Samsung (Smart Things) and Amazon (Sidewalk) also have similar mesh networks using the LoRa protocol. In principle, this infrastructure can be used for peer-to-peer messaging, as well as for retrieving data from devices outside the Internet access zone.
The first version of FireChat appeared in March 2014 for iOS, in April – for Android. Among the co-founders of Open Garden and the developers of the program are Stanislav Shalunov and Greg Hazel from BitTorrent, where they made the uTorrent torrent client (200 million users). There we met.
The entrepreneurs probably hoped that FireChat would become as successful as P2P file-sharing applications. If you imagine this picture, then the whole world can be united into a mesh network, and the Internet becomes practically unnecessary! Even website hosting can theoretically be smeared across a distributed network. Such a fantasy.
The main problem of FireChat during the mass protests in Hong Kong was security. The very architecture of an open mesh network assumes that all users of the application “shine” like radio beacons at a distance of 60 meters, or even more. So it was very easy for the police to catch them. The presence of the program on the phone clearly proved guilt. It can be assumed that hundreds or thousands of users were arrested thanks to FireChat. In addition, no encryption was used in the applicationso no messages were really private.
Perhaps criticism from information security specialists influenced the decision of the American company Open Garden to stop development and not publish the source code. Well, or the guys saw that the worldwide popularity of torrents did not shine for them, and the development of the program went completely the wrong way.
When FireСhat appeared, it was the only program of its kind that allowed users to create mesh networks offline (without the Internet) and exchange messagesone…
The tool, which was conceived for the communication of people, has de facto turned into a tip for repression and physical violence. Perhaps there is some kind of tragedy in this.

Photo from article “FireChat is the messenger running the protests in Hong Kong”, The Guardian
It is all the more offensive if FireСhat was created specifically for Hong Kong, like the development of a similar Commotion Wireless application in 2011 funded by the US State Department ahead of the Arab Spring… We wanted the best, but it turned out as always …
After FireСhat, Open Garden traded electronic SIM cards (eSIM), promoted its cryptocurrency, but in recent years nothing has been heard about her.
In general, the FireChat application was not very high quality. First, it’s closed source. Secondly, for registration it was necessary (!) To need access to the Internet, although later it worked offline. In short, a strange program. Maybe it’s good that the developers buried her.
Walkie Talkie Zello
The Internet walkie-talkie is similar in terms of the logic of its functioning. Zello, which is blocked in the Russian Federation in April 2017.
The radio works on the principle of walkie-talkie or push-to-talk. The main advantage is the ability to listen to voice messages over the speakerphone in real time, without touching the smartphone at all, and at the same time be in touch with a large number of users.
Although not text / pictures are transmitted here, but sound, the principle of operation is the same – via a mesh network, without the Internet. Close to each other users connect with each other directly and transmit messages further along the chain. Importantly, it uses end-to-end encryption (E2E).
In Russia, the application has gained particular popularity among truckers and other motorists, since it is very convenient (and pleasant) to talk with fellow travelers who are driving along the same highway. They will tell you about the radar in the bushes, about an accident on the road, etc. Repression by the state began after the massive protests of truckers in connection with the introduction of a mandatory payment to billionaire Igor Rotenberg for the passage of heavy trucks on the roads of Russia (system “Plato”). The protests were coordinated through Zello, so they decided to block the program.
 This was the first time the authorities tried to break a VPN messenger. It took a full year to block over 4,000 IP addresses from the AWS Cloud, which was unsuccessful. Then RKN went to blackmail Amazon, threatening to block 26 AWS subnets, in the amount of 13.5 million addresses.
This was the first time the authorities tried to break a VPN messenger. It took a full year to block over 4,000 IP addresses from the AWS Cloud, which was unsuccessful. Then RKN went to blackmail Amazon, threatening to block 26 AWS subnets, in the amount of 13.5 million addresses.
Amazon was not ready for war – and refused to provide Zello services. The service, which had lost its cloud infrastructure, was easily blocked.
Following the success of blocking Zello’s cloud-based VPN infrastructure, the authorities decided in 2018 that they could successfully block the same cloud-based infrastructure of the Telegram messenger. But here I found a scythe on a stone: Pavel Durov invested millions of dollars in the purchase of more and more AWS instances, his brother Nikolai and his colleagues programmed a proxy blocking bypass system, and Amazon and Google withstood the blocking of their subnets in the Russian Federation. As a result, the authorities had to block 18 million AWS and Google Cloud IP addresses, which disrupted the work of large retail companies, top 20 banks, private clinics and thousands of businesses in Russia. After two years of exhausting struggle, the state surrendered: the head of Roskomnadzor was fired, Telegram was unblocked, and the IP addresses of cloud services were removed from the black list.
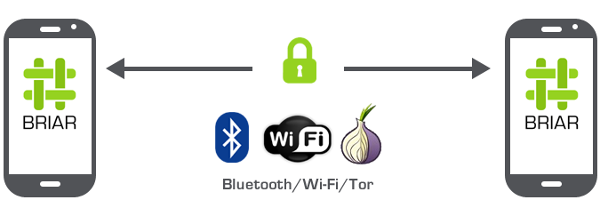
Crypto messenger Briar
Four years ago, in July 2017, the first public beta version of the messenger has been released Briarthat works over Tor or offline, through peering. Its development continued already three years… But the product came out extremely high quality.
This is already honest open source… The application can be compiled from source (step-by-step instruction for Android Studio). It is available in app catalogs (for example, Google play) and is perfectly supported: the latest version 1.2.20 dated April 2, 2021. Implemented strong cryptography, end-to-end encryption.
By default, the messenger works over the Internet using the Tor protocol (onion routing). In this case, the program creates a hidden Tor service on the user’s device and connects to the hidden Tor services of other people from the contact list. In the absence of the Internet, it switches to peer-to-peer communication via Wi-Fi Direct, local area network or Bluetooth.
Of course, when registering with a crypto messenger, you do not need to provide a phone number.
Supports posting (but not files), private groups, blogs / statuses, and RSS imports. There are several useful features such as an application lock (by PIN).
The system is relatively protected from outsiders: new contacts are added via a QR code from another phone (assuming the physical presence of a person) or through the exchange of contacts, or via a unique link. Thus, a person with whom no one is familiar should not get into contacts.

Briar Project is a non-profit project that is currently underway six volunteers… 97.7% of the code is written in Java (+ some Kotlin, Python and Ruby) and is shipped under GPLv3. Shortly after the first release the code has passed an independent security audit from Cure53. She is known for her auditing projects SecureDrop, Cryptocat and Dovecot. So Briar is a really reliable option for peer-to-peer communications.
The only negative is that the app is released Android version only… There is no official version for iOS, and there will not be, because “this platform imposes strict restrictions on developers that do not allow the implementation of some P2P ideas, and is a closed proprietary product.”
But the source code is open source, so theoretically anyone can try to make a third-party implementation of Briar for iOS, for example.
Matrix, Riot, Element
Official client Element (formerly Riot) for a relatively decentralized web Matrix not supports peer-to-peer offline communications and mesh network formation.
This client has gained some notoriety lately. Now the number of Matrix / Element users is comparable to Briar or more. It has end-to-end encryption, bridges to IRC, Slack, Telegram, Jitsi Meet, etc. But there is no peering in offline.
See also:
“Secure Scuttlebutt is a p2p social network that works offline” (there is a client Manyverse for Android and iOS)
PS In addition to FireСhat, protesters in Hong Kong used little-known mexican supplement Bridgefy, which also knows how to form a mesh network and transmit messages offline. In October 2020, the application switched to the Signal cryptographic protocol…
one In fact, there were other applications even earlier, such as Serval Mesh from the project Serval Project or ancient Commotion Wireless from the Open Technology Initiative (funded by the State Department), but all these developments have long been discontinued [вернуться]
Advertising
Powerful virtual servers powered by AMD EPYC processors for any purpose, including VPN setup.
Join the our Telegram chat…



 This was the first time the authorities tried to break a VPN messenger. It took a full year to block over 4,000 IP addresses from the AWS Cloud, which was unsuccessful. Then RKN went to blackmail Amazon, threatening to block 26 AWS subnets, in the amount of 13.5 million addresses.
This was the first time the authorities tried to break a VPN messenger. It took a full year to block over 4,000 IP addresses from the AWS Cloud, which was unsuccessful. Then RKN went to blackmail Amazon, threatening to block 26 AWS subnets, in the amount of 13.5 million addresses.