New opportunities for searching security and security threats in PVS-Studio 7.12
Security. What does this word mean to you? Nowadays, companies spend a lot of effort to ensure that their product is protected from hacking and all sorts of information leaks. PVS-Studio decided to help its users in this area and expand the functionality in this area. Therefore, one of the main innovations of the upcoming release will be the appearance in the analyzer of new possibilities for ensuring the safety and security of the code. This will be discussed in this article.

A few words about us in terms of safety and security
Currently PVS-Studio is developing not only as a static analyzer for finding code quality defects (quality control solution), but also as a solution for finding security and safety defects. In the context of security, we are a SAST solution. SAST (Static Application Security Testing) is a type of static code analysis aimed at finding potential security vulnerabilities. Such an analysis can reveal a large number of defects, including even those that did not have time to manifest themselves. As for security, this is a different direction, which is focused on ensuring the reliability and fault tolerance of programs.
As you understand from the title of this article, we are expanding our functionality in these areas. Previously, we already had various tables of compliance with safety and security standards on our website. But it was not very convenient to use this, because this information did not get directly into the results of the analyzer’s work. Now we are not only making the use of these analyzer capabilities more user-friendly (for example, by integrating plugins into the interfaces of our IDEs), but also expanding the existing base by adding support for new standards. An additional impetus for this was the mention of PVS-Studio in the Static Application Security Testing, Q3 2020 report from Forrester Research, one of the leading researchers of the impact of new and innovative technologies on business processes and the market. You can read more about this and how we developed into the SAST and safety solution. here…
New opportunities
Well, in order not to waste time, let’s immediately indicate what exactly was added. So, new, safe and cool in PVS-Studio:
New diagnostic groups OWASP ASVS and The AUTOSAR C ++ 14 Coding Guidelines have been added to the analyzer. Previously, compliance of PVS-Studio diagnostic rules with these standards was available only on our website. There are more than 50 new diagnostic rules!
In the results of the analyzer’s work, information is now given about the compliance of the detections with the SEI CERT standard for safe coding. Previously, this information was also available only on the PVS-Studio website.
The interface of our plugins for Visual Studio, JetBrains Rider, IntelliJ IDEA has been improved for convenient work with analyzer messages that have identifiers of security and safety standards.
New diagnostic groups (OWASP, AUTOSAR) supported in PlogConverter.
New diagnostics (OWASP, AUTOSAR) in SonarQube at the tag level are supported. Carried out work on the classification of our diagnostic rules according to the OWASP Top 10.
Note. Previous versions already supported security standards such as MISRA C: 2012 and MISRA C ++: 2008. At the time of this writing, 74 diagnostic rules have been implemented for them.
We also support the compliance of our diagnostics with the most common classification of potential vulnerabilities – CWE (Common Weakness Enumeration). The number of diagnostics that fit this classification we already have 514…
New diagnostic groups
Let’s talk a little about the new groups of diagnostics (OWASP and AUTOSAR), which were previously present only on our site in the form of comparisons. In the new release of PVS-Studio 7.12, we add diagnostics from these standards in the form of separate groups of rules with their own numbers, documentation and all the other things inherent in our diagnostic rules. That is, while checking the project, the analyzer will give you warnings for new groups, by analogy with the rest of the warnings. Previously, of all the security and safety rules, only PVS-Studio diagnostics corresponding to the MISRA C and C ++ standards had separate groups.
In general, what are these strange words: OWASP, AUTOSAR? Let’s clarify the situation a little.
The AUTOSAR C ++ 14 Coding Guidelines Is a set of guides for writing C ++ 14 code that is designed to work on systems where security and fault tolerance are important. The main field of application of this document is in the automotive industry. But it can also be used in other embedded systems industries.
For this standard, we have created a separate group and assigned it numbers from 3500 to 3999. You can see the comparison of these diagnostics with the AUTOSAR standard. here…
OWASP Application Security Verification Standard Is a list of application and test security requirements that can be used by software architects, developers, testers, application security specialists, vendors and users of tools for developing, building, testing, and verifying secure applications.
As you understand, unlike the AUTOSAR organization standard, OWASP ASVS is not tied to any particular language. Therefore, we have implemented diagnostics of this type in all the languages we analyze (C, C ++, C #, Java). These diagnostic rules have received their group and numbers from 5000 to 5999.
Now let’s move on to CERT. SEI CERT Coding Standard Is a set of standards for writing software to improve the reliability and security of software in C, C ++, Java and Perl. These standards are developed by the CERT Coordination Center (CERT / CC). Their comparison with PVS-Studio rules is presented here…
However, in the case of CERT, we did not create a new diagnostic group. The reason for this is that a significant part of our General Analysis diagnostics falls under this standard. But do not worry, you will still learn the information that diagnostics is a specific CERT rule. It is added to the analyzer output in the same way as OWASP ASVS or AUTOSAR C ++ 14 Coding Guidelines.
At the same time, we continue to support such standards as MISRA C: 2012 and MISRA C ++: 2008. These are software development standards, the main goal of which is to improve the security, portability and reliability of software for embedded systems (juxtaposition).
By the way, we do not plan to stop there and will make more and more new diagnostics aimed at finding security and security errors. This, among other things, we are talking about in our roadmap for 2021…
In plugins
Well, we have added new diagnostics. And where can you see the result of their work? Of course, in our plugins! We currently support displaying security standards information in plugins for three IDEs. These are Visual Studio (for versions from 2010 to 2019), JetBrains Rider and IntelliJ IDEA. The following improvements have been made to enable plugins to display these new triggers:
Added a new column SAST, which displays all information about MISRA C: 2012, MISRA C ++: 2008, The AUTOSAR C ++ 14 Coding Guidelines, OWASP ASVS, SEI CERT Coding Standard from warnings.
Column MISRA removed. Now all information is entered into the SAST column. This same column will be used in the future and with our support for new standards.
Added buttons for new standards that allow you to remove related warnings from the display. In the settings, added the ability to completely or partially disable / enable diagnostic rules for these categories.
Here are a couple of pictures so that you have an idea of what it looks like. In the plugin for Visual Studio 2019, it looks like this:
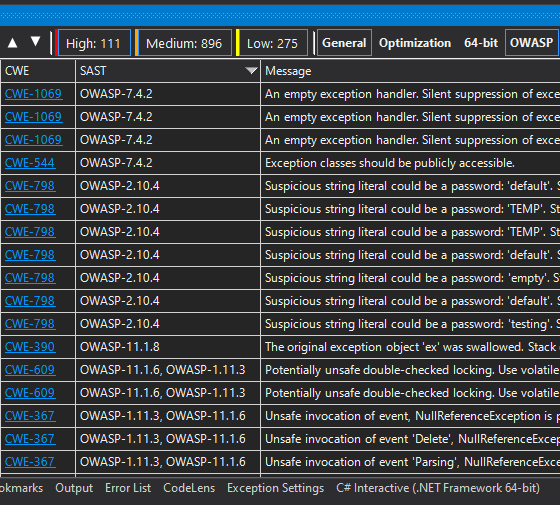
We’ve added the exact same functionality to Rider and IntelliJ IDEA. This is how it looks in Rider:
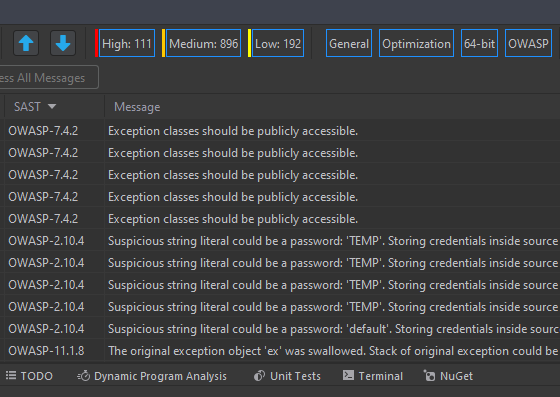
PlogConverter
We could not forget about our utility that allows you to convert reports into various formats. Now all of our report types, into which the analyzer results can be converted, support OWASP and AUTOSAR. For example, let’s take a look at perhaps the most commonly used type for conversion – FullHtml… This type allows you to study the report in a browser: nice and convenient if there is no way to work directly with the plugin in your development environment. Plus, it is convenient to send such a report or a link to it by mail.
Actually, we quickly got the required file and now let’s see it. As you can see, there is a new Total Warnings (OWASP) field in the header that says how many potential bugs you have from this category:

This is how the SAST column itself is displayed:

SonarQube
I would like to say a little about our integration with SonarQube. We provide a plugin that allows you to add messages found by the PVS-Studio analyzer to the SonarQube server message base. Then you can filter messages, navigate through the code to analyze errors, analyze the dynamics of the number of errors, evaluate the quality level of the project code, and so on.
At the moment, we are expanding the capabilities of our plugin by adding tags for diagnostics related to OWASP, AUTOSAR groups. Now the messages from the OWASP group look like this:

We also carried out work on the classification of our diagnostic rules according to the OWASP Top 10. OWASP Top 10 Is a ranking of the most dangerous attack vectors for web applications. Each place in this rating has a description and examples of attack scenarios, as well as links to the rules from the OWASP ASVS standard and the CWE classification that apply to it. For example you can lookwhat one of the places in the rating looks like.
OWASP Top 10 includes vulnerabilities such as:
injections;
broken authentication;
disclosure of confidential data;
external XML objects;
broken access control;
incorrect security configuration;
cross-site scripting;
unsafe deserialization;
using components with known vulnerabilities;
insufficient logging and monitoring.
In SonarQube, they are displayed here:

This is done by analogy with how we already display the CWE, which you can also see in the screenshot. For this we use a dedicated Security Category tab. Here’s an example of what a filled CWE looks like:
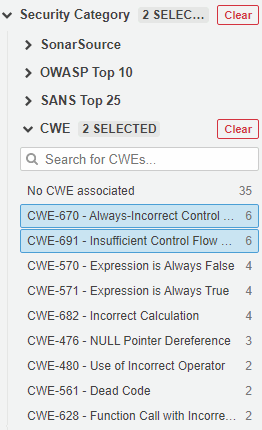
Conclusion
As you can see, this release came out quite rich. The analyzer has received new groups of diagnostics for the OWASP ASVS and AUTOSAR C ++ 14 Coding Guidelines standards. The results of the analyzer’s work additionally began to display information about the compliance of the detections with the SEI CERT standard. The interface of our plugins (Visual Studio, JetBrains Rider, IntelliJ IDEA) has been updated for convenient work with analyzer messages that have identifiers of security and safety standards. Also PlogConverter with SonarQube learned to work with new groups of diagnostics (OWASP, AUTOSAR). And all this is just what concerns the direction of safety and security!
This direction is very important. After all, the elimination of all kinds of vulnerabilities at the stage of software development reduces the chance of security threats in the future. Thanks to this, the company will not have to incur financial losses or lose its rating. Therefore, we try to help our users to avoid problems related to safety and security.
Be happy and keep track of the state of your code. Thanks for attention!
If you want to share this article with an English-speaking audience, please use the translation link: Nikolay Mironov, Paul Eremeev. PVS-Studio 7.12 New Features for Finding Safety and Security Threats.