Reliable, elusive, bulletproof: what kind of hosting does cybercrime use?
What is Bulletproof Hosting
Bulletproof Hosting, or BPH, is hosting that allows you to conduct illegal activities that are prohibited by regular providers: hosting malware, pirated content, or stolen data.
BPH providers either ignore complaints and requests from law enforcement or warn customers ahead of time so they have time to adapt their business. In many cases, BPHs allow an attacker to hide their true identity.
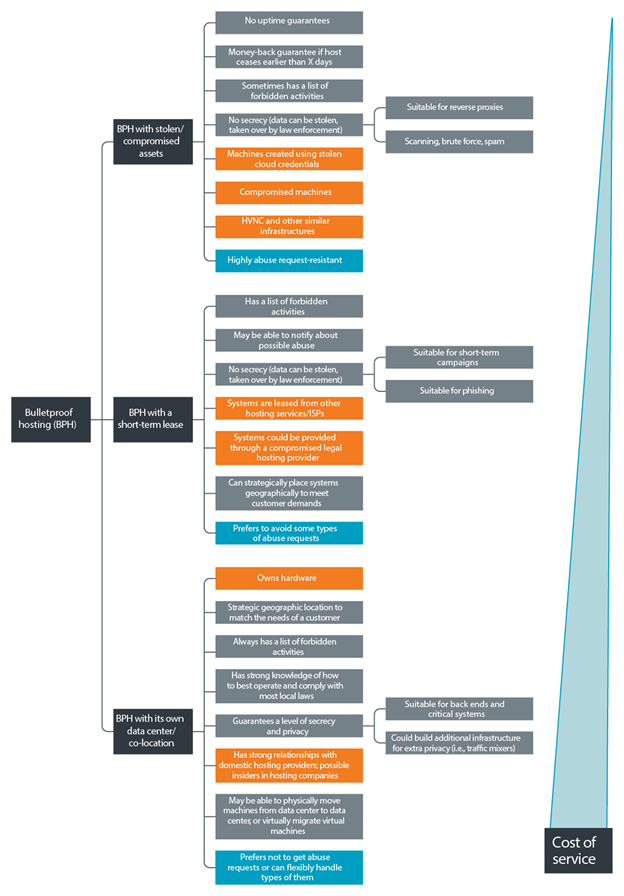
Varieties of BPH. Types of services and cost. Source (hereinafter, unless otherwise noted): Trend Micro
BPH has a high level of resilience using a short-lived infrastructure of hijacked or compromised servers. BPH providers are not the official owners of the resources they provide, so any claims will “fly” to the real owner, not to them. The consequence of this is that any host on their network can be deleted at any time, for example, after the owner discovers a compromise.
Such BPHs are extremely cheap and convenient for performing quick operations: spreading spam, placing reverse proxies, bulk crawling and brute-force. Even if the hijacked server is removed or deleted, only a small amount of information is lost.
Another type of BP hosters resells services from legal companies. Their bulletproofness is ensured by the ability of resellers to closely match the needs of cybercriminals, as well as through established relationships with legitimate hosting providers when handling abuse requests. In some cases, resellers can act as intermediaries in resolving conflicts and disputes between providers and consumers of hosting services.
For systems requiring long periods of availability, hosting in data centers where the BPH provider owns the infrastructure is a more viable approach. These providers tend to strategically allocate their resources and build or lease infrastructure around the world, taking into account local legal regulations, geographic and national characteristics, the professionalism of local law enforcement agencies and the level of corruption in government agencies. This BPH is the most expensive, but also the most stable.
Ways to ensure “impenetrability”
Each BPH-provider has a limited list of services that it provides to criminals. Depending on the agreements with upstream providers, they publish a list of strictly prohibited activities and a list of what is considered acceptable.
Using the features of legislation
The source of such restrictions is the differences in the laws of different countries, therefore, the subject of special attention of BPH providers is the region of the data center location, information about the registration of the company and partners in network peering.
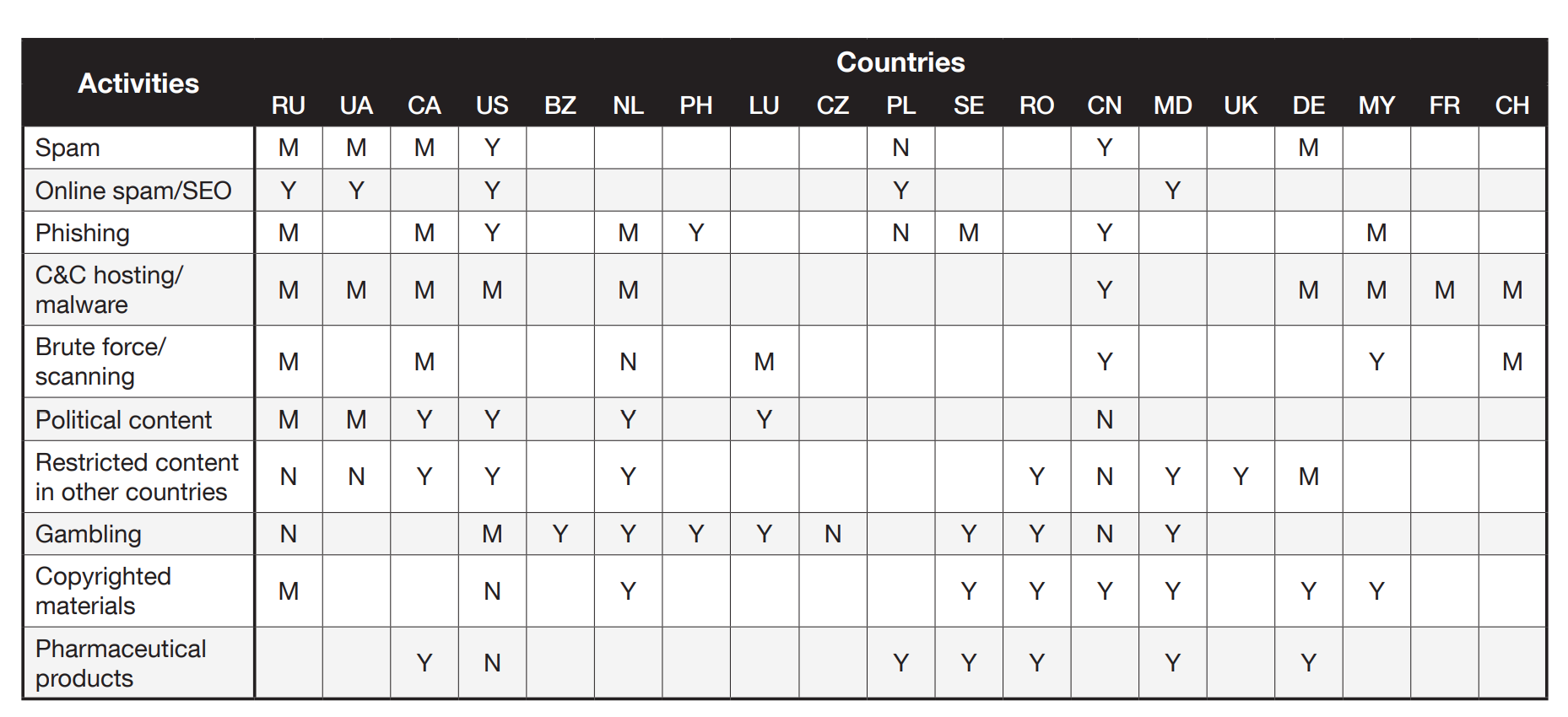
Criminal activities and their degree of acceptability in different countries. Y (yes) means that the specified actions, according to the reviews of the users of “underground” hosting services, are possible using servers located in the marked country, N (no) – for the specified actions, servers in this country are strongly discouraged, M (maybe) – using servers is possible, but with some restrictions
One of the most popular countries to host BPH infrastructure is Ukraine. The reason for this is that government regulation and law enforcement in this country in many cases is much less stringent than in neighboring countries. At the same time, the actions of Ukrainian law enforcement officers are less predictable: there are cases when the SBU conducted independent investigations and arrested the owners of bulletproof hosting…
Switzerland and the Netherlands are also popular with BPH owners as suitable countries to set up proxy hosting pad companies. This is due to the fact that, in accordance with the legislation of these countries, the hosting receives a notice of the complaint in advance, which makes it possible to move the systems to safe locations.
Chinese legislation is quite tolerant of spamming and network scanning, but it reacts extremely harshly to all types of activities related to gambling or political activity.
In Canada, the removal of content requires a lengthy preparation of documents, on the basis of which a court decision is made, and only then actions are taken with equipment and data.
In the United States, it is considered acceptable to post pornographic content, with the exception of, of course, child porn, but spamming, network scanning and brute-force leads to numerous complaints. In addition, US law enforcement officials are intolerant of violations of copyright laws (DMCA and other similar acts).
Russia is very strict about pornographic material, and most of the pornographic content is considered unacceptable. On many hosting sites, materials related to drugs and political content are classified as prohibited. However, users of such providers note that they show considerable flexibility, warning in advance about the received complaints, and also tolerate malicious activity as long as it is not directed against Russian companies and citizens.
The Seychelles, Belize, Dominican Republic and Panama are extremely popular as a BPH destination due to their good internet channels and loyal laws that allow for a very leisurely response to any complaints. For such BPH services, the term “offshore hosting” has even appeared.
Anonymity
One of the most important characteristics of BPH is the degree of anonymity. The ability to hide the identity of the owner of a criminal resource, accept anonymous payments in cryptocurrencies, register domains for fictitious data and other similar properties are decisive when choosing a platform for criminal hosting.
Anonymous hosting advertising
Even some legitimate hosting platforms advertise anonymity. For example, Domains by Proxy is building a business by hiding the identity of the client from most public inquiries. However, it should be noted that the company does respond to requests for disclosure of information about the owner of the site in the event of claims of copyright infringement.
Domains by Proxy Advertising
Flexibility and adaptability
These characteristics are extremely important for BPH providers. Their practical manifestation can be, for example, moving servers or virtual machines from one country to another, if unexpected legal problems arose in the previous location. This ensures that the malicious service continues to operate despite attempts by law enforcement agencies to seize the equipment. When bundled with an external reverse proxy server, this hosting model is ideal for high availability BPH services.
DDoS protection
A reliable network infrastructure is only half the battle. Like any other site on the Internet, cybercriminal resources can be targeted by cyber attacks ranging from denial of service (DoS) to hacking attempts. The likelihood of such incidents with such resources is higher than with ordinary sites: disgruntled users can be on ordinary sites, but visitors to hacker resources are more likely to arrange an attack.
Downtime during a DDoS attack can affect the reputation of a resource, as a result of which its audience will go to competitors, and the site owner will lose income.
DDoS attacks can be carried out at various layers of the OSI model. As a rule, attacks on level 7 require more sophisticated methods, but at the same time they are more difficult to defend against than against the common SYN-flood (level 4). That is why many sites use professional services that protect them from DoS attacks at the application level, and criminal forums in this regard are no different from legal resources.

Screen of one of the services for protection against DDoS attacks
Anti-scraping
Another problem faced by operators of criminal forums when choosing a hosting is that many search engines, organizations, law enforcement agencies and researchers are trying to automate the process of identifying illegal content.
The information collected is then published in threat reports or used in law enforcement investigations. This could attract unwanted attention and damage the reputation of the forum.
Different hosting mechanisms use different mechanisms to prevent scraping. For example, guests may have a limit on the number of pages they can view during the day.

Anti-scraping notification
Other forums use captcha or security questions to make sure they are dealing with a live person.
Countermeasures recommendations
It is quite difficult to counter the criminal resources hosted on BPH. In the course of our research, we developed the following methods that can help identify companies providing illegal hosting services. Here’s what you can do:
- determine which ranges of IP addresses are on public blacklists; pay special attention to addresses associated with a large number of public requests for abuse, as this may indicate BPH activities;
- analyze autonomous system behavior and peering data – this can also help identify BPH-related activity.
- after finding one BPH host, use the resulting digital fingerprint to find others that may be associated with the same provider.
We suggest the following as measures that can facilitate the termination of the activities of clandestine hosting companies without having to find or shut down their servers:
- sending duly filed abuse requests to the suspected illegal hosting provider and its upline partners;
- adding ranges of IP addresses of BPH networks to popular black lists;
- increasing BPH operating costs to undermine the profitability of their business;
- undermining the reputation of the BPH provider in the cybercriminal underground – creating accounts on underground forums and publishing on their behalf posts in which doubts about the safety of BPH or its possible cooperation with the authorities are expressed.






