The cinema is protected. How we prepared for a media content security audit
From the text you will learn:
- why watch the credits at the end of the film to the end;
- how many audit questionnaires need to be completed to be sure that the movie is protected;
- Why a media security audit is best avoided in a baggy hoodie.
 A source
A sourceIn the field of information security consulting, typical work has long been defined. This is the protection of personal data and trade secrets, attestation of state information systems, information protection in financial organizations, ensuring the security of critical information infrastructure, forming an information security development strategy, etc. The more interesting it was to get a task that was non-trivial for the domestic information security market.
Initially, the request received by “LANIT-Integration” from one Russian company, contained a minimum of information and sounded like this: “Good afternoon! Please tell me if you can help us: we need to undergo an audit for our organization’s compliance with the MPAA information security requirements. “
There was a need for a comprehensive study of this issue. First of all, it was necessary to understand what the MPAA is.

This logo is familiar to patient and stubborn viewers, that is, those who watch to the end not only films, but also credits… A source
The very first link in the Google search engine Yandex gave us the following response: “Film Companies Association of America (MPAA, English Motion Picture Association of America, originally Motion Picture Producers and Distributors of America (MPPDA), is an American non-profit organization founded in 1922 that brings together major filmmakers to advocate for their business interests. ”
The importance of this association can hardly be overestimated, especially given the composition of the participants. The seven largest Hollywood studios are members of the American Film Association: The Walt Disney Company, Sony Pictures, Paramount Pictures, 20th Century Fox, Universal Studios, Warner Bros, Netflix.
From this we can make a simple conclusion who is the general customer for our client.

This turn of events sparked our genuine interest in what the key players in the global film industry can make. As we studied this issue, it turned out that the circle of actors in the project is becoming noticeably larger.

In addition to the American Association of Film Companies, the requirements are formed by the specialized International Content Protection Association, and the verification of the implementation of the requirements is carried out by a network of trusted partners (Trusted Partner Network – TPN), created jointly by the two associations. A logical question arises why such forces were used to ensure the security of media content.
Who and what are film studios afraid of?
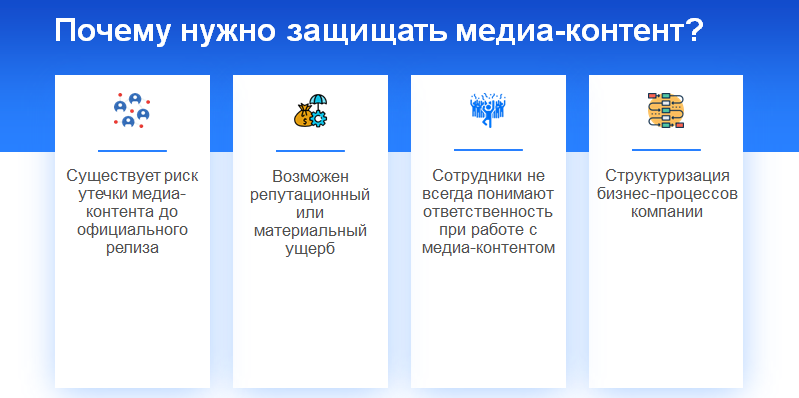
Of course, we all know various p2p file-sharing networks, on which, for example, you can download or watch movies bypassing the requirements of copyright holders. But how do they appear there? Often, such resources are the first to publish “pirated” videos from cinemas, from where the commercial return on the film starts. But an even greater danger for producers of media content is the leakage of material before the official release. With this development of events, companies receive serious financial and reputational damage, since the unassuming audience for the most part prefers not to pay for a product, but to receive it for free, even if in a lower quality.
Having identified the main reasons for the formation of the MPAA standard, we get:
It is not every day that office workers will be able to get involved in the field of cinema, and even as part of their work.
So what is the complete list of companies interested in media security? Having studied the market a little, we get the following.

We decided. Now to work. What is the standard that our customers need so much? After examining the structure, it became clear that the MPAA standard is structured in a rather familiar way, all the measures necessary for implementation are divided into three groups: information security management, physical security measures and technical measures.
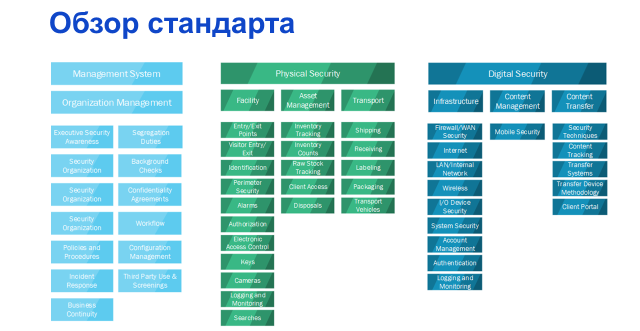 Standard overview
Standard overviewHaving analyzed the standard in detail, for the greatest convenience we have created a checklist for the implementation of security measures. Since the standard is in English, and, unfortunately, not everyone can freely read and translate the rather difficult written technical literature, we also translated it for our colleagues and for the customer. See what happened, can be here – plates of this size, to put it mildly, are not very convenient to insert as illustrations in a post (take care of your eyes️).
How we are working:
- Do it once. Let’s examine what we have to work with.
- Do two. We design an information security system and develop physical and organizational measures.
- Do three. Buy, implement, train.
- Do four. Get audited and help keep everything up to date.
The customer sent us a questionnaire from auditors, which consisted of 36 domains and more than 500 questions, which would give auditors clarity about the current status of compliance with the requirements of the standard. It became clear that the approach of the auditors is quite serious. But at the same time, there is something to start from.
Filling out the questionnaires, it became clear to us that, in fact, the company was concerned about information security in an amount insufficient to meet the requirements of the standard. First of all, it was necessary to determine the content itself, which is so necessary to secure, and this is the most interesting thing. After conducting an information survey with the customer, we found out that the media content for the company is the rendering results (in fact, frames from the film), 3D models, and also during dubbing, translation scripts, phrases, remarks appear, from which you can compose a whole plot.
Getting started
We examine business processes, obtain a diagram and description of business processes. We inspect information systems, services and infrastructure, get an infrastructure scheme. We examine the implemented measures, get an understanding of the degree of implementation of the requirements. Based on the results, we form recommendations. There are recommendations, let’s go to fulfill them.
Next, we prepare a technical project. We collect the specification and description of the information security system in a convenient form. We go through the list of requirements / recommendations, opposite each requirement we write explanations.
- Organizational measures are implemented not only by the approval of a policy / order / regulation in the company, but also by the implementation by employees of all procedures described in these very policies, orders and regulations.
- Technical measures are implemented both by imposed information protection tools and built-in security mechanisms. Fortunately, there are no requirements for certification of FSTEC security products. It is clear that all the processes associated with the implementation of technical measures must also be described in the organizational and administrative documentation.
- Physical security measures are implemented both technically (access control, video surveillance, fire safety, etc.) and organizationally (regulations for moving / removing drives, regulations for visiting a workplace, regulations for checking physical security systems, etc.).
Let’s talk about the most unusual requirements of the standard. During the implementation of the standard’s protection measures, I had to face some funny and sometimes slightly exaggerated requirements, for example:
- prevent the use of jailbreak, rooting and other things on working mobile devices (hardly anyone thought about this before in companies working with media content);
- use pseudonyms (AKA) for clients in the process of processing media content (obviously so that employees cannot know exactly who the customer is);
- mark each visitor with an identification badge or sticker, which should always be visible (we know all visitors – we are less worried about our content);
- bring food only in transparent containers and bags (in order to prevent illegal bringing / taking out of devices for collecting information);
- implement a dress code policy in such a way as to eliminate baggy pants and hooded sweatshirts (also in order to prevent the entry / exit of confidential information).
Documentation validity period
Many customers, unfortunately, believe that the documentation being developed is valid only when passing an audit, and then come what may. The simplest (profitable, if you know what i mean) solution was to take matters into their own hands and help the client keep everything up to date.

The audit was similar to the examinations that we are used to seeing in Russia (most often it is ISO 27001), but, just in case, in order.
First, a request is made to TPN for an audit. Next, the questionnaires that we talked about earlier are sent. After they were filled out and sent (of course, having previously implemented all the requirements), TPN determines the auditor (we got Alex from London). The first thing he did was to request a list of developed documentation in English (however, the standard does not require the development of documents in English). As it turned out, the plan was as follows: an expert on the composition and names will understand how this corresponds to the best practices, and already at a confrontation he will ask what is written in them. Since document verification was, in fact, based on our eloquence, Alex put a lot of emphasis on the technical side of the issue: all the settings of the network equipment were checked, the progress of each business process was demonstrated, the hardening of selected machines from each network segment was checked, and it was even checked. history of browsers on PCs that do not have Internet access. Also, much attention was paid to the issue of video surveillance, access control, etc.
 At lunch, the auditor relaxed and said that the auditor is not his main profession, he runs the same company that works with media content. Auditing is a hobby and some additional income (of course, Alex passed all the required exams to obtain this status).
At lunch, the auditor relaxed and said that the auditor is not his main profession, he runs the same company that works with media content. Auditing is a hobby and some additional income (of course, Alex passed all the required exams to obtain this status).Unlike the same ISO 27001, where the presence of a certificate allows you to declare compliance with the requirements of the standard (by no means complete security), in MPAA / TPN the audit results are recorded on the TPN portal, and it will also indicate exactly how this or another requirement so that the future counterparty could personally decide whether the set of measures is sufficient to work with them or whether it is worth thinking about.
All in all, it was a familiar job of preparing for an audit. But we got a lot of pleasure, understanding what turned out to be an interesting industry – the production and distribution of media content. Now we are sure that the customer has everything under control and no one (except for a person in a hoodie and with an opaque container) will be able to see the new movie ahead of time.
I will be glad to answer your questions in the comments.