Security Week 52: Managing SunBurst Attack Through DNS Queries

From March to June of this year, a malicious library with a developer’s digital signature was distributed from SolarWinds update servers and thus reached 18 thousand of the company’s customers. The infected module was tuned to provide maximum stealth, and only a select few were listed for the next stage of the attack. A set of backdoors was used for espionage (and not, say, installing a ransomware followed by extortion). The attackers analyzed the infrastructure of the affected organizations and also redirected emails to their servers.
This is a complex targeted attack, the analysis of which is just beginning: the reports of FireEye, Kaspersky Lab and Microsoft did not reveal the entire scheme of the malicious code. But this is definitely one of the most successful attacks on the supply chain with a perfectly matched entry point into the corporate infrastructure.
Sources:
– Report FireEye: An overview of targeted attacks.
– Report Microsoft: A closer look at malicious code spread from SolarWinds servers.
– Publication Kaspersky Lab: analysis of the scheme of working with the C&C server via DNS queries.
– Article on the Volexity website: Examples of PowerShell code for distribution over the victim company’s intranet, possible links to earlier attacks.
– Statement and FAQ from SolarWinds about the incident.
– Related news on Threatpost: about SolarWinds hack, about detection a malicious module in Microsoft networks, about affected in public sector USA (according to media publications).
In October this year, as part of a conference call with investors, the CEO of SolarWinds said that no other company has this level of access to the infrastructure of many large organizations. This also made the company an obvious target for a hack. Platform Solarwinds orion designed for centralized management and monitoring of the IT infrastructure of an enterprise, which means that this software has almost unlimited access to all corporate services. The attackers broke into the SolarWinds.Orion.Core.BusinessLayer.dll library, which is part of more than a dozen software solutions. The files with the backdoor were distributed for several months from the vendor’s official update server and were signed with a legitimate digital signature. How it happened is not yet known exactly. Most likely, there was a set of vulnerabilities.
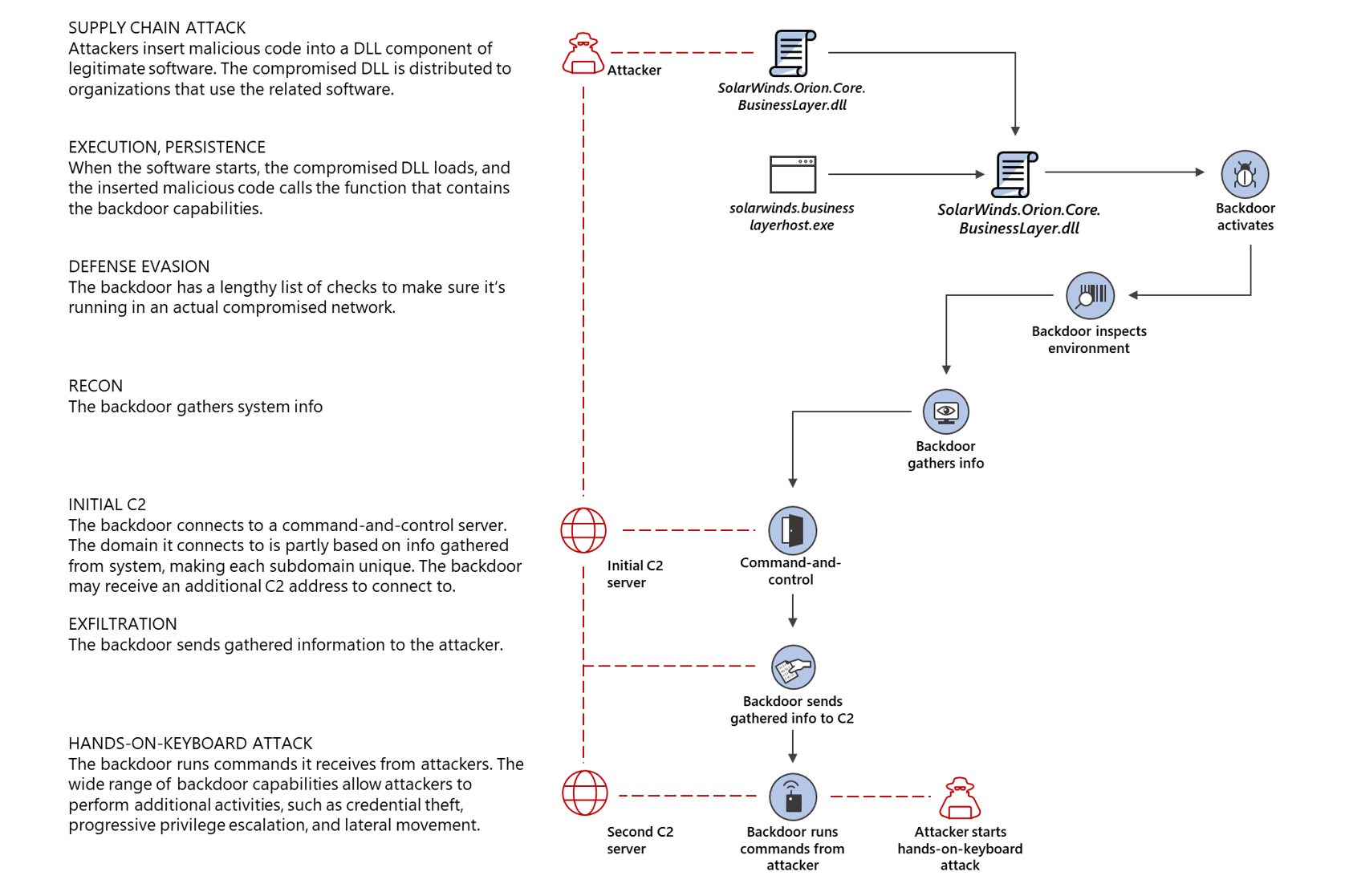
The malicious code itself is written in such a way as to ensure maximum secrecy – for example, the first communication with the C&C server occurs two weeks after the backdoor is installed. The general scheme of the attack at the initial stage is provided by Microsoft experts. A rather interesting technology is used to select promising victims: data from the backdoor is sent to the C&C server as part of a DNS request. If the organization is of interest, a response request arrives directing the backdoor to a second C&C server, and data is stolen in the process of interacting with it. Most likely, out of 18,000 potential victims, dozens of companies were actually affected.
This article by Kaspersky Lab experts examines interaction via DNS queries in more detail, including the data encryption method. Decrypting the information allows you to determine the network domain of real victims. Among the hundreds of victims in 17 countries identified by Kaspersky Lab experts, not one passed the initial attacker filter. Microsoft experts have identified 40 victims of the attack.
Companies using SolarWinds software should obtain updated software from the manufacturer at this time. A set of indicators of malicious activity published on Github by FireEye.