Osint-San is a tool with which you can become a cyber detective
Hello Habr! This is Maxim Gorshkov, information security specialist at Cloud4Y. I was privileged to be the first to test a new cyber intelligence tool: OSINT SAN. It was developed by my colleague in information security Maxim Ponomarev (Bafomet).
What is it and why
Bafomet decided to create with his own hands an affordable and fast tool for Osint on the principle of “all in one”, accumulating developments and technologies of third-party services. Why do you need OSINT-SAN if all the services included in it can be found on the Internet? The answer is simple: time is money. In the era of big data, saving time is one of the decisive arguments. Instead of a bunch of open tabs and creating paid accounts, you can get everything on one screen. Information comes in one click instantly, and, which is important for pentesters, as part of passive intelligence.
This is especially true if the penetration test takes place in Black Box mode with active opposition from the Blue Team (information security specialists). I want to remind you that any actions with someone else’s infrastructure, especially the critical one (CII), are punishable, up to and including criminal liability. Already, KII services are required to report incidents even about the Nmap scanner in NKTsKI, and this, for a moment, is the brainchild of the FSB of the Russian Federation. So, silence and passive intelligence is the key to success;)
What OSINT-SAN can do
What does the new OSINT-SAN Pro 3.0 offer?
The tool works on Unix systems. I installed on Parrot OS. Installation is simple, python3 is required. Download the directory, install the dependencies. Detailed instructions are in telegram group of the project…
Run using the command line: python3 osintsan.py…
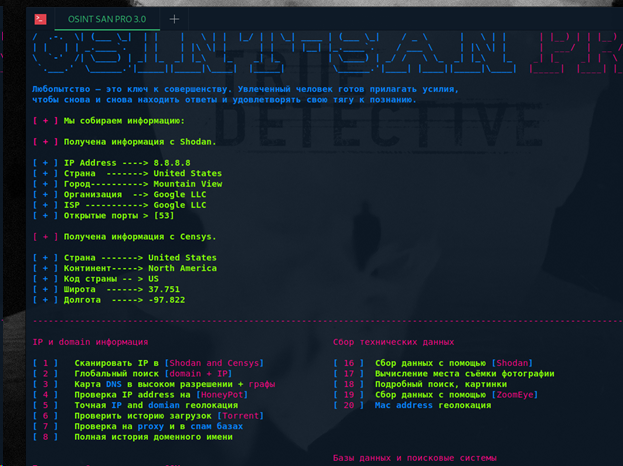
We see a menu with a large number of sections. I will analyze them in detail, choosing Cloud4Y as the object of research:

1) Scanning IP through the SHodan service, well-known in information security circles.

2) Harvester of passive intelligence of the web infrastructure, which allows you to get comprehensive information about the web infrastructure of the company.

Let’s check how some of the functions work. For example, the service discovered the installed CMS in less than a second.

The crawler sucks in site data and stores it in our directory for research.

3) DNS map. Convenient, beautiful. Very informative design. I’m not ready to demonstrate the company’s resources, and strangers are already illegal.
4) Check how deep the rabbit hole is. The tool will be needed to work with developed SOCs or just tricky information security.

5) We get an IP and get several sources of geolocation. It turns out breaking through IP at maximum speed.
6) Analysis of downloaded torrents. Do you remember that torrents live off distribution points and work over UDP? This information helped me a lot in my investigative work. Thus, at one time they caught distributors of child porn through torrents. A powerful tool.

7) Allows you to check the IP address on the proxy. I checked the IP behind which a certain hacker was hiding in one of the incidents I am investigating.

8) History of the domain name. Good scouting option in some cases.
10) Parses all email mentions on the site on the fly. Social engineers, phishers – freedom.
11) Search for information about mobile devices. The module searches the database. Weak, but I think it will improve
12) Database of email-password leaks. I entered one familiar email and received information on leaks in 10 services. The module will be useful when analyzing incidents.

13) Analyzes the reputation set by mail services to email using the database. A good service for checking imaginary counterparties or other lovers of social engineering by email.
14) Android Debug Bridge. This is the name of a module that constitutes 100% criminal liability under a number of articles of the Criminal Code of the Russian Federation (for example, 137 of the Criminal Code of the Russian Federation, 272 of the Criminal Code of the Russian Federation). Be extremely careful with this function. Please use it for reference only. Allows you to get control of the device through the enabled debug mode. I will not provide instructions. Works with modules of the classic Metasploit Framework

15) I’ve already talked about Bigbro. This time, more completely written phishing pages for deanon using JS have been added.
16) Convenient report from shodan.io – a well-known service for finding vulnerabilities on web resources with a built-in api.
17 and 18) Search for Metadata, data about data. If you are a young kulkhacker, you can ask the girl to send a photo from her phone. And then surprise her by knowing everything about her phone and location. 18 The AI-based item will parse the network into similar people. Works through online services.
19) Data collection over the zoomEye network of the same name
20) Another way to “find by IP”
21) Deanon via Telegram. The screenshot below shows the deanon of the “hacker” from the “anonymous” group (judging by his “Guy Fawkes” avatar). A bunch of data, phones, nickname changes, devices … Here’s another call to you that an innocent consent to the processing of “cookies, data, other consent” can lead to a complete deanon.


24, 25) Search engines with reasonable algorithms. They search without ads and any unnecessary garbage, which is more convenient than a regular search engine.


26) Do you remember that all transactions in Bitcoin chains are saved forever? If you install your bitcoin wallet, you can see all your income and expenses. Here’s an example:

27) Search by car, a third-party web service opens.
Other modules correspond to the name and do not require decryption.

What is the bottom line? The result is a finished product that I recommend to adopt for all penetration testers, Osint specialists or detectives. However, I want to remind you that the information is protected by the state (I recommend that you familiarize yourself with 152, 149 of the Federal Law of the Russian Federation), any implicit actions with the data of another person can lead to sanctions (administrative, criminal). Use these tools only within the framework of the law.
Thanks for attention.
What else is interesting in the blog Cloud4Y
→ Frequent errors in Nginx settings, due to which the web server becomes vulnerable
→ Phishing with a fake meeting invitation
→ Cloud kitchen: preparing data for monitoring using the vCloud API and a pressure cooker
→ Prepare vApp template for VMware vCenter + ESXi test environment
→ VMware warned of critical vulnerabilities in remote code execution in vCenter
Subscribe to our Telegram-channel so as not to miss another article. We write no more than twice a week and only on business.