Linux Experiments LAB
Future students of the course “Administrator Linux.Basic” and all those interested are invited to an open lesson on the topic “Bash. Writing Simple Scripts”.
The author of the article: OTUS expert – Alexander Kolesnikov.
The purpose of this article is to show how you can set up a stand on a regular laptop, which can help you learn about the various subsystems of any operating system. The purpose of this article will be the Linux operating system, but any operating system can be deployed at the same stand. In this article, the main focus will be on using Linux to work with network interfaces for access on a network where VLAN is used.
Stand description
A bench for testing OS subsystems will consist of:
-
Virtualization tools VirtualBox
-
Operating system Windows 8
-
Operating system Kali Linux (Debian)
-
Virtual machine GNS3to be used to emulate hardware for VLAN configuration.
All the tools used are free software, therefore they are completely free. To build a network, we will use the following scheme:
Setting up the stand
For GNS3 to work properly, you need to use a VM, which can be downloaded from the official website. It is on it that devices that can be deployed from official images of operating systems of devices, such as CISCO, will be emulated. The main problems with the stand configuration are carried out in the system GNS3. The following steps are worth doing before starting work:
-
Open “Settings” and go to the Server section:
The options that need to be changed are highlighted in red, enable the server and select the network interface that will be used by the GNS VM. It is very important that the GNS3 server and the virtual machine are on the same network. Otherwise, you will not be able to connect devices on the network diagram.
2. On the VirtualBox tab, through the new option, add virtual machines that will be used for the stand:
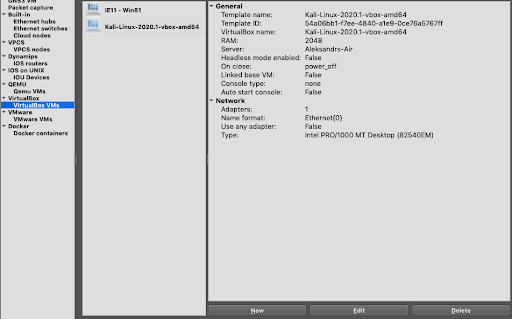
3. It is necessary to add device firmware, you can find test firmware on the network. You can add them to the interface through the “IOS Routers” section.
4. Disconnect all virtual machines and select the “Not Attached” option for the network interface.
5. Create a network diagram as described in the section “Description of the stand”.
Subsequent configuration steps relate to setting up operating systems and devices that are used on the network. To start this process, you need to run the circuit. This can be done from the control menu.
Important note: be careful about how much RAM you have allocated for each virtual machine, it may happen that there are not enough resources. An emergency reboot may damage data.
To configure devices, enter the following commands:
Windows operating system:
1.Start the operating system
2.Set through any convenient interface ip address – 10.0.20.3
Kali Linux operating system:
1.Start the operating system, set the ip address – 10.0.3.5
EtherSwitch1:
– vlan database
– vlan 20
– exit
– conf t
– (int fa0 / 0) Kali port
– no shut
– exit
– int fa0 / 1
– switchport mode trunk
– no shut
– exit
– exit
-write
EtherSwitch2:
– vlan database
– vlan 20
– exit
– conf t
– int fa0 / 0 (port between switches)
– switchport mode trunk
– no shut
– exit
– int fa0 / 1 (port for Windows 8)
– switchport mode access
– switchport access vlan 20
– no shut
– exit
– exit
– write
-
Run the Ping 10.0.20.3 command from the Kali Linux operating system. The required result is shown in the snapshot below:

Why is there no response from the target host? There are at least two reasons:
1.No route to the network where the host is located.
2. The network uses VLAN, which imposes special conditions on traffic marking. By default, they do not work for data being sent.
Is it possible to send packets to neighboring VLANs using the subsystems that are by default in the Linux operating system, in this case Debian? Spoiler – you can.
Experiment with network devices
For further testing, we will use a tool called yersinia. Basically, this tool is used to work with network protocols. It is used to test device misconfigurations. We will use its functionality to send packets with additional tags for VLAN networks. To run it, you will have to install it on the Kali Linux operating system. To install, just type in the terminal:
apt-get update && apt-get install yersinia
Our makeshift network uses 802.1q as the protocol for VLAN. This protocol assumes that a special Tag will be specified in the packet header, which will be used for routing. Let’s try to simulate the behavior of the protocol if we were a client of the target virtual network. To do this, run the command:
yersinia dot1q -attack 1 -source 08:00:27:1f:30:76 -dest FF:FF:FF:FF:FF:FF
-vlan1 0001 -priority1 07 -cfi1 0 -l2proto1 800
-vlan2 0020 -priority2 07 -cfi2 0 -l2proto2 800
-ipsource 10.0.20.6 -ipdest 10.0.20.3 -ipproto 1 -payload LINUXOTUS -interface eth0Unfortunately, we will not be able to catch this message on the end host. To do this, you need to listen for traffic between hosts on the network. This is very easy to do if you bring up the context menu in GNS3 by clicking on the connection, like this:
This will open WireShark:
And you can see all the traffic on any part of the network. By the way, here’s our payload:

Initially, when configuring the network, an error was made that allows sending data for all networks via the Native VLAN. So you can try to send data using standard OS tools. To do this, run the following commands in the terminal:
modprobe 8021q – Load the kernel module to work with encapsulation
vconfig add eth0 1 – add virtual interface
ifconfig eth0.1 up
vconfig add eth0.1 20 – add another virtual interface
ifconfig eth0.1.20 10.0.20.6 netmask 255.255.255.0 up
ip route add 10.0.20.0/24 via 10.0.20.6 dev eth0.1.20 – configure a route to the target network
arp -s 10.0.20.3 FF:FF:FF:FF:FF:FF -i eth0.1.20 – a small life hack so that the OS thinks that it has information about the remote machine.
It is worth mentioning that such interaction in real conditions is possible only in UDP format. For TCP, you will need to guess the identifiers that are used for the handshake procedure. Let’s try to send something meaningful to the target host. To do this, deploy on the host netcat:
And from a Kali Linux machine using a tool for working with network packages – Scapy. Send UDP message: LINUXOTUSNC:
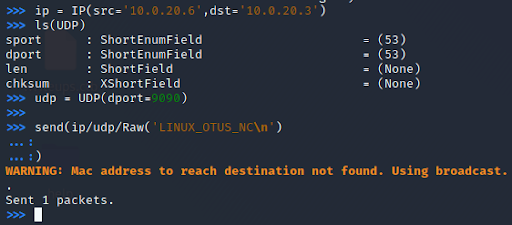
Let’s look at the data that was transmitted in traffic:
What ended up being displayed on the target machine:
As a result, we were able to use standard operating system tools to establish networking between hosts that were separated by VLANs. The experiment showed that the Linux operating system has amazing flexibility right out of the box and allows you to work with the peculiarities of network protocols using only a few commands. Not all operating systems can boast of such functionality, most would have to install additional software, which most likely cost extra money.
Learn more about the course “Administrator Linux.Basic”
Sign up for an open lesson on the topic “Bash. Writing Simple Scripts”.





