Mobile containers for separate data storage
Employers have become accustomed to the fact that they can not reimburse employees who use their cars, apartments and other property for business purposes. Therefore, the idea of using personal smartphones for work quickly found its adherents.
But this “medal” is also two-sided. Employees demand guarantees that the employer does not read their correspondence or look at their photographs. Employers, in turn, are against employees sharing corporate documents on social networks or transmitting them to the media.
In this article, we will talk about what containerization technologies exist and whether they can be used to effectively separate corporate and personal data on mobile devices.

Why do employers and their employees need a container?
Employers and employees want the container to protect THEIR secrets. Only the secrets of each side are on opposite sides of the container – the employer’s secrets are inside the container, and the employee’s secrets are outside.
Therefore, employers want employees not to be able to take data out of the container, and employees want the employer not to have access to data outside the container.
Employees are ready to put up with restrictions such as prohibiting the installation of applications from unverified sources, but even the potential ability to access their personal data is not worth it for them to work remotely from their smartphone or tablet.
There is another desire in which employers and employees converge. Both of them want to be able to put any application in the container without additional modifications. If applications need to be refined, this is expensive for the employer and often inconvenient for the employee.
Feature of containers for iOS
In our last article, we convinced the reader that iOS is a closed ecosystem that needs to be accepted as it is. IOS containers are another proof of this.
From a containerization point of view, iOS has a built-in mechanism for separating corporate and personal. Apple refers to corporate as managed and personal as unmanaged.
Apps, accounts, and URLs in Safari can be managed in iOS. With built-in policies, you can prevent data transfers between managed and unmanaged, but only random… This means that an employee cannot transfer an attachment from corporate mail to personal mail or WhatsApp, but can copy the attachment text and paste it anywhere!
Apple believes that it is impossible to protect against deliberate data leakage, so decided take care about your conscious users and prevent them from accidentally leaking …

If a company decides that the built-in security mechanisms in iOS are not enough for it, it has to implement additional security mechanisms in enterprise applications. For example, by blocking access to the clipboard in them. The easiest way to do this is using the SDK of the developers of mobility management systems, for example, SafePhone…
Variety of Android containers
Android has historically provided more options for containerization.
The first company to make Android containers possible was Samsung. In 2012, Samsung Knox Enterprise Security Platform features became available for the first time on the Samsung Galaxy S3 smartphone. In particular, Knox containers. Most modern Samsung devices support them as well. Many features of the Samsung Knox platform are free, but the Knox container features were a paid option. Google later announced its free enterprise platform, Android for Enterprise, with a smaller set of features.
Over the years, the number of container management features that were exclusively available on Samsung devices dwindled as they came to Google. As a result, starting from
On July 1, 2021, Samsung made the decision to provide Knox containerization capabilities for free. As part of the Samsung Knox platform, there are still paid options that Google does not have. For example, the corporate service for updating the firmware of mobile devices E-FOTA One, which we talked about in one of the previous articles.
But specifically, Knox containers are now free.
A container in Android, or, as Google calls it, a “work profile” looks to the user as a separate folder or a separate desktop where corporate applications are located. Applications in a container behave as if nothing exists outside the container. The container has its own clipboard, its own virtual memory for storing files, etc.
Without explicit permission from the administrator, the user cannot move anything outside the container.
Like what you need? Yes, but not without important features.
Samsung Knox includes client libraries for Android, with which you can develop a management client that will create a container itself, apply the necessary security policies in it and fill it with applications.

This scheme works like this:
The management client is installed on the mobile device.
The user registers the device with the management server.
The management client creates and configures the container for work. Then it periodically asks the management server if these settings have changed.
It is possible to deliver settings updates faster with Google push notifications, but they are optional.
The advantage of this scheme is that it can be built on the customer’s local infrastructure (on-premise). This is important for big business in Russia.
The Android for Enterprise platform from Google also has client libraries and with their help you can manage devices without containers – install applications, configure restrictions, etc. You can even create a container, put the built-in Gmail or Google Chrome into it and prevent the employee from copying files from the container. All of this will work on-premise.
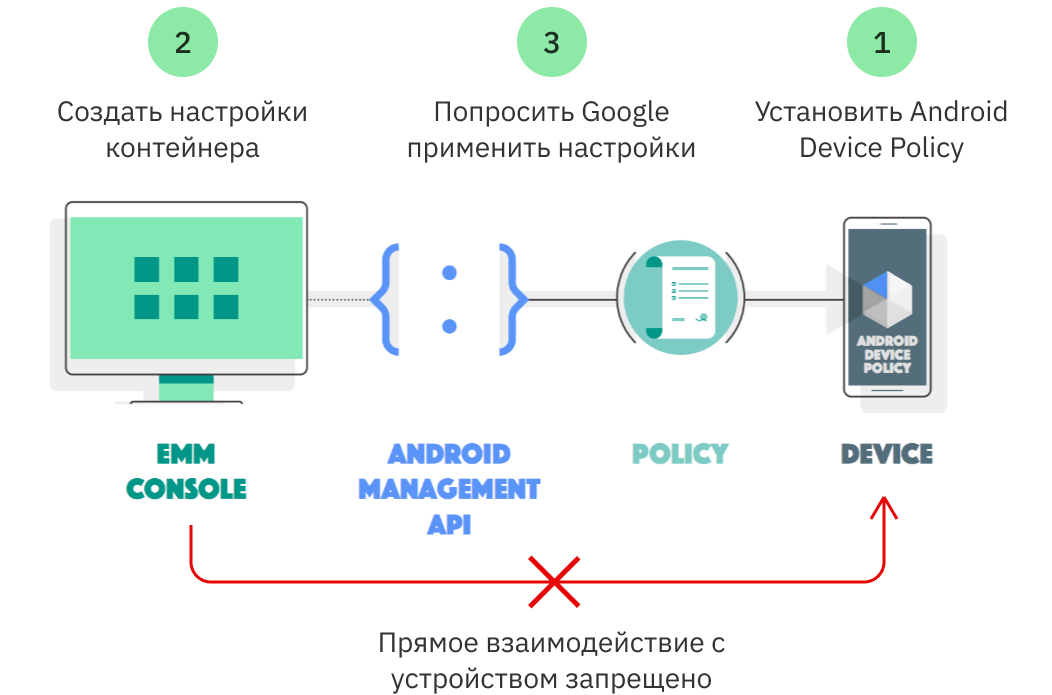
But Google client libraries will not help if you need to place your own application or some kind of application from Google Play in a container. In this case, you need to use the Android Management API, which works according to a simple scheme:
A management client from Google – Android Device Policy is installed on the mobile device.
The administrator creates container settings – which applications to install into it, which restriction policies to apply, etc.
The server passes the container settings to Google using the Android Management API. Further, Google provides their application on the device independently. In this case, all teams and all distributions of corporate applications must be transferred to Google.

Source: https://developers.google.com/android/management/introduction
IOS management works in a similar way, but in the case of iOS, the corporate management server sends to Apple only notifications about the presence of a command. Further, the device picks up commands and application distributions from the corporate server, and not from the Apple server.
Google may have wanted to create a more user-friendly control technology than Apple, but not all companies are willing to put up with the fact that Google knows what security settings and what control commands they tell their mobile devices. After all, this creates the risk that the commands may be changed or not delivered at all.
Corporate Android for personal use
Many companies that buy mobile devices for work for their employees also allow personal use. In this case, containers are also needed to separate corporate and personal data. If you plan to implement such a scenario, please note that starting with Android 11, this scenario has fundamental limitations.
Starting with Android 11, you cannot manage both the container and what is outside of it at the same time. This is done to prevent employers from accessing personal data of employees.
The price of privacy turned out to be quite high. Now, on corporate devices with a container, it is impossible to determine geolocation, install applications outside the container, and scan the device for viruses.
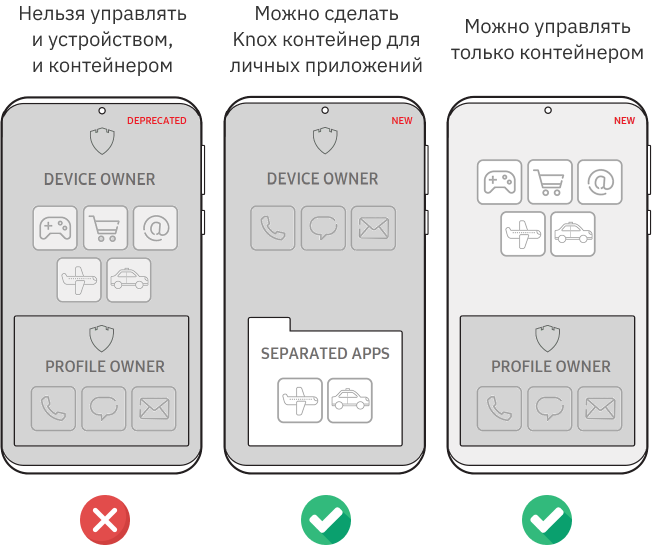
Samsung has offered the original Knox Separated Apps technology as an alternative. The technology allows you to create a container for personal applications on corporate devices. The employer controls the entire device and does not access employee data in the personal container. And applications in a personal container do not get access to corporate data, so they cannot be used to implement information leakage.
Knox Separated Apps, like Knox containers, will also become free from July 1, 2021.
Tips for top managers
No container needed on the working device… Any smartphone that the company gives to an employee is perceived as a worker. An employee will never believe that his employer does not have access to his personal data, even if it is promised by Google. Therefore, working devices are easier and cheaper to turn into containers as a whole, installing applications only from corporate storage, prohibiting unnecessary network activity and services that allow you to “share” corporate data with competitors or the media.
This approach has been proven, standardized, and has been used for years on most work laptops in large companies.
Personal devices are not always cheap and convenient… On the one hand, it may seem that the use of personal devices allows employees to save money on buying gadgets, but in practice it turns out that maintaining a “zoo” of smartphones from different manufacturers is more expensive than a “nursery” where there are many devices, but they are of the same type.

The corporate software does not work in a very special way on every new device. Each major version of Android from 4 to 12 is seriously different. Each manufacturer has its own build of Android. Each Android build, especially the Chinese one, has its own “cockroaches” – unmanaged memory and battery managers that strive to close the application as soon as possible or prevent it from receiving data from the server in time, additional permissions that the user must manually grant to the application and which he can take away any moment, etc.
If you plan to mobilize a company 3-5 years in advance, it is cheaper to choose several device models, and then check and develop corporate software (document flow client, applications with BI reporting, instant messengers, etc.) on these specific models. After all, not thousands of Facebook developers around the world write corporate software. Therefore, the less the variability of devices, the fewer errors, the fewer the number of vulnerabilities and the lower the likelihood of their successful exploitation. In short, everyone is more comfortable and safer.
If you have any questions or doubts after reading the article, write about them in the comments.