Microsoft released October security updates
Microsoft has released planned security updates to close 81 vulnerabilities, 3 of which have been classified as critical. Among the other 3 vulnerabilities were publicly disclosed (0-day), and the exploitation of one vulnerability was recorded in real attacks. The highest CVSS rating among all closed vulnerabilities was 9.0 out of 10. In this article I will talk about the most important moments of the October Tuesday updates.
Remember, almost 90% of all vulnerabilities already had patches from the manufacturers at the time of their release, so it is so important not only to update your software, but also to do it in a timely manner (according to Flexera’s Vulnerability Review Report).
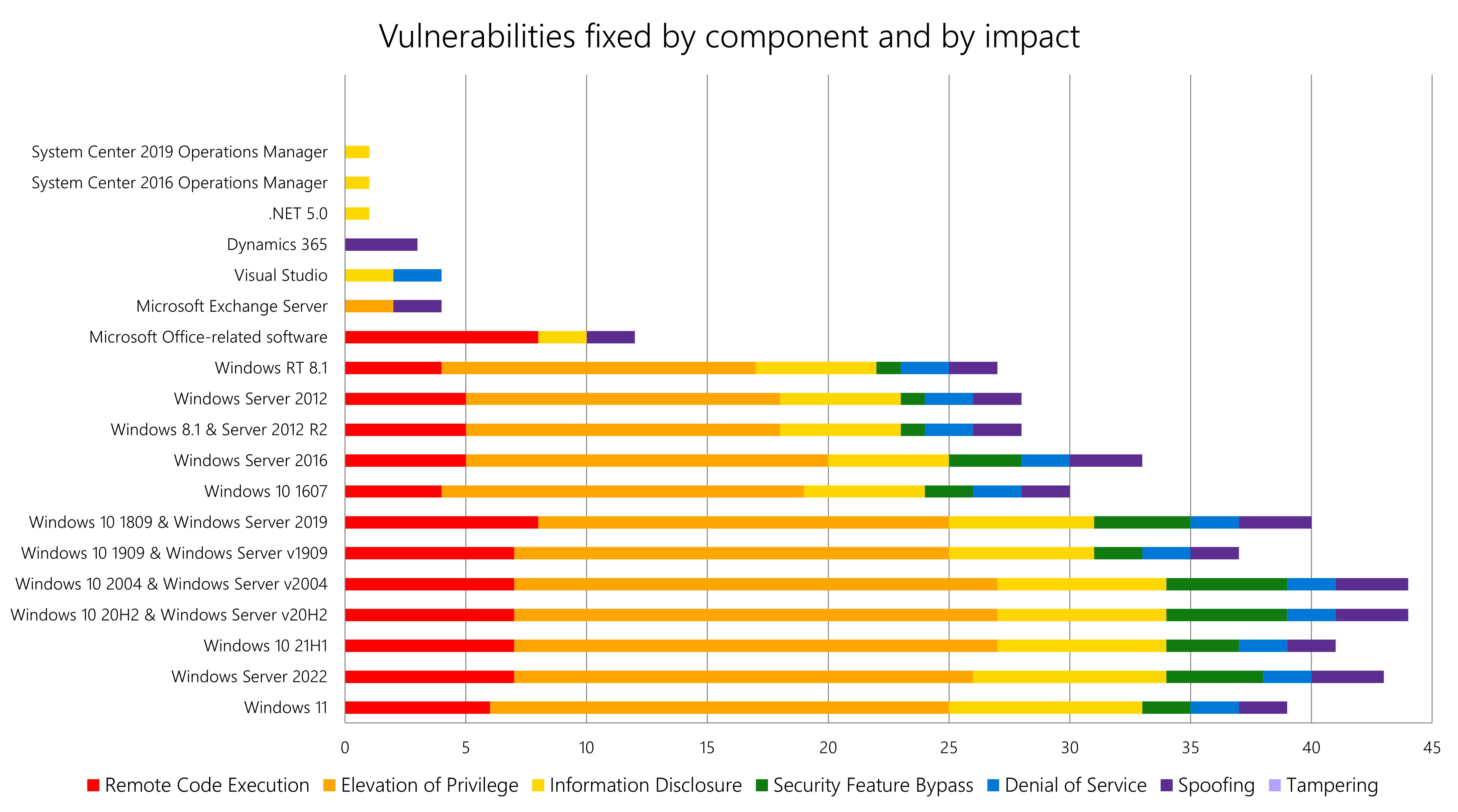
A summary of the number and type of vulnerabilities closed in October is shown in the graph.
The following vulnerabilities and security updates should be particularly noted
CVE-2021-36970 – Windows Print Spooler Spoofing Vulnerability (Important, CVSS Score 8.8)
According to the Microsoft Exploitation Index, the likelihood of attacks using this vulnerability is high.
It should be noted that after the installation of the August security update, the default behavior of the “Point and Print” function has changed – now only administrative accounts can install and update printer drivers. Details can be found in our blog…
CVE-2021-41340 – Windows Graphics Component Remote Code Execution Vulnerability (Important, CVSS Score 7.8)
CVE-2021-40461 – Windows Hyper-V Remote Code Execution Vulnerability (Critical, CVSS Score 8.0)
The vulnerability affects Windows 10 and Windows Server 2019 versions 1909, 2004, 20H2, 21H1, and Windows 11 and Windows Server 2022.
CVE-2021-38672 – Windows Hyper-V Remote Code Execution Vulnerability (Critical, CVSS Score 8.0)
Only Windows 11 and Windows Server 2022 are affected by this vulnerability.
CVE-2021-40486 – Microsoft Word Remote Code Execution Vulnerability (Critical, CVSS Score 7.8)
This vulnerability can be exploited through the preview panel.
CVE-2021-40485 – Microsoft Excel Remote Code Execution Vulnerability (Important, CVSS Score 7.8)
This vulnerability cannot be exploited through the preview panel.
CVE-2021-40480 – Microsoft Visio Remote Code Execution Vulnerability (Important, CVSS Score 7.8)
This vulnerability cannot be exploited through the preview panel.
CVE-2021-40487 – Microsoft SharePoint Server Remote Code Execution Vulnerability (Important, CVSS Score 8.1)
According to the Microsoft Exploitation Index, the likelihood of attacks using this vulnerability is high.
Information about the following vulnerabilities was made public:
CVE-2021-40469 – Windows DNS Server Remote Code Execution Vulnerability (Important, CVSS Score 7.2)
The exploitation of the next vulnerability was recorded in real attacks:
CVE-2021-40449 – Win32k Elevation of Privilege Vulnerability (Important, CVSS Score 7.8)
Servicing stack updates
Great news for administrators – OS servicing stack updates no longer need to be installed separately! Servicing Stack Updates (SSU) for Windows 10 and Windows Server 2019 versions 1809, 1909, 2004, 20H1, 20H2, 21H1 are now integrated into a single cumulative update package. All details on SSU updates you can look on our portal.
As always, you can find the most complete and up-to-date information on vulnerabilities and security updates on our portal Security Update Guide… For a complete list of KB articles for the respective service packs that have potential installation issues, see release notes…
you also can look recording our monthly webinar Microsoft Security Updates Briefing for a more detailed breakdown of this release of updates and the most important vulnerabilities.
Artyom Sinitsyn CISSP, CCSP, MCSE, Certified Azure Security Engineer
Senior Leader of Information Security Programs in Central and Eastern Europe
Microsoft