64 characters.
- Passwords must allow all printable ASCII characters, the space character, and Unicode characters.
- When setting or changing passwords, the verifier must inform the subscriber that he needs to choose a different password if he has chosen a weak or compromised password.
- Verifiers should offer recommendations, for example, password strength meterto help the user choose a strong password.
- Verifiers must store passwords in a form that is resistant to offline attacks. Passwords should be salted and hashed using an appropriate one-way key derivation function. The key derivation functions take a password, a salt, and the required computational resources (cost factor) as input, and then generate a hash of the password. Their goal is to make each password guessing attempt by an attacker who has obtained the password hash file costly and therefore the cost of a guessing attack is high or prohibitive.
Additionally, in questions B05 and B06 in the FAQ section of the NIST documentation for updated special publications (NIST, 2020), the organization has officially clarified that the mandatory password change “reduces the overall security of the password system” and should not be used. According to NIST’s explanation, changing passwords periodically reduces their entropy. Although this is a rather controversial issue, on which there is no consensus.
In addition, there is no consensus on all other rules for generating passwords, including the minimum length, minimum entropy, the presence / absence of special characters.
As an example, we can cite recommendations for creating strong passwords from leading computer corporations: Microsoft, Google and Apple.
Microsoft
Adviсe for creating secure passwords:
- Minimum 12 characters, preferably 14
- Upper and lower case letters, numbers and symbols
- It is forbidden to use words from the dictionary, as well as the names of people, symbols, products and companies
- The password must be significantly different from the user’s previous passwords
- An easy-to-remember but difficult-to-choose phrase. As an example, Microsoft cites
6MonkeysRLooking
Recommendations for passwords:
- Minimum 12 characters
- Upper and lower case letters, numbers and ASCII characters
Google recommends maximizing password entropy by creating very long passwords. To make them easier to remember, you can take familiar passages of the text:
- Lyrics from a song or poem
- Meaningful quote from movie or speech
- Excerpt from a book
- A series of words that matter to you
- Abbreviation: you can make a password from the first letter of each word in a sentence
Apple
Requirements to your Apple ID password:
- Minimum 8 characters
- Letters in upper and lower case
- At least one digit
Well, a useful recommendation for any passwords is to use a good password manager, rules for encrypting and backing up private data, as well as two-factor authentication.
If you come across a website or other computer system with extravagant password rules, you can add it to the collection Dumb Password Rules and mention in the comments to this article.




