Network segmentation for the smallest
Introduction
In this article, we will consider:
rules interservice interaction…
Demilitarized Zone (DMZ, Level I)
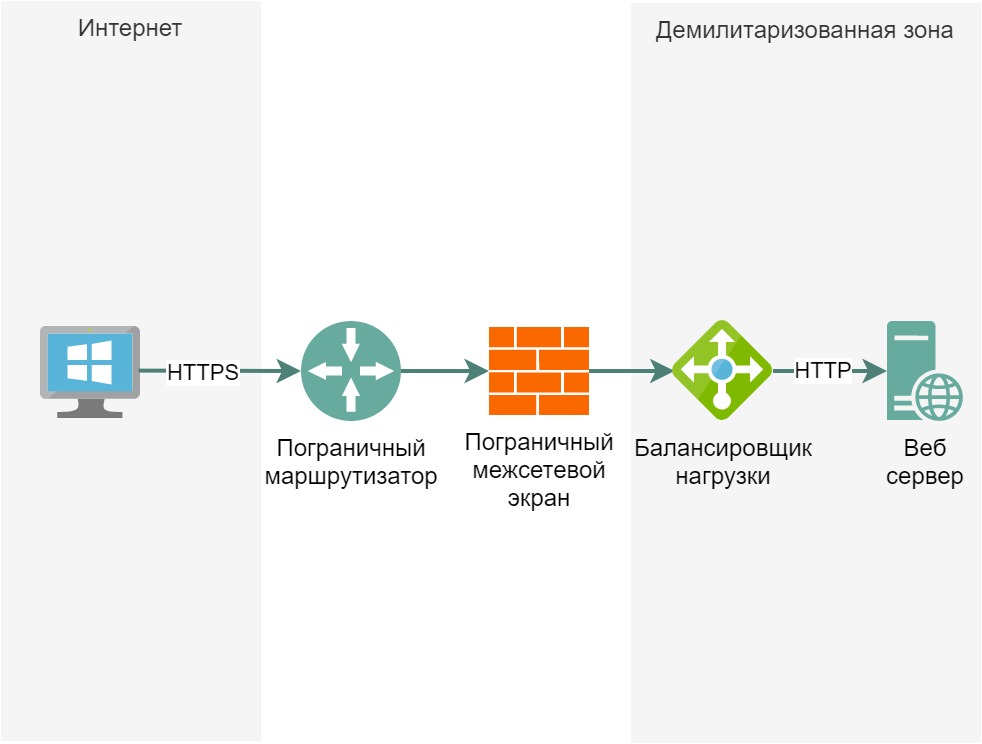
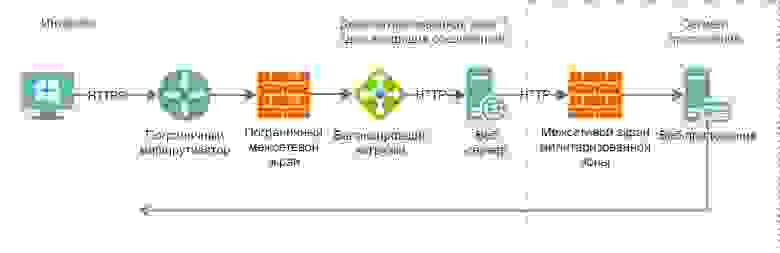
Let’s start looking at the principles of firewalling and network segmentation with the following diagram:
Border router – connects our corporate network with an edge firewall, filters traffic by ACL at the 3rd level of the OSI model;
Firewall – protects the network at the 4th layer of the OSI model, “terminates” connections;
Load balancer – software that distributes the load between web servers, decrypts HTTPS traffic;
The web server is the primary server that implements the processing of incoming requests.
Zone (security zone) – a set of network segments containing servers of the same purpose, for example, segments containing only databases, or segments containing only personal workstations, etc.
DMZ – a network segment designed to accommodate network devices interacting with external networks, in particular with the Internet.
Logical diagram of a single-layer network:
In the picture, the arrow means network access with the IP address of the source from the network device from which the arrow moves away, and with the destination IP address of the network device to which the arrow is directed. A double-headed arrow will accordingly indicate that there are two firewall rules in the firewall rule table.
Let’s see what the firewall rules will look like when traversing both network layer firewalls:
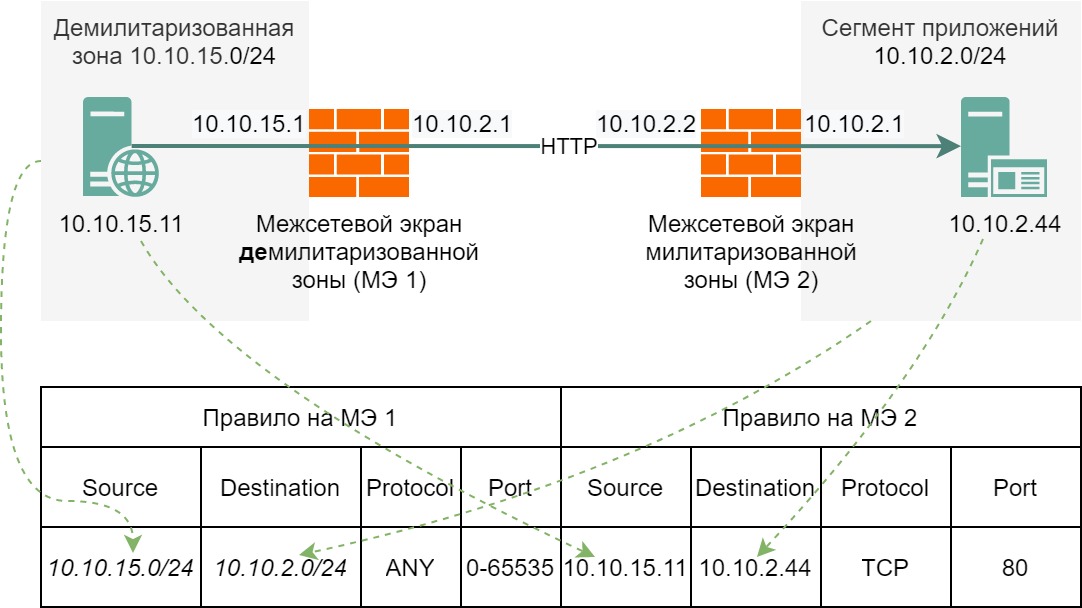
Where HTTP is the TCP transport protocol and the standard port is 80.
As you can see rules 2, the rules can be both identical and broader for the firewall due to which the traffic exits, and more point-based behind the firewall that the traffic receives. This makes it easier to write rules on the firewall due to which traffic comes out, it is enough to write one rule and if there are a lot of servers, then you will not need to write many duplicate rules. That is, the following rules are also permissible:
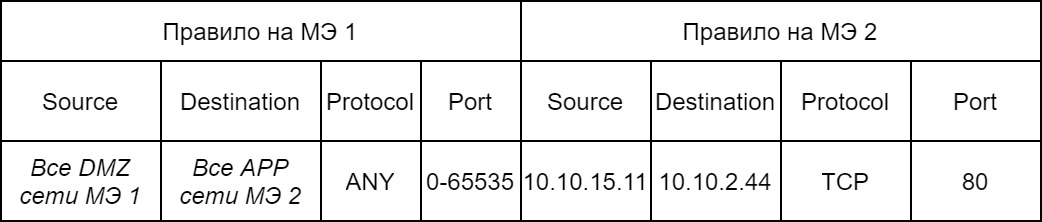
At the same time, we considered how to understand which firewall rule needs to be written.
From the point of view of practical security, the fact that the load balancer and the web server are those network devices in which vulnerabilities are likely to be found almost immediately, and if vulnerabilities are found, plays an important role remote code execution (RCE) an attacker would be able to gain high privileges in the operating system. In this case, if there was a database on the server, then the attacker would be able to get to it quickly enough.
Also, the web server performs a primary check of data for compliance with some rules and standards: both internal and well-known, for example, XML is checked against DTD, and the useful data themselves, for compliance with data formats, for example, checking that the user has entered really numbers in the number field, and not just symbols.
Roughly speaking, the demilitarized zone contains what is not a pity to lose, which can potentially be easily compromised.
Let’s go ahead and move on to the applications (APP) segment.
Application segment (APP, level II)
After initial verification, the data can be transferred to a web application that executes the main logic of the service and is hosted on a separate server:
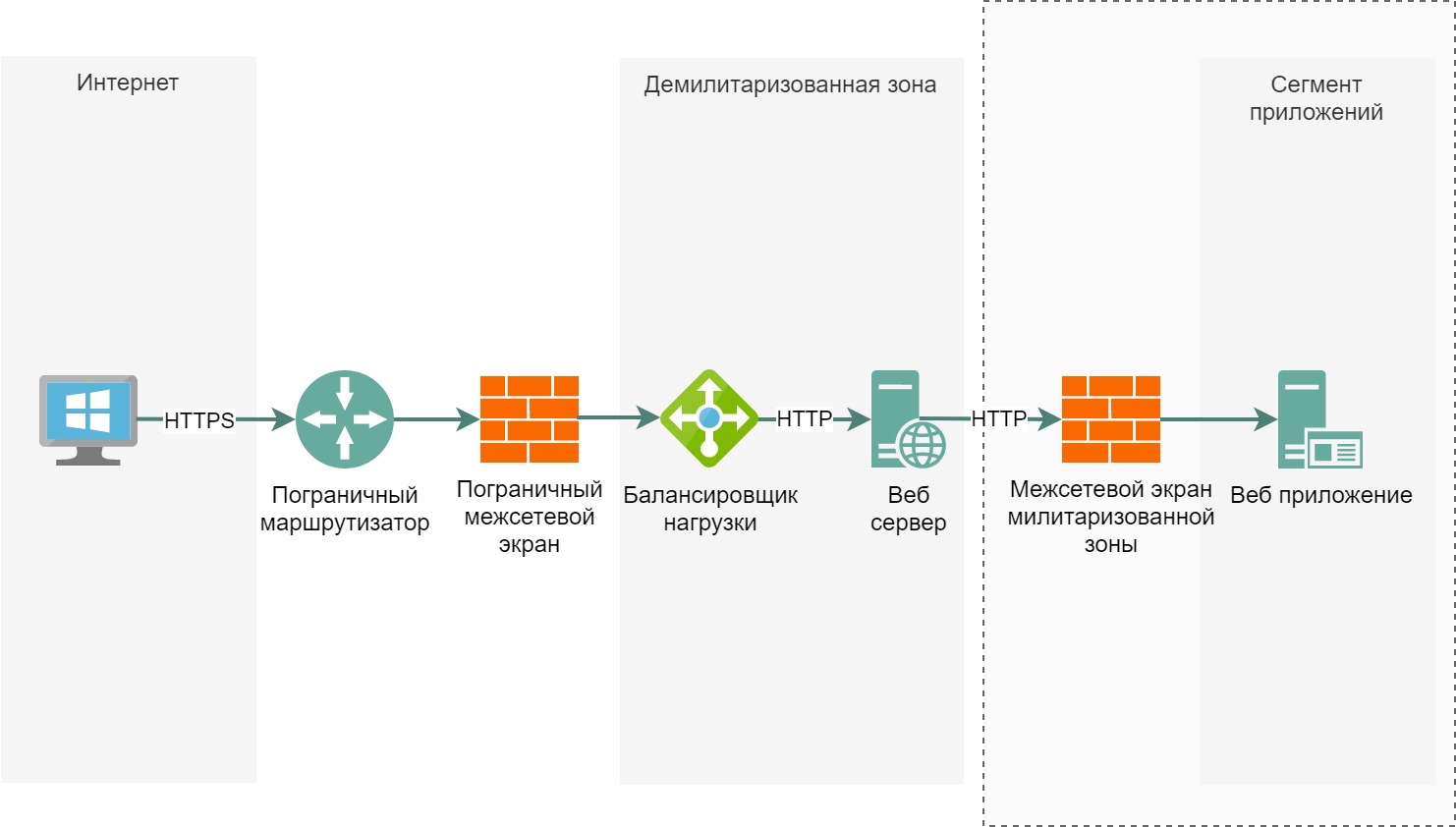
For convenience, the scheme has been simplified to 3 servers:
Server with a load balancer;
Server with web server;
Server with web application.
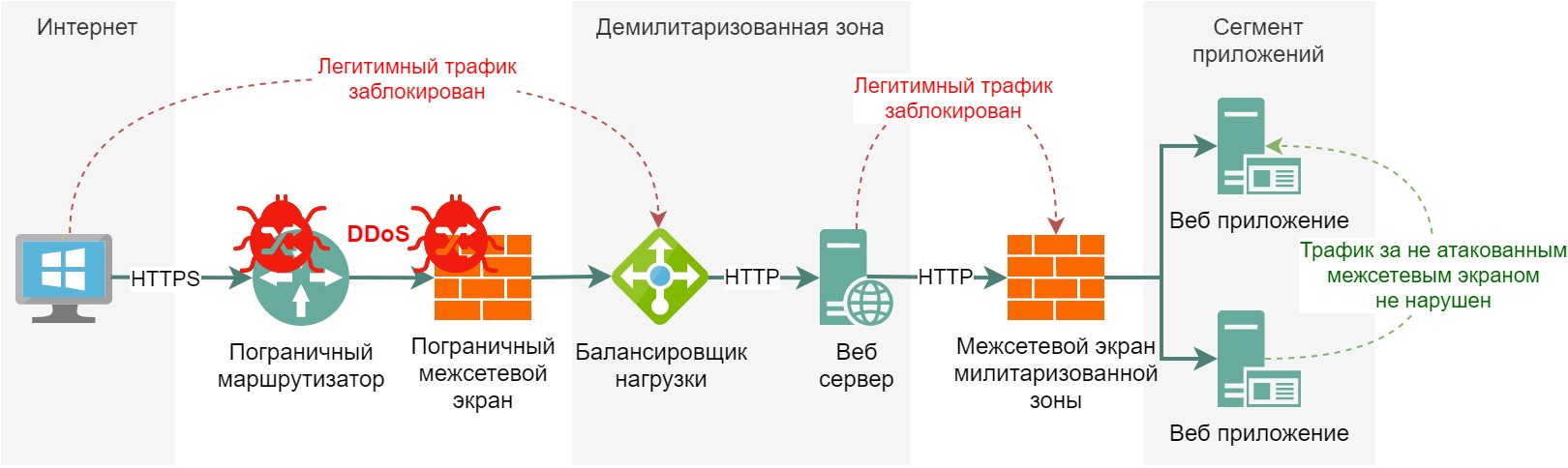
Pay attention to the dotted line, it shows the following: everything behind the demilitarized zone is a militarized zone protected by another firewall. A separate firewall is important for the following reason: if from the Internet the border firewall will be overloaded, then the entire network will stop working, it will not be able to pass the traffic of the second-level segments through itself. If we have 2 firewalls, then the internal interaction in case of failure of the border firewall will remain:
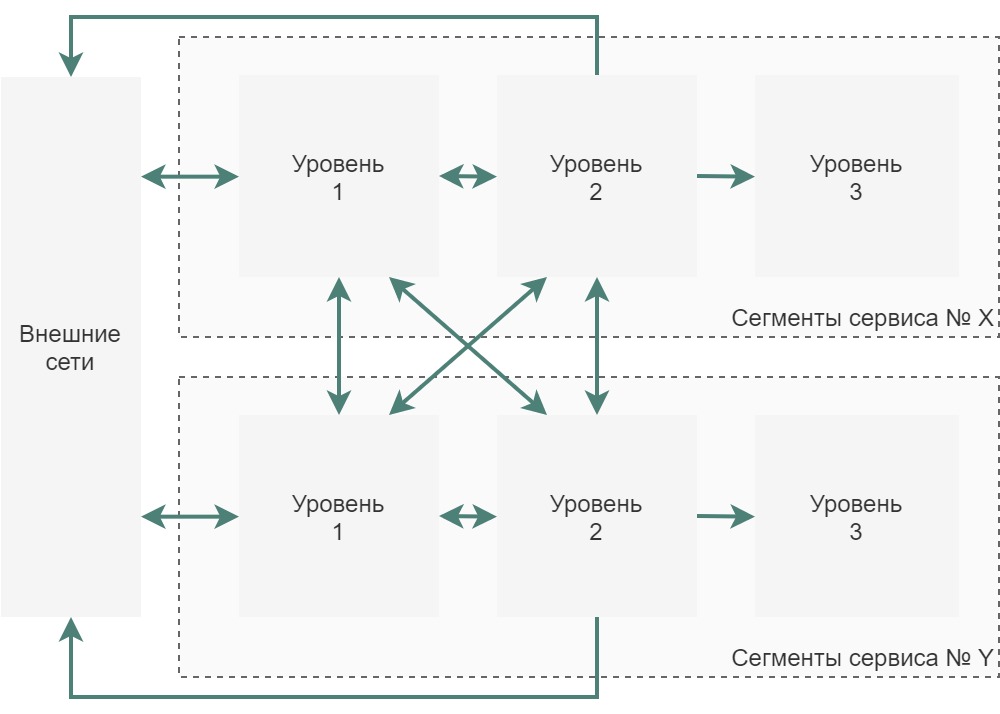
To better understand what a segment is and what a zone is, let’s complicate the scheme: let’s imagine that our company allows user authentication through an external authentication provider, let it be Unified identification and authentication system (ESIA). In this case? we have one more service in addition to what we already have – an authentication service:
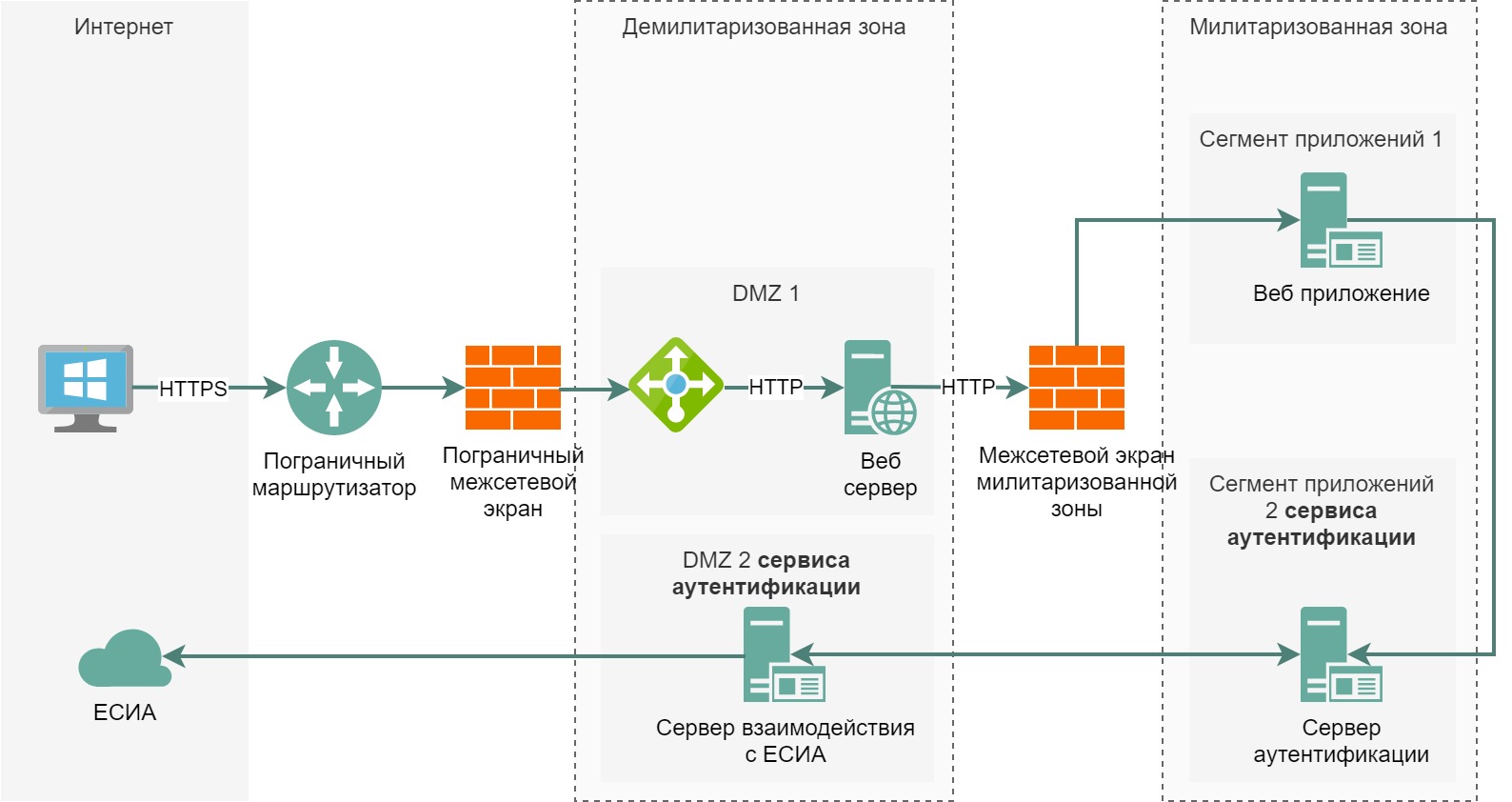
As you can see, the dashed rectangle logically unites all network segments of level 2 – application segments, in this example, there is one server in each segment.
In the demilitarized zone, we also have 2 network segments, in the original one there are 2 servers, in the new one – 1.
Let’s go back to the simplified single-service schema. Let’s take a look at our monolithic application with a huge number of lines of code in the context of the server:
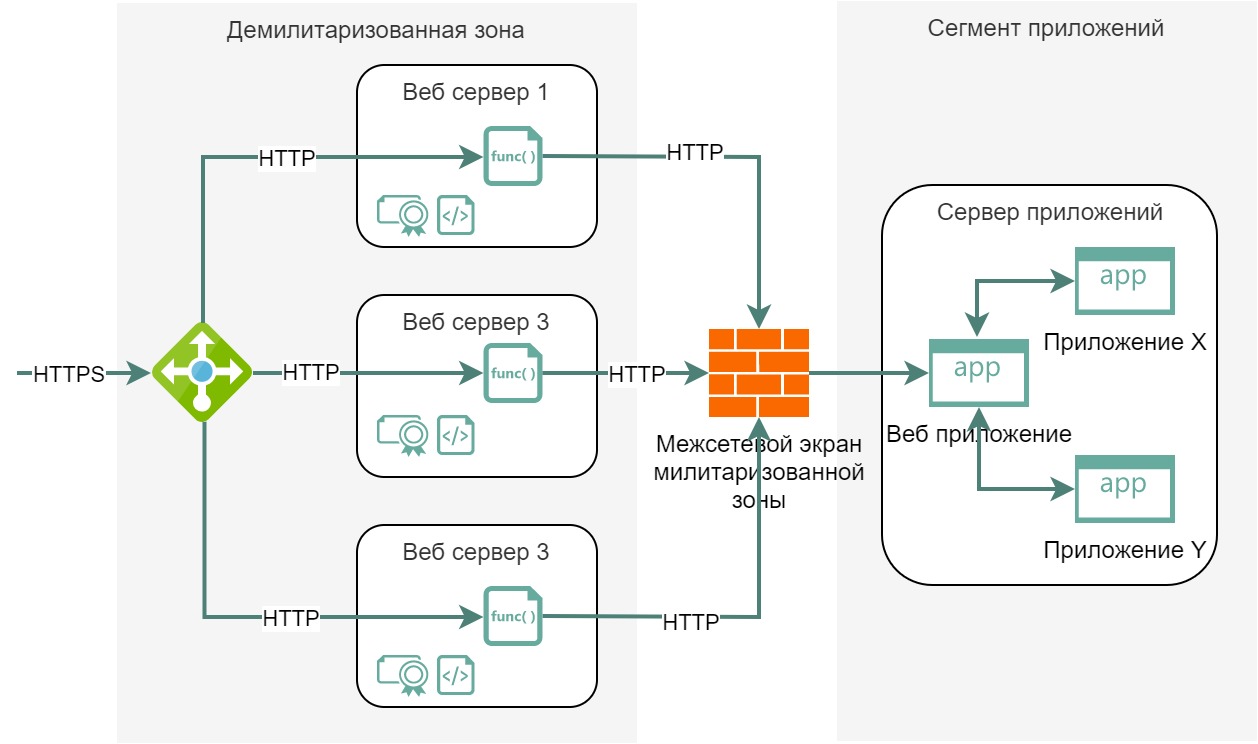
We see that the servers can contain some files necessary for the operation of applications, the applications themselves can be launched. Let’s imagine that we have not one monolithic application, but many small applications, and they all together solve the same problem, only they are located on different servers:
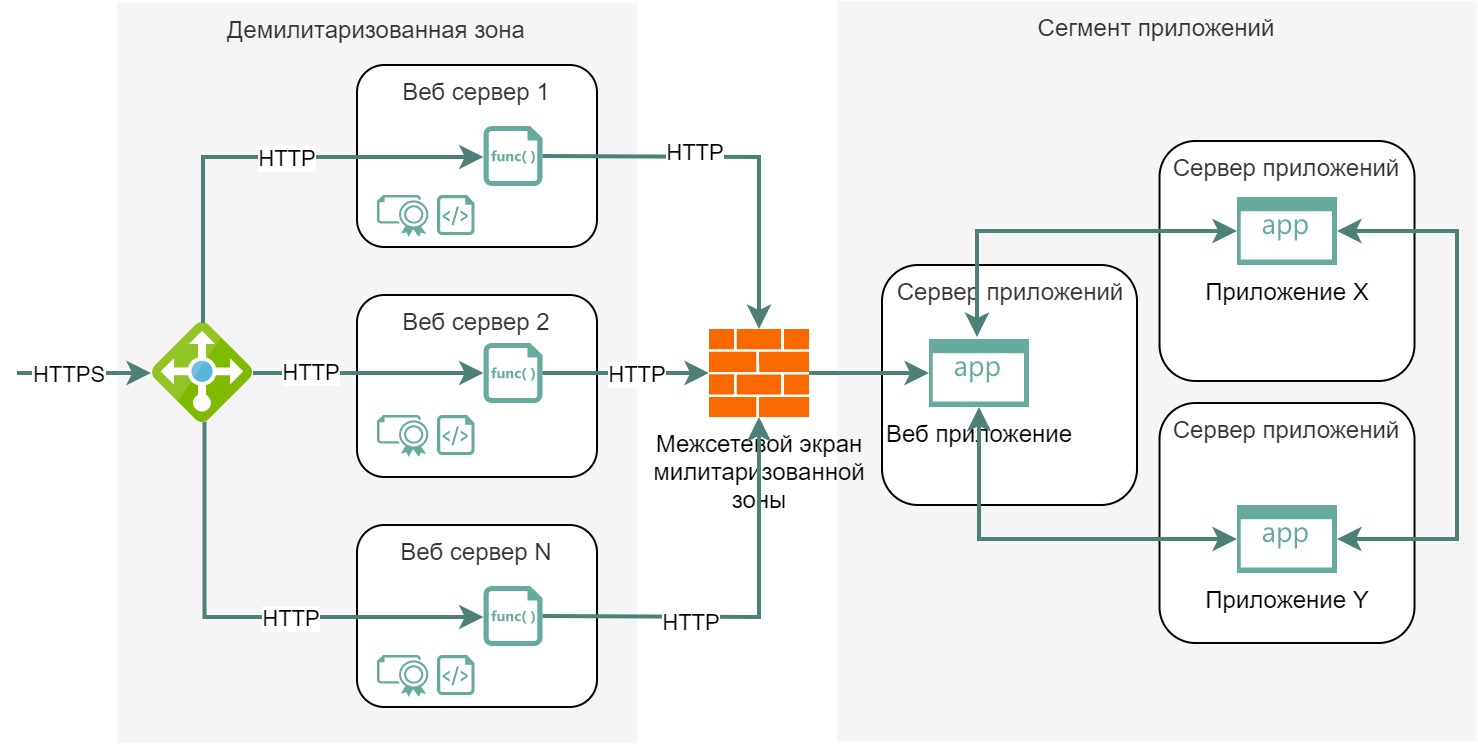
Now the initial service can have N servers in a single network segment of applications.
We can design our services like this:
One DMZ only for incoming connections from external networks;
Another DMZ is for outbound connections only.
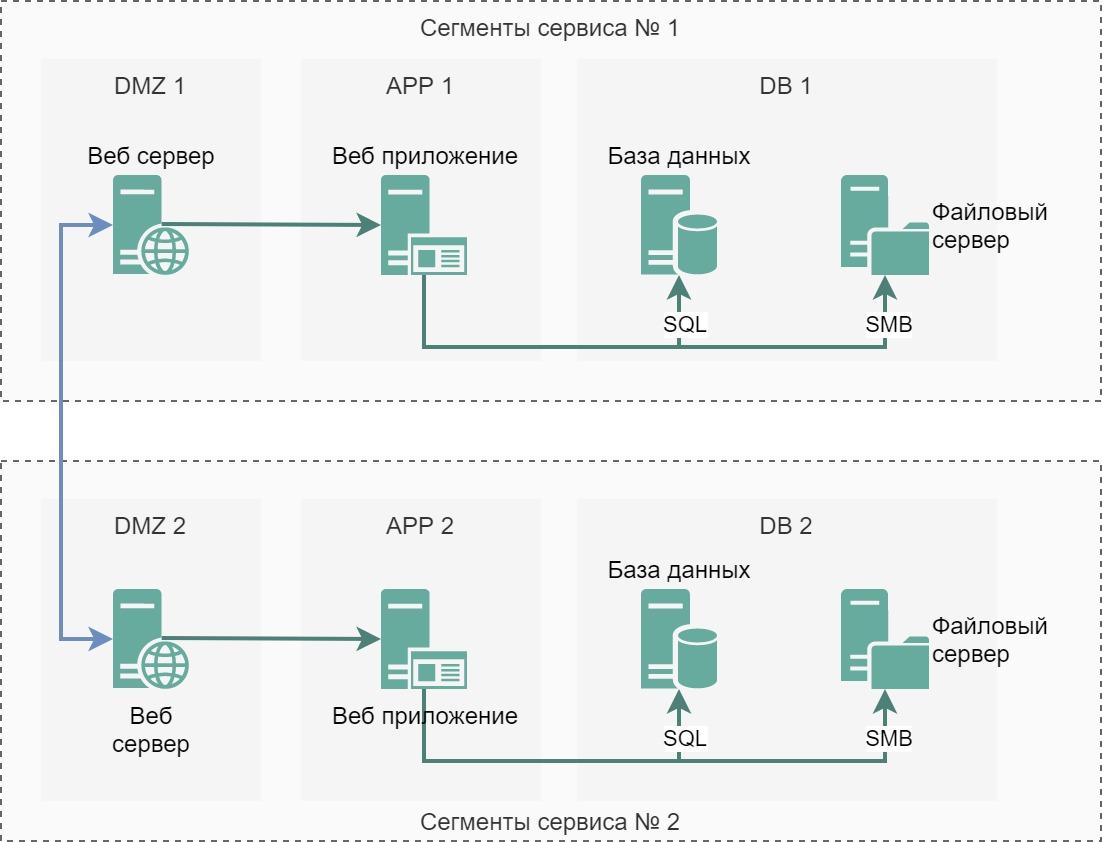
This trick will reduce possible attack vectors to our database, but will increase the number of servers and firewall rules:
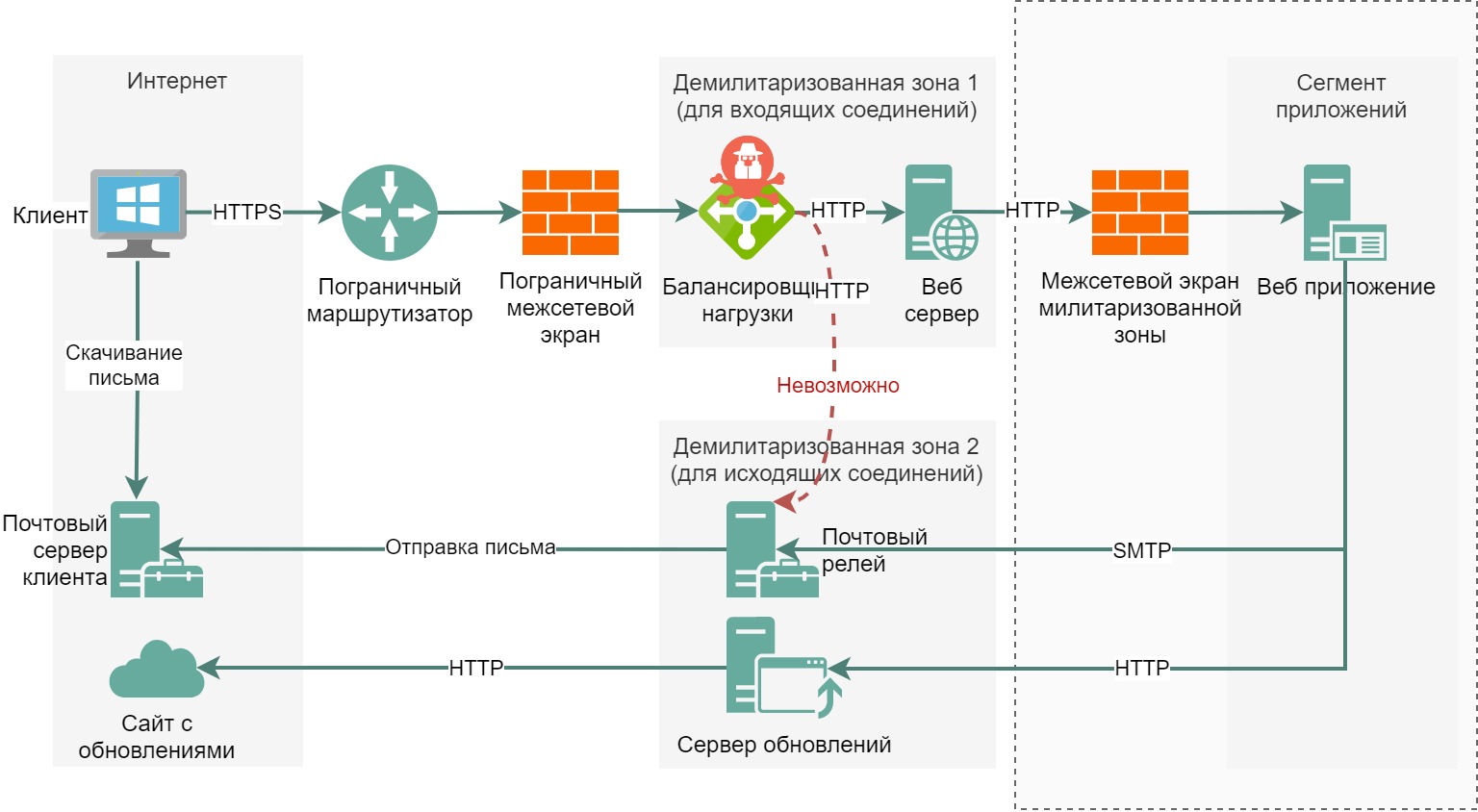
As you can see in the picture, we have DMZ 1 and DMZ 2. For example, if the balancer is compromised, the attacker will not be able to attack the servers in DMZ 2 due to the lack of rules allowing traffic, the attacker will first have to find a vulnerability in the web application in the application segment, get high privileges in the operating system of the server with the web application, and only then will it be able to attack the servers in the DMZ 2.
In this case, it becomes possible to allow outgoing accesses to external networks from segments of level 2 – APP bypassing the DMZ, since the especially demilitarized zone does not provide any protection:
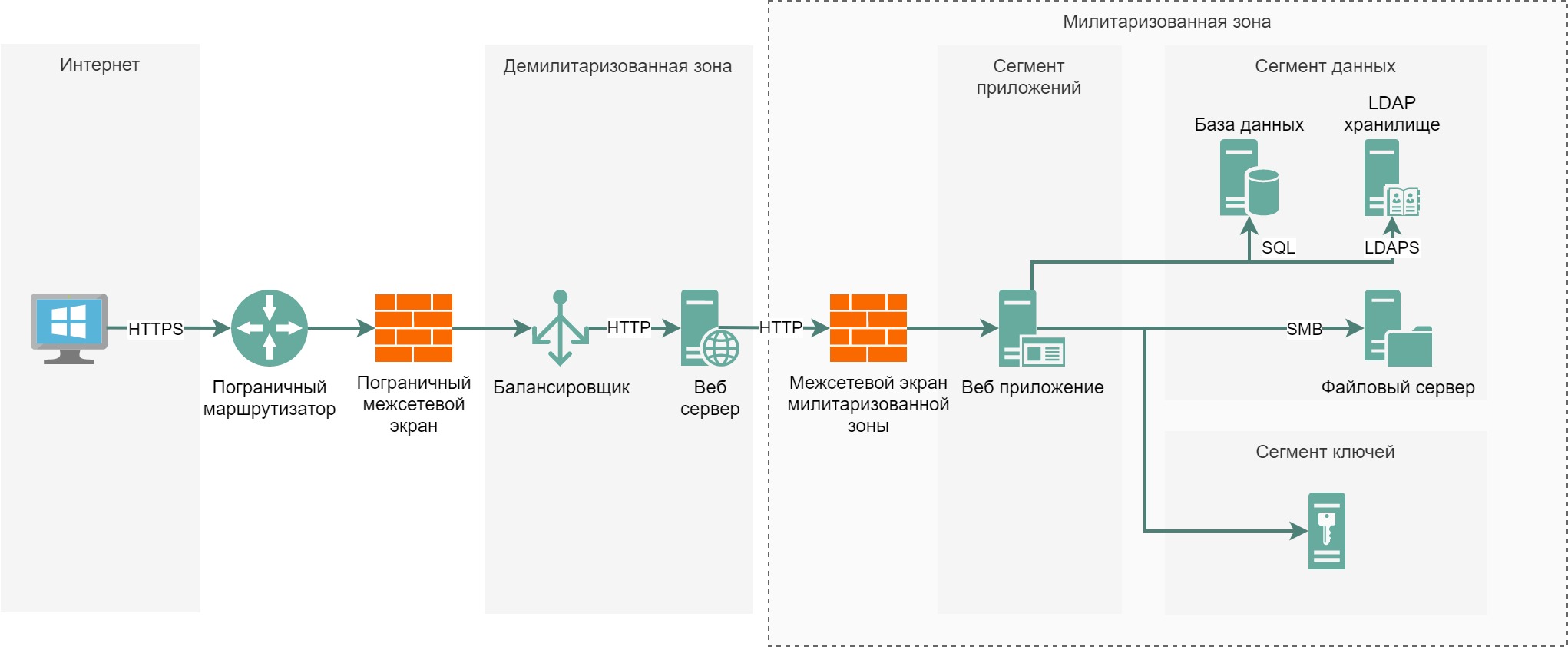
In the process of working with data, they need to be stored somewhere, it can be various SQL and no-SQL databases, file storages, LDAP directories, storages of cryptographic keys, passwords, etc.
So we move on to the third level zone – DB.
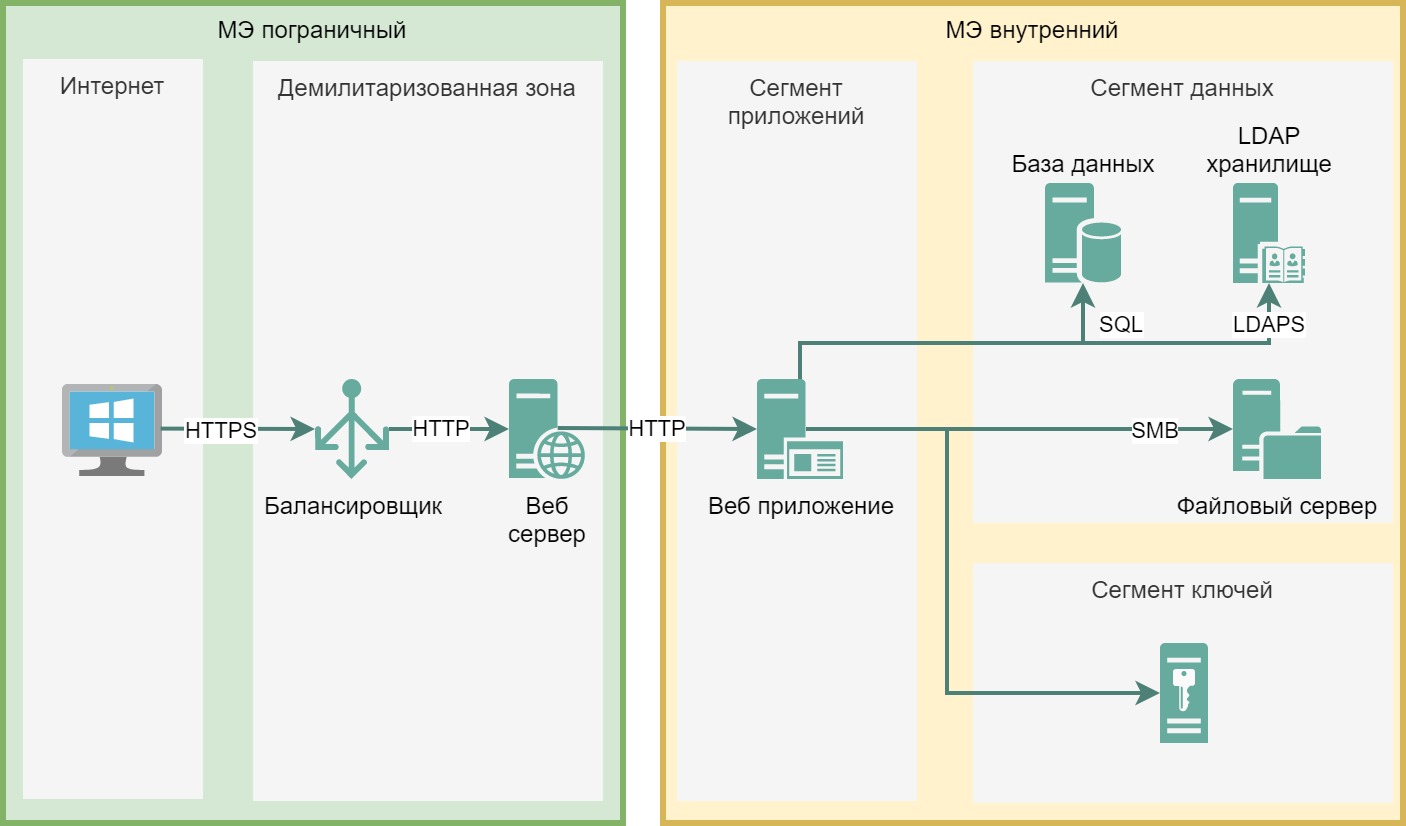
The picture does not show the third firewall, let’s imagine that the intersection of the rectangle showing the boundaries of the network segment = the intersection of the firewall, that is, we assume that any traffic movement between the segments is traffic passing through the firewall. Simplified diagram:

If you want to display firewalls, you can draw them like this:
So, without heavily loading the picture, we show which segments are behind which firewall. You can depict in some other way, for example, highlighting the segments with a certain color.
Interservice communication
Interservice communication is the interaction of servers of different services with each other. Such interaction should include rules for mutual authentication of servers with each other and firewalling rules.
The ideal situation is if, in an organization, communication between service servers always takes place through a DMZ:
Now imagine that we have configured each server and application securely enough, we trust the administrators, we have server protections, two-way strong authentication, and so on. Also, if an organization declares such a policy, then administrators, service architects, instead of developing services according to the declared policy, will place unconditional proxy servers in the DMZ, which will simply proxy traffic between the DMZ 1 and DMZ 2 segments without any verification. That is, the policy will be implemented only formally.
In this case, it would be logical to allow such interactions:

That is, we allow conditionally any interactions between the DMZ and APP zones of all services within the company.
At the same time, access to the database of someone else’s service should not be allowed in any case.
Outcome
As a result, we get the following list of basic basic rules for determining the possibility of providing network access: